Application Guard testing scenarios
Note
- Microsoft Defender Application Guard, including the Windows Isolated App Launcher APIs, will be deprecated for Microsoft Edge for Business and will no longer be updated. Please download the Microsoft Edge For Business Security Whitepaper to learn more about Edge for Business security capabilities.
- Because Application Guard is deprecated there will not be a migration to Edge Manifest V3. The corresponding extensions and associated Windows Store app will not be available after May 2024. This affects the following browsers: Application Guard Extension - Chrome and Application Guard Extension - Firefox. If you want to block unprotected browsers until you are ready to retire MDAG usage in your enterprise, we recommend using AppLocker policies or Microsoft Edge management service. For more information, see Microsoft Edge and Microsoft Defender Application Guard.
We've come up with a list of scenarios that you can use to test hardware-based isolation in your organization.
Application Guard in standalone mode
You can see how an employee would use standalone mode with Application Guard.
To test Application Guard in Standalone mode
Restart the device, start Microsoft Edge, and then select New Application Guard window from the menu.
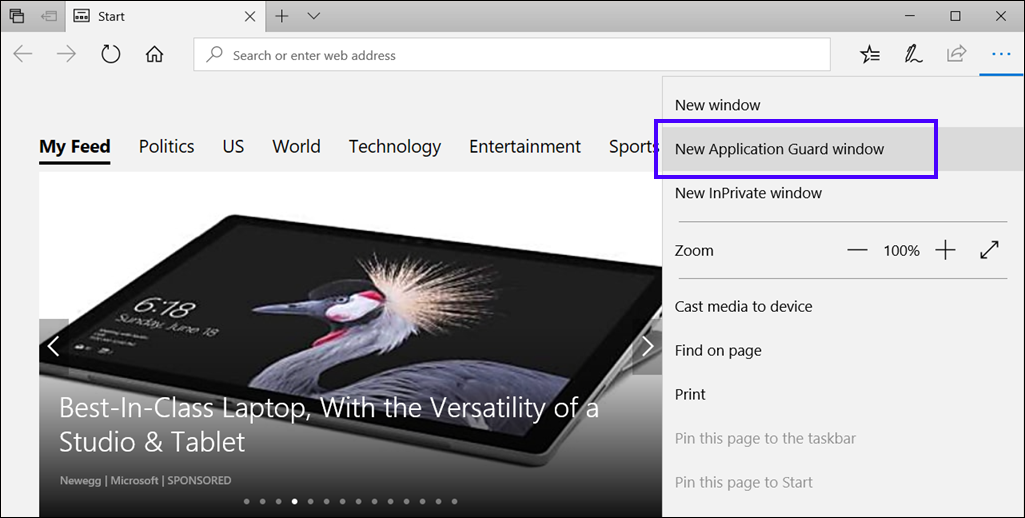
Wait for Application Guard to set up the isolated environment.
Note
Starting Application Guard too quickly after restarting the device might cause it to take a bit longer to load. However, subsequent starts should occur without any perceivable delays.
Go to an untrusted, but safe URL (for this example, we used msn.com) and view the new Microsoft Edge window, making sure you see the Application Guard visual cues.
