Update SOC processes
A security operations center (SOC) is a centralized function within an organization that integrates people, processes, and technology. A SOC implements the organization's overall cybersecurity framework. The SOC collaborates the organizational efforts to monitor, alert, prevent, detect, analyze, and respond to cybersecurity incidents. SOC teams, led by a SOC manager, may include incident responders, SOC analysts at levels 1, 2, and 3, threat hunters, and incident response managers.
SOC teams use telemetry from across the organization's IT infrastructure, including networks, devices, applications, behaviors, appliances, and information stores. The teams then co-relate and analyze the data, to determine how to manage the data and which actions to take.
To successfully migrate to Microsoft Sentinel, you need to update not only the technology that the SOC uses, but also the SOC tasks and processes. This article describes how to update your SOC and analyst processes as part of your migration to Microsoft Sentinel.
Update analyst workflow
Microsoft Sentinel offers a range of tools that map to a typical analyst workflow, from incident assignment to closure. Analysts can flexibly use some or all of the available tools to triage and investigate incidents. As your organization migrates to Microsoft Sentinel, your analysts need to adapt to these new toolsets, features, and workflows.
Incidents in Microsoft Sentinel
In Microsoft Sentinel, an incident is a collection of alerts that Microsoft Sentinel determines have sufficient fidelity to trigger the incident. Hence, with Microsoft Sentinel, the analyst triages incidents in the Incidents page first, and then proceeds to analyze alerts, if a deeper dive is needed. Compare your SIEM's incident terminology and management areas with Microsoft Sentinel.
Analyst workflow stages
This table describes the key stages in the analyst workflow, and highlights the specific tools relevant to each activity in the workflow.
| Assign | Triage | Investigate | Respond |
|---|---|---|---|
| Assign incidents: • Manually, in the Incidents page • Automatically, using playbooks or automation rules |
Triage incidents using: • The incident details in the Incident page • Entity information in the Incident page, under the Entities tab • Jupyter Notebooks |
Investigate incidents using: • The investigation graph • Microsoft Sentinel Workbooks • The Log Analytics query window |
Respond to incidents using: • Playbooks and automation rules • Microsoft Teams War Room |
The next sections map both the terminology and analyst workflow to specific Microsoft Sentinel features.
Assign
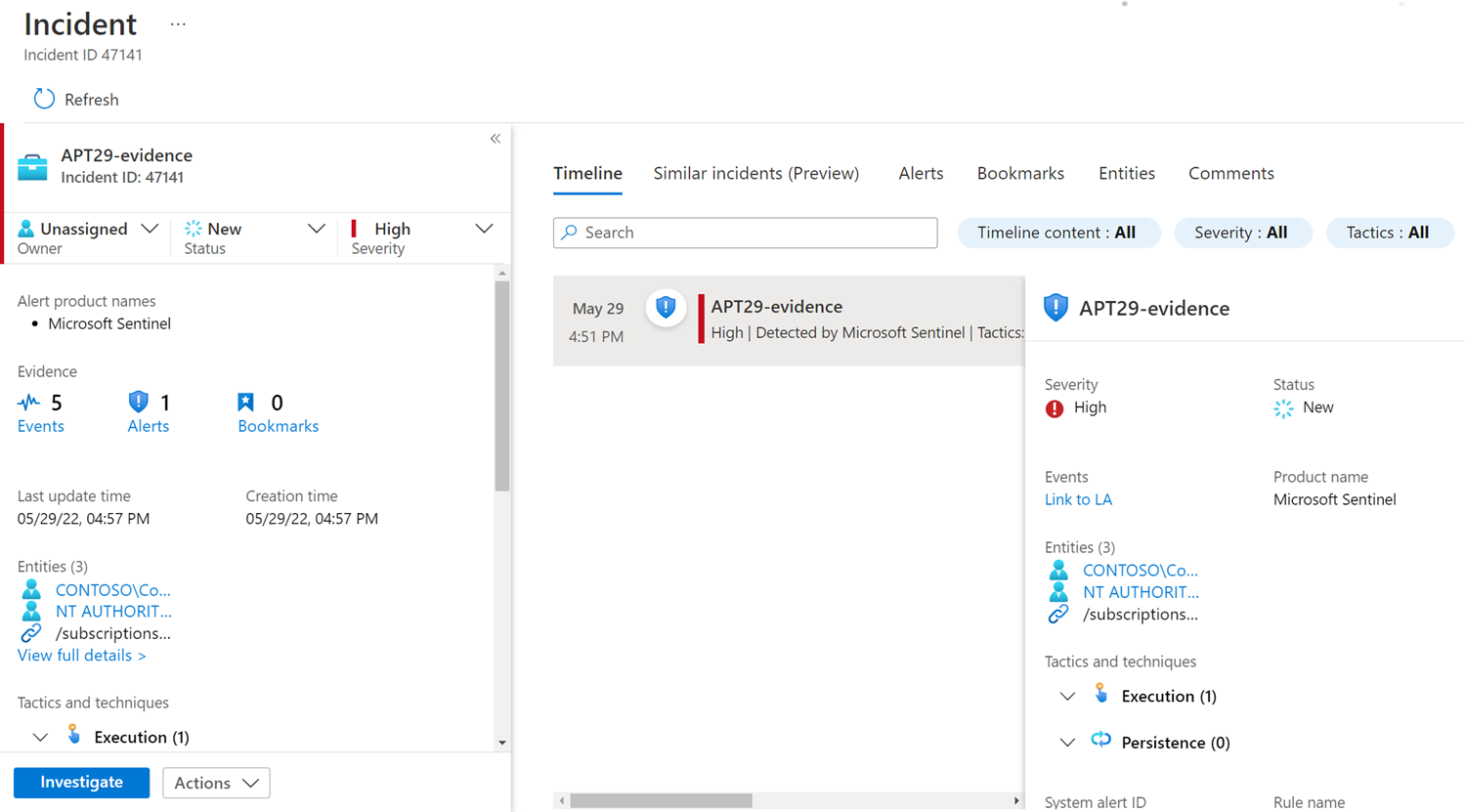
Use the Microsoft Sentinel Incidents page to assign incidents. The Incidents page includes an incident preview, and a detailed view for single incidents.
