Teams meeting add-in security when using your Outlook client
The Teams meeting add-in (or TMA) is used to schedule meetings in Teams from the Outlook desktop client on Windows.
TMA coordinates between the Outlook and Teams services, so it's important to keep TMA secure. Taking security measures helps lower the risk of cybersecurity attack.
Here are the ways to secure your Teams meeting add-in covered in this article:
- (Recommended) Use Microsoft Outlook Trust Center to prevent Outlook from loading TMA when the TMA DLLs aren’t signed with a certificate from a trusted publisher.
- Use group policies for the domain and update the Root certificate and trusted publisher, especially since it prevents users from being prompted to trust the publisher.
- AppLocker can also be used to stop DLLs from untrusted publishers from being loaded.
Microsoft Outlook Trust Center group policies
You can use Trust Center group policies for add-in management:
- To make sure only add-ins trusted by the organization are loaded
- To stop add-ins from unspecified locations from loading
This practice helps protect against malware compromising the COM registration to load from another location with planted DLLs.
Here are the steps:
- Protect Outlook from add-ins that aren't secure
- Go to the Outlook Trust Center, https://www.microsoft.com/en-us/trust-center.
- When you arrive, select File > Options > Trust Center.
- Select Microsoft Outlook Trust Center.
- Under Microsoft Outlook Trust Center in the left menu, select Trust Center Settings.
- Under Macro Settings, select Notifications for digitally signed macros, all other macros disabled.
- Admins must select Apply macro security settings to installed add-ins in this case.
- Select the OK button to make these changes and exit the trust center, and select OK again, to close options.
The choices persist from there.
Now, outside of the Outlook Trust Center:
Restart Outlook on your client.
When Outlook reopens, the application asks permission to load each add-in, automatically disabling any add-in that isn't signed.
- The image below is what the user experience of TMA looks like:
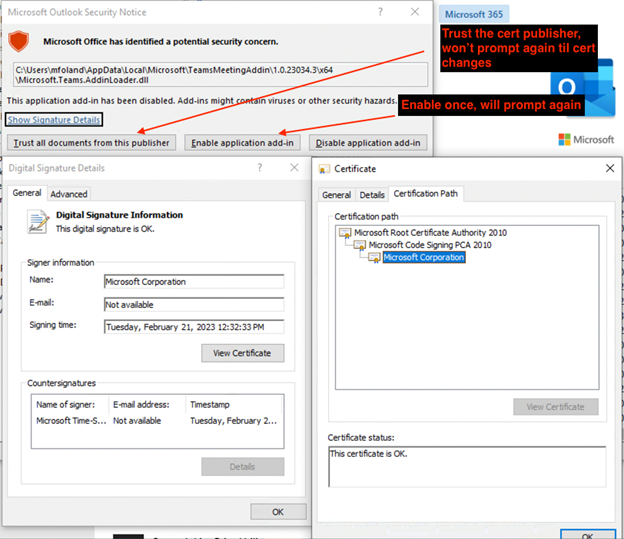
- End-users see a Microsoft Outlook Security Notice that may read Microsoft Office has identified a potential security concern listing Microsoft.Teams.AddinLoader.dll. The options are:
- Trust all documents from this Publisher.
- Selecting this option trusts the certificate’s publisher and the user won’t be prompted again until the certificate changes.
- 2. Enable application add-in.
- This option only enables on a case-by-case basis, so this add-in enables for this single time, and the user will be prompted again.
- 3. Disable application add-in.
- Disables the add-in.
- Trust all documents from this Publisher.
- Follow the steps to set up Group Policy to automatically trust a specific root certificate Authority.
- Open the Group Policy Management Console on your domain controller (DC).
- Create a new Group Policy Object (GPO) or edit an existing GPO that you want to use to configure the settings.
- Next go to Computer Configuration > Policies > Windows Settings > Security Settings > Public Key Policies.
- Right-click on Trusted Root Certification Authorities and select Import.
- Browse to the root certificate Microsoft Root Certificate Authority 2010 file for the certificate publisher you want to trust and import it.
- Link the GPO to the appropriate organizational unit to apply the settings to the computers that you want to use the policy. For more information on this process, see: Deploy the Applocker Policy into production
- Next, follow the steps to set up Group Policy to automatically trust the publisher.
- Open the Group Policy Management Console on your domain controller.