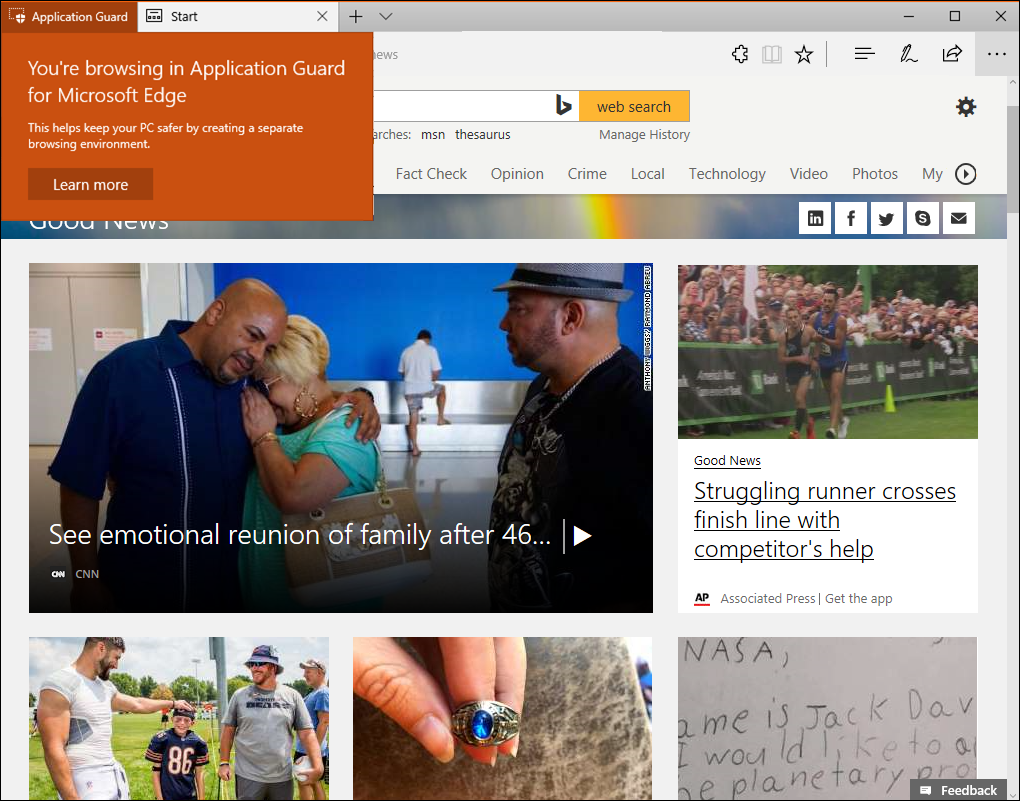
Application Guard in Enterprise-managed mode
How to install, set up, turn on, and configure Application Guard for Enterprise-managed mode.
Install, set up, and turn on Application Guard
Before you can use Application Guard in managed mode, you must install Windows 10 Enterprise edition, version 1709, and Windows 11 which includes the functionality. Then, you must use Group Policy to set up the required settings.
Restart the device, and then start Microsoft Edge.
Set up the Network Isolation settings in Group Policy:
a. Select the Windows icon, type
Group Policy, and then select Edit Group Policy.b. Go to the Administrative Templates\Network\Network Isolation\Enterprise resource domains hosted in the cloud setting.
c. For the purposes of this scenario, type
.microsoft.cominto the Enterprise cloud resources box.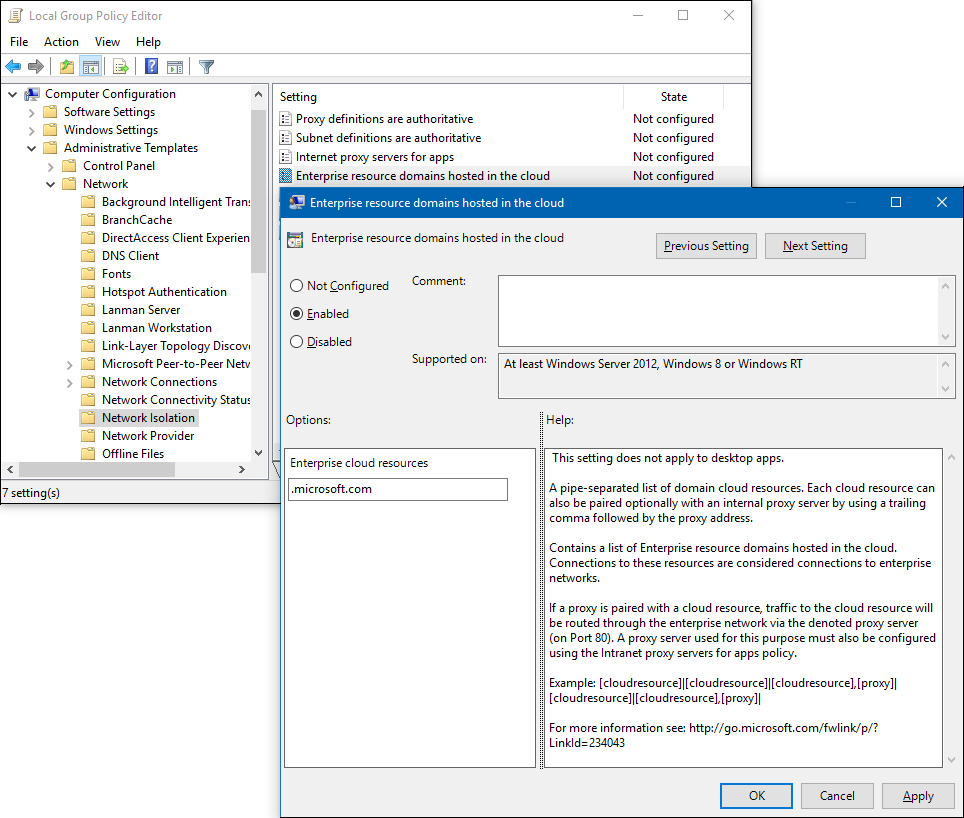
d. Go to the Administrative Templates\Network\Network Isolation\Domains categorized as both work and personal setting.
