Tutorial: Gathering vulnerability intelligence
Important
On June 30, 2024, The Microsoft Defender Threat Intelligence (Defender TI) standalone portal (https://ti.defender.microsoft.com) will be retired and will no longer be accessible. Customers can continue using Defender TI in the Microsoft Defender portal or with Microsoft Copilot for Security. Learn more
This tutorial walks you through how to perform several types of indicator searches to gather vulnerability intelligence using Microsoft Defender Threat Intelligence (Defender TI) in the Microsoft Defender portal.
Prerequisites
A Microsoft Entra ID or personal Microsoft account. Sign in or create an account
A Defender TI Premium license.
Note
Users without a Defender TI Premium license can still access our free Defender TI offering.
Disclaimer
Defender TI might include live, real-time observations and threat indicators, including malicious infrastructure and adversary-threat tooling. Any IP address and domain searches within Defender TI are safe to search. Microsoft shares online resources (for example, IP addresses, domain names) that are considered real threats posing a clear and present danger. We ask that you use their best judgment and minimize unnecessary risk while interacting with malicious systems when performing the following tutorial. Microsoft minimizes risks by defanging malicious IP addresses, hosts, and domains.
Before you begin
As the disclaimer states previously, suspicious and malicious indicators are defanged for your safety. Remove any brackets from IP addresses, domains, and hosts when searching in Defender TI. Don't search these indicators directly in your browser.
Open Defender TI in the Microsoft Defender portal
- Access the Defender portal and complete the Microsoft authentication process. Learn more about the Defender portal
- Navigate to Threat intelligence > Intel explorer.
Learn about Intel explorer home page features
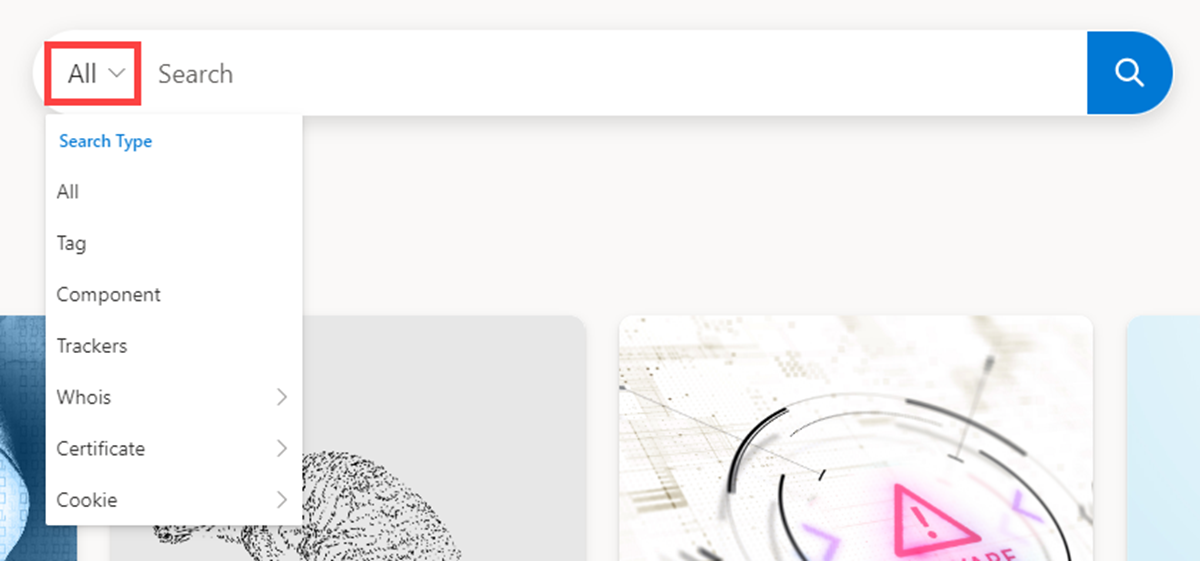
Review the Intel explorer search bar options by selecting its drop-down menu.
