Understand and use attack surface reduction capabilities
Applies to:
- Microsoft Defender XDR
- Microsoft Defender for Endpoint Plan 1
- Microsoft Defender for Endpoint Plan 2
- Microsoft Defender Antivirus
Platforms
- Windows
Tip
Want to experience Microsoft Defender for Endpoint? Sign up for a free trial.
Attack surfaces are all the places where your organization is vulnerable to cyberthreats and attacks. Defender for Endpoint includes several capabilities to help reduce your attack surfaces. Watch the following video to learn more about attack surface reduction.
Configure attack surface reduction capabilities
To configure attack surface reduction in your environment, follow these steps:
Enable application control.
Review base policies in Windows. See Example Base Policies.
Refer to Deploying Windows Defender Application Control (WDAC) policies.
Enable removable storage protection.
Enable Web protection.
Set up your network firewall.
Get an overview of Windows Firewall with advanced security.
Use the Windows Firewall design guide to decide how you want to design your firewall policies.
Use the Windows Firewall deployment guide to set up your organization's firewall with advanced security.
Tip
In most cases, when you configure attack surface reduction capabilities, you can choose from among several methods:
- Microsoft Intune
- Microsoft Configuration Manager
- Group Policy
- PowerShell cmdlets
Test attack surface reduction in Microsoft Defender for Endpoint
As part of your organization's security team, you can configure attack surface reduction capabilities to run in audit mode to see how they work. You can enable the following attack surface reduction security features in audit mode:
- Attack surface reduction rules
- Exploit protection
- Network protection
- Controlled folder access
- Device control
Audit mode lets you see a record of what would have happened if the feature were enabled.
You can enable audit mode when testing how the features work. Enabling audit mode only for testing helps to prevent audit mode from affecting your line-of-business apps. You can also get an idea of how many suspicious file modification attempts occur over a certain period of time.
The features don't block or prevent apps, scripts, or files from being modified. However, the Windows Event Log records events as if the features were fully enabled. With audit mode, you can review the event log to see what effect the feature would have had if it was enabled.
To find the audited entries, go to Applications and Services > Microsoft > Windows > Windows Defender > Operational.
Use Defender for Endpoint to get greater details for each event. These details are especially helpful for investigating attack surface reduction rules. Using the Defender for Endpoint console lets you investigate issues as part of the alert timeline and investigation scenarios.
You can enable audit mode using Group Policy, PowerShell, and configuration service providers (CSPs).
| Audit options | How to enable audit mode | How to view events |
|---|---|---|
| Audit applies to all events | Enable controlled folder access | Controlled folder access events |
| Audit applies to individual rules | Step 1: Test attack surface reduction rules using Audit mode | Step 2: Understand the Attack surface reduction rules reporting page |
| Audit applies to all events | Enable network protection | Network protection events |
| Audit applies to individual mitigations | Enable exploit protection | Exploit protection events |
For example, you can test attack surface reduction rules in audit mode before you enable them in block mode. Attack surface reduction rules are predefined to harden common, known attack surfaces. There are several methods you can use to implement attack surface reduction rules. The preferred method is documented in the following attack surface reduction rules deployment articles:
- Attack surface reduction rules deployment overview
- Plan attack surface reduction rules deployment
- Test attack surface reduction rules
- Enable attack surface reduction rules
- Operationalize attack surface reduction rules
View attack surface reduction events
Review attack surface reduction events in Event Viewer to monitor what rules or settings are working. You can also determine if any settings are too "noisy" or impacting your day to day workflow.
Reviewing events is handy when you're evaluating the features. You can enable audit mode for features or settings, and then review what would have happened if they were fully enabled.
This section lists all the events, their associated feature or setting, and describes how to create custom views to filter to specific events.
Get detailed reporting into events, blocks, and warnings as part of Windows Security if you have an E5 subscription and use Microsoft Defender for Endpoint.
