Windows Vista
Protect Your PC with New Security Features in Windows Vista
Justin Harrison
At a Glance:
- Using Windows Security Center
- Configuring and managing User Account Control settings
- Scanning for spyware with Windows Defender
Several years ago, Microsoft Chairman (and then Chief Software Architect) Bill Gates called on employees to make trustworthy computing the company's highest priority. Along with this announcement came a series of changes in how Microsoft developed software.
Windows Vista™ is the first operating system fully developed under the guidelines of the Security Development Lifecycle (SDL), a security-focused engineering process meant to move security into the very essence of software design; all widely deployed Microsoft products must follow these guidelines. (For more information about the SDL, check out the book The Security Development Lifecycle by Michael Howard and Steve Lipner, Microsoft Press®, 2006).
Windows Vista also includes new or upgraded built-in security technologies that actively work to detect and prevent security threats. All of these changes mean that Windows Vista is the most secure Windows® release yet. In this article I'll discuss the new security Control Panel applet, Windows Security Center, and the built-in protection including Windows Defender, Windows Firewall, and User Account Control.
The Security Control Panel
When you open the Control Panel in Windows Vista you'll notice that it is arranged into ten areas of functionality, with most of the security-related applets spread between Security, Programs, and Network and Internet. You can use the Security applet to access many of the new security technologies that protect you in Windows Vista, as shown in Figure 1.
Figure 1 Security Technologies in Windows Vista
| Function | Description |
| Security Center | Check for updates; check security status; turn on automatic updating; check firewall status; require a password on wake up. |
| Windows Firewall | Turn Windows Firewall on or off; allow a program through Windows Firewall. |
| Windows Update | Turn on automatic updating; check for updates; view installed updates. |
| Windows Defender | Scan for spyware and other potentially unwanted software. |
| Internet Options | Change security settings; delete cookies; clear history. |
| Parental Controls | Set up parental controls for any user; view activity reports. |
| BitLocker Drive Encryption | Turn on BitLocker Drive Encryption. |
You can also check for Windows Updates, turn on BitLocker™ Drive Encryption, delete cookies, clear history, and set a password for your computer to send a prompt for when it wakes up.
The Security applet also makes it easy to access the Security Center, an all-in-one location you can use to manage and check the status of your computer's security settings and built-in protection.
Centralized Security
Until the arrival of the Security Center in Windows XP Service Pack 2 (SP2), dealing with all of the Windows security settings was difficult. Now, Security Center is all you need to manage important Windows security settings in one place, and it's even more useful in Windows Vista.
Windows Security Center runs in the background and actively monitors four categories of functionality, as shown in Figure 2: Firewall, Automatic updating, Malware (viruses and spyware) protection, and Other security settings (Internet and User Account Control settings).
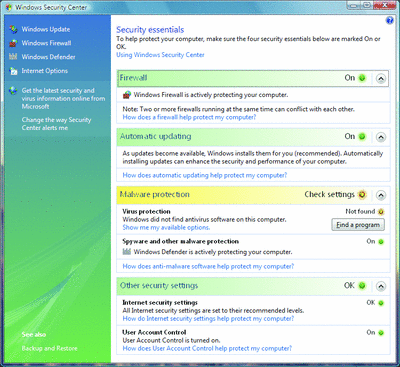
Figure 2** Manage Security Settings in One Place **(Click the image for a larger view)
With Windows Security Center, you can see which application is acting as your computer's firewall or anti-spyware and antivirus solution. You can also check the status of firewall, automatic update, and user account control settings. Windows Security Center is unique in that it monitors the status of third-party applications in addition to built-in Windows technologies. It checks for the following items:
- Whether a firewall is installed and whether it is turned on.
- Whether an antivirus program is installed and if the definitions are up to date and real-time scanning is enabled.
- Whether an anti-spyware program is installed and if the definitions are up to date and real-time scanning is enabled.
Windows Security Center uses two approaches to detect third-party antivirus and firewall applications. In manual mode, Windows Security Center searches for registry keys and files that let it detect the status of the software. It also queries Windows Management Instrumentation (WMI) providers made available by participating vendors that return the status of features. This means you can use non-Microsoft solutions for antivirus, anti-spyware, or firewall issues and still use Windows Security Center to monitor and protect your computer.
