Connect data from Microsoft Defender XDR to Microsoft Sentinel
Microsoft Sentinel's Microsoft Defender XDR connector with incident integration allows you to stream all Microsoft Defender XDR incidents and alerts into Microsoft Sentinel, and keeps the incidents synchronized between both portals. Microsoft Defender XDR incidents include all their alerts, entities, and other relevant information. They also include alerts from Microsoft Defender XDR's component services Microsoft Defender for Endpoint, Microsoft Defender for Identity, Microsoft Defender for Office 365, and Microsoft Defender for Cloud Apps, as well as alerts from other services such as Microsoft Purview Data Loss Prevention and Microsoft Entra ID Protection. The Microsoft Defender XDR connector also brings incidents from Microsoft Defender for Cloud, although in order to synchronize alerts and entities from these incidents, you must enable the Microsoft Defender for Cloud connector, otherwise your Microsoft Defender for Cloud incidents will appear empty. Learn more about the available connectors for Microsoft Defender for Cloud.
The connector also lets you stream advanced hunting events from all of the above Defender components into Microsoft Sentinel, allowing you to copy those Defender components' advanced hunting queries into Microsoft Sentinel, enrich Sentinel alerts with the Defender components' raw event data to provide additional insights, and store the logs with increased retention in Log Analytics.
For more information about incident integration and advanced hunting event collection, see Microsoft Defender XDR integration with Microsoft Sentinel.
The Microsoft Defender XDR connector is now generally available.
Note
For information about feature availability in US Government clouds, see the Microsoft Sentinel tables in Cloud feature availability for US Government customers.
Prerequisites
You must have a valid license for Microsoft Defender XDR, as described in Microsoft Defender XDR prerequisites.
Your user must be assigned the Global Administrator or Security Administrator roles on the tenant you want to stream the logs from.
Your user must have read and write permissions on your Microsoft Sentinel workspace.
To make any changes to the connector settings, your user must be a member of the same Microsoft Entra tenant with which your Microsoft Sentinel workspace is associated.
Install the solution for Microsoft Defender XDR from the Content Hub in Microsoft Sentinel. For more information, see Discover and manage Microsoft Sentinel out-of-the-box content.
Prerequisites for Active Directory sync via MDI
Your tenant must be onboarded to Microsoft Defender for Identity.
You must have the MDI sensor installed.
Connect to Microsoft Defender XDR
In Microsoft Sentinel, select Data connectors, select Microsoft Defender XDR from the gallery and select Open connector page.
The Configuration section has three parts:
Connect incidents and alerts enables the basic integration between Microsoft Defender XDR and Microsoft Sentinel, synchronizing incidents and their alerts between the two platforms.
Connect entities enables the integration of on-premises Active Directory user identities into Microsoft Sentinel through Microsoft Defender for Identity.
Connect events enables the collection of raw advanced hunting events from Defender components.
These are explained in greater detail below. See Microsoft Defender XDR integration with Microsoft Sentinel for more information.
Connect incidents and alerts
To ingest and synchronize Microsoft Defender XDR incidents, with all their alerts, to your Microsoft Sentinel incidents queue:
Mark the check box labeled Turn off all Microsoft incident creation rules for these products. Recommended, to avoid duplication of incidents.
(This check box will not appear once the Microsoft Defender XDR connector is connected.)Select the Connect incidents & alerts button.
Note
When you enable the Microsoft Defender XDR connector, all of the Microsoft Defender XDR components’ connectors (the ones mentioned at the beginning of this article) are automatically connected in the background. In order to disconnect one of the components’ connectors, you must first disconnect the Microsoft Defender XDR connector.
To query Microsoft Defender XDR incident data, use the following statement in the query window:
SecurityIncident
| where ProviderName == "Microsoft 365 Defender"
Connect entities
Use Microsoft Defender for Identity to sync user entities from your on-premises Active Directory to Microsoft Sentinel.
Verify that you've satisfied the prerequisites for syncing on-premises Active Directory users through Microsoft Defender for Identity (MDI).
