Certificate inventory
Applies to:
- Microsoft Defender Vulnerability Management
- Microsoft Defender XDR
- Microsoft Defender for Servers Plan 2
Note
To use this feature you'll require Microsoft Defender Vulnerability Management Standalone or if you're already a Microsoft Defender for Endpoint Plan 2 customer, the Defender Vulnerability Management add-on.
Certificates can be used in multiple ways. For example:
- As part of the TLS\SSL protocol.
- VPN client authentication, document signing, email encryption and email signing.
- Data encryption and authentication to ensure the secure transfer of information within your network and over the internet.
Issues with a certificate (for example, expiration or misconfiguration) could lead to the following results:
- A security vulnerability for your organization.
- A service outage.
- Negative results on day-to-day business operations.
The Certificate inventory lets you view a list of the certificates installed across your organization in a single central certificate inventory page. This feature can help you with the following tasks:
- Identify certificates that are about to expire so you can update them and prevent service disruption
- Detect potential vulnerabilities due to the use of weak signature algorithm (for example, SHA-1-RSA), short key size (for example, RSA 512 bit), or weak signature hash algorithm (for example, MD5)
- Ensure compliance with regulatory guidelines and organizational policy
Tip
Did you know you can try all the features in Microsoft Defender Vulnerability Management for free? Find out how to sign up for a free trial.
View your certificates
- Go to Vulnerability management > Software inventory in the Microsoft Defender portal.
- Select the Certificates tab.
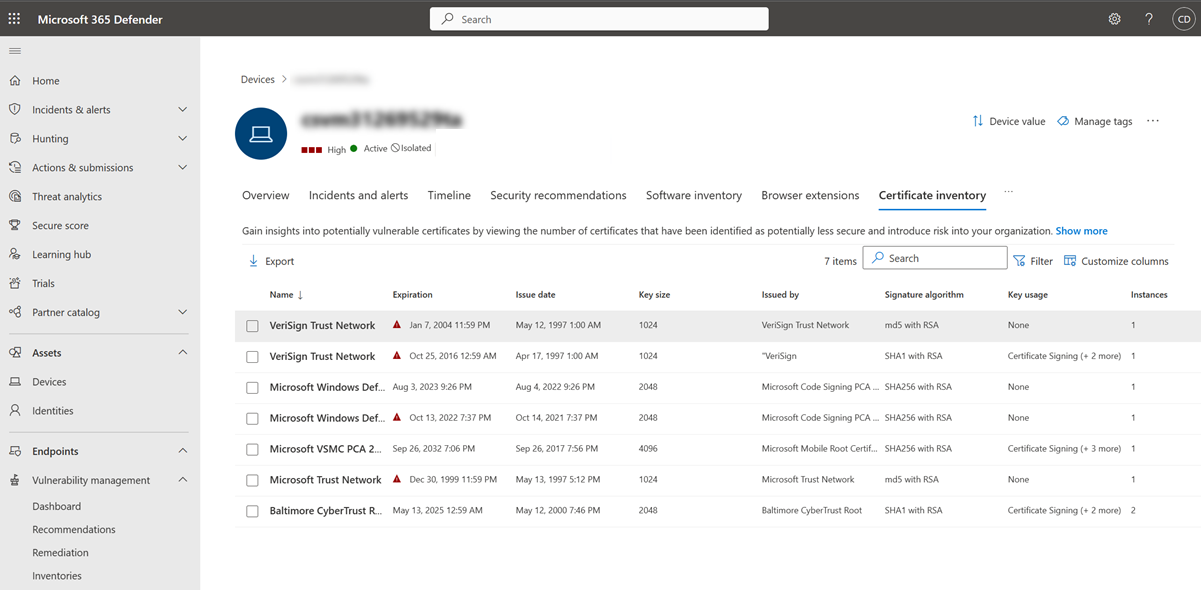
The Certificate inventory page opens with a list of the certificates installed across your organization, including details on the expiration date, key size, who issued the certificate, and the number of instances.
Note
Only certificates found on Windows devices (in the local machine certificate store) will be displayed in certificate inventory list.
Gain insights into potentially vulnerable certificates
At the top of the page, you can view the number of certificates that have been identified as potentially less secure and introduce risk into your organization. This number includes certificates with the following issues:
- Expired.
- Will expire in 60 days or less.
- Have a key size with fewer than 2,048 bits, as they're considered less secure.
- Have a weak signature algorithm, like SHA-1 and MD5.
- Are considered vulnerable since they're self-signed.
Use filters on the certificate inventory page
You can use filters to view the inventory based on:
- Certificate status: view the certificates that have expired, are expiring soon, are issued with a future date, or are current
- Self-signed: view certificates that are self-signed
- Key size: view certificates that have a short key size or valid key size
- Signature hash: view certificates that have a weak signature hash or valid signature hash
- Key usage: view certificates with key usage values, such as digital signature, repudiation, and certificate signing
Get more information on a discovered certificate
When you select the certificate that you want to investigate, a flyout panel opens with the certificate details page:
You can select the Issuing details tab to see information on who the certificate was issued to and who it was issued by.
Certificates on devices
To see the list of the devices the certificate is installed on, choose the Installed devices tab from the certificate flyout pane. From here, you can search for a particular device the certificate is installed on, and you can export a list of the devices to a csv file.
You can also view a list of certificates installed on a device:
Select the device from the Installed devices tab in the flyout panel or select the device directly from the Device inventory page.
Select the Certificate inventory tab to see a list of certificates installed on that device.
Select a certificate to open the flyout with more information.
Vulnerability management dashboard widget
See how many certificates have expired or are due to expire in the next 30, 60 or 90 days from the Expiring certificates widget available in the vulnerability management dashboard.
Select View all to go to the certificate inventory page.
Use advanced hunting
You can use advanced hunting queries to gain visibility on certificates in your organization. For example, using the DeviceTvmCertificateInfo table, you can query to show all expired certificates.
Related articles
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for