SCEP certificate request fails during the verification phase on the CRP
This article gives two methods to help resolve when a Simple Certificate Enrollment Protocol (SCEP) certificate request fails during verification.
Symptoms
The SCEP certificate request fails during the verification phase on the certificate registration point (CRP). Therefore, Android and iOS devices do not receive SCEP certificates even though NDES is configured.
Additionally, you see error entries in CRP logs.
Note
The default log file location is:
C:\Program Files\Microsoft Intune\NDESConnectorSvc\Logs\Logs\CertificateRegistrationPoint_xx_xx.svclog
Three log entries specify a Cryptography Exception error, as shown in the following image.
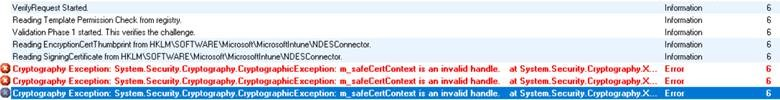
First error entry
<Source Name="CertificateRegistrationPoint" />
Cryptography Exception: System.Security.Cryptography.CryptographicException: m_safeCertContext is an invalid handle.
at System.Security.Cryptography.X509Certificates.X509Certificate.ThrowIfContextInvalid()
at System.Security.Cryptography.X509Certificates.X509Certificate.SetThumbprint()
at System.Security.Cryptography.X509Certificates.X509Certificate.GetCertHashString()
at Microsoft.ConfigurationManager.CertRegPoint.Helper.ValidateChallenge(String base64Encodedtoken, X509Certificate2Collection encryptedCerts, X509Certificate2 SigningCert, String& decodedChallengePassword)
Second error entry
Cryptography Exception: System.Security.Cryptography.CryptographicException: m_safeCertContext is an invalid handle.
at System.Security.Cryptography.X509Certificates.X509Certificate.ThrowIfContextInvalid()
at System.Security.Cryptography.X509Certificates.X509Certificate.SetThumbprint()
at System.Security.Cryptography.X509Certificates.X509Certificate.GetCertHashString()
at Microsoft.ConfigurationManager.CertRegPoint.Helper.ValidateChallenge(String base64Encodedtoken, X509Certificate2Collection encryptedCerts, X509Certificate2 SigningCert, String& decodedChallengePassword)
at Microsoft.ConfigurationManager.CertRegPoint.ChallengeValidation.ValidationPhase1(VerifyChallengeParams value, String& decodedChallenge, PKCSDecodedObject& pkcsObj)
Third error entry
Cryptography Exception: System.Security.Cryptography.CryptographicException: m_safeCertContext is an invalid handle.
at System.Security.Cryptography.X509Certificates.X509Certificate.ThrowIfContextInvalid()
at System.Security.Cryptography.X509Certificates.X509Certificate.SetThumbprint()
at System.Security.Cryptography.X509Certificates.X509Certificate.GetCertHashString()
at Microsoft.ConfigurationManager.CertRegPoint.Helper.ValidateChallenge(String base64Encodedtoken, X509Certificate2Collection encryptedCerts, X509Certificate2 SigningCert, String& decodedChallengePassword)
at Microsoft.ConfigurationManager.CertRegPoint.ChallengeValidation.ValidationPhase1(VerifyChallengeParams value, String& decodedChallenge, PKCSDecodedObject& pkcsObj)
at Microsoft.ConfigurationManager.CertRegPoint.Controllers.CertificateController.VerifyRequest(VerifyChallengeParams value)
Cause
This issue occurs because the registry keys that are responsible for verification of the certificate request are missing in NDES connector registry settings.
Solution 1
Complete these steps to restart the Intune Connector Service:
On the connector-installed server, open the Services snap-in. To do this, open the Start menu, enter
services.msc, and then select Services from the results list.In the Services snap-in, restart the Intune Connector Service.
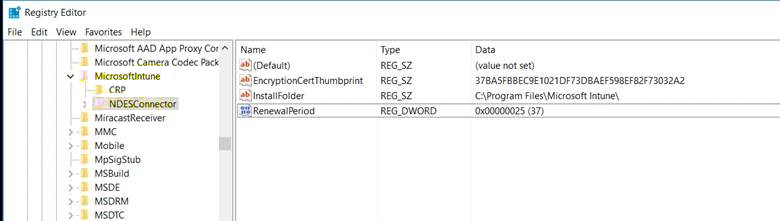
Check the
HKLM\Software\Microsoft\MicrosoftIntune\NDESConnectorregistry subkey to verify that the registry keys were created according to the following screenshot.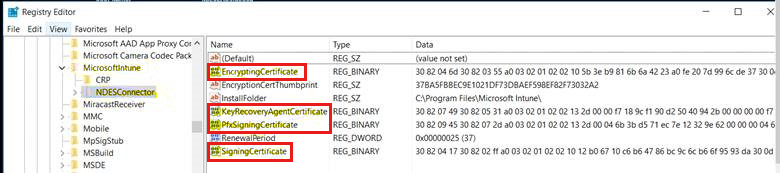
If restarting the service or computer does not fix the issue, continue to Solution 2.
Solution 2
Complete these steps to clear and reset the template name:
On the NDES computer, open the registry, and locate the following subkey:
HKEY_LOCAL_Machine\Software\Microsoft\Cryptography\MSCEPChange the template values to the default (IPSECIntermediateOffline), and restart the server.
After the server restarts, check the
HKEY_LOCAL_Machine\Software\Microsoft\MicrosoftIntune\NDESConnectorsubkey. You should now see the signing certificates.After the keys are created, change the template name under
HKEY_LOCAL_Machine\Software\Microsoft\Cryptography\MSCEPto the custom template name that was created for SCEP and NDES.
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for