Manage subscriptions and resources under the Azure plan
Appropriate roles: Admin agent
This article explains how Cloud Solution Provider (CSP) partners can use various role-based access control (RBAC) options to get operational control and management of a customer's Azure resources.
When you transition a customer to the Azure plan, you're assigned privileged admin rights in Azure—subscription owner rights through Admin on Behalf of (AOBO) by default.
Note
Admin rights to the Azure subscription can be removed by the customer at the subscription level, resource group level, or workload level.
Partners can get continuous operational control and management of a customer's Azure resources in CSP by using various options available through the role-based access control feature (RBAC).
Admin on Behalf of - With AOBO, any user with the Admin agent role in the partner tenant has RBAC owner access to Azure subscriptions that you create through the CSP program.
Azure Lighthouse: AOBO doesn't have the flexibility to create distinct groups that work with different customers, or to enable different roles for groups or users. However, using Azure Lighthouse, you can assign different groups to different customers or roles. Because users have the appropriate level of access through Azure delegated resource management, you can reduce the number of users who have the Admin agent role (and thus have full AOBO access). That helps improve security by limiting unnecessary access to your customers' resources. It also gives you more flexibility to manage multiple customers at scale. For more information, see Azure Lighthouse and the Cloud Solution Provider program.
Directory or Guest Users or Service Principals: You can delegate granular access to CSP subscriptions by adding users in the customer directory or by adding guest users and assigning specific RBAC roles.
As a security practice, Microsoft recommends assigning users the minimum permissions they need to do their work. For more information, see Microsoft Entra Privileged Identity Management resources.
Link your PartnerID to your credentials to manage a customer's Azure resources
The following table shows the methods used to associate your PartnerID (formerly MPN ID) with various RBAC access options.
| Category | Scenario | PartnerID association |
|---|---|---|
| AOBO | CSP direct partner or indirect provider creates the subscription for the customer, making the CSP direct partner or indirect provider the default owner of the subscription using AOBO. CSP direct partner or indirect provider gives indirect reseller access to the subscription using AOBO. | Automatic (no partner work required) |
| Azure Lighthouse | Partner creates a new Managed Service offer in Marketplace. The offer is accepted on the CSP subscription and the partner gets access to the CSP subscription. | Automatic (no partner work required) |
| Azure Lighthouse | Partner deploys an Azure Resource Manager (ARM) template in Azure subscription | Partner must associate the PartnerID with the user or service principal in the partner tenant. For more information, see Link your PartnerID to track your impact on delegated resources. |
| Directory or Guest user | Partner creates a new user or service principal in the customer directory and gives access to the CSP subscription to the user. Partner creates a new user or service principal in the customer directory. Partner adds the user to a group and gives access to the CSP subscription to the group. | Partner must associate the PartnerID with the user or service principal in the customer tenant. For more information, see Link a PartnerID to your account that's used to manage customers. |
Confirm that you have admin access
You must have admin access to manage your customer's services and to receive earned credits. For more information about earned credits, see Partner earned credits.
To determine whether you have admin access, use the following steps:
- Review the daily usage file: Review the unit price and effective unit price in the daily usage file and confirm whether a discount is being applied. If you're receiving the discount, you're the admin.
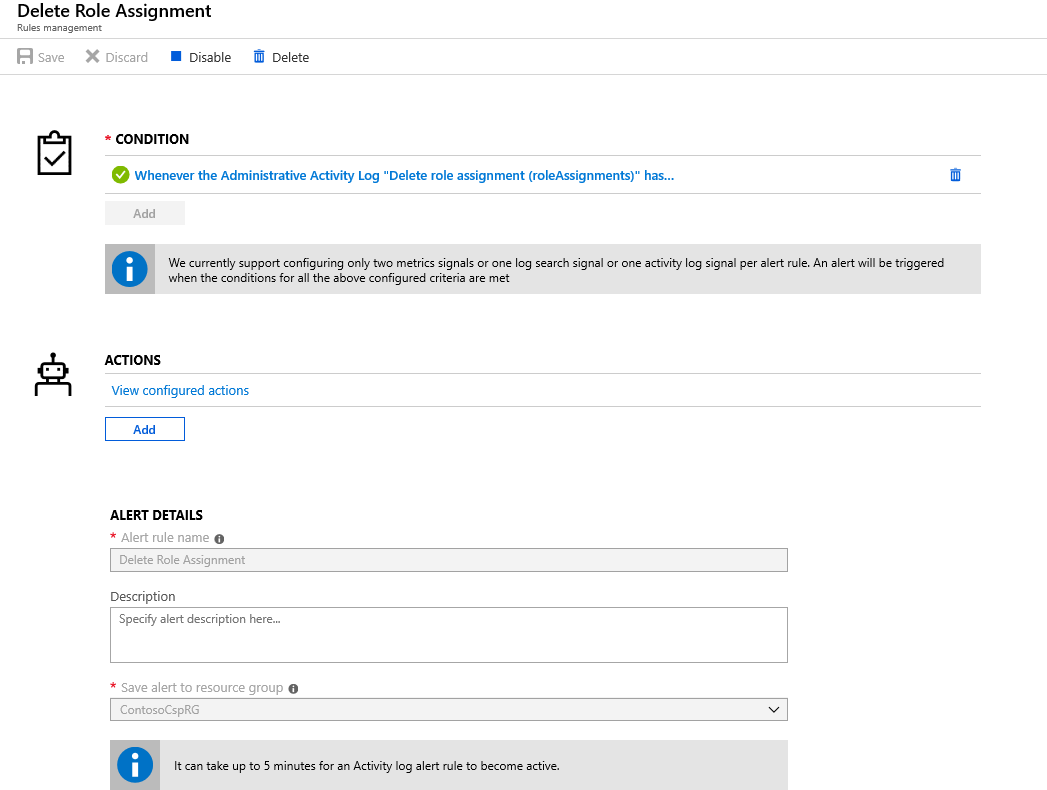
Create an Azure monitor alert
You can create an activity log Azure Monitor Alert to be notified if your RBAC access is removed from a CSP subscription.
