Register an application
Important
In June 2022, we introduced multi-factor authentication as a requirement for Bing Ads. You may still need to make a code change in order to become compliant with this requirement. Microsoft Advertising is performing technical enforcement checks in early October.
This blog post outlines the steps you should take to ensure compliance.
For more information, see the multi-factor authentication requirement guide.
Before your application can authenticate Microsoft Advertising users, you must register your application in an Azure Active Directory (AAD) tenant and get the corresponding client ID and client secret.
Navigate to the Microsoft identity platform for developers in the Azure portal - App registrations page. You can log in using or a Work or School Account. Note: You can no longer log in using a personal Microsoft account.
Select New registration.
When the Register an application page appears, enter your application's registration information:
- In the Name section, enter a meaningful application name that will be displayed to users of the app, for example
My browserless client. - In the Supported account types section, select Accounts in any organizational directory and personal Microsoft accounts.

Important
You must select Accounts in any organizational directory and personal Microsoft accounts during the initial app registration. This setting cannot be updated later in the portal unless you modify the application manifest e.g.,
"signInAudience": "AzureADandPersonalMicrosoftAccount".- In the Name section, enter a meaningful application name that will be displayed to users of the app, for example
Select Register to create the application.
On the app Overview page, find the Application (client) ID value and record it for later. You will use it as the
client_idwhen you request user consent and get an access token.Select the Add a Redirect URI link and then you should see the Redirect URIs page.
- For web applications, provide the base URL of your application. For example, http://localhost:31544 might be the URL for a web application running on your local machine. Users would use this URL to sign into a web client application.
- For public applications, locate the Suggested Redirect URIs for public clients (mobile, desktop) section. Select the https://login.microsoftonline.com/common/oauth2/nativeclient URI.
Important
Clients running apps on services that span regions and devices such as Microsoft Azure should register a web application with client secret. You can get a refresh token on one device and refresh it on another so long as you have the same client ID and client secret. If you register a public application without a client secret, then you cannot use a refresh token across devices. A confidential token is bound to the client secret.
For web applications, select Certificates & secrets under Manage. Select the New client secret button. Enter a value in Description, select any option for Expires and choose Add. Copy the client secret value before leaving the page. You will use it later as the
client_secretto get an access token.
Application behavior
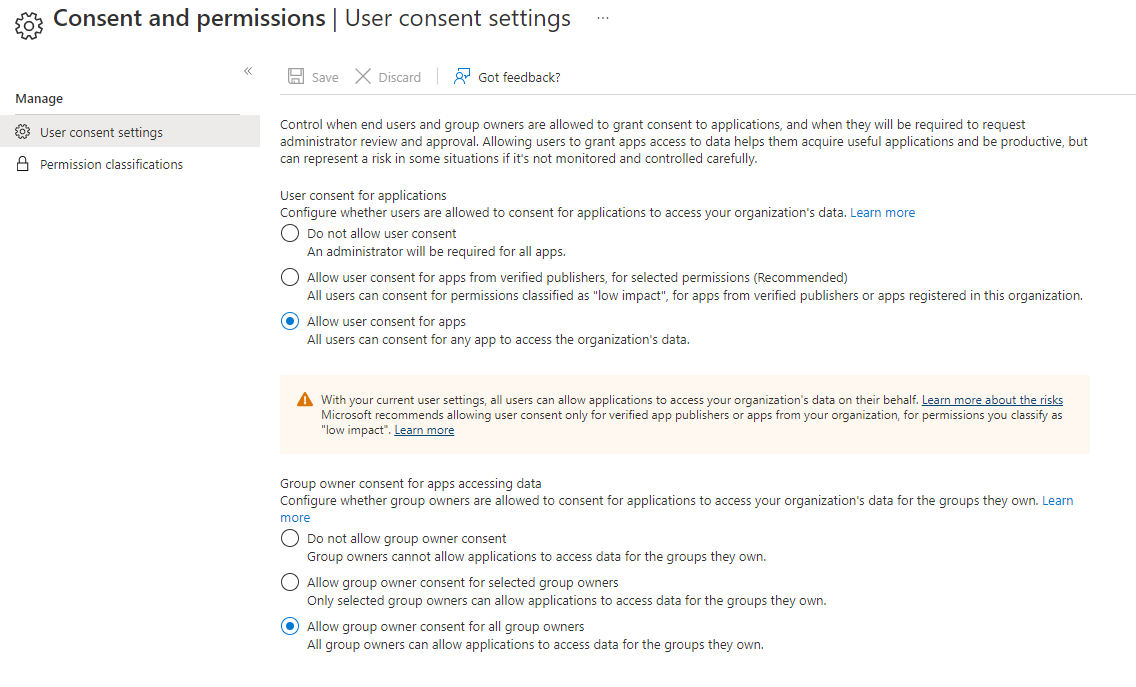
- Registered application behavior is determined by how your Azure AAD tenant has been set up and how users can provide the consent for any app during authentication process. Your Azure AAD tenant administrator can review user consent settings here. https://learn.microsoft.com/azure/active-directory/manage-apps/configure-user-consent?pivots=portal#configure-user-consent-settings
- If you are trying to authenticate but you are getting AADSTS650052 this means your Azure AAD tenant administrator has set up user consent for application with first option from screenshot below Do not allow user consent and this prevents you from authenticating using AAD application.
- To resolve AADSTS650052 error, please follow the setps outlined here
Important
These settings are only accessible to your Azure AAD tenant administrator
Next steps
See Also
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for