Windows Security Center can be controlled by Group Policy. By default, it is disabled in domain environments. To turn on Windows Security Center, access the Computer Configuration\Administrative Templates\Windows Components\Security Center node. The name of the policy to turn it on is Turn on Security Center (Domain PCs only).
Windows Security Center also monitors the status of User Account Control settings and Internet security settings. User Account Control lets you use your computer as a standard user rather than as an administrator, which is much safer. As a standard user, any changes you make can't affect the entire system and any software you install can only do so much damage.
In Windows Vista, if you are running as a standard user on a computer that is not part of a domain and software needs to perform an action that affects the entire system, the OS prompts for the password of an administrator account. If you are running as an administrator, Windows Vista prompts for permission to execute the system-wide action so that you are aware of (and consent to) the action before it takes place.
User Account Control is managed by Group Policy in a domain environment. If your computer is not part of a domain, it is handled by Local Security Policy. Policy settings are found under Computer Configuration\System Settings\Local Policies\Security Options in the Local Security Policy editor or Group Policy editor. You'll find the Local Security Policy editor in Control Panel under System and Maintenance | Administrative Tools.
As Figure 3 shows, Windows Security Center watches a number of Internet security options.
Figure 3 Internet Security Settings
| Windows Security Center monitors these Internet settings: |
| Download signed ActiveX controls |
| Download unsigned ActiveX controls |
| Initialize script and ActiveX controls not marked as safe for scripting |
| Installation of desktop items |
| Launching applications and unsafe files |
| Launching programs and files in an IFRAME |
| Software channel permissions |
If an option changes to a state that is not secure, the Internet Properties dialog indicates "Your security settings put your computer at risk" and Microsoft Internet Explorer® will show an information bar that says "Your current security settings put your computer at risk. Click here to change your security settings..." Windows Security Center also notifies you that "You're not using recommended security settings." If you open Internet Security Settings, the unsecure settings will be highlighted in red (see Figure 4).
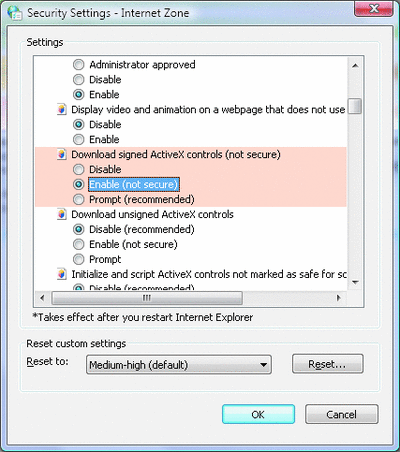
Figure 4** An Unsecure Setting Highlighted **(Click the image for a larger view)
Windows Security Center can restore unsecure security settings to a secure state. You do this by clicking Restore my Internet security settings now, as shown in Figure 5.

Figure 5** Eliminating a Risky Setting **(Click the image for a larger view)
Windows Defender
Rootkits, trojans, spyware, and other malicious software have become a huge problem. They put your information at risk, decrease your computer's performance, and can cause system crashes. Microsoft acquired Giant Software in 2004 to provide anti-spyware technology to protect customers. You can find this new technology built into Windows Vista as Windows Defender (which is also available as a download for Windows XP).
After installing Windows Vista, you don't need to change any of your Windows Defender settings immediately. Since Windows Defender comes configured to provide maximum security with minimal interruption, you can focus on using your computer rather than securing it. Windows Defender provides real-time protection as soon as it is started, and it will automatically check for and download updated spyware definitions every night around 2 A.M., and automatically remove all high-threat risks. You can adjust the settings by selecting Tools | General Settings in Windows Defender.
Real-time protection means that Windows Defender carefully watches for suspicious behavior on your computer at all times. It uses the nine security agents listed in Figure 6 to monitor different parts of your system for application behavior that is characteristic of spyware. Together, the Windows Defender security agents monitor almost all common entry points of spyware.
Figure 6 Windows Defender Security Agents
| Agent | Monitors |
| Internet Explorer configuration | Browser security settings. |
| Internet Explorer downloads | Applications that work with Internet Explorer, such as ActiveX controls and software installation applications. |
| Internet Explorer add-ons (browser helper objects) | Applications that automatically run when you start Internet Explorer. |
| Auto Start | Applications that start when Windows starts, including applications that start via the registry and the Windows start-up folder. |
| System configuration | Security-related settings in Windows. |
| Services and drivers | Services and drivers as they interact with Windows and applications. |
| Windows add-ons | Software utilities that integrate with Windows. |
| Application execution | Applications when they start, and their execution. |
| Application registration (API hooks) | Files and tools in the operating system where applications can insert themselves to run. |
Threat Response
Windows Defender alerts you when it finds potentially unwanted software or detects suspicious behavior. When innocuous (low threat) changes occur, Windows Defender lets you know by displaying an exclamation point in the system tray. For more severe threats (medium or high), Windows Defender displays a yellow or red dialog depending upon the threat level, as shown in Figure 7. These kinds of threats require an immediate response.
