Cross-tenant management experiences
As a service provider, you can use Azure Lighthouse to manage your customers' Azure resources from within your own Microsoft Entra tenant. Many common tasks and services can be performed across these managed tenants.
Tip
Azure Lighthouse can also be used within an enterprise which has multiple Microsoft Entra tenants of its own to simplify cross-tenant administration.
Understanding tenants and delegation
A Microsoft Entra tenant is a representation of an organization. It's a dedicated instance of Microsoft Entra ID that an organization receives when they create a relationship with Microsoft by signing up for Azure, Microsoft 365, or other services. Each Microsoft Entra tenant is distinct and separate from other Microsoft Entra tenants, and has its own tenant ID (a GUID). For more information, see What is Microsoft Entra ID?
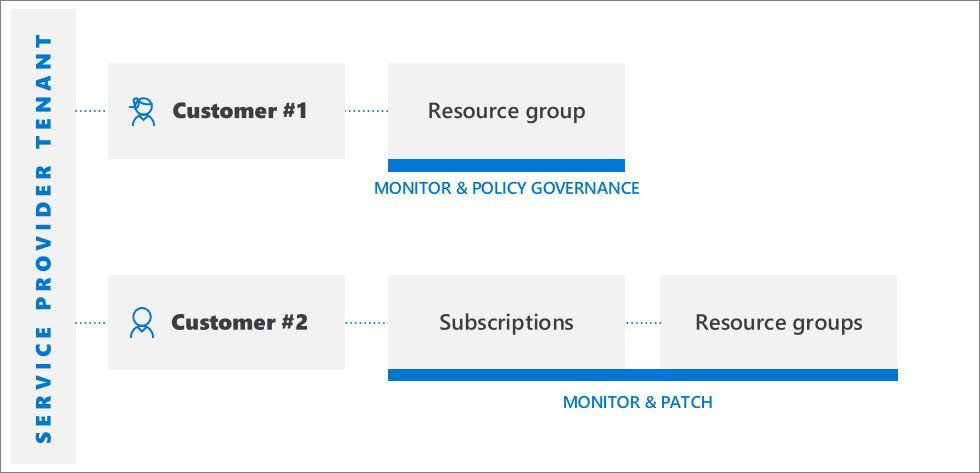
Typically, in order to manage Azure resources for a customer, service providers must sign in to the Azure portal using an account associated with that customer's tenant. In this scenario, an administrator in the customer's tenant must create and manage user accounts for the service provider.
With Azure Lighthouse, the onboarding process specifies users in the service provider's tenant who are assigned roles to delegated subscriptions and resource groups in the customer's tenant. These users can then sign in to the Azure portal, using their own credentials, and work on resources belonging to all of the customers to which they have access. Users in the managing tenant can see all of these customers by visiting the My customers page in the Azure portal. They can also work on resources directly within the context of that customer's subscription, either in the Azure portal or via APIs.
Azure Lighthouse provides flexibility to manage resources for multiple customers without having to sign in to different accounts in different tenants. For example, a service provider may have two customers with different responsibilities and access levels. Using Azure Lighthouse, authorized users can sign in to the service provider's tenant and access all of the delegated resources across these customers, according to the roles they've been assigned for each delegation.
APIs and management tool support
You can perform management tasks on delegated resources in the Azure portal, or you can use APIs and management tools such as Azure CLI and Azure PowerShell. All existing APIs can be used on delegated resources, as long as the functionality is supported for cross-tenant management and the user has the appropriate permissions.
The Azure PowerShell Get-AzSubscription cmdlet shows the TenantId for the managing tenant by default. The HomeTenantId and ManagedByTenantIds attributes for each subscription allow you to identify whether a returned subscription belongs to a managed tenant or to your managing tenant.
Similarly, Azure CLI commands such as az account list show the homeTenantId and managedByTenants attributes. If you don't see these values when using Azure CLI, try clearing your cache by running az account clear followed by az login --identity.
In the Azure REST API, the Subscriptions - Get and Subscriptions - List commands include ManagedByTenant.
Note
In addition to tenant information related to Azure Lighthouse, tenants shown by these APIs may also reflect partner tenants for Azure Databricks or Azure managed applications.