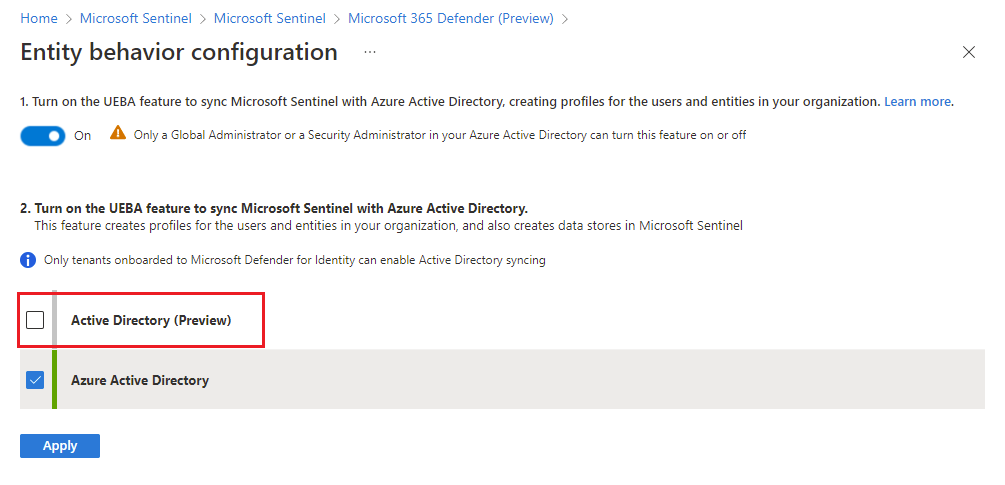
Select the Go the UEBA configuration page link.
In the Entity behavior configuration page, if you haven't yet enabled UEBA, then at the top of the page, move the toggle to On.
Mark the Active Directory (Preview) check box and select Apply.
Connect events
If you want to collect advanced hunting events from Microsoft Defender for Endpoint or Microsoft Defender for Office 365, the following types of events can be collected from their corresponding advanced hunting tables.
Mark the check boxes of the tables with the event types you wish to collect:
- Defender for Endpoint
- Defender for Office 365
- Defender for Identity
- Defender for Cloud Apps
- Defender alerts
Table name Events type DeviceInfo Machine information, including OS information DeviceNetworkInfo Network properties of devices, including physical adapters, IP and MAC addresses, as well as connected networks and domains DeviceProcessEvents Process creation and related events DeviceNetworkEvents Network connection and related events DeviceFileEvents File creation, modification, and other file system events DeviceRegistryEvents Creation and modification of registry entries DeviceLogonEvents Sign-ins and other authentication events on devices DeviceImageLoadEvents DLL loading events DeviceEvents Multiple event types, including events triggered by security controls such as Windows Defender Antivirus and exploit protection DeviceFileCertificateInfo Certificate information of signed files obtained from certificate verification events on endpoints Click Apply Changes.
To query the advanced hunting tables in Log Analytics, enter the table name from the list above in the query window.
Verify data ingestion
The data graph in the connector page indicates that you are ingesting data. You'll notice that it shows one line each for incidents, alerts, and events, and the events line is an aggregation of event volume across all enabled tables. Once you have enabled the connector, you can use the following KQL queries to generate more specific graphs.
Use the following KQL query for a graph of the incoming Microsoft Defender XDR incidents:
let Now = now();
(range TimeGenerated from ago(14d) to Now-1d step 1d
| extend Count = 0
| union isfuzzy=true (
SecurityIncident
| where ProviderName == "Microsoft 365 Defender"
| summarize Count = count() by bin_at(TimeGenerated, 1d, Now)
)
| summarize Count=max(Count) by bin_at(TimeGenerated, 1d, Now)
| sort by TimeGenerated
| project Value = iff(isnull(Count), 0, Count), Time = TimeGenerated, Legend = "Events")
| render timechart
Use the following KQL query to generate a graph of event volume for a single table (change the DeviceEvents table to the required table of your choosing):
let Now = now();
(range TimeGenerated from ago(14d) to Now-1d step 1d
| extend Count = 0
| union isfuzzy=true (
DeviceEvents
| summarize Count = count() by bin_at(TimeGenerated, 1d, Now)
)
| summarize Count=max(Count) by bin_at(TimeGenerated, 1d, Now)
| sort by TimeGenerated
| project Value = iff(isnull(Count), 0, Count), Time = TimeGenerated, Legend = "Events")
| render timechart
In the Next steps tab, you’ll find some useful workbooks, sample queries, and analytics rule templates that have been included. You can run them on the spot or modify and save them.
Next steps
In this document, you learned how to integrate Microsoft Defender XDR incidents, and advanced hunting event data from Microsoft Defender component services, into Microsoft Sentinel, using the Microsoft Defender XDR connector. To learn more about Microsoft Sentinel, see the following articles:
- Learn how to get visibility into your data, and potential threats.
- Get started detecting threats with Microsoft Sentinel.
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for