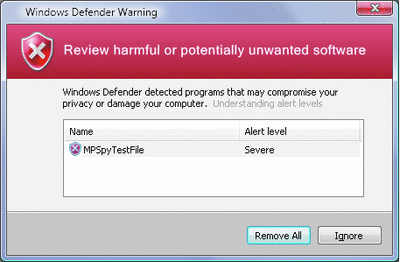
Figure 7** Red Window Indicates High-Level Threat **(Click the image for a larger view)
All actions Windows Defender performs are logged in the System Event Log with source "Windows Defender". Such actions include definition updates and spyware scans and removals.
Windows Defender threat alerts are intelligent, so you can continue working through them. Multiple threats can be listed and you can choose to respond to all threats ("Remove All") in a threat-alert dialog. You can also configure threat alerts to react differently based upon unclassified threats and known software that is allowed to run. To configure threat alerts, open Windows Defender and click Tools | Options. Scroll down to "Real-time protection options" and choose whether Windows Defender should notify you about software that hasn't yet been classified for risks and about changes made to your computer by software that is allowed to run.
Note that if an application you've created or an application you use is being incorrectly classified by Windows Defender, you can file a vendor dispute at microsoft.com/athome/security/spyware/software/isv/cdform.aspx. If the application is being mistaken for spyware, you can report a false positive at microsoft.com/athome/security/spyware/software/isv/fpform.aspx.
Protection On Demand
Windows Defender watches carefully for potentially unwanted software, but you can also start spyware scans whenever you think it's necessary. Windows Defender offers three types of scans:
- A Quick Scan rapidly checks places on your computer that spyware is most likely to infect.
- A Full Scan scans all files on your hard disk, running applications, the registry, and other places.
- A Custom Scan lets you scan specific files or folders; it automatically runs a Quick Scan when it begins.
To initiate a scan, start Windows Defender and click the down arrow next to the Scan button; then select the type of scan you'd like to start, as shown in Figure 8.
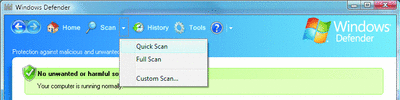
Figure 8** Choose the Type of Scan **(Click the image for a larger view)
When Windows Defender detects a threat during a scan, it displays a description of the threat and actions you can take to resolve the threat. By default, it displays the best action to take. If multiple threats are found, you can select responses and apply them all at once by clicking Apply Actions, or you can remove all threats by clicking Remove All. Among the actions you can take are:
- Remove—Remove the threat from your system completely.
- Ignore—Ignore the threat. The next time you scan, Windows Defender will detect the threat again.
- Quarantine—Temporarily disables the threat. You can use this to test whether removing the threat has any ill affects on your system. You can always restore it from inside Windows Defender.
- Always allow—Stop detecting the threat and add it to the allowed items list. You can remove items from the allowed items list by clicking Tools | Options in Windows Defender.
Preventing Network Intrusion
Windows Firewall in Windows Vista is a bidirectional stateful firewall that contains many advances over the Windows XP version. In Windows Vista, Windows Firewall filters both incoming and outgoing traffic. Rules can also be configured for:
- Active Directory accounts and groups
- IP protocol number
- Specific types of interfaces
- Services
- ICMP and ICMPv6 by type and code
- Source and destination IP addresses
- All TCP or UDP ports, or specified ports
In Windows Vista, you can also allow a specific program access to the network or deny traffic through the Exceptions list. To access the Exceptions list, click Start | Control Panel | Security, and then Allow a program through Windows Firewall.
By default Windows Firewall blocks all incoming traffic unless it is solicited or matches a rule, and allows all outgoing traffic unless it matches a rule.
Windows Vista comes with a new Microsoft Management Console (MMC) snap-in called Windows Firewall and Advanced Security (see Figure 9), which lets administrators configure Windows Firewall settings on remote computers. To access the new snap-in, click System and Maintenance and then Administrative Tools in Control Panel, then click Windows Firewall with Advanced Security.