Use custom views to review attack surface reduction capabilities
Create custom views in the Windows Event Viewer to only see events for specific capabilities and settings. The easiest way is to import a custom view as an XML file. You can copy the XML directly from this page.
You can also manually navigate to the event area that corresponds to the feature.
Import an existing XML custom view
Create an empty .txt file and copy the XML for the custom view you want to use into the .txt file. Do this for each of the custom views you want to use. Rename the files as follows (ensure you change the type from .txt to .xml):
- Controlled folder access events custom view: cfa-events.xml
- Exploit protection events custom view: ep-events.xml
- Attack surface reduction events custom view: asr-events.xml
- Network/ protection events custom view: np-events.xml
Type event viewer in the Start menu and open Event Viewer.
Select Action > Import Custom View...
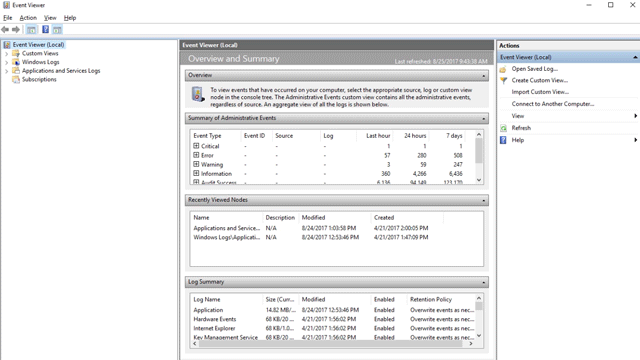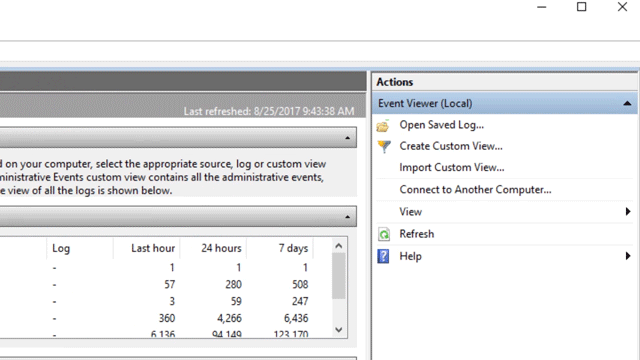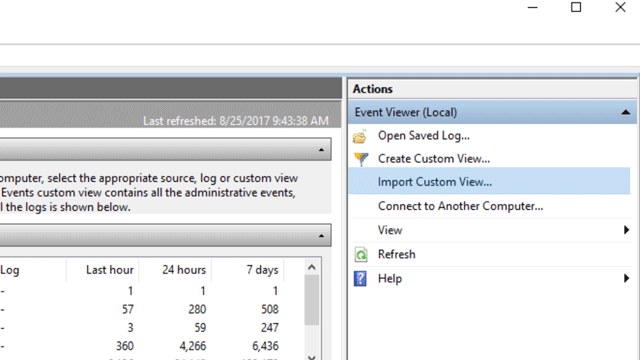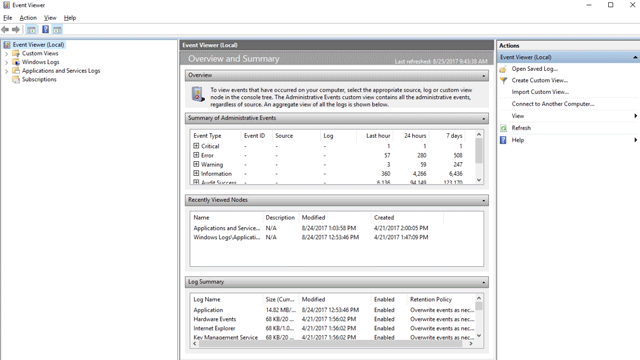
Navigate to where you extracted the XML file for the custom view you want and select it.
Select Open.
It creates a custom view that filters to only show the events related to that feature.
