Security recommendations
Applies to:
- Microsoft Defender Vulnerability Management
- Microsoft Defender for Endpoint Plan 2
- Microsoft Defender XDR
- Microsoft Defender for Servers Plan 1 & 2
Tip
Did you know you can try all the features in Microsoft Defender Vulnerability Management for free? Find out how to sign up for a free trial.
Cybersecurity weaknesses identified in your organization are mapped to actionable security recommendations and prioritized by their impact. Prioritized recommendations help shorten the time to mitigate or remediate vulnerabilities and drive compliance.
Each security recommendation includes actionable remediation steps. To help with task management, the recommendation can also be sent using Microsoft Intune and Microsoft Endpoint Configuration Manager. When the threat landscape changes, the recommendation also changes as it continuously collects information from your environment.
Tip
To get emails about new vulnerability events, see Configure vulnerability email notifications in Microsoft Defender for Endpoint
How it works
Each device in the organization is scored based on three important factors to help customers to focus on the right things at the right time.
- Threat: Characteristics of the vulnerabilities and exploits in your organizations' devices and breach history. Based on these factors, the security recommendations show the corresponding links to active alerts, ongoing threat campaigns, and their corresponding threat analytic reports.
- Breach likelihood: Your organization's security posture and resilience against threats.
- Business value: Your organization's assets, critical processes, and intellectual properties.
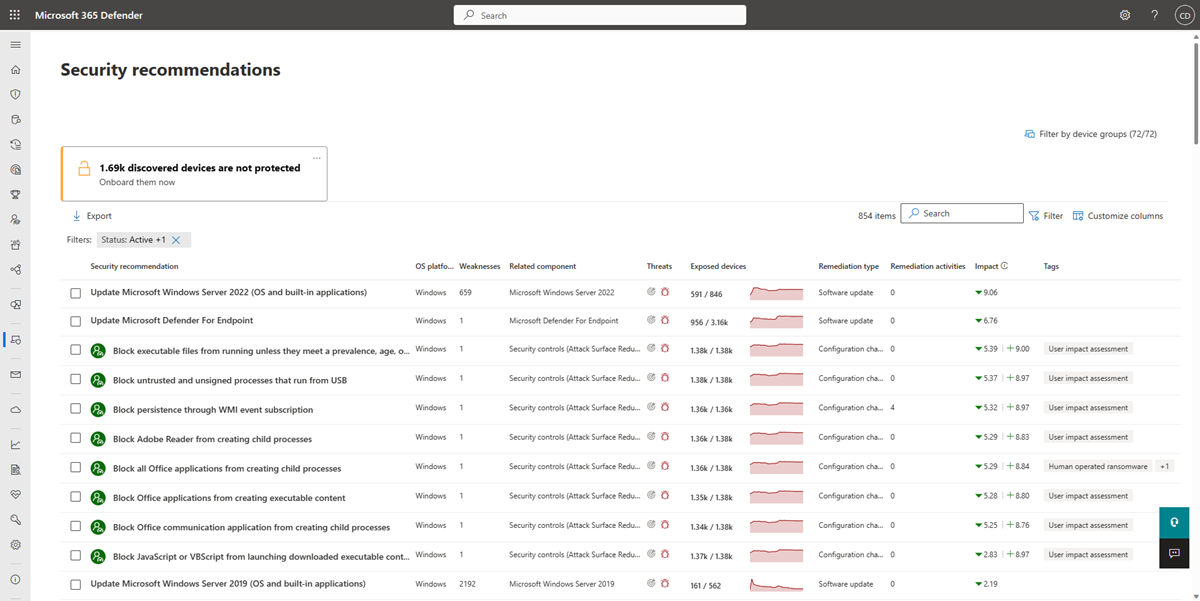
Navigate to the Security recommendations page
Access the Security recommendations page a few different ways:
- Vulnerability management navigation menu in the Microsoft Defender portal
- Top security recommendations in the vulnerability management dashboard
Navigation menu
Go to the Vulnerability management navigation menu and select Recommendations. The page contains a list of security recommendations for the threats and vulnerabilities found in your organization.
