Grant or restrict access using permissions
Azure DevOps Services | Azure DevOps Server 2022 - Azure DevOps Server 2019
You can grant or restrict access to resources that you manage in Azure DevOps. You may want to open up or close down access to a select set of features and for a select set of users. While the built-in security groups provide a standard set of permission assignments, you may need more security requirements not met by these assignments.
If you're new to administrating permissions and groups, review Get started with permissions, access, and security groups to learn about permission states and inheritance.
In this article you learn how to do the following tasks:
- Recommended method for granting and restricting permissions
- Delegate tasks by assigning select permissions to specific roles
- Limit user visibility to organization information
- Limit people picker to project users and groups
- Restrict access to view or modify objects
- Restrict modification of work items based on a user or group
- Recommended method for granting and restricting permissions
- Delegate tasks by assigning select permissions to specific roles
- Restrict access to view or modify objects
- Restrict modification of work items based on a user or group
Tip
Because you set many permissions at an object-level, such as repositories and area paths, how you structure your project determines the areas you can open up or close down.
Recommended method for granting and restricting permissions
For maintenance purposes, we recommend you use either the built-in security groups or custom security groups to manage permissions.
You can't change the permission settings for the Project Administrators group or the Project Collection Administrators group, which is by design. However, for all other groups, you can change the permissions.
If you manage a few users, then you may find changing individual permissions a valid option. However, custom security groups allow you to better track roles and permissions assigned to those roles.
Delegate tasks to specific roles
As an administrator or account owner, it's a good idea to delegate administrative tasks to those team members who lead or manage an area. Several of the main built-in roles that come with default permissions and role assignments are:
- Readers
- Contributors
- Team Administrator (role)
- Project Administrators
- Project Collection Administrators
For a summary of permissions for the above roles, see Default permissions and access, or for the Project Collection Administrators, see Change project collection-level permissions.
To delegate tasks to other members within your organization, consider creating a custom security group and then granting permissions as indicated in the following table.
Role
Tasks to perform
Permissions to set to Allow
Development lead (Git)
Manage branch policies
Edit policies, Force push, and Manage permissions
See Set branch permissions.
Development lead (TFVC)
Manage repository and branches
Administer labels, Manage branch, and Manage permissions
See Set TFVC repository permissions.
Software architect (Git)
Manage repositories
Create repositories, Force push, and Manage permissions
See Set Git repository permissions
Team administrators
Add area paths for their team
Add shared queries for their team
Create child nodes, Delete this node, Edit this node
See Create child nodes, modify work items under an area path
Contribute, Delete, Manage permissions (for a query folder), See Set query permissions.
Contributors
Add shared queries under a query folder, Contribute to dashboards
Contribute, Delete (for a query folder), See Set query permissions
View, Edit, and Manage dashboards, See Set dashboard permissions.
Project or product manager
Add area paths, iteration paths, and shared queries
Delete and restore work items, Move work items out of this project, Permanently delete work items
Edit project-level information, See Change project-level permissions.
Process template manager (Inheritance process model)
Work tracking customization
Administer process permissions, Create new projects, Create process, Delete field from account, Delete process, Delete project, Edit process
See Change project collection-level permissions.
Process template manager (Hosted XML process model)
Work tracking customization
Edit collection-level information, See Change project collection-level permissions.
Project management (On-premises XML process model)
Work tracking customization
Edit project-level information, See Change project-level permissions.
Permissions manager
Manage permissions for a project, account, or collection
For a project, Edit project-level information
For an account or collection, Edit instance-level (or collection-level) information
To understand the scope of these permissions, see Permission lookup guide. To request a change in permissions, See Request an increase in permission levels.
You can also grant permissions to manage permissions for the following objects:
Limit user visibility to organization and project information
Important
- The limited visibility features described in this section apply only to interactions through the web portal. With the REST APIs or
azure devopsCLI commands, project members can access the restricted data. - Guest users who are members in the limited group with default access in Microsoft Entra ID, can't search for users with the people picker. When the preview feature's turned off for the organization, or when guest users aren't members of the limited group, guest users can search all Microsoft Entra users, as expected.
By default, users added to an organization can view all organization and project information and settings. To restrict access to only those projects that you add users to, you can enable the Limit user visibility and collaboration to specific projects preview feature for the organization. For more information, see Manage preview features.
With this feature enabled, users added to the Project-Scoped Users group can't view most Organization settings and can only connect to those projects to which they've been added.
Warning
When the Limit user visibility and collaboration to specific projects preview feature is enabled for the organization, project-scoped users are unable to search for users who were added to the organization through Microsoft Entra group membership, rather than through an explicit user invitation. This is an unexpected behavior and a resolution is being worked on. To self-resolve this issue, disable the Limit user visibility and collaboration to specific projects preview feature for the organization.
Limit people picker to project users and groups
For organizations that manage their users and groups using Microsoft Entra ID, people pickers support searching all users and groups added to Microsoft Entra ID, not just those users or groups added to a project. People pickers support the following Azure DevOps functions:
- Selection of a user identity from a work tracking identity field such as Assigned To
- Selection of a user or group using @mention in a work item discussion or rich-text field, a pull request discussion, commit comments, or changeset or shelveset comments
- Selection of a user or group using @mention from a wiki page
As shown in the following image, you simply start typing into a people picker box until you find a match to a user name or security group.
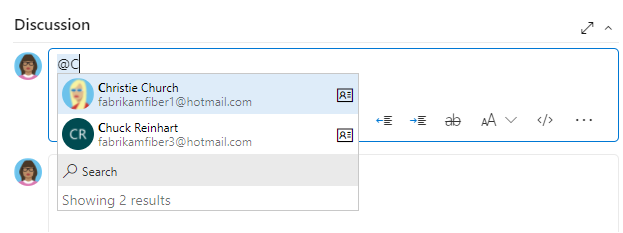
Users and groups who are added to the Project-Scoped Users group can only see and select users and groups in the project they're connected to from a people picker. To scope people pickers for all project members, see Manage your organization, Limit identity search and selection.
Restrict access to view or modify objects
Azure DevOps is designed to enable all valid users to view all objects defined in the system. You can restrict access to resources by setting the permission state to Deny. You can set permissions for members that belong to a custom security group or for an individual user. To learn more about how to set these types of permissions, see Request an increase in permission levels.
Area to restrict
Permissions to set to Deny
View or contribute to a repository
View, Contribute
See Set Git repository permissions or Set TFVC repository permissions.
View, create, or modify work items within an area path
Edit work items in this node, View work items in this node
See Set permissions and access for work tracking, Modify work items under an area path.
View or update select build and release pipelines
Edit build pipeline, View build pipeline
Edit release pipeline, View release pipeline
You set these permissions at the object level. See Set build and release permissions.
Edit a dashboard
View dashboards
See Set dashboard permissions.
Restrict modification of work items or select fields
For examples that illustrate how to restrict modification of work items or select fields, see Sample rule scenarios.
Next steps
Related articles
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for