Scroll down and review the featured and recent articles in their respective sections. Learn more about Defender TI articles
Perform indicator searches and gather vulnerability intelligence
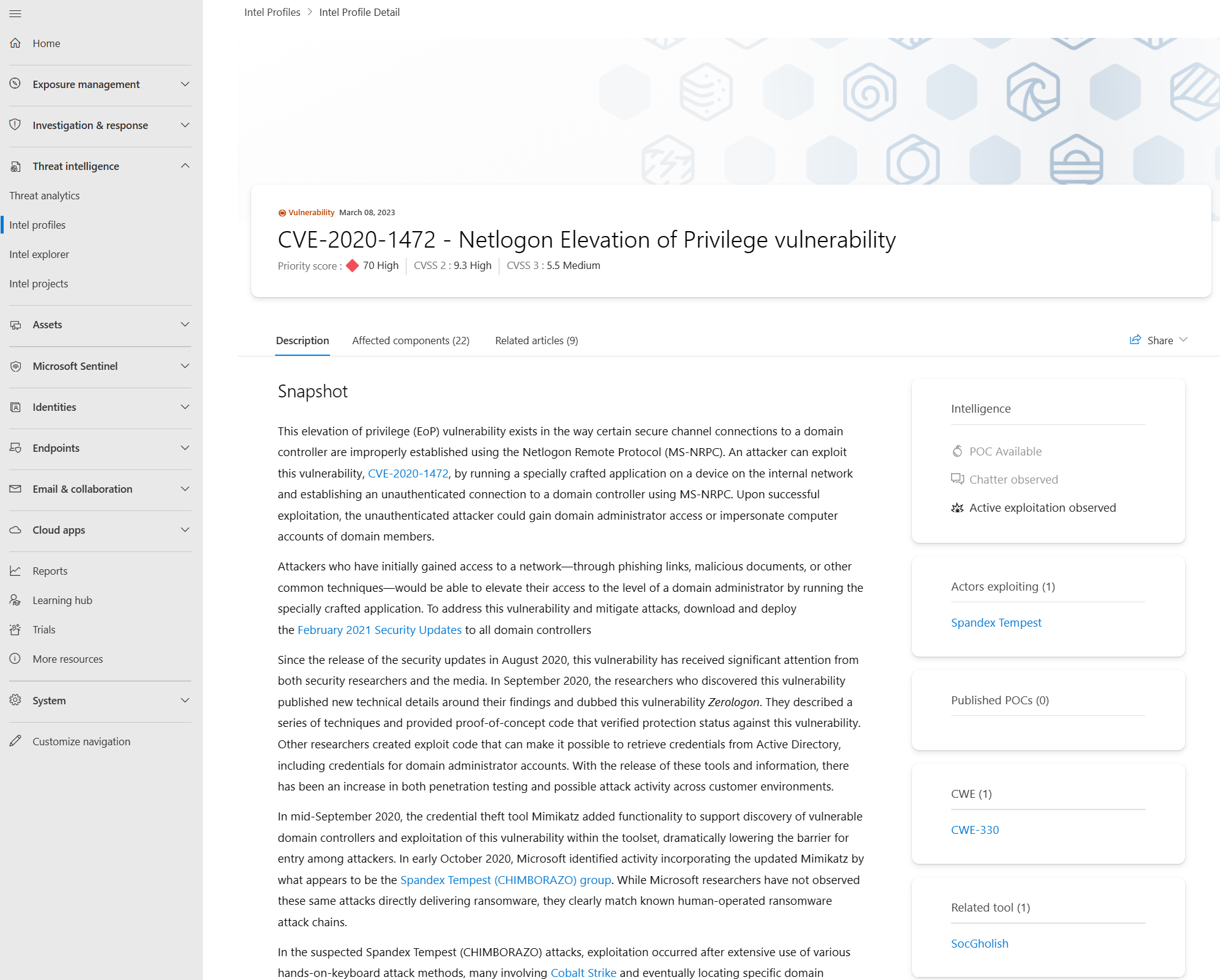
Search CVE-2020-1472 in the Intel explorer search bar, the select and review the associated Intel profile CVE-2020-1472 - Netlogon Elevation of Privilege vulnerability.
