Azure Disk Encryption for Windows VMs
Applies to: ✔️ Windows VMs ✔️ Flexible scale sets
Azure Disk Encryption helps protect and safeguard your data to meet your organizational security and compliance commitments. It uses the BitLocker feature of Windows to provide volume encryption for the OS and data disks of Azure virtual machines (VMs), and is integrated with Azure Key Vault to help you control and manage the disk encryption keys and secrets.
Azure Disk Encryption is zone resilient, the same way as Virtual Machines. For details, see Azure Services that support Availability Zones.
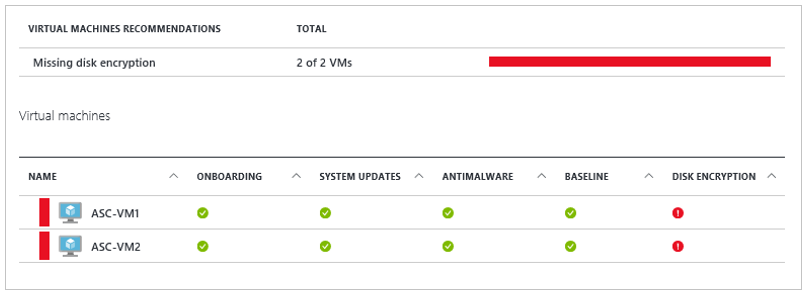
If you use Microsoft Defender for Cloud, you're alerted if you have VMs that aren't encrypted. The alerts show as High Severity and the recommendation is to encrypt these VMs.
Warning
- If you have previously used Azure Disk Encryption with Microsoft Entra ID to encrypt a VM, you must continue use this option to encrypt your VM. See Azure Disk Encryption with Microsoft Entra ID (previous release) for details.
- Certain recommendations might increase data, network, or compute resource usage, resulting in additional license or subscription costs. You must have a valid active Azure subscription to create resources in Azure in the supported regions.
- Do not use BitLocker to manually decrypt a VM or disk that was encrypted through Azure Disk Encryption.
You can learn the fundamentals of Azure Disk Encryption for Windows in just a few minutes with the Create and encrypt a Windows VM with Azure CLI quickstart or the Create and encrypt a Windows VM with Azure PowerShell quickstart.
Supported VMs and operating systems
Supported VMs
Windows VMs are available in a range of sizes. Azure Disk Encryption is supported on Generation 1 and Generation 2 VMs. Azure Disk Encryption is also available for VMs with premium storage.
Azure Disk Encryption is not available on Basic, A-series VMs, or on virtual machines with a less than 2 GB of memory. For more exceptions, see Azure Disk Encryption: Restrictions.
Supported operating systems
- Windows client: Windows 8 and later.
- Windows Server: Windows Server 2008 R2 and later.
- Windows 10 Enterprise multi-session and later.
Note
Windows Server 2022 and Windows 11 do not support an RSA 2048 bit key. For more information, see FAQ: What size should I use for my key encryption key?
Windows Server 2008 R2 requires the .NET Framework 4.5 to be installed for encryption; install it from Windows Update with the optional update Microsoft .NET Framework 4.5.2 for Windows Server 2008 R2 x64-based systems (KB2901983).
Windows Server 2012 R2 Core and Windows Server 2016 Core requires the bdehdcfg component to be installed on the VM for encryption.
Networking requirements
To enable Azure Disk Encryption, the VMs must meet the following network endpoint configuration requirements:
- To get a token to connect to your key vault, the Windows VM must be able to connect to a Microsoft Entra endpoint, [login.microsoftonline.com].
- To write the encryption keys to your key vault, the Windows VM must be able to connect to the key vault endpoint.
- The Windows VM must be able to connect to an Azure storage endpoint that hosts the Azure extension repository and an Azure storage account that hosts the VHD files.
- If your security policy limits access from Azure VMs to the Internet, you can resolve the preceding URI and configure a specific rule to allow outbound connectivity to the IPs. For more information, see Azure Key Vault behind a firewall.
Group Policy requirements
Azure Disk Encryption uses the BitLocker external key protector for Windows VMs. For domain joined VMs, don't push any group policies that enforce TPM protectors. For information about the group policy for "Allow BitLocker without a compatible TPM," see BitLocker Group Policy Reference.
BitLocker policy on domain joined virtual machines with custom group policy must include the following setting: Configure user storage of BitLocker recovery information -> Allow 256-bit recovery key. Azure Disk Encryption will fail when custom group policy settings for BitLocker are incompatible. On machines that didn't have the correct policy setting, apply the new policy, and force the new policy to update (gpupdate.exe /force). Restarting may be required.
Microsoft BitLocker Administration and Monitoring (MBAM) group policy features aren't compatible with Azure Disk Encryption.
Warning
Azure Disk Encryption does not store recovery keys. If the Interactive logon: Machine account lockout threshold security setting is enabled, machines can only be recovered by providing a recovery key via the serial console. Instructions for ensuring the appropriate recovery policies are enabled can be found in the Bitlocker recovery guide plan.
Azure Disk Encryption will fail if domain level group policy blocks the AES-CBC algorithm, which is used by BitLocker.
Encryption key storage requirements
Azure Disk Encryption requires an Azure Key Vault to control and manage disk encryption keys and secrets. Your key vault and VMs must reside in the same Azure region and subscription.
For details, see Creating and configuring a key vault for Azure Disk Encryption.
Terminology
The following table defines some of the common terms used in Azure disk encryption documentation:
| Terminology | Definition |
|---|---|
| Azure Key Vault | Key Vault is a cryptographic, key management service that's based on Federal Information Processing Standards (FIPS) validated hardware security modules. These standards help to safeguard your cryptographic keys and sensitive secrets. For more information, see the Azure Key Vault documentation and Creating and configuring a key vault for Azure Disk Encryption. |
| Azure CLI | The Azure CLI is optimized for managing and administering Azure resources from the command line. |
| BitLocker | BitLocker is an industry-recognized Windows volume encryption technology that's used to enable disk encryption on Windows VMs. |
| Key encryption key (KEK) | The asymmetric key (RSA 2048) that you can use to protect or wrap the secret. You can provide a hardware security module (HSM)-protected key or software-protected key. For more information, see the Azure Key Vault documentation and Creating and configuring a key vault for Azure Disk Encryption. |
| PowerShell cmdlets | For more information, see Azure PowerShell cmdlets. |
Next steps
- Quickstart - Create and encrypt a Windows VM with Azure CLI
- Quickstart - Create and encrypt a Windows VM with Azure PowerShell
- Azure Disk Encryption scenarios on Windows VMs
- Azure Disk Encryption prerequisites CLI script
- Azure Disk Encryption prerequisites PowerShell script
- Creating and configuring a key vault for Azure Disk Encryption
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for