e. For the purposes of this scenario, type
bing.cominto the Neutral resources box.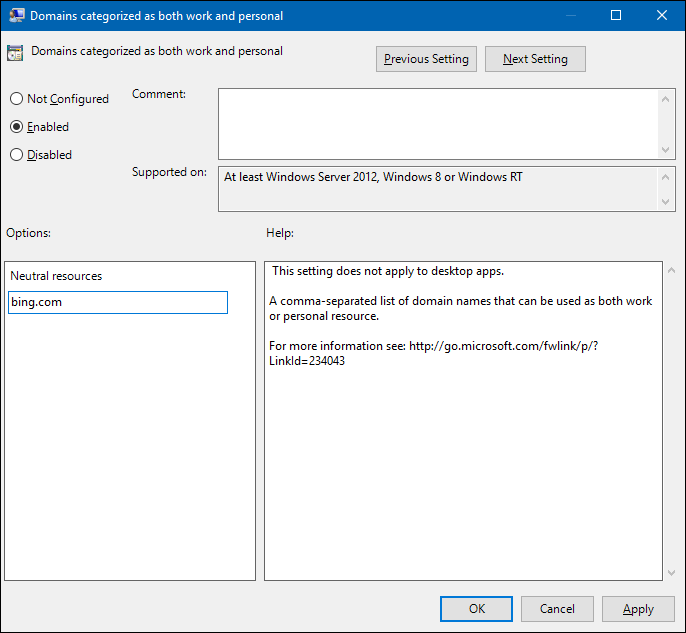
Go to the Computer Configuration\Administrative Templates\Windows Components\Microsoft Defender Application Guard\Turn on Microsoft Defender Application Guard in Managed Mode setting.
Select Enabled, choose Option 1, and select OK.
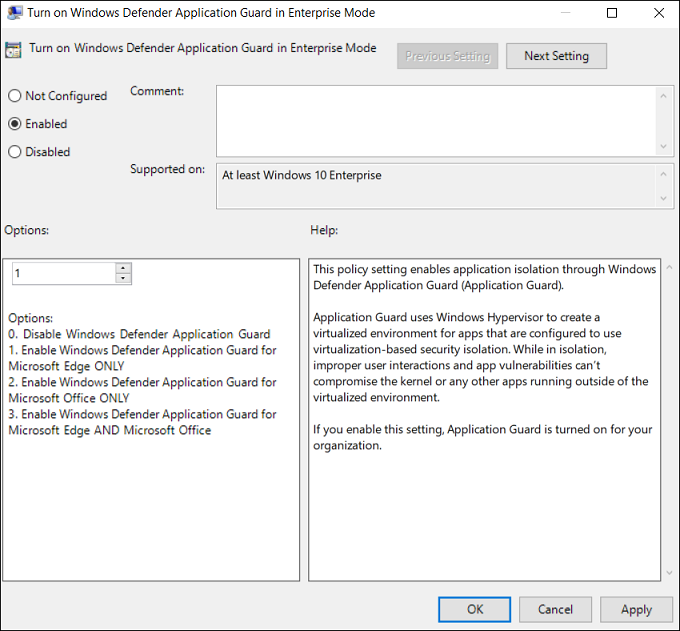
Note
Enabling this setting verifies that all the necessary settings are properly configured on your employee devices, including the network isolation settings set earlier in this scenario.