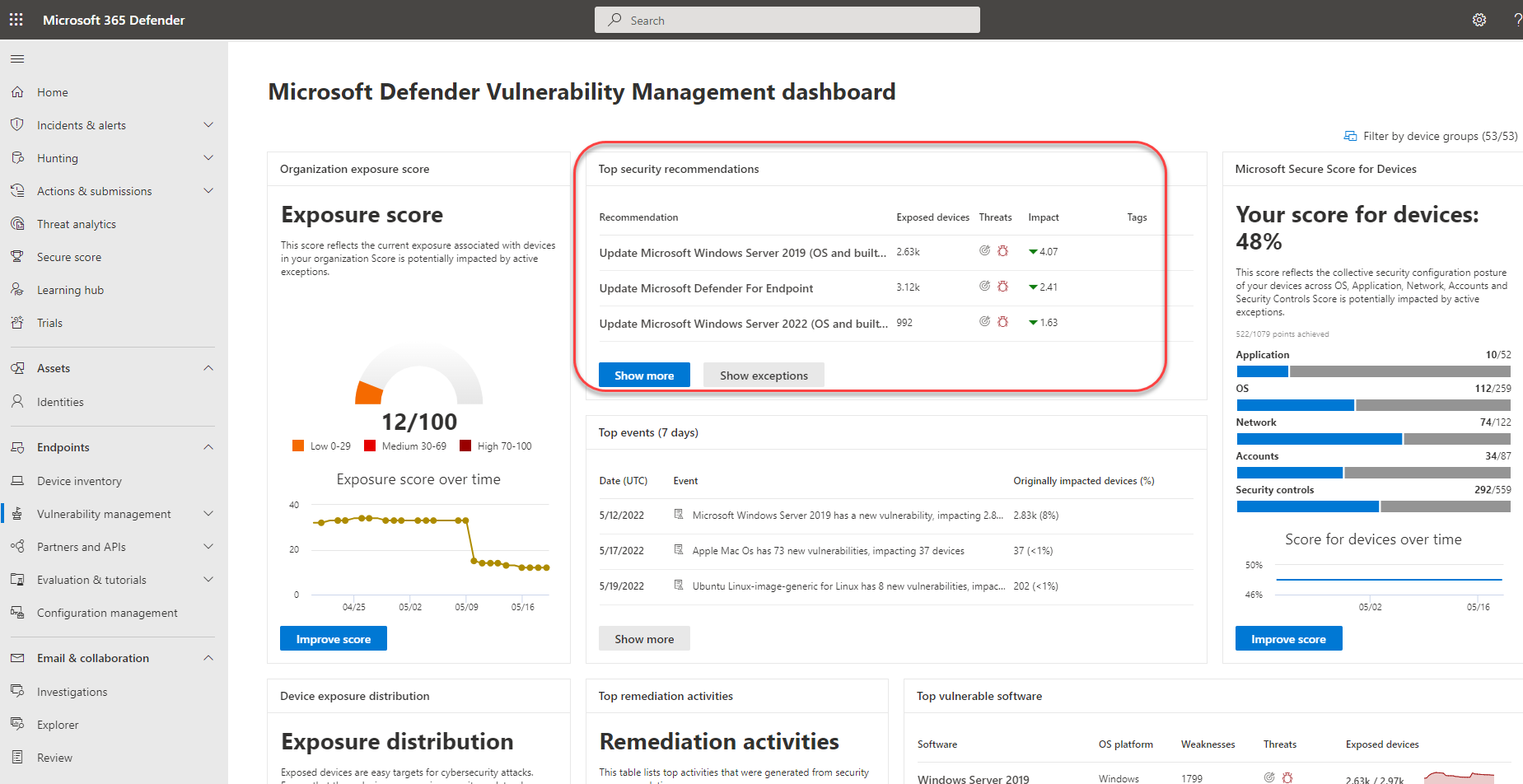
Top security recommendations in the vulnerability management dashboard
In a given day as a Security Administrator, you can take a look at the vulnerability management dashboard to see your exposure score side by side with your Microsoft Secure Score for Devices. The goal is to lower your organization's exposure from vulnerabilities, and increase your organization's device security to be more resilient against cybersecurity threat attacks. The top security recommendations list can help you achieve that goal.
The top security recommendations list the improvement opportunities prioritized based on the important factors mentioned in the previous section - threat, likelihood to be breached, and value. Selecting a recommendation will take you to the security recommendations page with more details.
Security recommendations overview
View recommendations, the number of weaknesses found, related components, threat insights, number of exposed devices, status, remediation type, remediation activities, impact to your exposure score and Secure Score for Devices once the recommendation is implemented, and associated tags.
The color of the Exposed devices graph changes as the trend changes. If the number of exposed devices is on the rise, the color changes to red. If there's a decrease in the number of exposed devices, the color of the graph will change to green.