- Create a new GPO or edit an existing GPO that you want to use to configure the settings.
- Navigate to Computer Configuration > Policies > Windows Settings > Security Settings > Public Key Policies.
- Right-click on Trusted Publishers and select Import.
- Browse to the leaf certificate Microsoft Corporation file for the certificate publisher you want to trust and import it.
- Link the GPO to the appropriate organizational unit to apply the settings to the computers you choose.
- The image below is what the user experience of TMA looks like:
Add-in Management through Group Policies
- Download Administrative Template files (ADMX/ADML) for Microsoft 365 Apps for enterprise/Office LTSC 2021/Office 2019/Office 2016 and the Office Customization Tool for Office 2016.
- Add the ADMX/ADML template files to the Group Policy Management:
- Under User Configuration > Administrative Templates > Microsoft Outlook (version number) > Security > Trust Center.
- Apply Macro security settings to Macros, add-ins and additional actions: This policy setting controls whether Outlook also applies the Macro security settings to installed COM add-ins and additional actions.
- Set to: Enabled
- Security setting for macros: This policy setting controls the security level for macros in Outlook.
- Set to: Warning for signed, disable unsigned.
- This option corresponds to the Notifications for digitally signed macros, all other macros disabled option in the Trust Center. If an add-in is digitally signed by a trusted publisher, the add-in can run signed by a trusted publisher.
- Set to: Warning for signed, disable unsigned.
- Apply Macro security settings to Macros, add-ins and additional actions: This policy setting controls whether Outlook also applies the Macro security settings to installed COM add-ins and additional actions.
- Additional Group Policies around Add-ins.
- Under User Configuration > Administrative Templates > Microsoft Outlook 2016 > Security
- Configure add-in trust level: All installed trusted COM add-ins can be trusted. Exchange Settings for the add-ins still override if present and this option is selected.
- Under User Configuration > Administrative Templates > Microsoft Outlook 2016 > Miscellaneous
- Block all unmanaged add-ins: This policy setting Blocks all add-ins that aren't managed by the "List of managed add-ins" policy setting.
- List of managed add-ins: This policy setting allows you to specify which add-ins are always enabled, always disabled (blocked), or configurable by the user. To block add-ins that aren't managed by this policy setting, you must also configure the "Block all unmanaged add-ins" policy setting.
- Under User Configuration > Administrative Templates > Microsoft Outlook 2016 > Security > Security Form Settings > Programmatic Security > Trusted Add-ins
- Configure Trusted Add-ins: This policy setting is used to specify a list of Trusted Add-ins that can be run without being restricted by the security measures in Outlook.
- Under User Configuration > Administrative Templates > Microsoft Outlook 2016 > Security
- Under User Configuration > Administrative Templates > Microsoft Outlook (version number) > Security > Trust Center.
AppLocker
The AppLocker application control policies help you control which apps and files users can run. These file types include executable files, scripts, Windows Installer files, dynamic-link libraries (DLLs), packaged apps, and packaged app installers.
Let's focus on using AppLocker to stop DLLs that aren't signed by a trusted publisher from loading.
Use AppLocker to stop unsigned DLLs from loading.
To use Applocker to stop your unsigned DLLs from loading, you have to create a new DLL rule in your Local or Group Policy.
Note
The pre-requisites for this section are Windows 10 Enterprise and, Education or Windows Server 2012 or later.
To set up AppLocker on Windows 10 or Windows 11 for a specific DLL, follow these steps:
- Open policy editor.
- Local Machine
- Open the Local Security Policy editor. Type secpol.msc into the Run dialog box or the Start menu search bar, and then press Enter.
- Group Policy
- Edit an AppLocker policy Through Group Policies | Microsoft Learn
- Local Machine
- In the Local Security Policy editor, navigate go to Application Control Policies > AppLocker > DLL Rules.
- If you're using a supported edition of Windows and still don't see DLL rules, it's possible that AppLocker isn't enabled or configured on your system. In this case, you can follow these steps to enable AppLocker:
- Open the Local Security Policy editor. Type secpol.msc into the Run dialog box or the Start menu search bar, then press Enter.
- In the Local Security Policy editor, navigate to Application Control Policies > AppLocker.
- Right-click on AppLocker and select Properties.
- Under AppLocker Properties, in the Enforcement tab:
- Select Configured next to Configure rule enforcement.