We also provide APIs that are specific to performing Azure Lighthouse tasks. For more info, see the Reference section.
Enhanced services and scenarios
Most Azure tasks and services can be used with delegated resources across managed tenants, assuming the appropriate roles are granted. Below are some of the key scenarios where cross-tenant management can be especially effective.
- Manage hybrid servers at scale - Azure Arc-enabled servers:
- Onboard servers to delegated customer subscriptions and/or resource groups in Azure
- Manage Windows Server or Linux machines outside Azure that are connected to delegated subscriptions
- Manage connected machines using Azure constructs, such as Azure Policy and tagging
- Ensure the same set of policies are applied across customers' hybrid environments
- Use Microsoft Defender for Cloud to monitor compliance across customers' hybrid environments
- Manage hybrid Kubernetes clusters at scale - Azure Arc-enabled Kubernetes:
- Connect Kubernetes clusters to delegated subscriptions and/or resource groups
- Use GitOps to deploy configurations to connected clusters
- Perform management tasks such as enforcing policies across connected clusters
- Use Automation accounts to access and work with delegated resources
- Back up and restore customer data from on-premises workloads, Azure VMs, Azure file shares, and more
- View data for all delegated customer resources in Backup center
- Use the Backup Explorer to help view operational information of backup items (including Azure resources not yet configured for backup) and monitoring information (jobs and alerts) for delegated subscriptions. The Backup Explorer is currently available only for Azure VM data.
- Use Backup reports across delegated subscriptions to track historical trends, analyze backup storage consumption, and audit backups and restores.
- Use Azure Blueprints to orchestrate the deployment of resource templates and other artifacts (requires additional access to prepare the customer subscription)
Azure Cost Management + Billing:
- From the managing tenant, CSP partners can view, manage, and analyze pre-tax consumption costs (not inclusive of purchases) for customers who are under the Azure plan. The cost is based on retail rates and the Azure role-based access control (Azure RBAC) access that the partner has for the customer's subscription. Currently, you can view consumption costs at retail rates for each individual customer subscription based on Azure RBAC access.
- Create Key Vaults in customer tenants
- Use a managed identity to create Key Vaults in customer tenants
Azure Kubernetes Service (AKS):
- Manage hosted Kubernetes environments and deploy and manage containerized applications within customer tenants
- Deploy and manage clusters in customer tenants
- Use Azure Monitor for containers to monitor performance across customer tenants
- Create migration projects in the customer tenant and migrate VMs
- View alerts for delegated subscriptions, with the ability to view and refresh alerts across all subscriptions
- View activity log details for delegated subscriptions
- Log analytics: Query data from remote workspaces in multiple tenants (note that automation accounts used to access data from workspaces in customer tenants must be created in the same tenant)
- Create, view, and manage alerts in customer tenants
- Create alerts in customer tenants that trigger automation, such as Azure Automation runbooks or Azure Functions, in the managing tenant through webhooks
- Create diagnostic settings in workspaces created in customer tenants, to send resource logs to workspaces in the managing tenant
- For SAP workloads, monitor SAP Solutions metrics with an aggregated view across customer tenants
- For Azure AD B2C, route sign-in and auditing logs to different monitoring solutions
- Deploy and manage Azure Virtual Network and virtual network interface cards (vNICs) within managed tenants
- Deploy and configure Azure Firewall to protect customers’ Virtual Network resources
- Manage connectivity services such as Azure Virtual WAN, Azure ExpressRoute, and VPN Gateway
- Use Azure Lighthouse to support key scenarios for the Azure Networking MSP Program
- Create and edit policy definitions within delegated subscriptions
- Deploy policy definitions and policy assignments across multiple tenants
- Assign customer-defined policy definitions within delegated subscriptions
- Customers see policies authored by the service provider alongside any policies they've authored themselves
- Can remediate deployIfNotExists or modify assignments within the managed tenant
- Note that viewing compliance details for non-compliant resources in customer tenants is not currently supported
- See the tenant ID in returned query results, allowing you to identify whether a subscription belongs to a managed tenant
- Monitor the health of customer resources with Azure Resource Health
- Track the health of the Azure services used by your customers