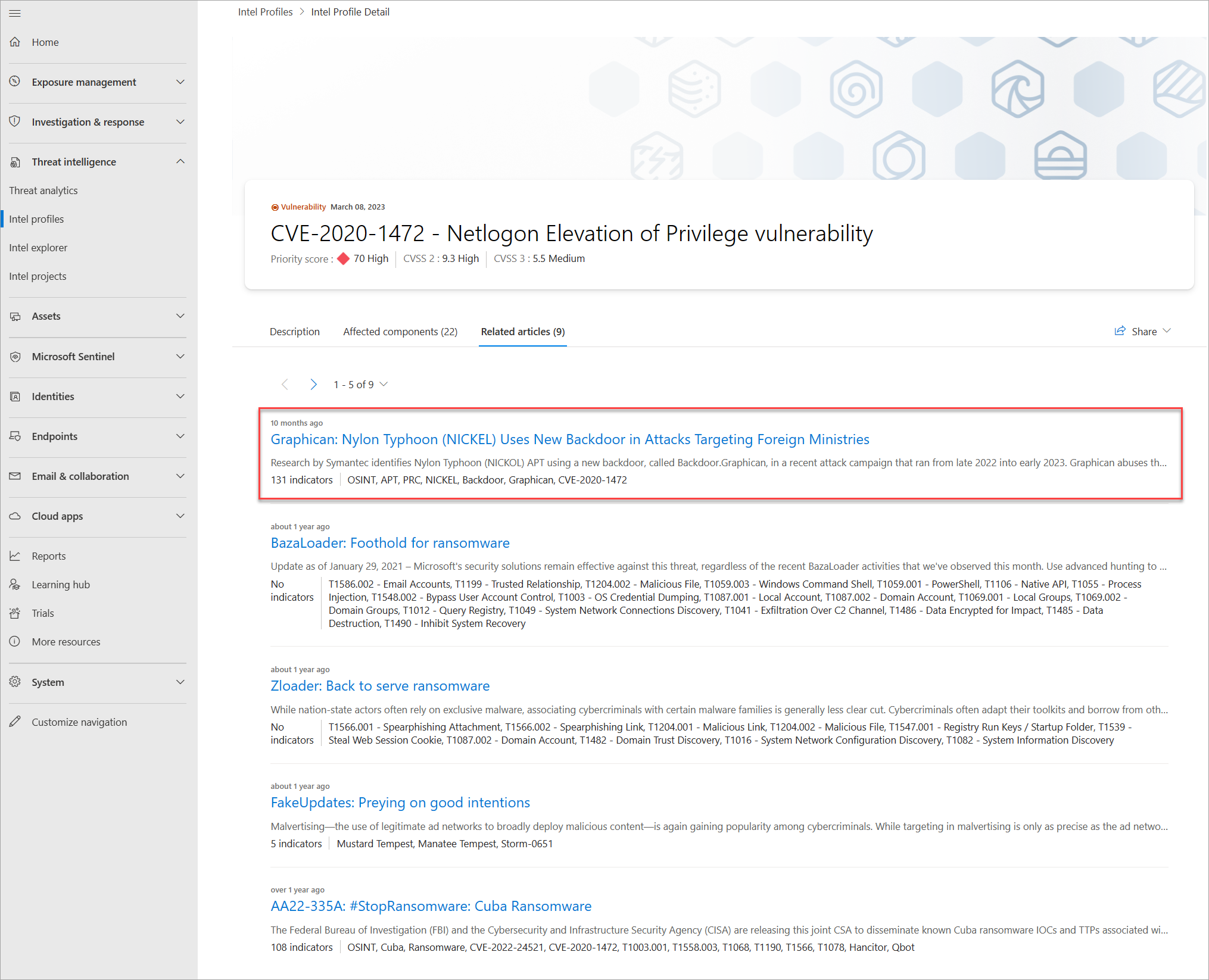
Select the profile's Related articles tab then select the article Graphican: Nylon Typhoon (NICKEL) Uses New Backdoor in Attacks Targeting Foreign Ministries.
