Microsoft Defender for Cloud は、Defender for Storage プランを使用してストレージ アカウントに対する潜在的な脅威を識別するセキュリティ インテリジェンスの Azure ネイティブ レイヤーを提供します。
Defender for Storage は、悪意のあるファイルのアップロード、機密データの流出、データの破損を防ぎ、データとワークロードのセキュリティと整合性を確保します。
Defender for Storage では、Azure Blob Storage、Azure Files、Azure Data Lake Storage の各サービスによって生成されたデータ プレーンとコントロール プレーンのテレメトリを分析することで、包括的なセキュリティが提供されます。
Microsoft Defender 脅威インテリジェンス、Microsoft Defender ウイルス対策、機密データ検出を利用した高度な脅威検出機能を使用して、潜在的な脅威の特定と軽減に役立ちます。
Defender for Storage には、次の機能が含まれています。
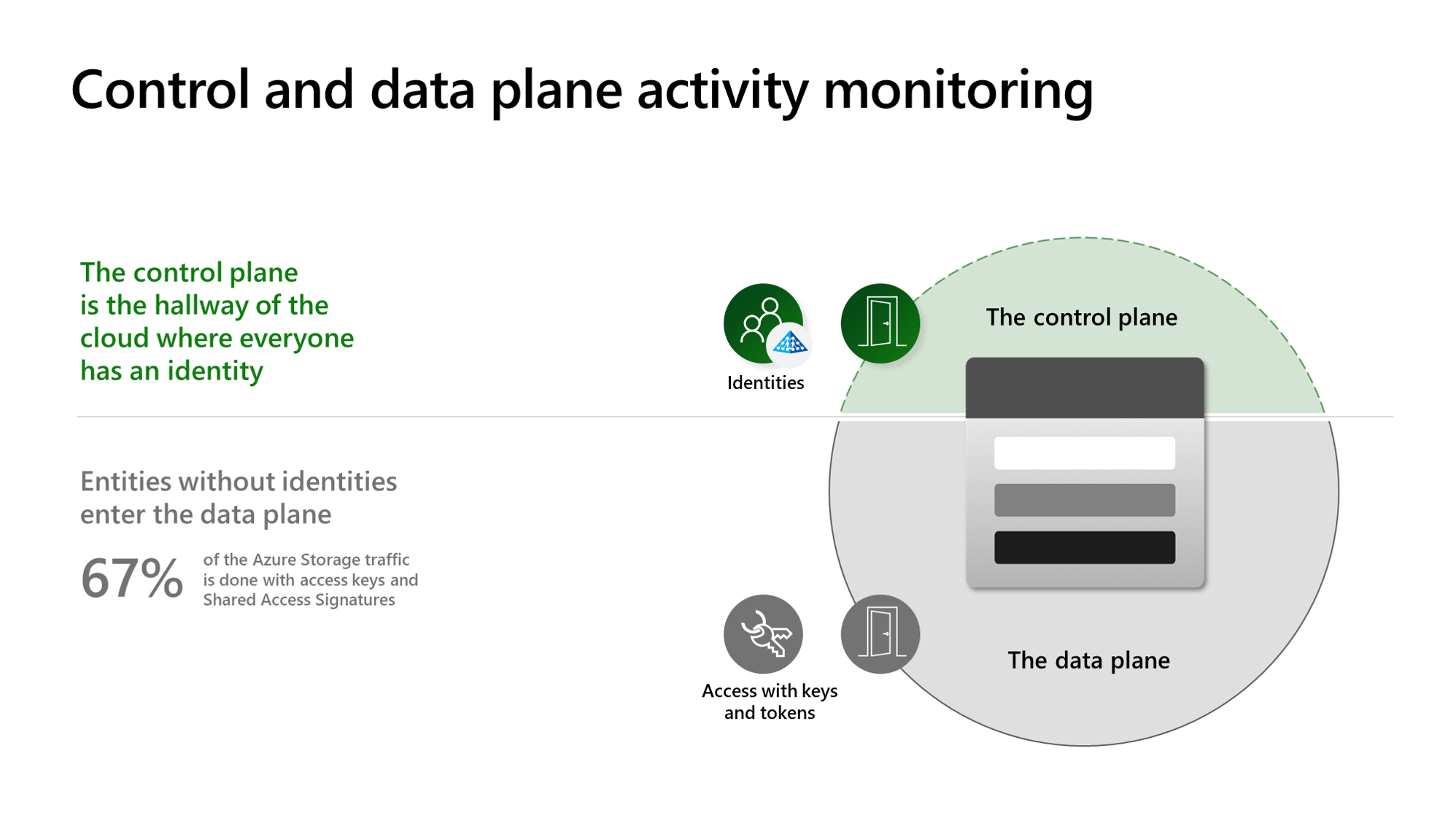
アクティビティの監視 - アクセス パターンと動作を分析して、ストレージ アカウントに関連する異常で有害なアクティビティを検出します。 これは、未承認のアクセス、データ流出の試行、およびその他のセキュリティ上の脅威を特定するために重要です。
機密データの脅威の検出 - 潜在的なセキュリティ上の脅威を示す可能性のある疑わしいアクティビティを検出することで、ストレージ アカウント内の機密データを特定して保護します。 Defender for Storage は、異常なデータ アクセス パターンや潜在的なデータ流出などのアクションを監視することで、Azure に格納されている機密情報のセキュリティを強化します。
