Authorization_RequestDenied error when you try to change a password using Graph API
This article provides information about troubleshooting a problem in which you receive Authorization_RequestDenied error when trying to change a password using Graph API.
Original product version: Microsoft Entra ID
Original KB number: 3004133
Symptoms
You try to change the password of a Microsoft Entra user. If the Organizational Role setting for that user is set to any "Administrator" option, the process fails. It generates the following error message:
{"odata.error":{"code":"Authorization_RequestDenied","message":{"lang":"en","value":"Insufficient privileges to complete the operation." }} }
When you give the Read and write directory data permission to your application or Application Service Principal, the application can change the password of a typical Microsoft Entra user by using Graph API. This setting is shown in the following screenshot.
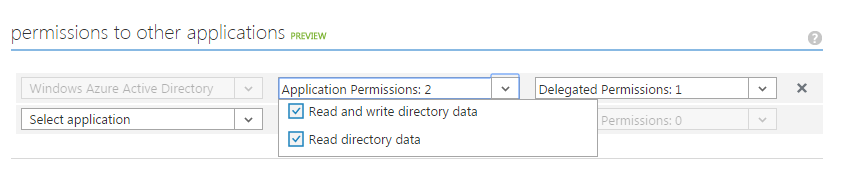
You can delegate a Microsoft Entra user as an administrator by changing the user's Organizational Role setting, as shown in the following screenshot.
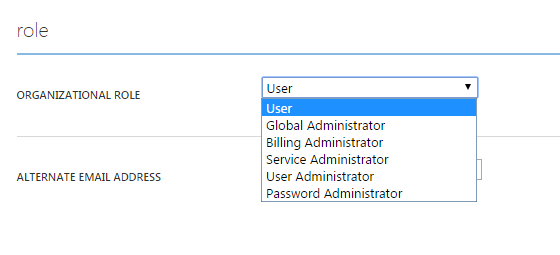
Cause
This problem occurs because the users who have any of the Administrator organizational roles aren't members of Company Administrator or User Account Administrator in the Office 365 administrative roles.
Resolution
Note
Azure AD and MSOnline PowerShell modules are deprecated as of March 30, 2024. To learn more, read the deprecation update. After this date, support for these modules are limited to migration assistance to Microsoft Graph PowerShell SDK and security fixes. The deprecated modules will continue to function through March, 30 2025.
We recommend migrating to Microsoft Graph PowerShell to interact with Microsoft Entra ID (formerly Azure AD). For common migration questions, refer to the Migration FAQ. Note: Versions 1.0.x of MSOnline may experience disruption after June 30, 2024.
To resolve this problem, add your application to Company Administrator in the Office 365 administrative roles. To do so, run all the following Azure AD module for Windows PowerShell (MSOL) cmdlets:
Connect-MsolService
It will prompt you for your tenant's credential. You should be able to use your Microsoft Entra administrative user name in the admin@tenant.onmicrosoft.com format.
$displayName = "Application Name"
$objectId = (Get-MsolServicePrincipal -SearchString $displayName).ObjectId
Replace the "Application Name" with the name of your "Application Service Principal".
$roleName = "Company Administrator"
Add-MsolRoleMember -RoleName $roleName -RoleMemberType ServicePrincipal -RoleMemberObjectId $objectId
It will add your "Application Service Principal" to the Company Administrator role.
Also, you must add your application to User Account Administrator in the Office 365 administrative roles if the Microsoft Entra user has any of the following Administrator organizational roles:
- Global Administrator
- Billing Administrator
- Service Administrator
To do so, run all the following MSOL cmdlets:
Connect-MsolService
$displayName = "Application Name"
$objectId = (Get-MsolServicePrincipal -SearchString $displayName).ObjectId
$roleName = "User Account Administrator"
Add-MsolRoleMember -RoleName $roleName -RoleMemberType ServicePrincipal -RoleMemberObjectId $objectId
After you run both sets of cmdlets, your application will be enabled to change the password of all Administrator organizational roles.
Note
It can take up to 30 minutes for the permissions to be applied to the Application Service Principal after you add the permissions to the Office 365 administrative roles.
Contact us for help
If you have questions or need help, create a support request, or ask Azure community support. You can also submit product feedback to Azure feedback community.
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for