4.3 NetrJoinDomain2 Example
In this example, "SrvrA" is a machine that is not joined to a domain, and there exists a domain with the name "DomainA" and a domain controller of that domain named "DC-A".
A client calls the NetrJoinDomain2 method (section 3.2.4.13) on the server named "SrvrA":
-
unsigned long NetrJoinDomain2( [in] handle_t RpcBindingHandle, [in, string, unique] wchar_t* ServerName = { "SrvrA" }, [in, string] wchar_t* DomainName = { "DomainA\DC-A" }, [in, string, unique] wchar_t* MachineAccountOU = { NULL }, [in, string, unique] wchar_t* AccountName = { NULL }, [in, unique] PJOINPR_ENCRYPTED_USER_PASSWORD Password = { NULL }, [in] unsigned long Options = { 0x00000001 } );
Upon receiving this message, "SrvrA" establishes an SMB session with the domain controller "DC-A", using the credentials presented. In this example, there are no credentials; therefore the session is established as an anonymous session.
The server then queries for the domain_name and security identifier (SID) properties of "DC-A", and stores them locally.
As a last step, "SrvrA" creates a domain-object ([MS-ADTS] section 6.4.2) for itself, and sets the following attributes:
sAMAccountName
userAccountControl
unicodePwd
dNSHostName
servicePrincipalName
The server then responds to the client with the following message:
-
unsigned long = { 0 } NetrJoinDomain2( [in] handle_t RpcBindingHandle, [in, string, unique] wchar_t* ServerName, [in, string] wchar_t* DomainName, [in, string, unique] wchar_t* MachineAccountOU, [in, string, unique] wchar_t* AccountName, [in, unique] PJOINPR_ENCRYPTED_USER_PASSWORD Password, [in] unsigned long Options );
The following sequence diagram shows the sequence of messages that can be exchanged as a result of a NetrJoinDomain2 message sent to the server.
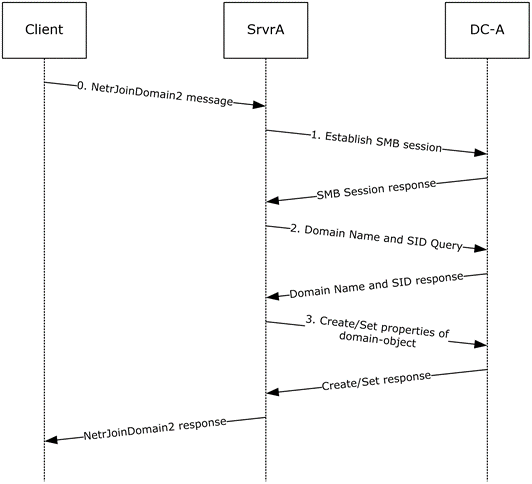
Figure 6: NetrJoinDomain2 sequence
The following state changes occur as a part of this message:
Initial states:
SrvrA
DC-A
DomainNameNetBIOS = "Workgroup".
DomainSID = NULL.
Domain-Secret-Value = NULL.
DomainNameNetBIOS = "DomainA".
DomainSID = { SID-Value}.
End states:
SrvrA
DC-A
DomainNameNetBIOS = "DomainA".
DomainSID = {SID-Value}.
Domain-Secret-Value = { domain-secret }.
DomainNameNetBIOS = "DomainA".
DomainSID = { SID-Value }.
A computer account object exists with the following LDAP attributes:
userAccountControl = USER_WORKSTATION_TRUST_ACCOUNT.
samAccountName = "SrvrA$".
unicodePwd = { domain-secret }.
dNSHostName = "SrvrA.<DomainA-DNS-Name>.
servicePrincipalName = {
"HOST/SrvrA",
"HOST/SrvrA.<DomainA-DNS-Name>"
}