- Manage disaster recovery options for Azure virtual machines in customer tenants (note that you can't use
RunAsaccounts to copy VM extensions)
- Use virtual machine extensions to provide post-deployment configuration and automation tasks on Azure VMs
- Use boot diagnostics to troubleshoot Azure VMs
- Access VMs with serial console
- Integrate VMs with Azure Key Vault for passwords, secrets, or cryptographic keys for disk encryption by using managed identity through policy, ensuring that secrets are stored in a Key Vault in the managed tenants
- Note that you can't use Microsoft Entra ID for remote login to VMs
- Cross-tenant visibility
- Monitor compliance with security policies and ensure security coverage across all tenants' resources
- Continuous regulatory compliance monitoring across multiple tenants in a single view
- Monitor, triage, and prioritize actionable security recommendations with secure score calculation
- Cross-tenant security posture management
- Manage security policies
- Take action on resources that are out of compliance with actionable security recommendations
- Collect and store security-related data
- Cross-tenant threat detection and protection
- Detect threats across tenants' resources
- Apply advanced threat protection controls such as just-in-time (JIT) VM access
- Harden network security group configuration with Adaptive Network Hardening
- Ensure servers are running only the applications and processes they should be with adaptive application controls
- Monitor changes to important files and registry entries with File Integrity Monitoring (FIM)
- Note that the entire subscription must be delegated to the managing tenant; Microsoft Defender for Cloud scenarios are not supported with delegated resource groups
- Manage Microsoft Sentinel resources in customer tenants
- Track attacks and view security alerts across multiple tenants
- View incidents across multiple Microsoft Sentinel workspaces spread across tenants
Support requests:
- Open support requests from Help + support in the Azure portal for delegated resources (selecting the support plan available to the delegated scope)
- Use the Azure Quota API to view and manage Azure service quotas for delegated customer resources
Current limitations
With all scenarios, be aware of the following current limitations:
- Requests handled by Azure Resource Manager can be performed using Azure Lighthouse. The operation URIs for these requests start with
https://management.azure.com. However, requests that are handled by an instance of a resource type (such as Key Vault secrets access or storage data access) aren't supported with Azure Lighthouse. The operation URIs for these requests typically start with an address that is unique to your instance, such ashttps://myaccount.blob.core.windows.netorhttps://mykeyvault.vault.azure.net/. The latter are also typically data operations rather than management operations. - Role assignments must use Azure built-in roles. All built-in roles are currently supported with Azure Lighthouse, except for Owner or any built-in roles with
DataActionspermission. The User Access Administrator role is supported only for limited use in assigning roles to managed identities. Custom roles and classic subscription administrator roles are not supported. For more information, see Role support for Azure Lighthouse. - For users in the managed tenant, role assignments made through Azure Lighthouse aren't shown under Access Control (IAM) or with CLI tools such as
az role assignment list. These assignments are only visible in the Azure portal in the Delegations section of Azure Lighthouse, or through the Azure Lighthouse API. - While you can onboard subscriptions that use Azure Databricks, users in the managing tenant can't launch Azure Databricks workspaces on a delegated subscription.
- While you can onboard subscriptions and resource groups that have resource locks, those locks won't prevent actions from being performed by users in the managing tenant. Deny assignments that protect system-managed resources (system-assigned deny assignments), such as those created by Azure managed applications or Azure Blueprints, do prevent users in the managing tenant from acting on those resources. However, users in the customer tenant can't create their own deny assignments.
- Delegation of subscriptions across a national cloud and the Azure public cloud, or across two separate national clouds, is not supported.
Next steps
- Onboard your customers to Azure Lighthouse, either by using Azure Resource Manager templates or by publishing a private or public managed services offer to Azure Marketplace.
- View and manage customers by going to My customers in the Azure portal.
- Learn more about Azure Lighthouse architecture.
Athugasemdir
Væntanlegt: Á árinu 2024 munum við hætta með GitHub-mál sem ábendingaleið fyrir efni og skipta því út fyrir nýtt ábendingakerfi. Frekari upplýsingar er að finna hér: https://aka.ms/ContentUserFeedback.
Senda inn og skoða endurgjöf fyrir