Resource logging for a network security group
A network security group (NSG) includes rules that allow or deny traffic to a virtual network subnet, network interface, or both.
When you enable logging for an NSG, you can gather the following types of resource log information:
- Event: Entries are logged for which NSG rules are applied to virtual machines, based on MAC address.
- Rule counter: Contains entries for how many times each NSG rule is applied to allow or deny traffic. The status for these rules is collected every 300 seconds.
Resource logs are only available for NSGs deployed through the Azure Resource Manager deployment model. You can't enable resource logging for NSGs deployed through the classic deployment model. For more information, see Understand deployment models.
Resource logging is enabled separately for each NSG for which to collect diagnostic data. If you're interested in activity, or operational, logs instead, see Overview of Azure platform logs. If you're interested in IP traffic flowing through NSGs, see Flow logs for network security groups.
Enable logging
You can use the Azure portal, Azure PowerShell, or the Azure CLI to enable resource logging.
Azure portal
Sign in to the Azure portal.
In the search box at the top of the Azure portal, enter network security groups. Select Network security groups in the search results.
Select the NSG for which to enable logging.
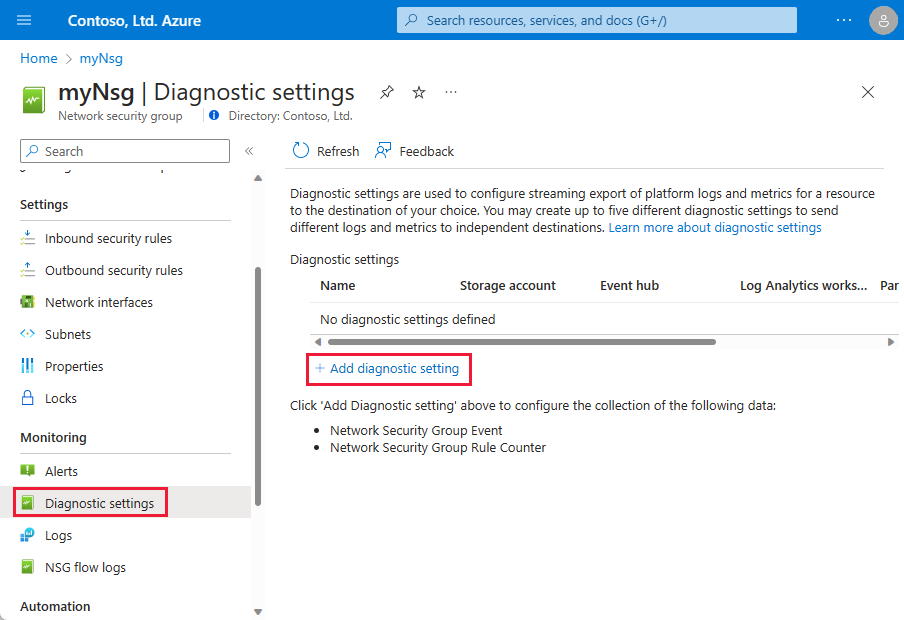
Under Monitoring, select Diagnostic settings, and then select Add diagnostic setting:
In Diagnostic setting, enter a name, such as myNsgDiagnostic.
For Logs, select allLogs or select individual categories of logs. For more information about each category, see Log categories.
Under Destination details, select one or more destinations:
- Send to Log Analytics workspace
- Archive to a storage account
- Stream to an event hub
- Send to partner solution
For more information, see Log destinations.
Select Save.
View and analyze logs. For more information, see View and analyze logs.
Azure PowerShell
Note
We recommend that you use the Azure Az PowerShell module to interact with Azure. See Install Azure PowerShell to get started. To learn how to migrate to the Az PowerShell module, see Migrate Azure PowerShell from AzureRM to Az.
You can run the commands that in this section in the Azure Cloud Shell, or by running PowerShell from your computer. The Azure Cloud Shell is a free interactive shell. It has common Azure tools preinstalled and configured to use with your account.
If you run PowerShell from your computer, you need the Azure PowerShell module, version 1.0.0 or later. Run Get-Module -ListAvailable Az to find the installed version. If you need to upgrade, see Install Azure PowerShell module. If you run PowerShell locally, you also need to run the Connect-AzAccount cmdlet to sign in to Azure with an account that has the necessary permissions.
To enable resource logging, you need the ID of an existing NSG. If you don't have an existing NSG, create one by using the New-AzNetworkSecurityGroup cmdlet.