Start Microsoft Edge and type
https://www.microsoft.com.After you submit the URL, Application Guard determines the URL is trusted because it uses the domain you've marked as trusted and shows the site directly on the host PC instead of in Application Guard.
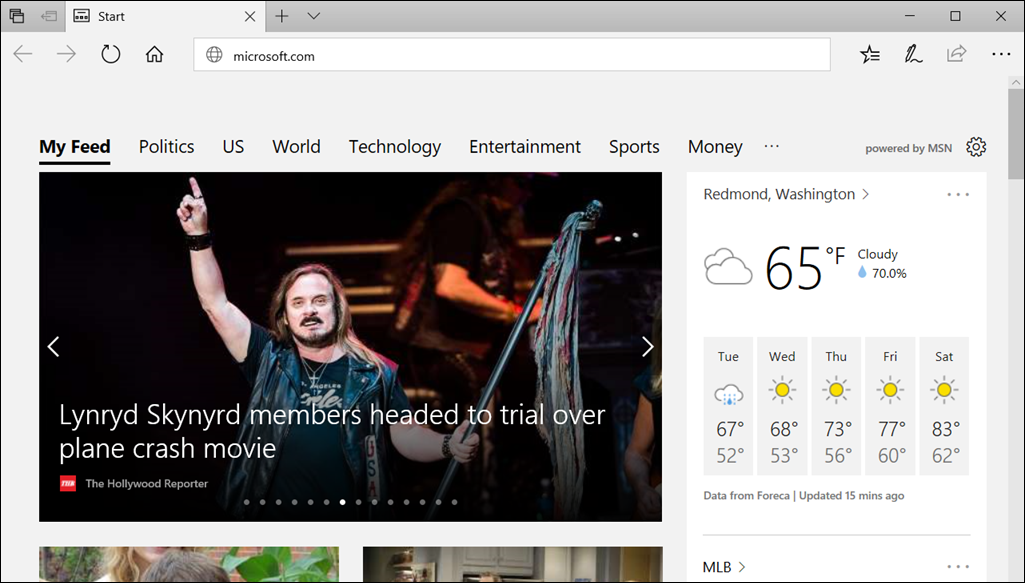
In the same Microsoft Edge browser, type any URL that isn't part of your trusted or neutral site lists.
After you submit the URL, Application Guard determines the URL is untrusted and redirects the request to the hardware-isolated environment.

Customize Application Guard
Application Guard lets you specify your configuration, allowing you to create the proper balance between isolation-based security and productivity for your employees.
Application Guard provides the following default behavior for your employees:
No copying and pasting between the host PC and the isolated container.
No printing from the isolated container.
No data persistence from one isolated container to another isolated container.
You have the option to change each of these settings to work with your enterprise from within Group Policy.
Applies to:
- Windows 10 Enterprise or Pro editions, version 1803 or later
- Windows 11 Enterprise or Pro editions
Copy and paste options
Go to the Computer Configuration\Administrative Templates\Windows Components\Microsoft Defender Application Guard\Configure Microsoft Defender Application Guard clipboard settings.
Select Enabled and select OK.