マルウェアスキャン - 既知の脅威と疑わしいコンテンツのファイルを分析して、ストレージ アカウントのマルウェアをスキャンします。 これにより、Azure ストレージ アカウントに保存またはアップロードされる可能性がある悪意のあるファイルから潜在的なセキュリティ リスクを特定して軽減できます。 その結果、データ ストレージの全体的なセキュリティ体制が強化されます。
Defender for Storage は、サブスクリプション レベル、リソース レベル、または大規模でエージェントレスで有効にすることができます。
サブスクリプション レベルで Defender for Storage を有効にすると、そのサブスクリプション下の既存および新しく作成されたストレージ アカウントのすべてが、自動的に含まれて保護されます。 保護されたサブスクリプションから特定のストレージ アカウントを除外できます。
注意
Defender for Storage (クラシック) が有効になっていて、現在のセキュリティ機能と価格にアクセスする場合は、 新しい価格プランに移行する必要があります。
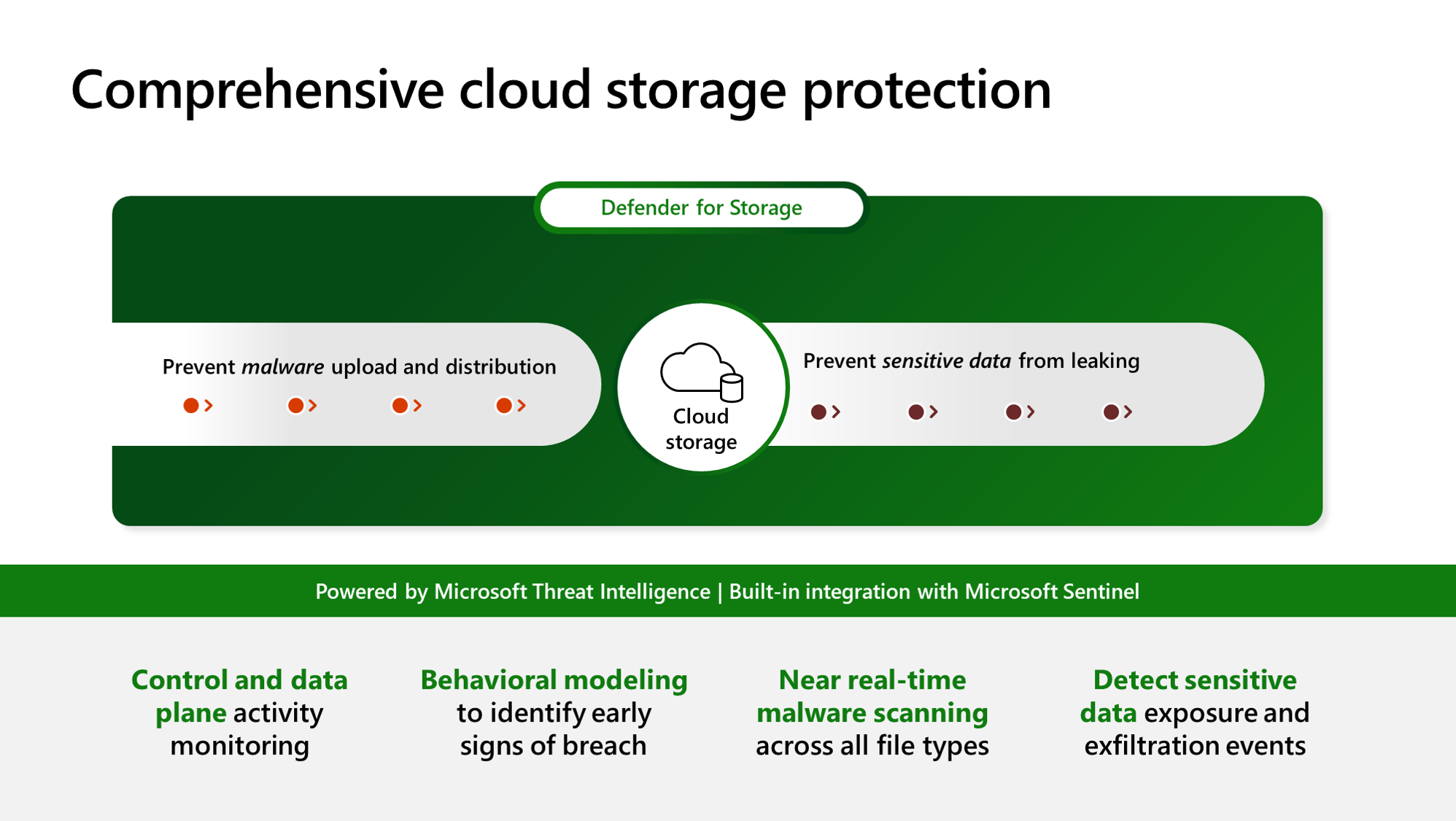
Defender for Storage には次の機能があります。
マルウェアに対する保護の強化: マルウェア スキャンでは、アップロードされたすべての BLOB のアーカイブを含め、ほぼリアルタイムですべてのファイルの種類が検出されます。 これにより、高速で信頼性の高い結果が得られ、ストレージ アカウントが脅威のエントリおよび配布ポイントとして機能するのを防ぐことができます。
マルウェア スキャンの詳細について確認してください。
脅威の検出と機密データの保護の強化: 機密データの脅威検出は、セキュリティ専門家がセキュリティ アラートに優先順位を付けて効率的に調査するのに役立ちます。 リスクのあるデータの機密性が考慮され、潜在的な脅威に対する検出と保護が向上します。 この機能は、最も重大なリスクを特定して対処することで、データ侵害の可能性を軽減します。 機密データを含むリソースに対する露出イベントと疑わしいアクティビティを検出することで、機密データ保護が向上します。
