Microsoft 365 Certification - Initial Document Submission Guide
The initial document submission is part of the pre-assessment phase of the certification. The information provided will give certification analysts with the background necessary to identify which controls and system components will be in-scope for your assessment. This document is intended to serve only as an example of what is expected of your initial document submission. The documentation you provide will vary depending on how your solution is architected, implemented, and managed.
What is the hosting environment or service model used to run your app?
- Infrastructure as a Service (IaaS) is a cloud service model where your cloud service provider hosts your infrastructure components but ISVs are still responsible for deploying and managing the components individually such as Virtual Machines/Operating Systems, Data Stores and Networking Components. Examples of this are Azure Virtual Machine and Azure Disk Storage.
- Platform as a Service (PaaS) is a cloud service model where the infrastructure components are managed by the cloud service provider. ISVs are only responsible for deploying their own applications and services. Examples of this are Azure App Services, Azure Functions, and Azure CDN.
- ISV Hosted in this context means that no cloud service provider is used. The ISV physically manages their own Servers, Disks, Networking independently on-premises.
- Hybrid in this context means that one of more of the above models are used. For example, some ISVs may elect to use a mixture of IaaS Services, and PaaS services to support their app, or they may have some on-premises ISV Hosted components, and outsource others to a cloud service provider. If you use one of more service model, select hybrid.
Penetration Test Report
Include the full penetration testing report with dates evidencing that it has been completed within the last 12 months.
- This report must be produced from manual penetration testing, it can't be the output of an automated scanning/testing tool.
- This report must include the environment that supports the deployment of the app/add along with any additional environment that supports the operation of the app/add-ins.
System Component Inventory
An up-to-date inventory of all system components used by the supporting infrastructure. This will be used to help with sampling when performing the assessment phase. If your environment includes PaaS, it would be useful if you can provide detail of all PaaS services consumed.
Note: IaaS/PaaS wouldn't have any hardware that would be under the ISVs control. In this case, please provide a list or screenshot of all the visual resources.
Example:
| Asset Name | Asset Type | Description | Manufacturer | Model |
|---|---|---|---|---|
| D212 | Windows Machine | Virtual Machine | N/A | N/A |
| LT101 | Laptop | Workstation | Microsoft | Surface 3 |
| C2938 | Switch | Switch | N/A | N/A |
| LXM2 | Linux Machine | Test Machine | N/A | N/A |
Software Inventory
An up-to-date inventory of all software assets including all software used within the in-scope environment along with the versions.
Example:
| Software | Publisher | Version | Purpose |
|---|---|---|---|
| Windows Server | Microsoft 2016 | Build 14393 | Server operating system for the production environment |
| Linux Ubuntu | N/A | 16.04 (Xenial) | Server operating system in use within the DMZ. |
| ESXi | VMware | 6.5.0 (Build 13004031) | Used to support the virtual servers. |
| Mysql (Windows) | N/A | 8.0.2.1 | Database server to store the chat history. |
| Tomcat | Apache | 7.0.92 | Customer portal. |
| IIS | Microsoft | 10.0 | Supports the APIs. |
Third Party Dependencies
Documentation listing all dependencies used by the app / add-in with the current running versions.
Example:
| Web Dependencies | Current Version in Use |
|---|---|
| JQuery | 3.5.1 |
| React | 16.13.1 |
| Bootstrap | 4.5.2 |
| Express | 4.17.1 |
| Angular | 10.0.14 |
| AngularJS | 1.8.0 |
Public IP Addresses
Detailing all public IP Addresses and URLs used by the supporting infrastructure. This must include the full routable IP range allocated to the environment unless adequate segmentation has been implemented to split the range in use (adequate evidence of segmentation will be required).
Example:
| URLs | IP Address |
|---|---|
| https://portal.contoso.com | 40.113.200.201 |
| https://filesapi.contoso.com | 40.113.200.201 |
| https://customerapi.contoso.com | 40.113.200.202 |
| https://bot.contoso.com | 40.113.200.202 |
| N/A (Jump Server) | 40.113.200.200 |
Resource Endpoints
API Name Endpoint Address Contoso Customer API https://customerapi.contoso.com Contoso Bot Service https://bot.contoso.com Contoso Files API https://filesapi.contoso.com
A complete listing of all API Endpoints used by your app including internally developed, and external resource endpoints. To help understand the environment scope, provide API endpoint locations within your environment.
Example:
| API Name | Endpoint Address |
|---|---|
| Contoso Customer API | https://customerapi.contoso.com |
| Contoso Bot Service | https://bot.contoso.com |
| Contoso Files API | https://filesapi.contoso.com |
| Microsoft Graph | https://graph.microsoft.com/v1.0/| |
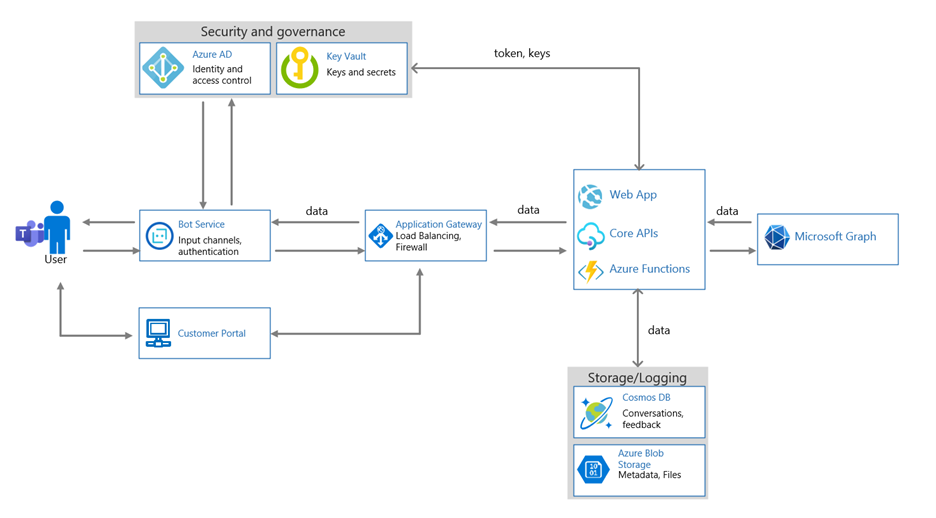
Architectural Diagram
A logical architecture diagram representing a high-level overview of your app's / add-in’s supporting infrastructure. This must include all hosting environments and supporting infrastructure supporting the app/add-in. This diagram MUST depict all the different supporting system components within the environment to help certification analysts understand systems in scope and help to determine sampling. Also indicate what hosting environment type is used; ISV Hosted, IaaS, PaaS, or Hybrid. Where PaaS is used, please indicate the various PaaS services that are used to provide the supporting services within the environment.

Data Flow Diagram
Flow diagrams detailing the following:
- Data flows to and from the App / Add-in (including customer data).
- Data flows within the supporting infrastructure (where applicable)
- Diagrams highlighting where and what data is stored, how data is passed to external third parties (including details of what third parties), and how data is protected in transit over open/public networks and at rest.
External Certifications (SOC2, PCI DSS, ISO27001) - OPTIONAL
If you've already obtained a SOC2, PCI DSS, or ISO27001 certification, and have a report issued within the last 12 months that includes the full scope of the application being certified as well as the supporting environment, you may submit this during your initial document submission. We'll attempt to use it to satisfy a subset of controls and expedite your assessment. However this isn't required to obtain a Microsoft 365 Certification.