Copy the XML directly
Type event viewer in the Start menu and open the Windows Event Viewer.
On the left panel, under Actions, select Create Custom View...
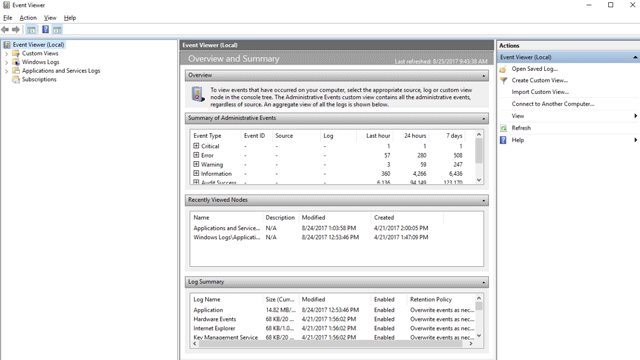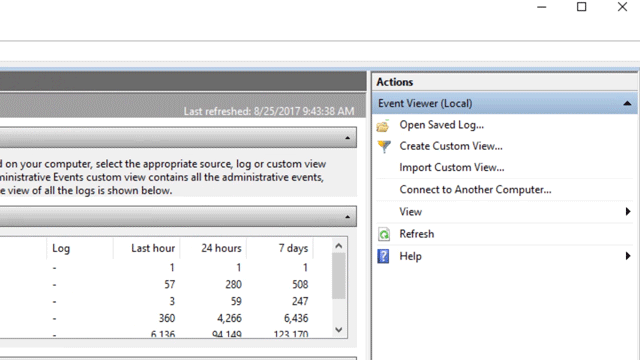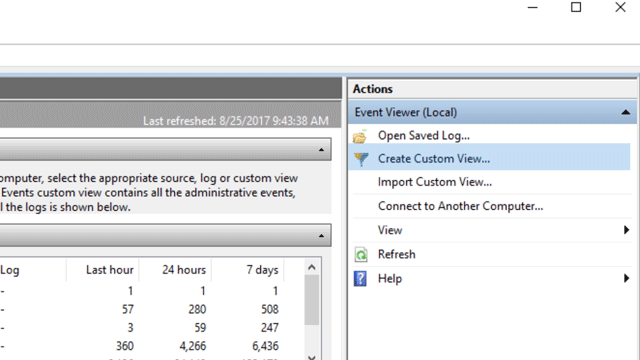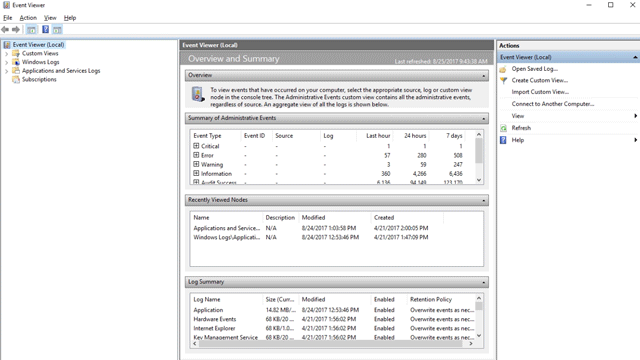
Go to the XML tab and select Edit query manually. You see a warning that you can't edit the query using the Filter tab if you use the XML option. Select Yes.
Paste the XML code for the feature you want to filter events from into the XML section.
Select OK. Specify a name for your filter. This action creates a custom view that filters to only show the events related to that feature.