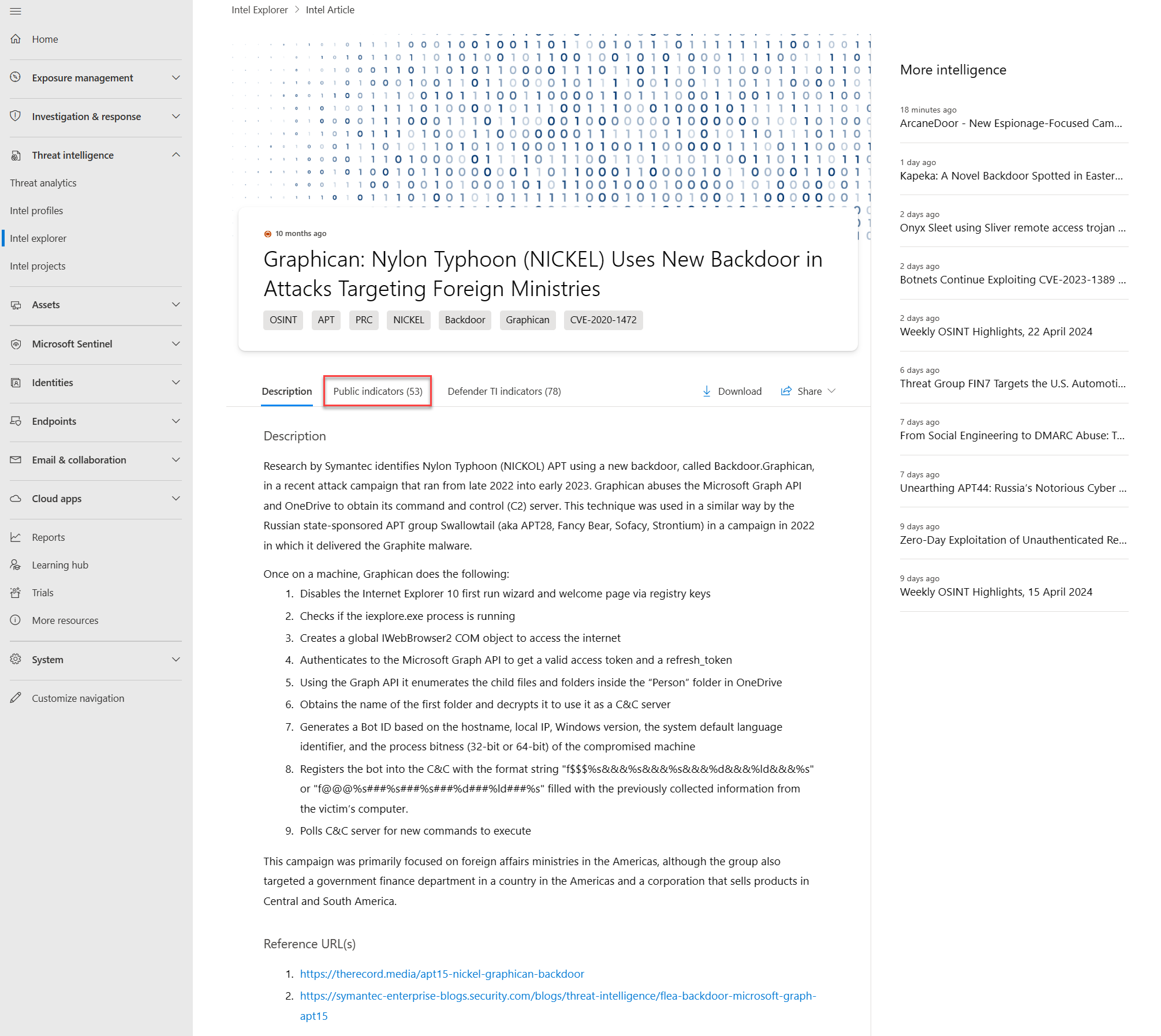
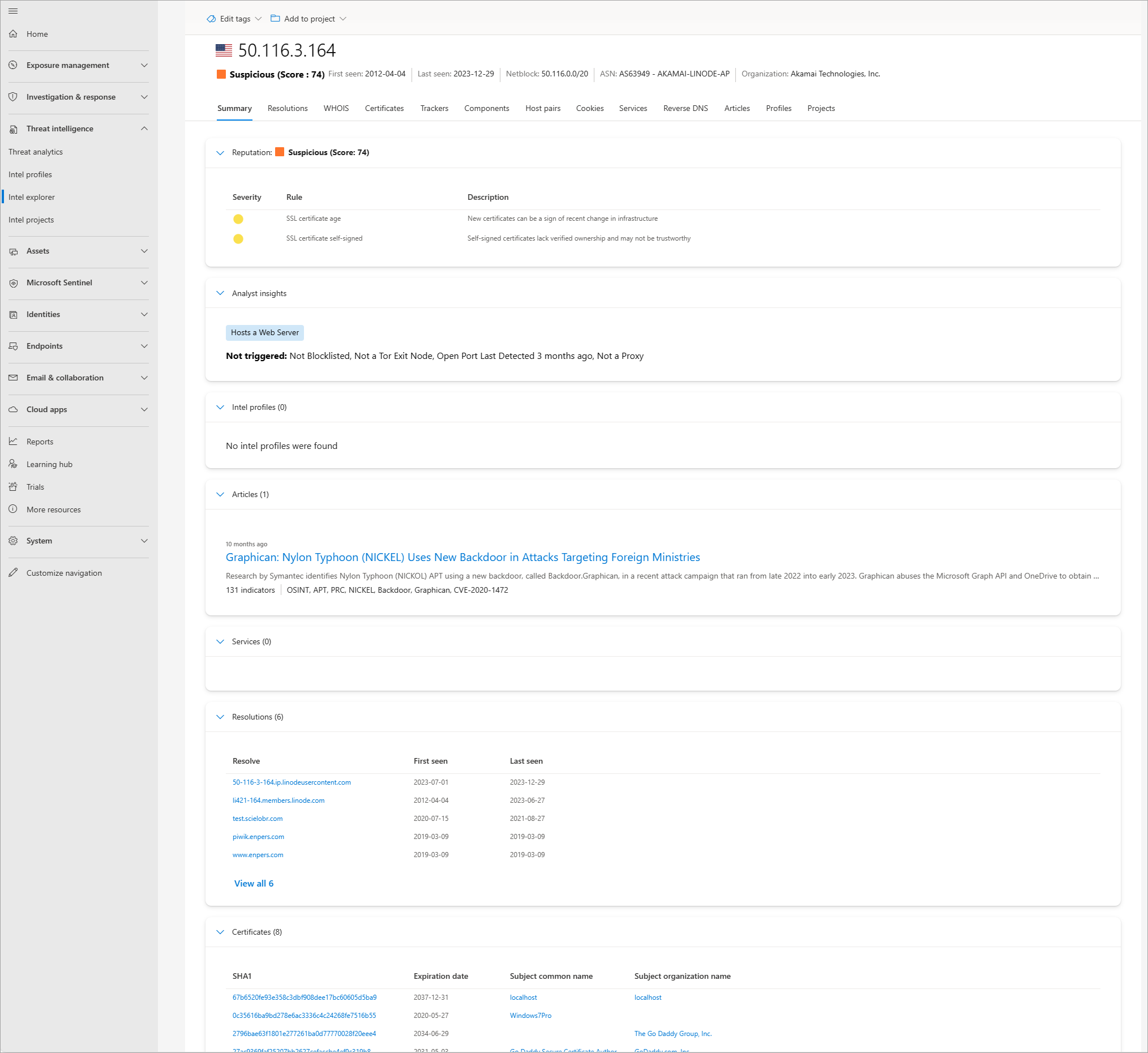
Select this newly opened article's Public indicators. You should see the IP address 50.116.3[.]164 among the listed indicators.
Navigate back to the Intel explorer search bar and search 50.116.3[.]164.
Review the following results in the Summary tab:
- Reputation
- Analyst insights
- Articles
- Services
- Resolutions
- Certificates
- Projects
You can also select and review the information in their respective tabs.