機密データの脅威検出の詳細について確認してください。
ID のないエンティティの検出: Defender for Storage は、誤って構成され、過度に制限された Shared Access Signature (SAS) を使用して、データにアクセスする ID のないエンティティからの疑わしいアクティビティを検出します。 これらの SAS が漏洩または侵害される可能性があります。 セキュリティを強化し、不正アクセスのリスクを軽減できます。 この機能により、アクティビティ監視セキュリティ アラート スイートが拡張されます。
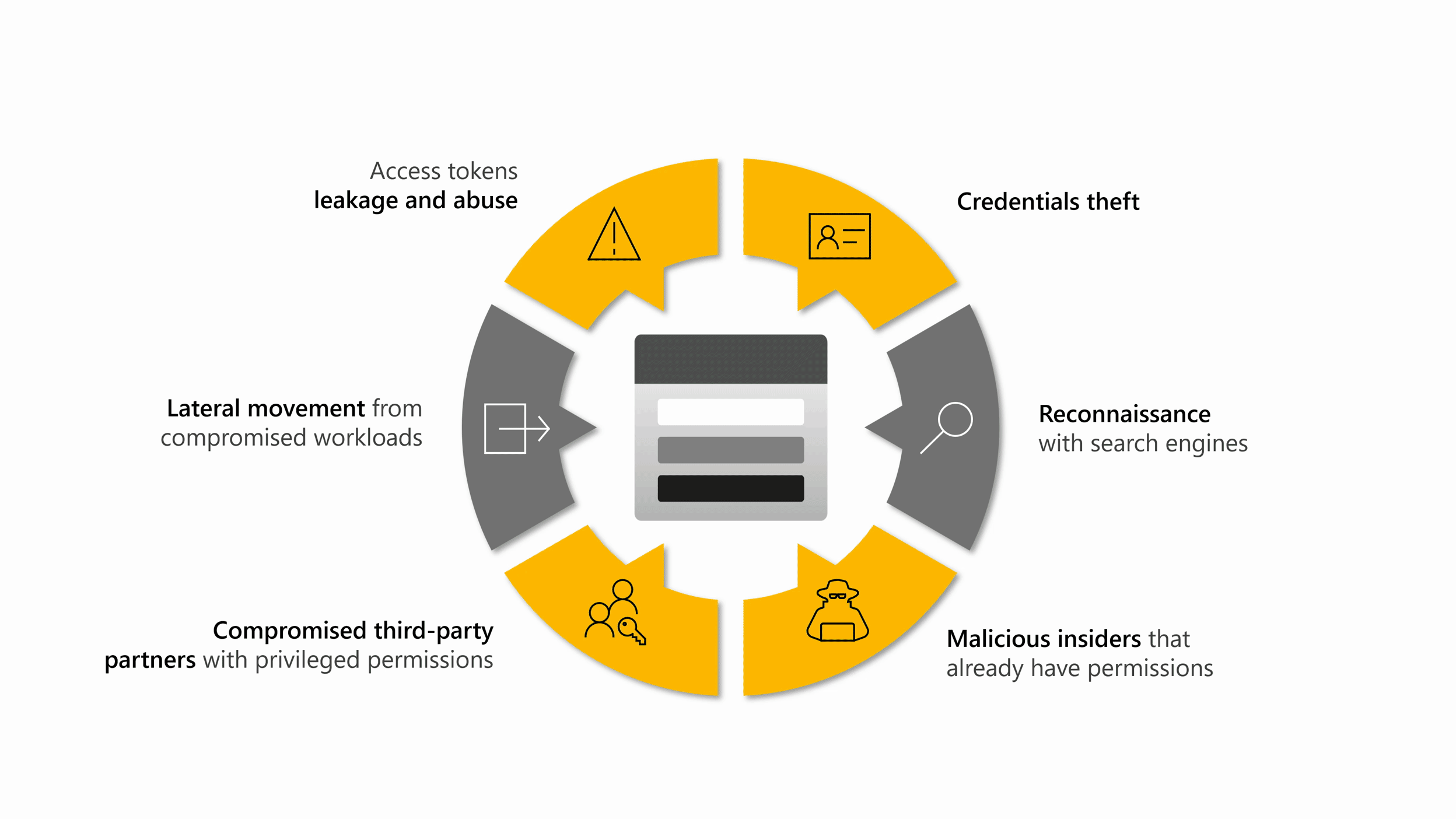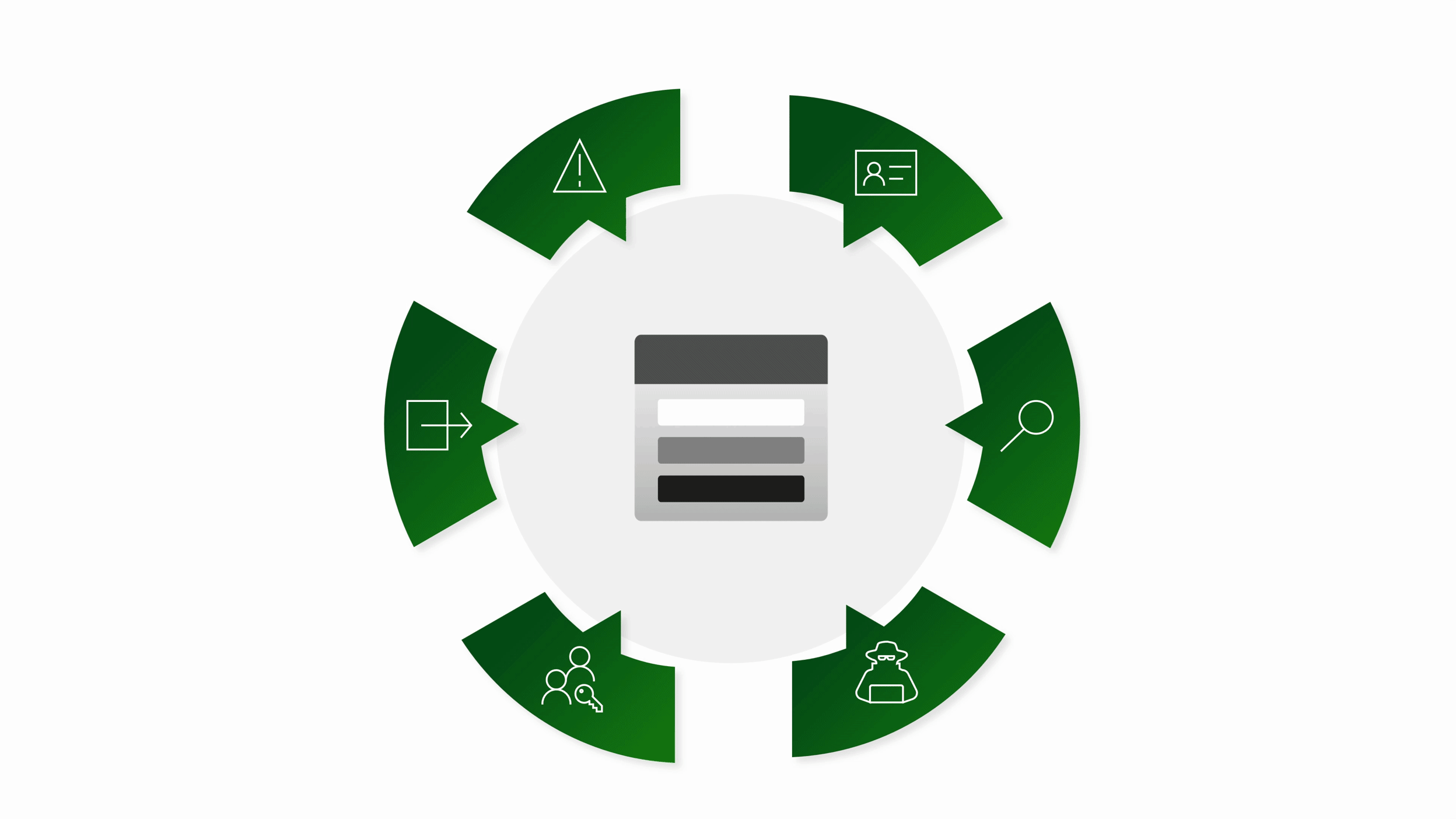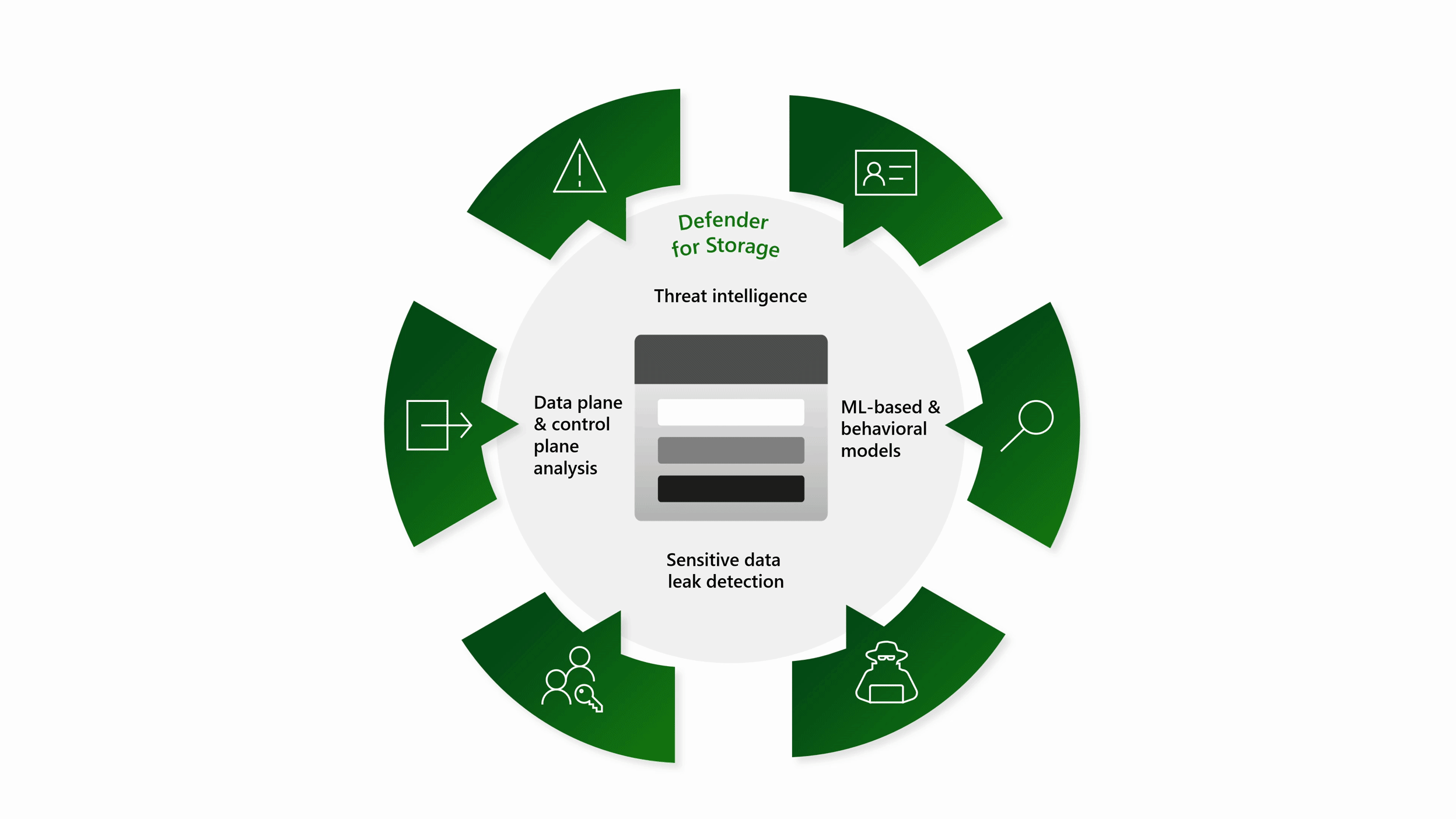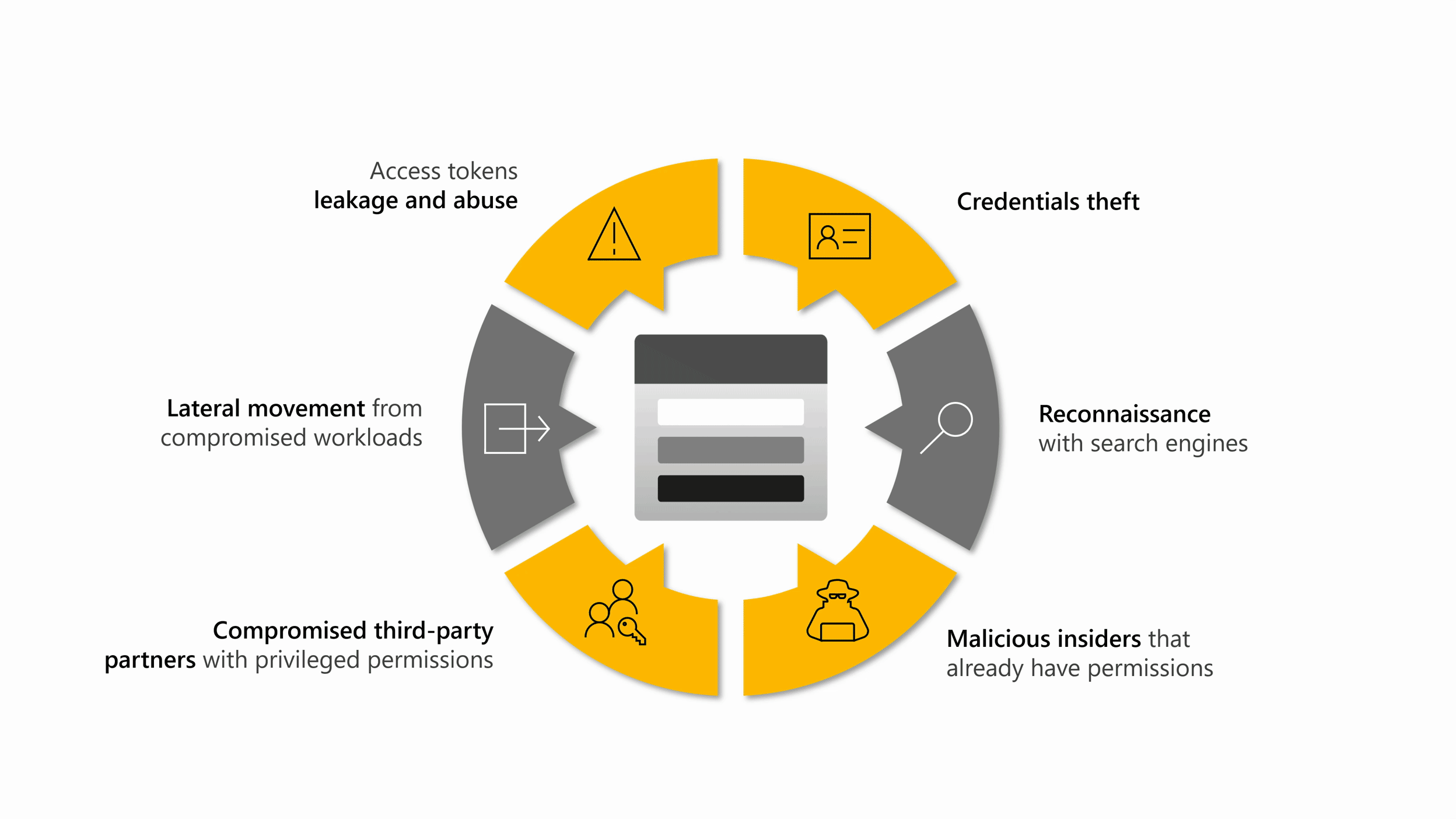
