Authenticate users with Azure Mobile Apps or the Active Directory Authentication Library for Cordova
Security is a very broad topic that covers a number of different aspects of an app's lifecycle. Securing an app often represents a number of tradeoffs and key decisions. For the most part you should apply the same best practices to your code as you do for web apps. However, given the increased capabilities Cordova apps are afforded, it is important to limit your risk as much as possible.
A critical task for application security is authenticating and authorizing users accessing your app and its associated local or remote data. In this article we'll touch on some options that can help get you get auth up and running.
Azure App Service Auth and Azure Mobile Apps
Azure App Service is a suite of services designed to help you build great web and mobile apps. Azure Mobile Apps are mobile integrated client apps that take advantage of features within the broader Azure App Service including Web Apps and API Apps along with some additional useful features and client libraries.
A core first step in accessing all of these great services, however, is authorizing users both to access the app for the app to then access data in the cloud. Fortunately, the Cordova plugin for Azure Mobile Apps has an unified authentication interface that currently supports authenticating against Azure Active Directory, Facebook, Google, Twitter, and Microsoft accounts. The unified interface means that you're abstracted from downstream changes and can expect additional provider options and features in the future to streamline things even more.
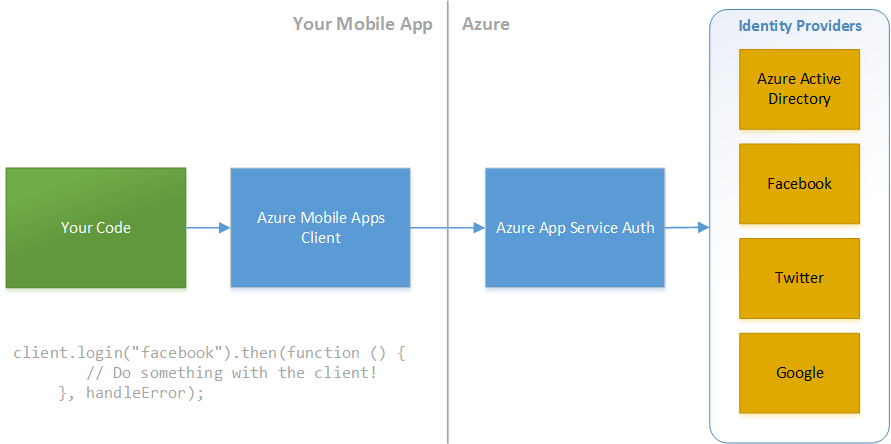
You can add the Azure Mobile Apps plugin your app as follows:
Visual Studio Tools for Apache Cordova Update 8 and up, simply click "Add" on the Azure Mobile Apps plugin in the config.xml designer.
When using the command line or Visual Studio Code, you can add the plugin using the Cordova CLI as follows:
cordova plugin add cordova-plugin-ms-azure-mobile-apps --save
Note that you can also get basic information about the user logged in by making a REST call to the /.auth/me service endpoint and passing the appropriate auth token. See the Azure Mobile Apps authentication documentation and the article on securely transmitting data for additional details on token passing.
Try the Azure connected services sample app
To get the sample, find the Azure connected services sample on GitHub.
Then follow these steps:
Download the sample and open it in Visual Studio.
On the Azure portal, create an Azure Mobile App backend. Follow steps in this video to create the Azure Mobile App backend. You will need to create an Azure account if you don't have one.
For documentation that shows similar steps, see the Getting Started Tutorial. You can skip the section on downloading the client app.
Note: You can follow steps described in the Getting Started Tutorial to download the Azure sample, but if you use the getting started sample instead of the Azure connected services sample, you must take extra steps to add required plugins, to add login code, and to update the Cordova version in your app.
Watch this video to add authentication to the Azure connected services sample. The video shows adding authentication with Twitter, but steps are similar for other services as well.
To follow similar steps in the tutorial, see How to: Authenticate users
Update code in the login callback function.
If you're not using push notifications, comment out this code.
// Added to register for push notifications. registerForPushNotifications();
Active Directory Authentication Library for Cordova
Active Directory (AD) provides an industry leading identity server both in the cloud and on-premises through Azure Active Directory (AAD) and Active Directory Federation Services (ADFS). You can securely authenticate, authorize, access information in AD, and take advantage of device level single sign on and multi-factor authentication (MFA) capabilities through the powerful Active Directory Authentication Library (ADAL) available for all major native and cross-platform mobile and server side technologies.
For Cordova this functionality is provided via the ADAL plugin which can be used both with AAD and on-premises ADFS v3 and up. Note that the ADAL plugin is activley maintained but currently in preview. It uses the Android, iOS, and .NET ADAL native libraries under the covers and therefore persists auth tokens in a secure cache that you can then query to pass to downstream services.
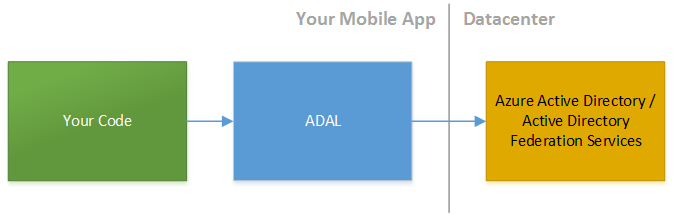
Adding the plugin is easy.
In Visual Studio, simply click "Add" on the ADAL for Cordova plugin in the config.xml designer.
When using the command line or Visual Studio Code, you can add the plugin using the Cordova CLI as follows:
cordova plugin add cordova-plugin-ms-adal --save
See the Active Directory Quick Start for Cordova for additional details on setup. You can also read this blog post on some of the internals and the advantages it provides over other methods.
While the quick start uses Azure AD, the plugin also works with ADFS v3 and up by simply changing the authority and redirect URIs to the appropriate ones for your ADFS installation.
The quick start also has code that demonstrates calling the Azure AD Graph REST API directly using an AD token from the plugin. This approach can be reused across Azure services and O365 services. See the article on securely transmitting data along with documentation on Azure JSON based REST APIs and O365 for additional details on token passing to downstream services.
JavaScript & 3rd Party Options
Cordova also can take advantage of pure JavaScript based solutions to authenticate against Oauth providers thanks to the InAppBrowser plugin. See this article for an excellent overview on the general approach JavaScript based solutions take. These options can be useful when client libraries are not available. The ngCordovaOauth library encapsulates this approach to allow you to target an impressive array of different Oauth providors including on-prem ADFS. However, in general we recommend using provider Cordova plugins, the ADAL plugin, or Azure when security is of paramount concern.
If neither of the above options meet your needs, there are a number of 3rd party solutions that may be of use. First note that many Single Sign-On (SSO) solutions including Auth0 actually explictly support PhoneGap/Cordova in their JavaScript client libraries or related Cordova plugins. If you already have a SSO provider, be sure to check with them to see what best practices they provide for Cordova apps.