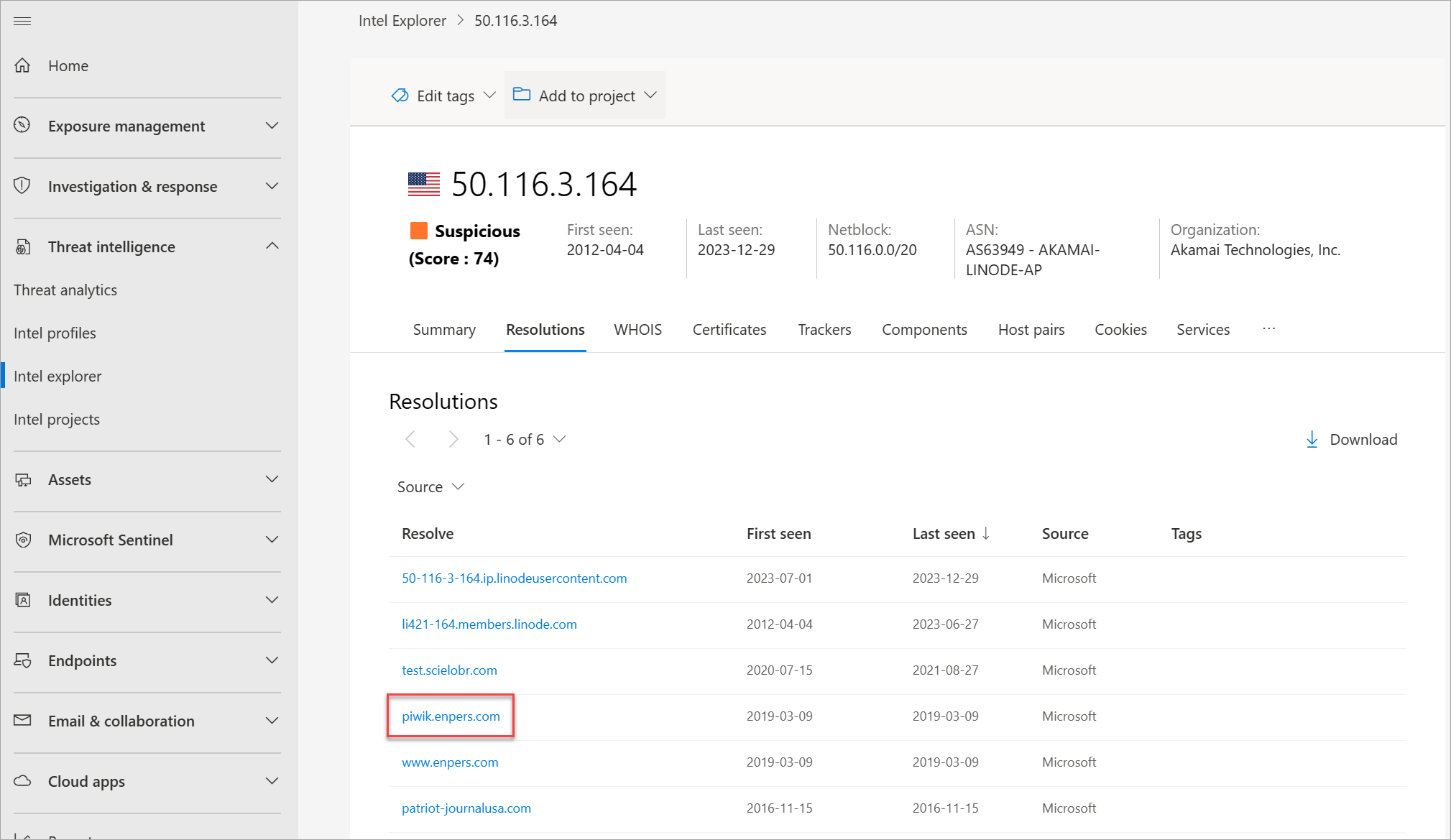
Select the Resolutions tab then select piwik.enpers[.]com.