To create an Azure monitor alert, use the following steps:
Select the type of action that you want the alert to take.
For example, if you specify that you want an email, you'll receive an email notifying you if any role assignment deletion occurs.
AOBO removal
Customers can manage access to their subscriptions by going to Access Control at the Azure portal. From the Role assignments tab, they can select Remove access.
If a customer removes your access, you can:
Talk with your customer to see if admin access can be reinstated.
Use the access provided through role-based access control (RBAC).
Use access provided through Azure Lighthouse.
Role-based access differs from admin access. Roles delimit precisely what you can and can't do. Admin access is broader.
To see the roles eligible to earn partner earned credit (PEC), see Roles and permissions for the partner earned credit.
Suspend and reactivate an Azure plan
Partners can suspend or reactivate Azure plan directly in Partner Center from the Azure plan details page.
- In Partner Center, in Customers, select the customer account
- Navigate to the customer's Azure subscriptions
- Select the Azure plan
- Select the Status: Suspended and then Submit to suspend the Azure plan.
- Select the Status: Active and then Submit to reactivate the Azure plan.
You can only suspend an existing Azure plan if it no longer has any active usage assets associated with it, including Azure usage subscriptions and Azure reservations.
Partners can only buy one Azure plan per specific reseller and customer combination. If a reseller's customer has a suspended plan, that customer can't purchase a new plan. Cancellation isn't available for Azure plan.
For Azure plan suspension by API, see Suspend a subscription - Partner app developer.
For Azure plan reactivation by API, see Reactivate a suspended subscription - Partner app developer.
Cancel an Azure subscription
In the event the customer's Azure plan subscriptions have been compromised, Partners can cancel Azure subscriptions from the Partner Center. This capability is available only to Global Administrators with Admin Agent roles. To do this:
- Select the Customer from the customer list
- Navigate to the customer's Azure subscriptions
- Select the Azure plan the subscription is under
- On the Azure plan details page, select the Azure subscriptions to cancel
- Submit the changes by selecting Cancel subscription
This cancels only the selected Azure subscriptions. Customers with access to the Azure subscription can reactivate the subscription if the Azure plan is still active. To stop this from happening, Partners should cancel all the Azure subscriptions and then the Azure plan itself.
Partners can multiselect the subscriptions but can't cancel more than 10 subscriptions at a time. Partners can cancel the Azure plan when there are no active Azure subscriptions under it. This enables partners to shut down Azure plans and subscriptions that might have been compromised, even if a bad actor has removed their RBAC permissions.
Partners can cancel Azure subscriptions through the Partner Center portal or by API. For API details, see Cancel an Azure subscription and to try it out, see Azure spending - Cancel an Azure entitlement - REST API.
To learn more about canceling Azure subscriptions, see What happens after subscription cancellation?
Reactivate an Azure subscription
Partners can reactivate Azure subscriptions that were canceled due to customer compromise from their Azure plan details page, using the Inactive Azure subscriptions tab. This capability is available only to Global Administrators with Admin Agent roles. To do this:
- Select the Customer from the customer list
- Navigate to the customer's Azure subscriptions
- Select the Azure plan the subscription is under
- On the Azure plan details page, under the Azure subscription section, select the Inactive tab
- Select the Azure subscription to reactivate
- Submit the changes by selecting Reactivate subscription
This reactivates only the selected Azure subscriptions. Partners can multiselect the subscriptions but can't reactivate more than 10 subscriptions at a time. The associated Azure plan must be active to reactivate Azure subscriptions. Partners can reactivate Azure plans directly in Partner Center by going to the Azure plan details page and updating the status of the Azure plan back to Active.
If the Azure subscription was canceled by the customer or billing owner in the Azure portal, the customer or billing owner will need to be contacted to reactivate the subscription from the Azure portal.
For reactivating by API, see Reactivate an Azure subscription - Partner app developer. To try it out, see Azure spending - Reactivate an Azure entitlement.
More on reactivating Azure subscriptions can be found in the Azure documentation.
Next steps
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for