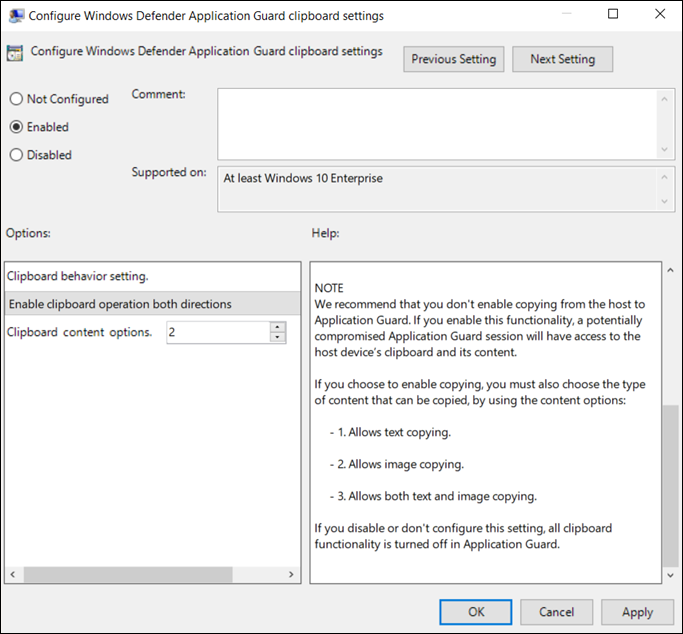
Choose how the clipboard works:
Copy and paste from the isolated session to the host PC
Copy and paste from the host PC to the isolated session
Copy and paste both directions
Choose what can be copied:
Only text can be copied between the host PC and the isolated container.
Only images can be copied between the host PC and the isolated container.
Both text and images can be copied between the host PC and the isolated container.
Select OK.
Print options
Go to the Computer Configuration\Administrative Templates\Windows Components\Microsoft Defender Application Guard\Configure Microsoft Defender Application Guard print settings.
Select Enabled and select OK.
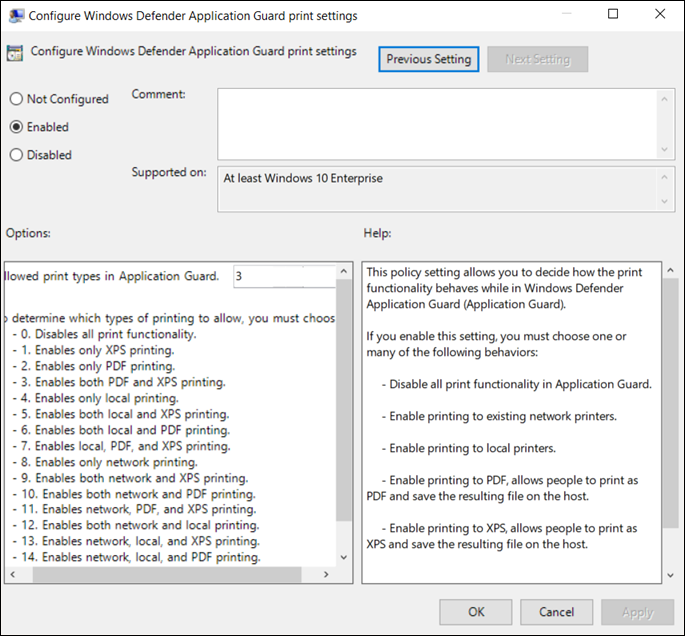
Based on the list provided in the setting, choose the number that best represents what type of printing should be available to your employees. You can allow any combination of local, network, PDF, and XPS printing.
Select OK.
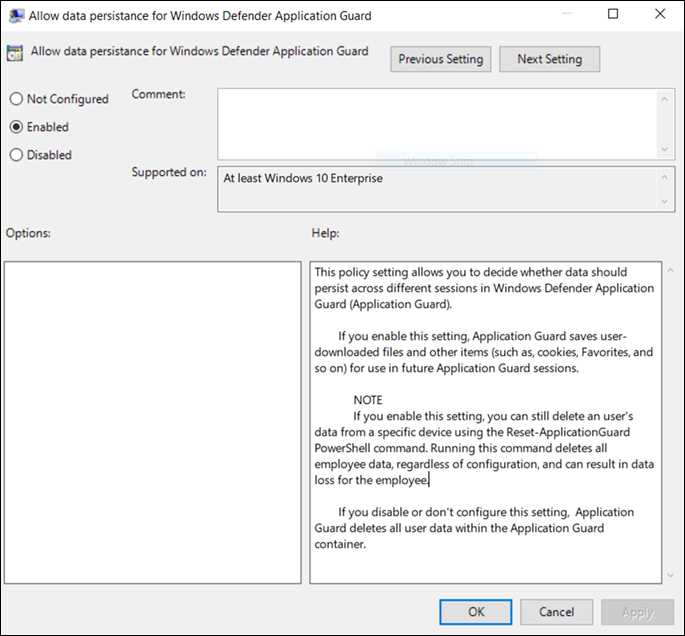
Data persistence options
Go to the Computer Configuration\Administrative Templates\Windows Components\Microsoft Defender Application Guard\Allow data persistence for Microsoft Defender Application Guard setting.
