Detect threats out-of-the-box
After you've set up Microsoft Sentinel to collect data from all over your organization, you'll need to dig through all that data to detect security threats to your environment. But don't worry—Microsoft Sentinel provides templates to help you create threat detection rules to do all that work for you. These rules are known as analytics rules.
Microsoft's team of security experts and analysts designed these analytics rule templates based on known threats, common attack vectors, and suspicious activity escalation chains. Rules created from these templates automatically search across your environment for any activity that looks suspicious. Many of the templates can be customized to search for activities, or filter them out, according to your needs. The alerts generated by these rules create incidents that you can assign and investigate in your environment.
This article helps you understand how to detect threats with Microsoft Sentinel.
View detections
To view the installed analytics rules and detections in Microsoft Sentinel, go to Analytics > Rule templates. This tab contains all the installed rule templates, according to the types displayed in the following table. To find more rule templates, go to the Content hub in Microsoft Sentinel to install the related product solutions or standalone content.
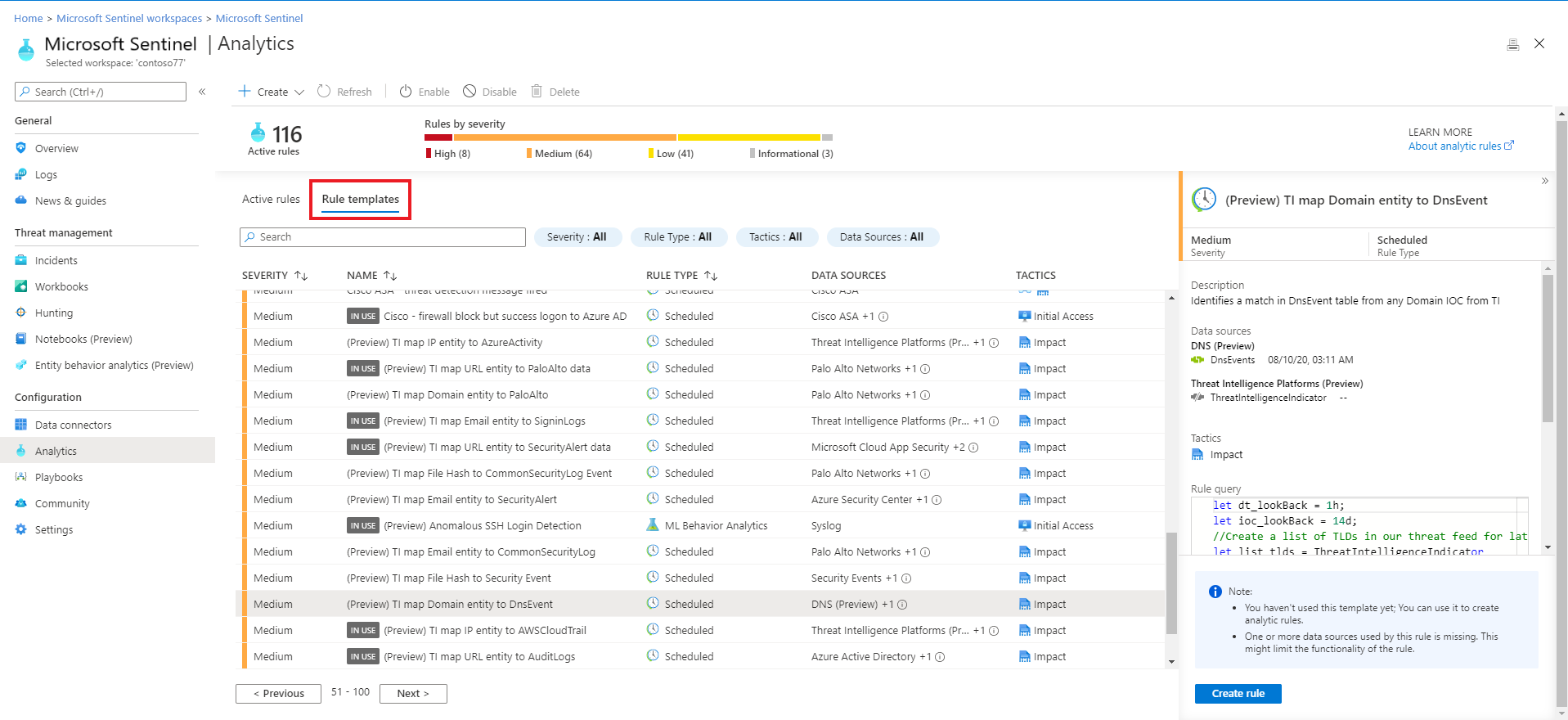
Detections include:
| Rule type | Description |
|---|---|
| Microsoft security | Microsoft security templates automatically create Microsoft Sentinel incidents from the alerts generated in other Microsoft security solutions, in real time. You can use Microsoft security rules as a template to create new rules with similar logic. For more information about security rules, see Automatically create incidents from Microsoft security alerts. |
| Fusion (some detections in Preview) |
Microsoft Sentinel uses the Fusion correlation engine, with its scalable machine learning algorithms, to detect advanced multistage attacks by correlating many low-fidelity alerts and events across multiple products into high-fidelity and actionable incidents. Fusion is enabled by default. Because the logic is hidden and therefore not customizable, you can only create one rule with this template. The Fusion engine can also correlate alerts produced by scheduled analytics rules with alerts from other systems, producing high-fidelity incidents as a result. |
| Machine learning (ML) behavioral analytics | ML behavioral analytics templates are based on proprietary Microsoft machine learning algorithms, so you can't see the internal logic of how they work and when they run. Because the logic is hidden and therefore not customizable, you can only create one rule with each template of this type. |
