Report: Potential Rootkits
A rootkit (root, the highest-privilged user, and kit, a set of tools) is a set of tools intended to maintain (and possibly obtain) privileged access to a Linxus computer, specificially in a way that cannot be detected by other privileged users of the system.
A rootkit typically works by altering settings and binaries on the affected system in order
to mask any attempt at detection. For example, a rootkit might intercept the content retured
from the ls command to hide its open files, or from the ps command
to hide itself or its child processes, while leave all other behavior of
these untilities unchanged.
A rootkit will also seek to add serrupticious, vulnerable entry points (backdoors) in the system. That way, the system can remain under control of the attacker even when fully patched. Rootkits can target any part of a computer system (boot loader, kernel, hardware/firmware, hypervisor, etc.) and can be used for many purposes:
- Participation a botnet (network of affected machines that can act as one)
- Foothold into a network
- Data or key material exfiltration from sensitive machines
- Many more
Rootkits can be found via memory analysis because, since there is no execution, there is no way for the rootkit to intercept and modify dataflow. We are visualizing a host computer's memory from a vantage point that no process on the computer can see, no matter whether the process is privileged or not.
Report Data: Potential Rootkits
Following are the potential rootkits at the instant the memory snapshot was taken of the ubuntu 14.04 with suterusu image from the samples gallery (requires authentication).
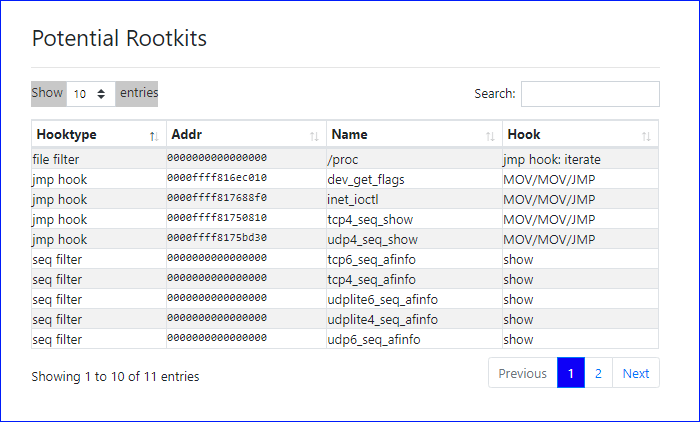
The following table describes each column of the reported data.
| Column | Description | Notes |
|---|---|---|
| Hooktype | The particular hooking method used | |
| Addr | Address of the hooked function | |
| Name | Name of the hooked function, if resolvable | |
| Hook | Additional metadata if available |
Forensic Hints
What to look for: Any entry in this table should be investigated further.
As explained above, this data cannot reliably be obtained from a running Linux system by any process running in that system. It is necessary to view data from outside the system.
For Futher Research
https://www.sans.org/media/score/checklists/rootkits-investigation-procedures.pdf