Select Enabled and select OK.
Open Microsoft Edge and browse to an untrusted, but safe URL.
The website opens in the isolated session.
Add the site to your Favorites list and then close the isolated session.
Sign out and back in to your device, opening Microsoft Edge in Application Guard again.
The previously added site should still appear in your Favorites list.
Note
Starting with Windows 11, version 22H2, data persistence is disabled by default. If you don't allow or turn off data persistence, restarting a device or signing in and out of the isolated container triggers a recycle event. This action discards all generated data, such as session cookies and Favorites, and removes the data from Application Guard. If you turn on data persistence, all employee-generated artifacts are preserved across container recycle events. However, these artifacts only exist in the isolated container and aren't shared with the host PC. This data persists after restarts and even through build-to-build upgrades of Windows 10 and Windows 11.
If you turn on data persistence, but later decide to stop supporting it for your employees, you can use our Windows-provided utility to reset the container and to discard any personal data.
To reset the container, follow these steps:
1. Open a command-line program and navigate to Windows/System32.
2. Typewdagtool.exe cleanup. The container environment is reset, retaining only the employee-generated data.
3. Typewdagtool.exe cleanup RESET_PERSISTENCE_LAYER. The container environment is reset, including discarding all employee-generated data.Microsoft Edge version 90 or later no longer supports
RESET_PERSISTENCE_LAYER.
Applies to:
- Windows 10 Enterprise or Pro editions, version 1803
- Windows 11 Enterprise or Pro editions, version 21H2. Data persistence is disabled by default in Windows 11, version 22H2 and later.
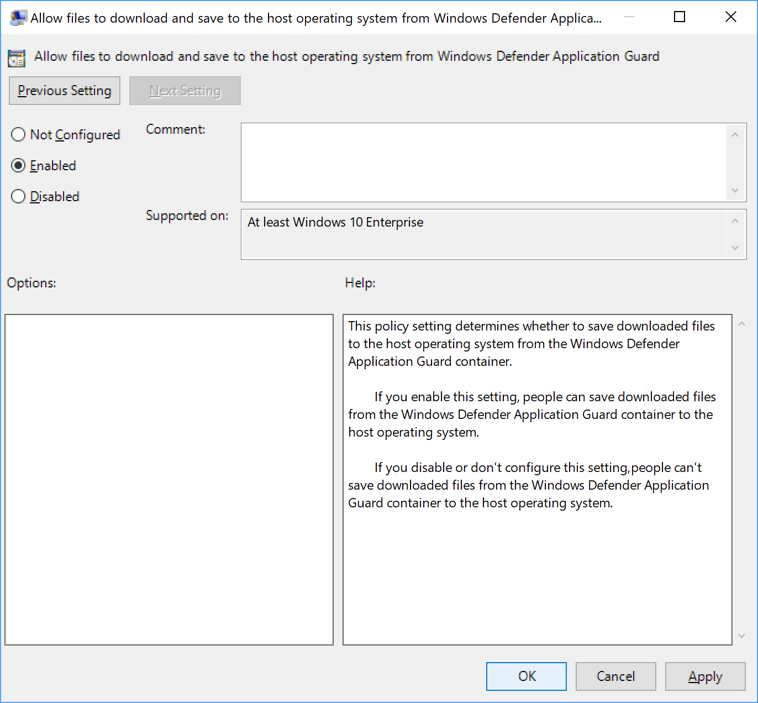
Download options
Go to the Computer Configuration\Administrative Templates\Windows Components\Microsoft Defender Application Guard\Allow files to download and save to the host operating system from Microsoft Defender Application Guard setting.
Select Enabled and select OK.
Sign out and back in to your device, opening Microsoft Edge in Application Guard again.
Download a file from Microsoft Defender Application Guard.
Check to see the file has been downloaded into This PC > Downloads > Untrusted files.
