Troubleshooting Microsoft Security intelligence malware submission errors caused by administrator block
In some instances, an administrator block might cause submission issues when you try to submit a potentially infected file to the Microsoft Security intelligence website for analysis. The following process shows how to resolve this problem.
Review your settings
Open your Azure Enterprise application settings. Under Enterprise Applications > Users can consent to apps accessing company data on their behalf, check whether Yes or No is selected.
If No is selected, a Microsoft Entra administrator for the customer tenant will need to provide consent for the organization. Depending on the configuration with Microsoft Entra ID, users might be able to submit a request right from the same dialog box. If there's no option to ask for admin consent, users need to request for these permissions to be added to their Microsoft Entra admin. Go to the following section for more information.
If Yes is selected, ensure the Windows Defender Security Intelligence app setting Enabled for users to sign in? is set to Yes in Azure. If No is selected, you'll need to request a Microsoft Entra admin enable it.
Implement Required Enterprise Application permissions
This process requires a global or application admin in the tenant.
Select Grant admin consent for organization.
If you're able to do so, review the API permissions required for this application, as the following image shows. Provide consent for the tenant.
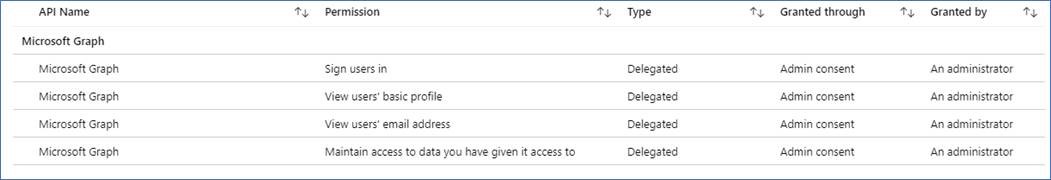
If the administrator receives an error while attempting to provide consent manually, try either Option 1 or Option 2 as possible workarounds.
Option 1 Approve enterprise application permissions by user request
Note
This is currently a preview feature.
Microsoft Entra admins will need to allow for users to request admin consent to apps. Verify the setting is configured to Yes in Enterprise applications.
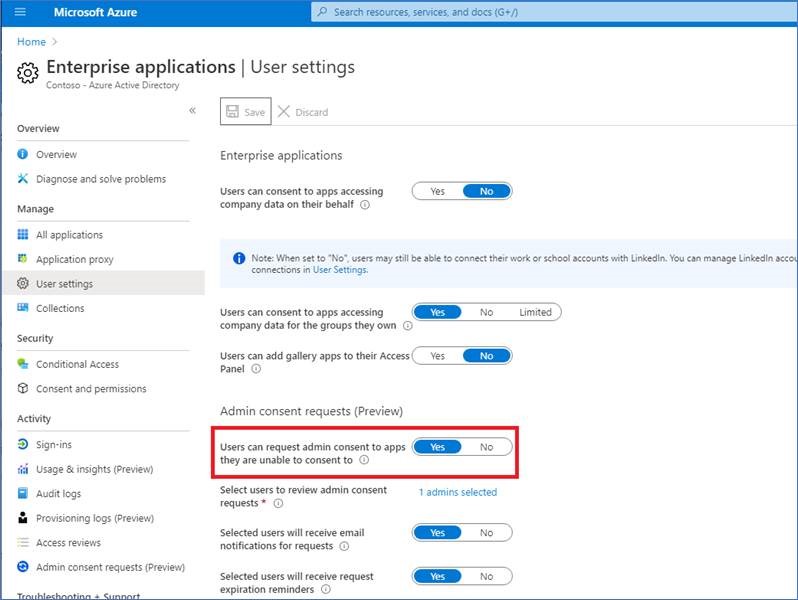
More information is available in Configure Admin consent workflow.
Once this setting is verified, users can go through the enterprise customer sign-in at Microsoft security intelligence, and submit a request for admin consent, including justification.
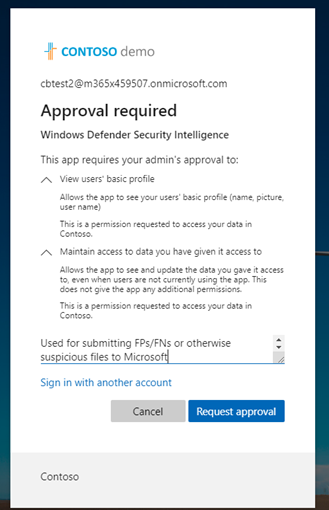
Admin will be able to review and approve the application permissions Azure admin consent requests.
After providing consent, all users in the tenant will be able to use the application.
