Microsoft Defender for Endpoint sensitivity labels protect and prioritize incident response
Applies to:
- Microsoft Defender for Endpoint Plan 1
- Microsoft Defender for Endpoint Plan 2
- Microsoft Defender XDR
Want to experience Defender for Endpoint? Sign up for a free trial.
A typical advanced persistent threat lifecycle (or APT) involves some data exfiltration -- the point at which data is taken from the organization. In those situations, sensitivity labels can tell security operations where to start by spelling out what data is highest priority to protect.
Defender for Endpoint helps to make prioritization of security incidents simpler with the use of sensitivity labels too. For example, sensitivity labels quickly identify incidents that can involve devices with sensitive information on them (such as confidential information).
Here's how to use sensitivity labels in Defender for Endpoint.
Investigate incidents that involve sensitive data on devices with Defender for Endpoint
Learn how to use data sensitivity labels to prioritize incident investigation.
Note
Labels are detected for Windows 10, version 1809 or later, and Windows 11.
In Microsoft Defender portal, select Incidents & alerts > Incidents.
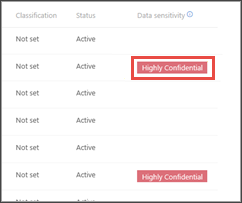
Scroll over to see the Data sensitivity column. This column reflects sensitivity labels that are observed on devices related to the incidents providing an indication of whether sensitive files are impacted by the incident.
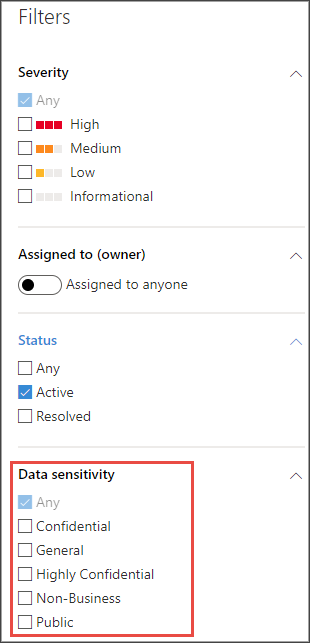
You can also filter based on Data sensitivity
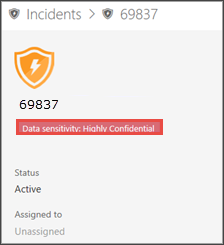
Open the incident page to further investigate.
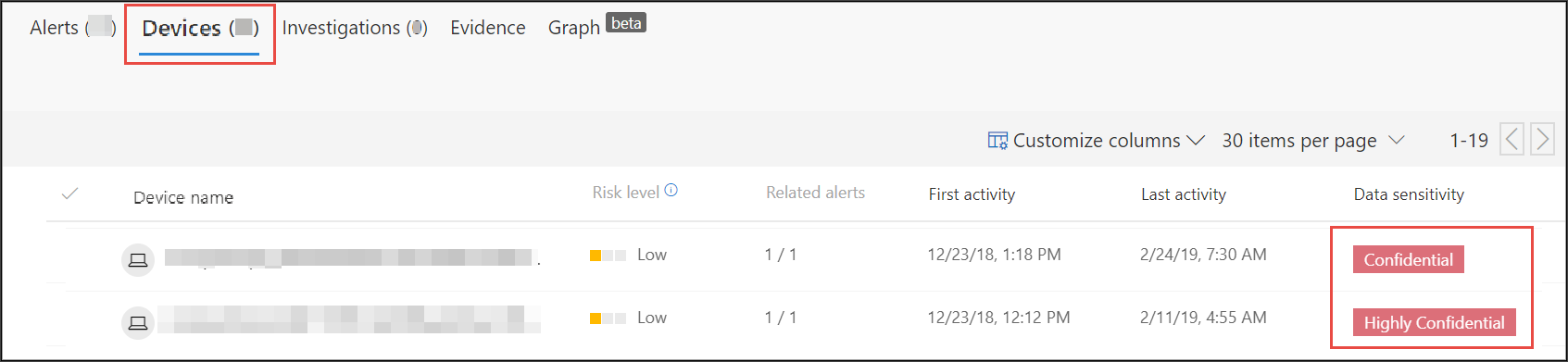
Select the Devices tab to identify devices storing files with sensitivity labels.
Select the devices that store sensitive data and search through the timeline to identify which files might be impacted then take appropriate action to ensure that data is protected.
You can narrow down the events shown on the device timeline by searching for data sensitivity labels. Doing this shows only events associated with files that the label name.
Tip
These data points are also exposed through the 'DeviceFileEvents' in advanced hunting, allowing advanced queries and schedule detection to take into account sensitivity labels and file protection status.
Related information about sensitivity labels
- Learn about sensitivity labels in Office 365
- Learn to apply sensitivity label inside of email or Office
- Learn how to use sensitivity labels as a condition when applying Data Loss Prevention
Tip
Do you want to learn more? Engage with the Microsoft Security community in our Tech Community: Microsoft Defender for Endpoint Tech Community.
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for