Threat investigation and response
Tip
Did you know you can try the features in Microsoft Defender XDR for Office 365 Plan 2 for free? Use the 90-day Defender for Office 365 trial at the Microsoft Defender portal trials hub. Learn about who can sign up and trial terms here.
Threat investigation and response capabilities in Microsoft Defender for Office 365 help security analysts and administrators protect their organization's Microsoft 365 for business users by:
- Making it easy to identify, monitor, and understand cyberattacks.
- Helping to quickly address threats in Exchange Online, SharePoint Online, OneDrive for Business and Microsoft Teams.
- Providing insights and knowledge to help security operations prevent cyberattacks against their organization.
- Employing automated investigation and response in Office 365 for critical email-based threats.
Threat investigation and response capabilities provide insights into threats and related response actions that are available in the Microsoft Defender portal. These insights can help your organization's security team protect users from email- or file-based attacks. The capabilities help monitor signals and gather data from multiple sources, such as user activity, authentication, email, compromised PCs, and security incidents. Business decision makers and your security operations team can use this information to understand and respond to threats against your organization and protect your intellectual property.
Get acquainted with threat investigation and response tools
Threat investigation and response capabilities in the Microsoft Defender portal at https://security.microsoft.com are a set of tools and response workflows that include:
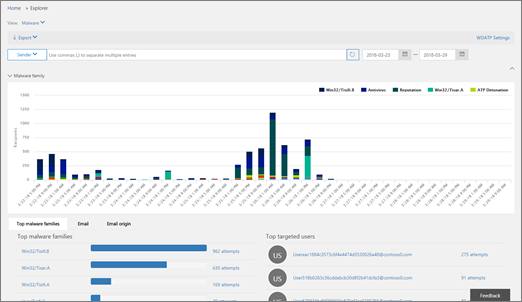
Explorer
Use Explorer (and real-time detections) to analyze threats, see the volume of attacks over time, and analyze data by threat families, attacker infrastructure, and more. Explorer (also referred to as Threat Explorer) is the starting place for any security analyst's investigation workflow.
To view and use this report in the Microsoft Defender portal at https://security.microsoft.com, go to Email & collaboration > Explorer. Or, to go directly to the Explorer page, use https://security.microsoft.com/threatexplorer.
Office 365 Threat Intelligence connection
This feature is only available if you have an active Office 365 E5 or G5 or Microsoft 365 E5 or G5 subscription or the Threat Intelligence add-on. For more information, see the Office 365 Enterprise E5 product page.
Data from Microsoft Defender for Office 365 is incorporated into Microsoft Defender XDR to conduct a comprehensive security investigation across Office 365 mailboxes and Windows devices.
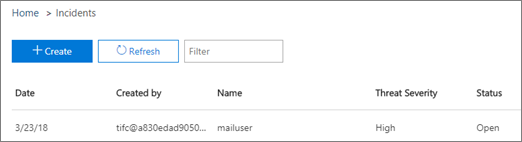
Incidents
Use the Incidents list (this is also called Investigations) to see a list of in flight security incidents. Incidents are used to track threats such as suspicious email messages, and to conduct further investigation and remediation.
To view the list of current incidents for your organization in the Microsoft Defender portal at https://security.microsoft.com, go to Incidents & alerts > Incidents. Or, to go directly to the Incidents page, use https://security.microsoft.com/incidents.
Attack simulation training
Use Attack simulation training to set up and run realistic cyberattacks in your organization, and identify vulnerable people before a real cyberattack affects your business. To learn more, see Simulate a phishing attack.
To view and use this feature in the Microsoft Defender portal at https://security.microsoft.com, go to Email & collaboration > Attack simulation training. Or, to go directly to the Attack simulation training page, use https://security.microsoft.com/attacksimulator?viewid=overview.
Automated investigation and response
Use automated investigation and response (AIR) capabilities to save time and effort correlating content, devices, and people at risk from threats in your organization. AIR processes can begin whenever certain alerts are triggered, or when started by your security operations team. To learn more, see automated investigation and response in Office 365.
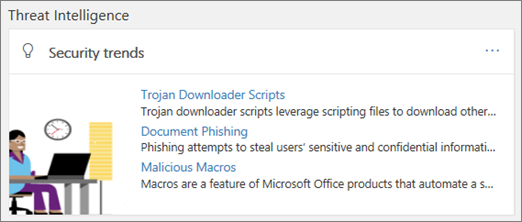
Threat intelligence widgets
As part of the Microsoft Defender for Office 365 Plan 2 offering, security analysts can review details about a known threat. This is useful to determine whether there are additional preventative measures/steps that can be taken to keep users safe.
How do we get these capabilities?
Microsoft 365 threat investigation and response capabilities are included in Microsoft Defender for Office 365 Plan 2, which is included in Enterprise E5 or as an add-on to certain subscriptions. To learn more, see Defender for Office 365 Plan 1 vs. Plan 2 cheat sheet.
Required roles and permissions
Microsoft Defender for Office 365 uses role-based access control. Permissions are assigned through certain roles in Microsoft Entra ID, the Microsoft 365 admin center, or the Microsoft Defender portal.
Tip
Although some roles, such as Security Administrator, can be assigned in the Microsoft Defender portal, consider using either the Microsoft 365 admin center or Microsoft Entra ID instead. For information about roles, role groups, and permissions, see the following resources:
| Activity | Roles and permissions |
|---|---|
| Use the Microsoft Defender Vulnerability Management dashboard View information about recent or current threats |
One of the following:
These roles can be assigned in either Microsoft Entra ID (https://portal.azure.com) or the Microsoft 365 admin center (https://admin.microsoft.com). |
| Use Explorer (and real-time detections) to analyze threats | One of the following:
These roles can be assigned in either Microsoft Entra ID (https://portal.azure.com) or the Microsoft 365 admin center (https://admin.microsoft.com). |
| View Incidents (also referred to as Investigations) Add email messages to an incident |
One of the following:
These roles can be assigned in either Microsoft Entra ID (https://portal.azure.com) or the Microsoft 365 admin center (https://admin.microsoft.com). |
| Trigger email actions in an incident Find and delete suspicious email messages |
One of the following:
The Global Administrator and Security Administrator roles can be assigned in either Microsoft Entra ID (https://portal.azure.com) or the Microsoft 365 admin center (https://admin.microsoft.com). The Search and Purge role must be assigned in the Email & collaboration roles in the Microsoft 36 Defender portal (https://security.microsoft.com). |
| Integrate Microsoft Defender for Office 365 Plan 2 with Microsoft Defender for Endpoint Integrate Microsoft Defender for Office 365 Plan 2 with a SIEM server |
Either the Global Administrator or the Security Administrator role assigned in either Microsoft Entra ID (https://portal.azure.com) or the Microsoft 365 admin center (https://admin.microsoft.com). --- plus --- An appropriate role assigned in additional applications (such as Microsoft Defender Security Center or your SIEM server). |
Next steps
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for