Option 2 Provide admin consent by authenticating the application as an admin
This process requires that global admins go through the Enterprise customer sign-in flow at Microsoft security intelligence.
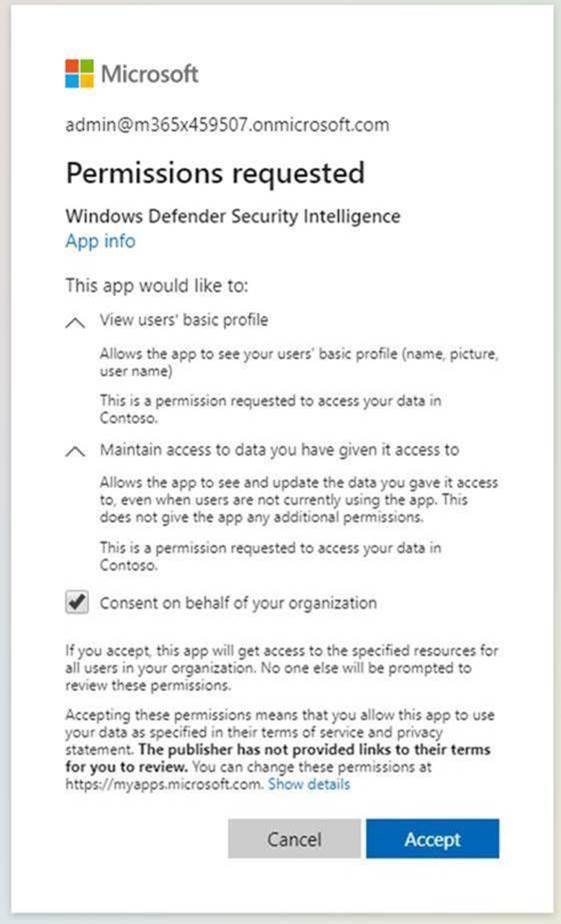
Then, admins review the permissions and make sure to select Consent on behalf of your organization, and then select Accept.
All users in the tenant will now be able to use this application.
Option 3: Delete and readd app permissions
If neither of these options resolve the issue, try the following steps (as an admin):
Remove previous configurations for the application. Go to Enterprise applications and select delete.
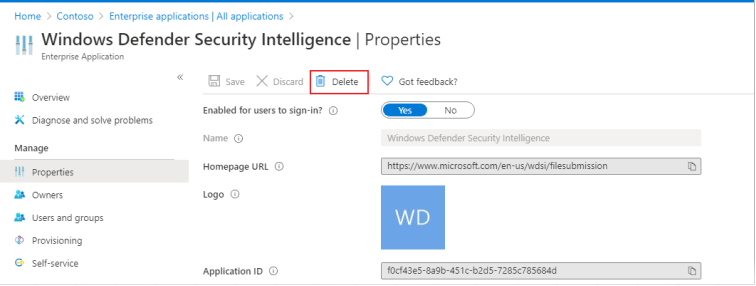
Capture TenantID from Properties.
Replace {tenant-id} with the specific tenant that needs to grant consent to this application in the URL below. Copy this URL into browser. The rest of the parameters are already completed.
https://login.microsoftonline.com/{tenant-id}/v2.0/adminconsent?client_id=f0cf43e5-8a9b-451c-b2d5-7285c785684d&state=12345&redirect_uri=https%3a%2f%2fwww.microsoft.com%2fwdsi%2ffilesubmission&scope=openid+profile+email+offline_access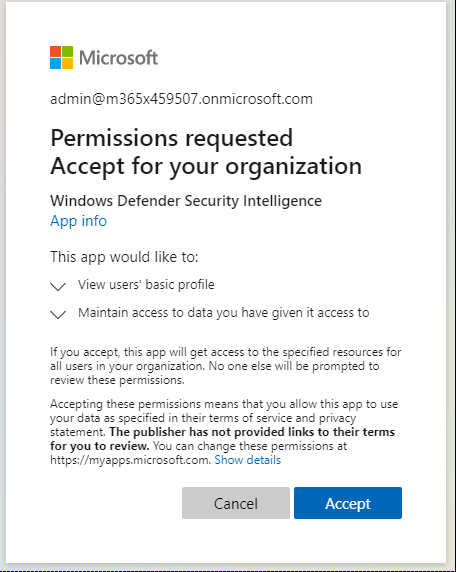
Review the permissions required by the application, and then select Accept.
Confirm the permissions are applied in the Azure portal.

Sign in to Microsoft security intelligence as an enterprise user with a non-admin account to see if you have access.
If the warning is not resolved after following these troubleshooting steps, call Microsoft support.
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for