XML for attack surface reduction rule events
<QueryList>
<Query Id="0" Path="Microsoft-Windows-Windows Defender/Operational">
<Select Path="Microsoft-Windows-Windows Defender/Operational">*[System[(EventID=1121 or EventID=1122 or EventID=5007)]]</Select>
<Select Path="Microsoft-Windows-Windows Defender/WHC">*[System[(EventID=1121 or EventID=1122 or EventID=5007)]]</Select>
</Query>
</QueryList>
XML for controlled folder access events
<QueryList>
<Query Id="0" Path="Microsoft-Windows-Windows Defender/Operational">
<Select Path="Microsoft-Windows-Windows Defender/Operational">*[System[(EventID=1123 or EventID=1124 or EventID=5007)]]</Select>
<Select Path="Microsoft-Windows-Windows Defender/WHC">*[System[(EventID=1123 or EventID=1124 or EventID=5007)]]</Select>
</Query>
</QueryList>
XML for exploit protection events
<QueryList>
<Query Id="0" Path="Microsoft-Windows-Security-Mitigations/KernelMode">
<Select Path="Microsoft-Windows-Security-Mitigations/KernelMode">*[System[Provider[@Name='Microsoft-Windows-Security-Mitigations' or @Name='Microsoft-Windows-WER-Diag' or @Name='Microsoft-Windows-Win32k' or @Name='Win32k'] and ( (EventID >= 1 and EventID <= 24) or EventID=5 or EventID=260)]]</Select>
<Select Path="Microsoft-Windows-Win32k/Concurrency">*[System[Provider[@Name='Microsoft-Windows-Security-Mitigations' or @Name='Microsoft-Windows-WER-Diag' or @Name='Microsoft-Windows-Win32k' or @Name='Win32k'] and ( (EventID >= 1 and EventID <= 24) or EventID=5 or EventID=260)]]</Select>
<Select Path="Microsoft-Windows-Win32k/Contention">*[System[Provider[@Name='Microsoft-Windows-Security-Mitigations' or @Name='Microsoft-Windows-WER-Diag' or @Name='Microsoft-Windows-Win32k' or @Name='Win32k'] and ( (EventID >= 1 and EventID <= 24) or EventID=5 or EventID=260)]]</Select>
<Select Path="Microsoft-Windows-Win32k/Messages">*[System[Provider[@Name='Microsoft-Windows-Security-Mitigations' or @Name='Microsoft-Windows-WER-Diag' or @Name='Microsoft-Windows-Win32k' or @Name='Win32k'] and ( (EventID >= 1 and EventID <= 24) or EventID=5 or EventID=260)]]</Select>
<Select Path="Microsoft-Windows-Win32k/Operational">*[System[Provider[@Name='Microsoft-Windows-Security-Mitigations' or @Name='Microsoft-Windows-WER-Diag' or @Name='Microsoft-Windows-Win32k' or @Name='Win32k'] and ( (EventID >= 1 and EventID <= 24) or EventID=5 or EventID=260)]]</Select>
<Select Path="Microsoft-Windows-Win32k/Power">*[System[Provider[@Name='Microsoft-Windows-Security-Mitigations' or @Name='Microsoft-Windows-WER-Diag' or @Name='Microsoft-Windows-Win32k' or @Name='Win32k'] and ( (EventID >= 1 and EventID <= 24) or EventID=5 or EventID=260)]]</Select>
<Select Path="Microsoft-Windows-Win32k/Render">*[System[Provider[@Name='Microsoft-Windows-Security-Mitigations' or @Name='Microsoft-Windows-WER-Diag' or @Name='Microsoft-Windows-Win32k' or @Name='Win32k'] and ( (EventID >= 1 and EventID <= 24) or EventID=5 or EventID=260)]]</Select>
<Select Path="Microsoft-Windows-Win32k/Tracing">*[System[Provider[@Name='Microsoft-Windows-Security-Mitigations' or @Name='Microsoft-Windows-WER-Diag' or @Name='Microsoft-Windows-Win32k' or @Name='Win32k'] and ( (EventID >= 1 and EventID <= 24) or EventID=5 or EventID=260)]]</Select>
<Select Path="Microsoft-Windows-Win32k/UIPI">*[System[Provider[@Name='Microsoft-Windows-Security-Mitigations' or @Name='Microsoft-Windows-WER-Diag' or @Name='Microsoft-Windows-Win32k' or @Name='Win32k'] and ( (EventID >= 1 and EventID <= 24) or EventID=5 or EventID=260)]]</Select>
<Select Path="System">*[System[Provider[@Name='Microsoft-Windows-Security-Mitigations' or @Name='Microsoft-Windows-WER-Diag' or @Name='Microsoft-Windows-Win32k' or @Name='Win32k'] and ( (EventID >= 1 and EventID <= 24) or EventID=5 or EventID=260)]]</Select>