| Threat Intelligence | Take advantage of threat intelligence produced by Microsoft to generate high fidelity alerts and incidents with the Microsoft Threat Intelligence Analytics rule. This unique rule isn't customizable, but when enabled, automatically matches Common Event Format (CEF) logs, Syslog data or Windows DNS events with domain, IP and URL threat indicators from Microsoft Threat Intelligence. Certain indicators contain more context information through MDTI (Microsoft Defender Threat Intelligence). For more information on how to enable this rule, see Use matching analytics to detect threats. For more information on MDTI, see What is Microsoft Defender Threat Intelligence |
| Anomaly | Anomaly rule templates use machine learning to detect specific types of anomalous behavior. Each rule has its own unique parameters and thresholds, appropriate to the behavior being analyzed. While the configurations of out-of-the-box rules can't be changed or fine-tuned, you can duplicate a rule, and then change and fine-tune the duplicate. In such cases, run the duplicate in Flighting mode and the original concurrently in Production mode. Then compare results, and switch the duplicate to Production if and when its fine-tuning is to your liking. For more information, see Use customizable anomalies to detect threats in Microsoft Sentinel and Work with anomaly detection analytics rules in Microsoft Sentinel. |
| Scheduled | Scheduled analytics rules are based on queries written by Microsoft security experts. You can see the query logic and make changes to it. You can use the scheduled rules template and customize the query logic and scheduling settings to create new rules. Several new scheduled analytics rule templates produce alerts that are correlated by the Fusion engine with alerts from other systems to produce high-fidelity incidents. For more information, see Advanced multistage attack detection. Tip: Rule scheduling options include configuring the rule to run every specified number of minutes, hours, or days, with the clock starting when you enable the rule. We recommend being mindful of when you enable a new or edited analytics rule to ensure that the rules get the new stack of incidents in time. For example, you might want to run a rule in synch with when your SOC analysts begin their workday, and enable the rules then. |
| Near-real-time (NRT) | NRT rules are limited set of scheduled rules, designed to run once every minute, in order to supply you with information as up-to-the-minute as possible. They function mostly like scheduled rules and are configured similarly, with some limitations. For more information, see Detect threats quickly with near-real-time (NRT) analytics rules in Microsoft Sentinel. |
Important
Some of the Fusion detection templates are currently in PREVIEW (see Advanced multistage attack detection in Microsoft Sentinel to see which ones). See the Supplemental Terms of Use for Microsoft Azure Previews for additional legal terms that apply to Azure features that are in beta, preview, or otherwise not yet released into general availability.