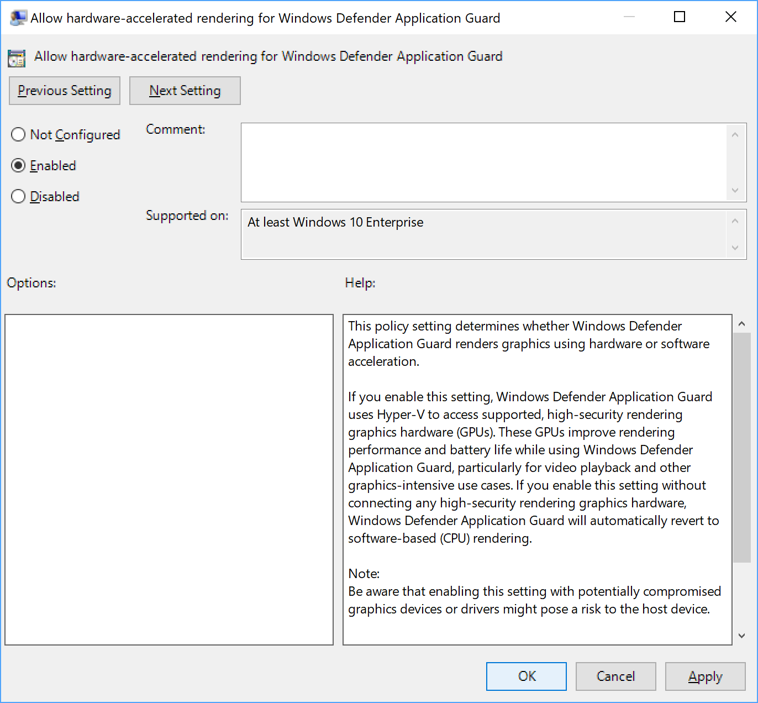
Hardware acceleration options
Go to the Computer Configuration\Administrative Templates\Windows Components\Microsoft Defender Application Guard\Allow hardware-accelerated rendering for Microsoft Defender Application Guard setting.
Select Enabled and Select OK.
Once you have enabled this feature, open Microsoft Edge and browse to an untrusted, but safe URL with video, 3D, or other graphics-intensive content. The website opens in an isolated session.
Assess the visual experience and battery performance.
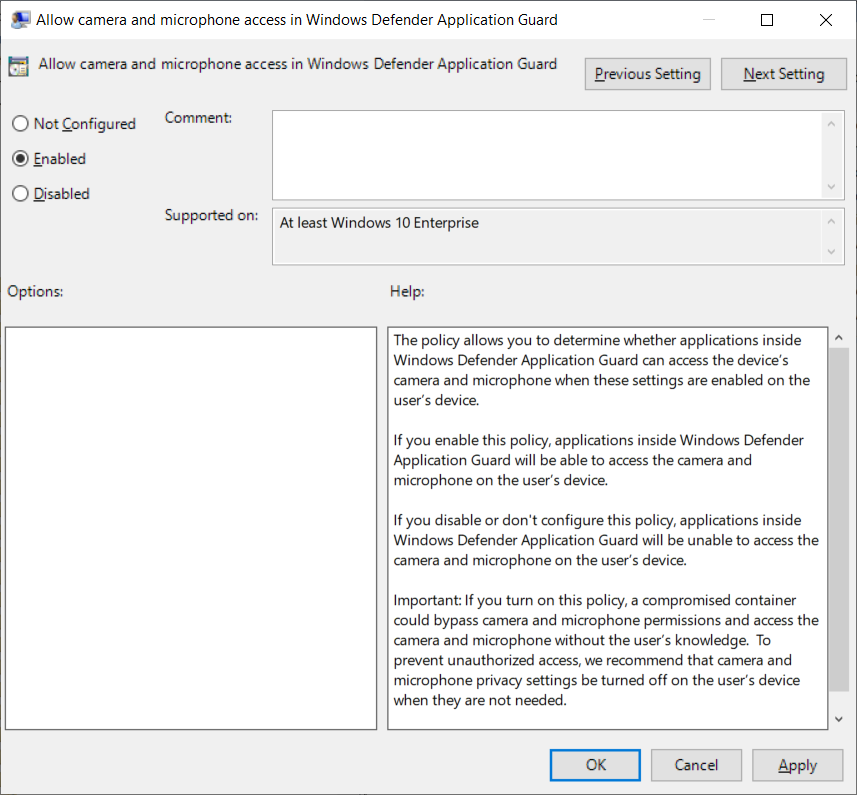
Camera and microphone options
Go to the Computer Configuration\Administrative Templates\Windows Components\Microsoft Defender Application Guard\Allow camera and microphone access in Microsoft Defender Application Guard setting.