To assign an incident:
- Manually. Set the Owner field to the relevant user name.
- Automatically. Use a custom solution based on Microsoft Teams and Logic Apps, or an automation rule.
Triage
To conduct a triage exercise in Microsoft Sentinel, you can start with various Microsoft Sentinel features, depending on your level of expertise and the nature of the incident under investigation. As a typical starting point, select View full details in the Incident page. You can now examine the alerts that comprise the incident, review bookmarks, select entities to drill down further into specific entities, or add comments.
Here are suggested actions to continue your incident review:
- Select Investigation for a visual representation of the relationships between the incidents and the relevant entities.
- Use a Jupyter notebook to perform an in-depth triage exercise for a particular entity. You can use the Incident triage notebook for this exercise.
Expedite triage
Use these features and capabilities to expedite triage:
- For quick filtering, in the Incidents page, search for incidents associated to a specific entity. Filtering by entity in the Incidents page is faster than filtering by the entity column in legacy SIEM incident queues.
- For faster triage, use the Alert details screen to include key incident information in the incident name and description, such as the related user name, IP address, or host. For example, an incident could be dynamically renamed to
Ransomware activity detected in DC01, whereDC01is a critical asset, dynamically identified via the customizable alert properties. - For deeper analysis, in the Incidents page, select an incident and select Events under Evidence to view specific events that triggered the incident. The event data is visible as the output of the query associated with the analytics rule, rather than the raw event. The rule migration engineer can use this output to ensure that the analyst gets the correct data.
- For detailed entity information, in the Incidents page, select an incident and select an entity name under Entities to view the entity's directory information, timeline, and insights. Learn how to map entities.
- To link to relevant workbooks, select Incident preview. You can customize the workbook to display additional information about the incident, or associated entities and custom fields.
Investigate
Use the investigation graph to deeply investigate incidents. From the Incidents page, select an incident and select Investigate to view the investigation graph.
With the investigation graph, you can:
- Understand the scope and identify the root cause of potential security threats by correlating relevant data with any involved entity.
- Dive deeper into entities, and choose between different expansion options.
- Easily see connections across different data sources by viewing relationships extracted automatically from the raw data.
- Expand your investigation scope using built-in exploration queries to surface the full scope of a threat.
- Use predefined exploration options to help you ask the right questions while investigating a threat.
From the investigation graph, you can also open workbooks to further support your investigation efforts. Microsoft Sentinel includes several workbook templates that you can customize to suit your specific use case.
Respond
Use Microsoft Sentinel automated response capabilities to respond to complex threats and reduce alert fatigue. Microsoft Sentinel provides automated response using Logic Apps playbooks and automation rules.
Use one of the following options to access playbooks:
- The Automation > Playbook templates tab
- The Microsoft Sentinel Content hub
- The Microsoft Sentinel GitHub repository
These sources include a wide range of security-oriented playbooks to cover a substantial portion of use cases of varying complexity. To streamline your work with playbooks, use the templates under Automation > Playbook templates. Templates allow you to easily deploy playbooks into the Microsoft Sentinel instance, and then modify the playbooks to suit your organization's needs.
See the SOC Process Framework to map your SOC process to Microsoft Sentinel capabilities.
Compare SIEM concepts
Use this table to compare the main concepts of your legacy SIEM to Microsoft Sentinel concepts.
| ArcSight | QRadar | Splunk | Microsoft Sentinel |
|---|---|---|---|
| Event | Event | Event | Event |
| Correlation Event | Correlation Event | Notable Event | Alert |
| Incident | Offense | Notable Event | Incident |
| List of offenses | Tags | Incidents page | |
| Labels | Custom field in SOAR | Tags | Tags |
| Jupyter Notebooks | Jupyter Notebooks | Microsoft Sentinel notebooks | |
| Dashboards | Dashboards | Dashboards | Workbooks |
| Correlation rules | Building blocks | Correlation rules | Analytics rules |
| Incident queue | Offences tab | Incident review | Incident page |
Next steps
After migration, explore Microsoft's Microsoft Sentinel resources to expand your skills and get the most out of Microsoft Sentinel.
Also consider increasing your threat protection by using Microsoft Sentinel alongside Microsoft Defender XDR and Microsoft Defender for Cloud for integrated threat protection. Benefit from the breadth of visibility that Microsoft Sentinel delivers, while diving deeper into detailed threat analysis.
For more information, see:
- Rule migration best practices
- Webinar: Best Practices for Converting Detection Rules
- Security Orchestration, Automation, and Response (SOAR) in Microsoft Sentinel
- Manage your SOC better with incident metrics
- Microsoft Sentinel learning path
- SC-200 Microsoft Security Operations Analyst certification
- Microsoft Sentinel Ninja training
- Investigate an attack on a hybrid environment with Microsoft Sentinel
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for