<Select Path="Microsoft-Windows-Security-Mitigations/UserMode">*[System[Provider[@Name='Microsoft-Windows-Security-Mitigations' or @Name='Microsoft-Windows-WER-Diag' or @Name='Microsoft-Windows-Win32k' or @Name='Win32k'] and ( (EventID >= 1 and EventID <= 24) or EventID=5 or EventID=260)]]</Select>
</Query>
</QueryList>
XML for network protection events
<QueryList>
<Query Id="0" Path="Microsoft-Windows-Windows Defender/Operational">
<Select Path="Microsoft-Windows-Windows Defender/Operational">*[System[(EventID=1125 or EventID=1126 or EventID=5007)]]</Select>
<Select Path="Microsoft-Windows-Windows Defender/WHC">*[System[(EventID=1125 or EventID=1126 or EventID=5007)]]</Select>
</Query>
</QueryList>
List of attack surface reduction events
All attack surface reduction events are located under Applications and Services Logs > Microsoft > Windows and then the folder or provider as listed in the following table.
You can access these events in Windows Event viewer:
Open the Start menu and type event viewer, and then select the Event Viewer result.
Expand Applications and Services Logs > Microsoft > Windows and then go to the folder listed under Provider/source in the table below.
Double-click on the sub item to see events. Scroll through the events to find the one you're looking.

| Feature | Provider/source | Event ID | Description |
|---|---|---|---|
| Exploit protection | Security-Mitigations (Kernel Mode/User Mode) | 1 | ACG audit |
| Exploit protection | Security-Mitigations (Kernel Mode/User Mode) | 2 | ACG enforce |
| Exploit protection | Security-Mitigations (Kernel Mode/User Mode) | 3 | Don't allow child processes audit |
| Exploit protection | Security-Mitigations (Kernel Mode/User Mode) | 4 | Don't allow child processes block |
| Exploit protection | Security-Mitigations (Kernel Mode/User Mode) | 5 | Block low integrity images audit |
| Exploit protection | Security-Mitigations (Kernel Mode/User Mode) | 6 | Block low integrity images block |
| Exploit protection | Security-Mitigations (Kernel Mode/User Mode) | 7 | Block remote images audit |
| Exploit protection | Security-Mitigations (Kernel Mode/User Mode) | 8 | Block remote images block |
| Exploit protection | Security-Mitigations (Kernel Mode/User Mode) | 9 | Disable win32k system calls audit |
| Exploit protection | Security-Mitigations (Kernel Mode/User Mode) | 10 | Disable win32k system calls block |
| Exploit protection | Security-Mitigations (Kernel Mode/User Mode) | 11 | Code integrity guard audit |
| Exploit protection | Security-Mitigations (Kernel Mode/User Mode) | 12 | Code integrity guard block |
| Exploit protection | Security-Mitigations (Kernel Mode/User Mode) | 13 | EAF audit |
| Exploit protection | Security-Mitigations (Kernel Mode/User Mode) | 14 | EAF enforce |
| Exploit protection | Security-Mitigations (Kernel Mode/User Mode) | 15 | EAF+ audit |
| Exploit protection | Security-Mitigations (Kernel Mode/User Mode) | 16 | EAF+ enforce |
| Exploit protection | Security-Mitigations (Kernel Mode/User Mode) | 17 | IAF audit |
| Exploit protection | Security-Mitigations (Kernel Mode/User Mode) | 18 | IAF enforce |
| Exploit protection | Security-Mitigations (Kernel Mode/User Mode) | 19 | ROP StackPivot audit |
| Exploit protection | Security-Mitigations (Kernel Mode/User Mode) | 20 | ROP StackPivot enforce |
| Exploit protection | Security-Mitigations (Kernel Mode/User Mode) | 21 | ROP CallerCheck audit |
| Exploit protection | Security-Mitigations (Kernel Mode/User Mode) | 22 | ROP CallerCheck enforce |
| Exploit protection | Security-Mitigations (Kernel Mode/User Mode) | 23 | ROP SimExec audit |
| Exploit protection | Security-Mitigations (Kernel Mode/User Mode) | 24 | ROP SimExec enforce |