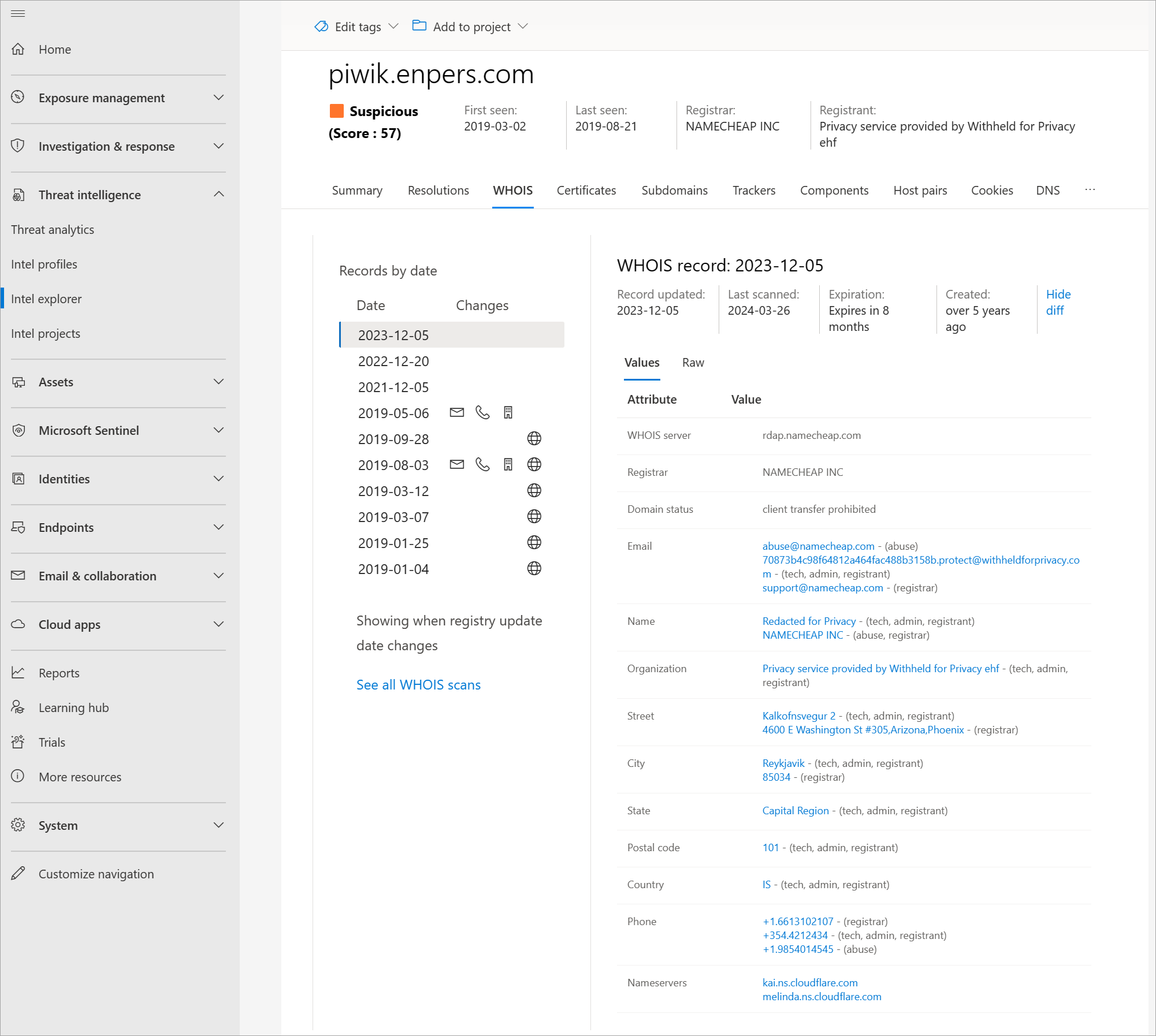
Review this domain's resolutions, WHOIS, certificates, subdomains, trackers, components, cookies, DNS, and reverse DNS data sets.
Perform the respective artifact searches from the previous steps. You could reference and use the different search options in Intel explorer search bar dropdown menu.
Clean up resources
There are no resources to clean up in this section.
See also
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for