Note
Vulnerability management shows devices that were in use up to 30 days ago. This is different from the rest of Microsoft Defender for Endpoint, where if a device has not been in use for more than 7 days it has in an 'Inactive' status.
Icons
Useful icons also quickly call your attention to:
 possible active alerts
possible active alerts associated public exploits
associated public exploits recommendation insights
recommendation insights
Impact
The impact column shows the potential impact on your exposure score and Secure Score for Devices once a recommendation is implemented. You should prioritize items that will lower your exposure score and raise your Secure Score for Devices.
The potential reduction in your exposure score is displayed as:
 . A lower exposure score means devices are less vulnerable to exploitation. Since the exposure score is based on a combination of factors, including new remediations or newly discovered vulnerabilities, the actual score reduction may be lower.
. A lower exposure score means devices are less vulnerable to exploitation. Since the exposure score is based on a combination of factors, including new remediations or newly discovered vulnerabilities, the actual score reduction may be lower.The projected increase to your Secure Score for Devices is displayed as:
 . A higher Secure Score for Devices means your endpoints are more resilient against cybersecurity attacks.
. A higher Secure Score for Devices means your endpoints are more resilient against cybersecurity attacks.
Explore security recommendation options
Select the security recommendation that you want to investigate or process.
From the flyout, you can choose any of the following options:
Open software page - Open the software page to get more context on the software and how it's distributed. The information can include threat context, associated recommendations, weaknesses discovered, number of exposed devices, discovered vulnerabilities, names and detailed of devices with the software installed, and version distribution.
Remediation options - Submit a remediation request to open a ticket in Microsoft Intune for your IT administrator to pick up and address. Track the remediation activity in the Remediation page.
Exception options - Submit an exception, provide justification, and set exception duration if you can't remediate the issue yet.
Note
When a software change is made on a device, it typically takes 2 hours for the data to be reflected in the security portal. However, it may sometimes take longer. Configuration changes can take anywhere from 4 to 24 hours.
Investigate changes in device exposure or impact
If there is a large jump in the number of exposed devices, or a sharp increase in the impact on your organization exposure score and Secure Score for Devices, then that security recommendation is worth investigating.
- Select the recommendation and Open software page
- Select the Event timeline tab to view all the impactful events related to that software, such as new vulnerabilities or new public exploits. Learn more about event timeline
- Decide how to address the increase or your organization's exposure, such as submitting a remediation request
Recommendations on devices
To see the list of security recommendations that apply to a device you can:
Select the device from the Exposed devices tab in the recommendation flyout panel or select the device directly from the Device inventory page.
Select the Security recommendations tab to see a list of security recommendations for this device.
Note
If you have the Microsoft Defender for IoT integration enabled in Defender for Endpoint, recommendations for Enterprise IoT devices that appear on IoT devices tab will appear on the security recommendations page. For more information, see Enable Enterprise IoT security with Defender for Endpoint.
Request remediation
The vulnerability management remediation capability bridges the gap between Security and IT administrators through the remediation request workflow. Security admins like you can request for the IT Administrator to remediate a vulnerability from the Security recommendation page to Intune. Learn more about remediation options
How to request remediation
Select a security recommendation you would like to request remediation for, and then select Remediation options. Fill out the form and select Submit request. Go to the Remediation page to view the status of your remediation request. Learn more about how to request remediation
File for exception
As an alternative to a remediation request when a recommendation is not relevant at the moment, you can create exceptions for recommendations. Learn more about exceptions
Only users with "exceptions handling" permissions can add exception. Learn more about RBAC roles.
When an exception is created for a recommendation, the recommendation is no longer active. The recommendation state will change to Full exception or Partial exception (by device group).
How to create an exception
Select a security recommendation you would like to create an exception for, and then select Exception options.
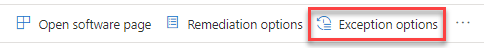
Fill out the form and submit. To view all your exceptions (current and past), navigate to the Remediation page under the Threat & Vulnerability Management menu and select the Exceptions tab. Learn more about how to create an exception
Report inaccuracy
You can report a false positive when you see any vague, inaccurate, incomplete, or already remediated security recommendation information.
Open the Security recommendation.
Select the three dots beside the security recommendation that you want to report, then select Report inaccuracy.
From the flyout pane, select the inaccuracy category from the drop-down menu, fill in your email address, and details regarding the inaccuracy.
Select Submit. Your feedback is immediately sent to the vulnerability management experts.
Related articles
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for