- Configure extra policies such as rule collections as audit-only mode.
- Once this is verified, it can be updated to Enforce
- Select OK to save the changes.
- Be sure the Application Identity service is running.
- If you're using a supported edition of Windows and still don't see DLL rules, it's possible that AppLocker isn't enabled or configured on your system. In this case, you can follow these steps to enable AppLocker:
- Create a new DLL Rule
- From the Local Security Policy editor
- Right-click on DLL Rules and select Create New Rule.
- In the Create DLL Rule wizard, select Use an Existing File and browse to the DLL file that you want to create a rule for.
- Select the type of rule that you want to create (such as to allow or deny) and configure any other rule conditions that are needed.
- Complete the wizard and save the new rule.
- Or from PowerShell:
- The PowerShell cmdlets that are needed to create a new DLL Rule can be piped together.
- From the Local Security Policy editor
- Add-in Management through AppLocker Group Policies
- Get-ChildItem - Gets the object for the file
- Get-AppLockerFileInformation - Gets the file information necessary to create AppLocker rules from a list of files or an event log
- New-AppLockerPolicy - Creates a new AppLocker policy from a list of file information and other rule creation options.
- RuleType needs to be published and this enforces code signing.
- User can be an individual user or group, all examples use Everyone.
- AllowWindows indicates that the AppLocker policy allows all local Windows components.
- To create the DLL rule per file
- TMA file location depends on the installation type
- Per user installation
- Install location: %localappdata%\Microsoft\TeamsMeetingAddin
- Per machine installation
- Install location: C:\Program Files(x86)\TeamsMeetingAddin
- Per user installation
Get-ChildItem <TMAFileLocation>\Microsoft.Teams.AddinLoader.dll | Get-AppLockerFileInformation | New-AppLockerPolicy -RuleType Publisher, Hash -User Everyone -RuleNamePrefix TeamsMeetingAddin -AllowWindows -Xml | Out-File .\TMA.xml- Set the policy:
- Local Machines
i.
Set-AppLockerPolicy -XmlPolicy .\TMA.xml -Merge - Group Policy
i.
Set-AppLockerPolicy -XMLPolicy .\TMA.xm -LDAP "<LDAP Info for Group Policy>"
- Local Machines
i.
- Steps 1 and 2 need to be completed for each DLL under x64 and x86 directories for TMA.
- TMA file location depends on the installation type
- Create all DLL rules at once:
- Get-AppLockerFileInformation -Directory .\Microsoft\TeamsMeetingAddin\1.0.23089.2 -Recurse | New-AppLockerPolicy -Verbose -RuleType Publisher, Hash -User Everyone -RuleNamePrefix TeamsMeetingAddin -AllowWindows -Xml | Out-File .\TMA.xml`
Set-AppLockerPolicy -XmlPolicy .\TMA.xml -Merge3. LDAP info is needed to perform Group Policy updates.
Important things to know:
- It’s assumed that if AppLocker is turned on in an environment, then the IT department is familiar with AppLocker. They're aware it’s designed to use an Allow model and anything not Allowed will be blocked.
- Hash rules are provided for fallback when Publisher rule fails. Hash rules need to be updated every time TMA updates.
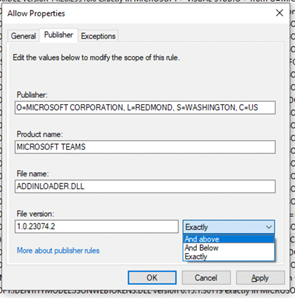
- The PowerShell command for adding AppLocker policies will be set up to match only the exact version of the DLL being added > go into the Allow Properties for the Publisher Rule and change the File Versions options for scope to And Above the listed version.
- To make AppLocker accept a wider range of DLL versions for Publisher Rules, go to the Allow Properties for the Publisher Rule and change the drop-down for File version to And above (from Exactly).
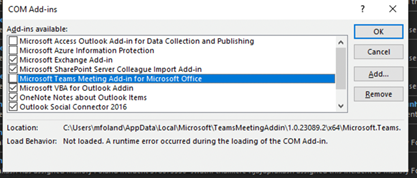
- Once enabled if the AppLocker policy blocks the add-in, it will not show, and inspecting COM add-ins will show:
For more information
Enable or disable macros in Microsoft 365 files - Microsoft Support AppLocker (Windows) | Microsoft Learn
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for