Select Enabled and select OK.
Sign out and back in to your device, opening Microsoft Edge in Application Guard again.
Open an application with video or audio capability in Edge.
Check that the camera and microphone work as expected.
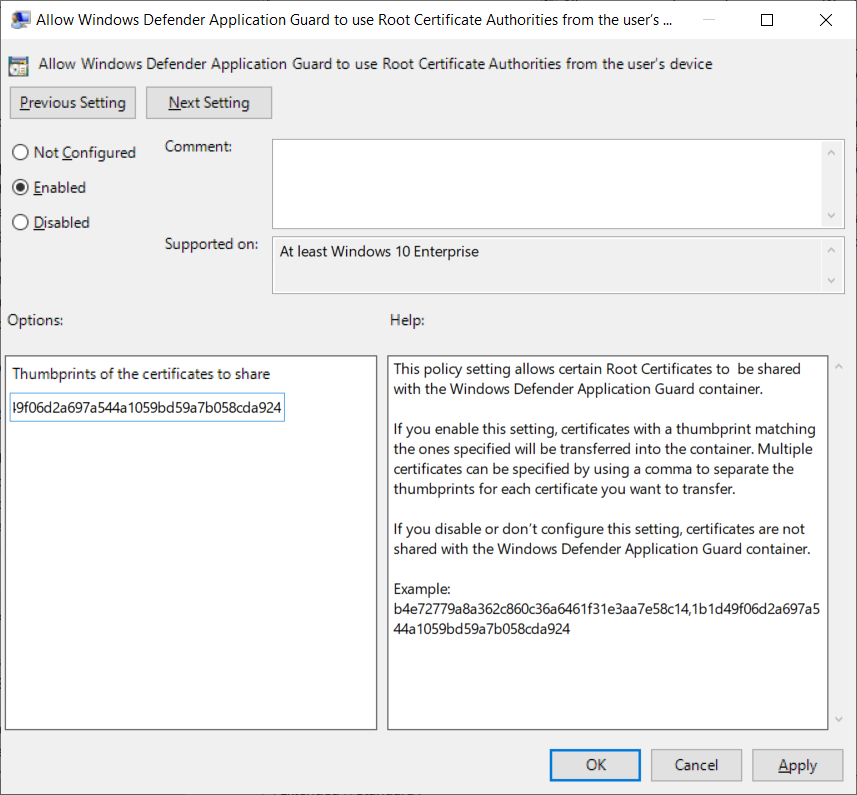
Root certificate sharing options
Go to the Computer Configuration\Administrative Templates\Windows Components\Microsoft Defender Application Guard\Allow Microsoft Defender Application Guard to use Root Certificate Authorities from the user's device setting.
Select Enabled, copy the thumbprint of each certificate to share, separated by a comma, and select OK.
Sign out and back in to your device, opening Microsoft Edge in Application Guard again.
Application Guard Extension for third-party web browsers
The Application Guard Extension available for Chrome and Firefox allows Application Guard to protect users even when they are running a web browser other than Microsoft Edge or Internet Explorer.
Once a user has the extension and its companion app installed on their enterprise device, you can run through the following scenarios.
Open either Firefox or Chrome, whichever browser you have the extension installed on.
Navigate to an organizational website. In other words, an internal website maintained by your organization. You might see this evaluation page for an instant before the site is fully loaded.

Navigate to a non-enterprise, external website site, such as www.bing.com. The site should be redirected to Microsoft Defender Application Guard Edge.

Open a new Application Guard window, by selecting the Microsoft Defender Application Guard icon, then New Application Guard Window

Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for