Get the network security group that you want to enable resource logging for by using the Get-AzNetworkSecurityGroup cmdlet. Store the NSG in a variable for later use. For example, to retrieve an NSG named myNsg that exists in a resource group named myResourceGroup, enter the following command:
$Nsg=Get-AzNetworkSecurityGroup `
-Name myNsg `
-ResourceGroupName myResourceGroup
You can write resource logs to different destination types. For more information, see Log destinations. In this article, logs are sent to a Log Analytics workspace destination. If you don't have an existing workspace, you can create one by using the New-AzOperationalInsightsWorkspace cmdlet.
Retrieve an existing Log Analytics workspace with the Get-AzOperationalInsightsWorkspace cmdlet. For example, to get and store an existing workspace named myWorkspace in a resource group named myWorkspaces, enter the following command:
$Oms=Get-AzOperationalInsightsWorkspace `
-ResourceGroupName myWorkspaces `
-Name myWorkspace
There are two categories of logging that you can enable. For more information, see Log categories. Enable resource logging for the NSG with the New-AzDiagnosticSetting cmdlet. The following example logs both event and counter category data to the workspace for an NSG. It uses the IDs for the NSG and workspace that you got with the previous commands:
New-AzDiagnosticSetting `
-Name myDiagnosticSetting `
-ResourceId $Nsg.Id `
-WorkspaceId $Oms.ResourceId
If you want to log to a different destination than a Log Analytics workspace, use an appropriate parameter in the command. For more information, see Azure resource logs.
For more information about settings, see New-AzDiagnosticSetting.
View and analyze logs. For more information, see View and analyze logs.
Azure CLI
You can run the commands in this section in the Azure Cloud Shell, or by running the Azure CLI from your computer. The Azure Cloud Shell is a free interactive shell. It has common Azure tools preinstalled and configured to use with your account.
If you run the CLI from your computer, you need version 2.0.38 or later. Run az --version on your computer, to find the installed version. If you need to upgrade, see Install Azure CLI. If you run the CLI locally, you also need to run az login to sign in to Azure with an account that has the necessary permissions.
To enable resource logging, you need the ID of an existing NSG. If you don't have an existing NSG, create one by using az network nsg create.
Get and store the network security group that you want to enable resource logging for with az network nsg show. For example, to retrieve an NSG named myNsg that exists in a resource group named myResourceGroup, enter the following command:
nsgId=$(az network nsg show \
--name myNsg \
--resource-group myResourceGroup \
--query id \
--output tsv)
You can write resource logs to different destination types. For more information, see Log destinations. In this article, logs are sent to a Log Analytics workspace destination, as an example. For more information, see Log categories.
Enable resource logging for the NSG with az monitor diagnostic-settings create. The following example logs both event and counter category data to an existing workspace named myWorkspace, which exists in a resource group named myWorkspaces. It uses the ID of the NSG that you saved by using the previous command.
az monitor diagnostic-settings create \
--name myNsgDiagnostics \
--resource $nsgId \
--logs '[ { "category": "NetworkSecurityGroupEvent", "enabled": true, "retentionPolicy": { "days": 30, "enabled": true } }, { "category": "NetworkSecurityGroupRuleCounter", "enabled": true, "retentionPolicy": { "days": 30, "enabled": true } } ]' \
--workspace myWorkspace \
--resource-group myWorkspaces
If you don't have an existing workspace, create one using the Azure portal or Azure PowerShell. There are two categories of logging for which you can enable logs.
If you only want to log data for one category or the other, remove the category you don't want to log data for in the previous command. If you want to log to a different destination than a Log Analytics workspace, use an appropriate parameter. For more information, see Azure resource logs.
View and analyze logs. For more information, see View and analyze logs.
Log destinations
You can send diagnostics data to the following options:
Log categories
JSON-formatted data is written for the following log categories: event and rule counter.