Figure 9** Create Advanced Rules to Protect Your Computer from Network Threats **(Click the image for a larger view)
To add a rule, you can also use the Group Policy editor snap-in to access Computer Configuration\Windows Settings\Security Settings\Windows Firewall with Advanced Security. You can even configure new Advanced Security settings from the command line using netsh advfirewall.
Each time you connect to a new network, Windows Vista creates a profile just for that network. When you connect to the network again, Windows Vista uses the saved settings from that profile. One of the first things that the OS asks when you connect to a new network is whether it is a public or private network. This determines what profile Windows Firewall loads for configuration and rules. If you want to edit the profiles, click Windows Firewall Properties in the Windows Firewall with Advanced Security snap-in, then click either the Private Profile or Public Profile tab, as shown in Figure 10.
If you like, you can change the profile associated with a network after you connect to it from the Network and Sharing Center. To do so, go to Control Panel | Network and Internet | Network and Sharing Center). To change the network profile, click Customize next to the name of the network to which you are connected.
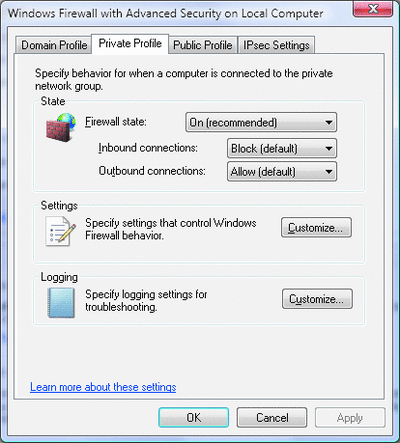
Figure 10** Customize Protection Based on Network Type **(Click the image for a larger view)
Conclusion
Windows Vista is the first complete operating system release since the trustworthy computing initiative announcement several years ago. Developed under the guidelines of the Security Development Lifecycle and with built-in protection such as Windows Defender, Windows Firewall, and User Account Control, Windows Vista offers unparalleled protection both for standalone systems and for those that are part of a domain. Windows Security Center, Windows Firewall and User Account Control all offer Group Policy configuration that enables you to deploy them effectively in your domain environment or configure them very extensively locally on your personal computer.
The SpyNet Community
Security threats are ever changing and sometimes even daily updates are not enough to keep up with all of the security threats your computer might encounter. For even more protection than providing spyware definition updates, Microsoft also brings users together in the SpyNet Community, an online group that shares information about spyware.
The Spynet Community is a voluntary worldwide community of Windows Defender users that report spyware findings to Microsoft. Users who participate in this community play an important role in determining what suspicious applications are eventually classified as spyware, and they also help discover new threats quickly so all Windows Defender users are better protected.
The SpyNet Community is opt-in. You must explicitly decide to participate. You can choose not to become a member, in which case no information about your possible spyware infections is sent to SpyNet. You will not be notified if unclassified, potentially unwanted software is found on your computer. The unclassified, potentially unwanted software may eventually be classified in the regular spyware definition updates.
If you choose to participate, there are two levels of membership:
Advanced membership. Participants send information to Microsoft about unclassified software and actions taken. Advanced participants are alerted of currently unclassified software that may not be safe. Some personal information may be sent, but Microsoft will not use it to contact you.
Advanced Members receive removal statistics showing how other advanced members reacted to the same threat. This information can help you make a decision whether or not currently unclassified potentially unwanted software is dangerous. For example, if a new application is being distributed on the Internet and Windows Defender detects it as being suspicious, some advanced users may report it to SpyNet and remove it. SpyNet will tell you how many Advanced Members reported and removed it, so that you can use the information to make a better decision on what you should do.
Basic membership. Basic information about suspicious software is sent to Microsoft. Personal information may also be sent, but Microsoft will not use it to contact you. Basic participants are not alerted about unclassified software.
To join the Spynet Community, open Windows Defender and select Tools, then click Microsoft SpyNet.
Justin Harrison Justin Harrison (justin@harrison.org) is an expert in Windows security, digital media technology, and digital documents. He has worked for GE Energy and the Digital Documents team and the Casual Games team at Microsoft.
© 2008 Microsoft Corporation and CMP Media, LLC. All rights reserved; reproduction in part or in whole without permission is prohibited.