Use analytics rule templates
This procedure describes how to use analytics rules templates.
To use an analytics rule template:
In the Microsoft Sentinel > Analytics > Rule templates page, select a template name, and then select the Create rule button on the details pane to create a new active rule based on that template.
Each template has a list of required data sources. When you open the template, the data sources are automatically checked for availability. If there's an availability issue, the Create rule button may be disabled, or you may see a warning to that effect.
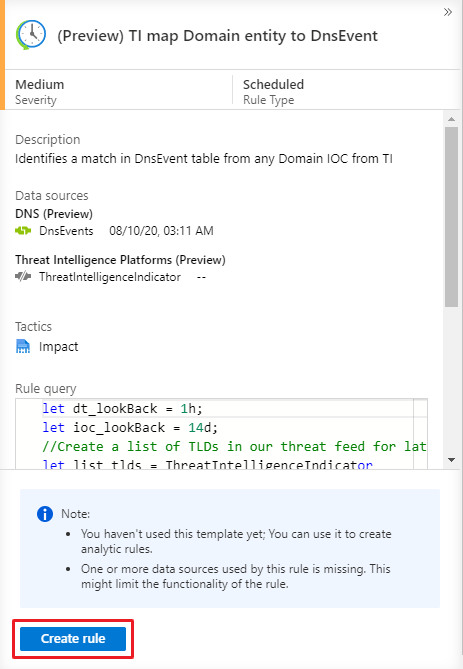
Selecting Create rule opens the rule creation wizard based on the selected template. All the details are autofilled, and with the Scheduled or Microsoft security templates, you can customize the logic and other rule settings to better suit your specific needs. You can repeat this process to create more rules based on the template. After following the steps in the rule creation wizard to the end, you finished creating a rule based on the template. The new rules appear in the Active rules tab.
For more details on how to customize your rules in the rule creation wizard, see Create custom analytics rules to detect threats.
Tip
Make sure that you enable all rules associated with your connected data sources in order to ensure full security coverage for your environment. The most efficient way to enable analytics rules is directly from the data connector page, which lists any related rules. For more information, see Connect data sources.
You can also push rules to Microsoft Sentinel via API and PowerShell, although doing so requires additional effort.
When using API or PowerShell, you must first export the rules to JSON before enabling the rules. API or PowerShell may be helpful when enabling rules in multiple instances of Microsoft Sentinel with identical settings in each instance.
Access permissions for analytics rules
When you create an analytics rule, an access permissions token is applied to the rule and saved along with it. This token ensures that the rule can access the workspace that contains the data queried by the rule, and that this access will be maintained even if the rule's creator loses access to that workspace.
There is one exception to this, however: when a rule is created to access workspaces in other subscriptions or tenants, such as what happens in the case of an MSSP, Microsoft Sentinel takes extra security measures to prevent unauthorized access to customer data. For these kinds of rules, the credentials of the user that created the rule are applied to the rule instead of an independent access token, so that when the user no longer has access to the other subscription or tenant, the rule stops working.
If you operate Microsoft Sentinel in a cross-subscription or cross-tenant scenario, when one of your analysts or engineers loses access to a particular workspace, any rules created by that user stops working. You will get a health monitoring message regarding "insufficient access to resource", and the rule will be auto-disabled after having failed a certain number of times.
Export rules to an ARM template
You can easily export your rule to an Azure Resource Manager (ARM) template if you want to manage and deploy your rules as code. You can also import rules from template files in order to view and edit them in the user interface.
Next steps
To create custom rules, use existing rules as templates or references. Using existing rules as a baseline helps by building out most of the logic before you make any changes needed. For more information, see Create custom analytics rules to detect threats.
To learn how to automate your responses to threats, Set up automated threat responses in Microsoft Sentinel.
To learn how to find more rule templates, see Discover and manage Microsoft Sentinel out-of-the-box content.
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for