| Exploit protection | WER-Diagnostics | 5 | CFG Block |
| Exploit protection | Win32K (Operational) | 260 | Untrusted Font |
| Network protection | Windows Defender (Operational) | 5007 | Event when settings are changed |
| Network protection | Windows Defender (Operational) | 1125 | Event when Network protection fires in Audit-mode |
| Network protection | Windows Defender (Operational) | 1126 | Event when Network protection fires in Block-mode |
| Controlled folder access | Windows Defender (Operational) | 5007 | Event when settings are changed |
| Controlled folder access | Windows Defender (Operational) | 1124 | Audited Controlled folder access event |
| Controlled folder access | Windows Defender (Operational) | 1123 | Blocked Controlled folder access event |
| Controlled folder access | Windows Defender (Operational) | 1127 | Blocked Controlled folder access sector write block event |
| Controlled folder access | Windows Defender (Operational) | 1128 | Audited Controlled folder access sector write block event |
| Attack surface reduction | Windows Defender (Operational) | 5007 | Event when settings are changed |
| Attack surface reduction | Windows Defender (Operational) | 1122 | Event when rule fires in Audit-mode |
| Attack surface reduction | Windows Defender (Operational) | 1121 | Event when rule fires in Block-mode |
Note
From the user's perspective, attack surface reduction Warn mode notifications are made as a Windows Toast Notification for attack surface reduction rules.
In attack surface reduction, Network Protection provides only Audit and Block modes.
Resources to learn more about attack surface reduction
As mentioned in the video, Defender for Endpoint includes several attack surface reduction capabilities. Use the following resources to learn more:
| Article | Description |
|---|---|
| Application control | Use application control so that your applications must earn trust in order to run. |
| Attack surface reduction rules reference | Provides details about each attack surface reduction rule. |
| Attack surface reduction rules deployment guide | Presents overview information and prerequisites for deploying attack surface reduction rules, followed by step-by-step guidance for testing (audit mode), enabling (block mode) and monitoring. |
| Controlled folder access | Help prevent malicious or suspicious apps (including file-encrypting ransomware malware) from making changes to files in your key system folders (Requires Microsoft Defender Antivirus). |
| Device control | Protects against data loss by monitoring and controlling media used on devices, such as removable storage and USB drives, in your organization. |
| Exploit protection | Help protect the operating systems and apps your organization uses from being exploited. Exploit protection also works with third-party antivirus solutions. |
| Hardware-based isolation | Protect and maintain the integrity of a system as it starts and while it's running. Validate system integrity through local and remote attestation. Use container isolation for Microsoft Edge to help guard against malicious websites. |
| Network protection | Extend protection to your network traffic and connectivity on your organization's devices. (Requires Microsoft Defender Antivirus). |
| Test attack surface reduction rules | Provides steps to use audit mode to test attack surface reduction rules. |
| Web protection | Web protection lets you secure your devices against web threats and helps you regulate unwanted content. |
Tip
Do you want to learn more? Engage with the Microsoft Security community in our Tech Community: Microsoft Defender for Endpoint Tech Community.
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for