Event
The event log contains information about which NSG rules are applied to virtual machines, based on MAC address. The following data is logged for each event. In the following example, the data is logged for a virtual machine with the IP address 192.168.1.4 and a MAC address of 00-0D-3A-92-6A-7C:
{
"time": "[DATE-TIME]",
"systemId": "[ID]",
"category": "NetworkSecurityGroupEvent",
"resourceId": "/SUBSCRIPTIONS/[SUBSCRIPTION-ID]/RESOURCEGROUPS/[RESOURCE-GROUP-NAME]/PROVIDERS/MICROSOFT.NETWORK/NETWORKSECURITYGROUPS/[NSG-NAME]",
"operationName": "NetworkSecurityGroupEvents",
"properties": {
"vnetResourceGuid":"[ID]",
"subnetPrefix":"192.168.1.0/24",
"macAddress":"00-0D-3A-92-6A-7C",
"primaryIPv4Address":"192.168.1.4",
"ruleName":"[SECURITY-RULE-NAME]",
"direction":"[DIRECTION-SPECIFIED-IN-RULE]",
"priority":"[PRIORITY-SPECIFIED-IN-RULE]",
"type":"[ALLOW-OR-DENY-AS-SPECIFIED-IN-RULE]",
"conditions":{
"protocols":"[PROTOCOLS-SPECIFIED-IN-RULE]",
"destinationPortRange":"[PORT-RANGE-SPECIFIED-IN-RULE]",
"sourcePortRange":"[PORT-RANGE-SPECIFIED-IN-RULE]",
"sourceIP":"[SOURCE-IP-OR-RANGE-SPECIFIED-IN-RULE]",
"destinationIP":"[DESTINATION-IP-OR-RANGE-SPECIFIED-IN-RULE]"
}
}
}
Rule counter
The rule counter log contains information about each rule applied to resources. The following example data is logged each time a rule is applied. In the following example, the data is logged for a virtual machine with the IP address 192.168.1.4 and a MAC address of 00-0D-3A-92-6A-7C:
{
"time": "[DATE-TIME]",
"systemId": "[ID]",
"category": "NetworkSecurityGroupRuleCounter",
"resourceId": "/SUBSCRIPTIONS/[SUBSCRIPTION ID]/RESOURCEGROUPS/[RESOURCE-GROUP-NAME]/PROVIDERS/MICROSOFT.NETWORK/NETWORKSECURITYGROUPS/[NSG-NAME]",
"operationName": "NetworkSecurityGroupCounters",
"properties": {
"vnetResourceGuid":"[ID]",
"subnetPrefix":"192.168.1.0/24",
"macAddress":"00-0D-3A-92-6A-7C",
"primaryIPv4Address":"192.168.1.4",
"ruleName":"[SECURITY-RULE-NAME]",
"direction":"[DIRECTION-SPECIFIED-IN-RULE]",
"type":"[ALLOW-OR-DENY-AS-SPECIFIED-IN-RULE]",
"matchedConnections":125
}
}
Note
The source IP address for the communication is not logged. You can enable NSG flow logging for an NSG, which logs all of the rule counter information and the source IP address that initiated the communication. NSG flow log data is written to an Azure Storage account. You can analyze the data with the traffic analytics capability of Azure Network Watcher.
View and analyze logs
If you send diagnostics data to:
Azure Monitor logs: You can use the network security group analytics solution for enhanced insights. The solution provides visualizations for NSG rules that allow or deny traffic, per MAC address, of the network interface in a virtual machine.
Azure Storage account: Data is written to a PT1H.json file. You can find the:
- Event log that is in the following path: insights-logs-networksecuritygroupevent/resourceId=/SUBSCRIPTIONS/[ID]/RESOURCEGROUPS/[RESOURCE-GROUP-NAME-FOR-NSG]/PROVIDERS/MICROSOFT.NETWORK/NETWORKSECURITYGROUPS/[NSG NAME]/y=[YEAR]/m=[MONTH/d=[DAY]/h=[HOUR]/m=[MINUTE]
- Rule counter log that is in the following path: insights-logs-networksecuritygrouprulecounter/resourceId=/SUBSCRIPTIONS/[ID]/RESOURCEGROUPS/[RESOURCE-GROUP-NAME-FOR-NSG]/PROVIDERS/MICROSOFT.NETWORK/NETWORKSECURITYGROUPS/[NSG NAME]/y=[YEAR]/m=[MONTH/d=[DAY]/h=[HOUR]/m=[MINUTE]
To learn how to view resource log data, see Azure platform logs overview.
Next steps
For more information about Activity logging, see Overview of Azure platform logs.
Activity logging is enabled by default for NSGs created through either Azure deployment model. To determine which operations were completed on NSGs in the activity log, look for entries that contain the following resource types:
- Microsoft.ClassicNetwork/networkSecurityGroups
- Microsoft.ClassicNetwork/networkSecurityGroups/securityRules
- Microsoft.Network/networkSecurityGroups
- Microsoft.Network/networkSecurityGroups/securityRules
To learn how to log diagnostic information, see Log network traffic to and from a virtual machine using the Azure portal.
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for