1.4 Relationship to Other Protocols
The extensions to the CIFS protocol rely on the Simple and Protected Generic Security Service Application Program Interface Negotiation Mechanism (SPNEGO), as described in [MS-AUTHSOD] section 2.1.2.3.1 and specified in [RFC4178], for authentication, which in turn relies on Kerberos, as specified in [MS-KILE], and/or the NT LAN Manager (NTLM), as specified in [MS-NLMP], challenge/response authentication protocol.
The Server Message Block (SMB) Version 2 Protocol is a new version of SMB. For more information about the SMB Version 2 Protocol, see [MS-SMB2]. This specification does not require implementation of the SMB Version 2 Protocol.
The following protocols extend this specification to provide additional functionality:
The Distributed File System (DFS): Namespace Referral Protocol, as specified in [MS-DFSC]. For more information, see [MSDFS]. For management of DFS, see [MS-DFSNM].
The following protocols can use the SMB Version 1.0 Protocol as a transport:
The Remote Procedure Call (RPC) Protocol Extensions. Note that when named pipes are used, this protocol requires the SMB Protocol. For more information, see [MS-RPCE].
The Remote Mailslot Protocol. This protocol can use the SMB Version 1.0 Protocol as a transport but supports other transports as well. For more information, see [MS-MAIL].
The CIFS Browser Protocol. This protocol uses the Remote Mailslot Protocol and the RAP as transport protocols, which in turn can use this specification. It does not use this specification directly, but is included here for completeness. For more information, see [MS-BRWS].
The SMB protocol server, upon request from an underlying object store, optionally invokes the Encrypting File System Remote (EFSRPC) protocol when a user attempts to open or create a new encrypted file. For more information, see [MS-FSA] and [MS-EFSR].
For more information, see [MS-BRWSA] and [MS-WKST].
The following diagram illustrates the relationship amongst the protocols.
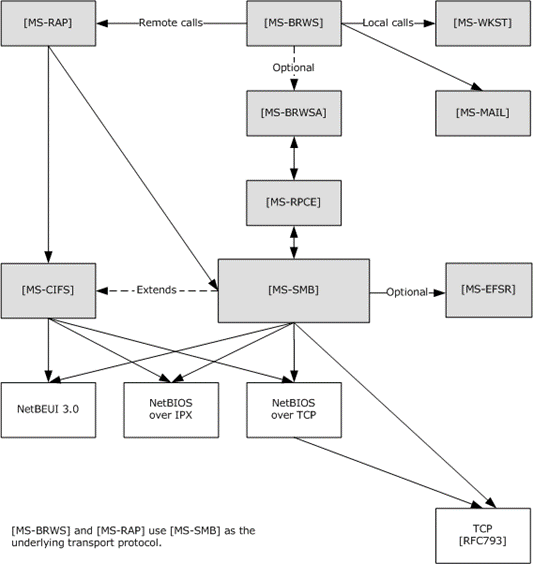
Figure 1: Relationships to other protocols