クラウド ストレージに関する上位の脅威を網羅: Defender for Storage では、Microsoft 脅威インテリジェンス、行動モデル、機械学習モデルを利用して、異常で疑わしいアクティビティを検出します。 Defender for Storage のセキュリティ アラートは、機密データの流出、データの破損、悪意のあるファイルのアップロードなど、クラウド ストレージに関する上位の脅威を対象としています。
ログを有効にせずに包括的なセキュリティ: Microsoft Defender for Storage を有効にすると、Azure Blob Storage、Azure Files、および Azure Data Lake Storage サービスからのデータと制御テレメトリ ストリームが継続的に分析されます。 分析のために診断ログを有効にする必要はありません。
大規模な摩擦なしの有効化: Microsoft Defender for Storage はエージェントレス ソリューションであり、デプロイが簡単で、ネイティブの Azure ソリューションを使用して大規模なセキュリティ保護を実現します。
Defender for Storage のしくみ
Defender for Storage は、保護されたストレージ アカウントからデータとコントロール プレーン ログを継続的に分析します。 セキュリティ上の利点のためにリソース ログを有効にする必要はありません。 Microsoft 脅威インテリジェンスは、悪意のある IP アドレス、Tor 出口ノード、潜在的に危険なアプリなどの疑わしい署名を識別します。 データ モデルを構築し、統計的および機械学習の方法を使用してベースライン アクティビティの異常を特定します。これは、悪意のある動作を示している可能性があります。 不審なアクティビティに関するセキュリティ アラートを受け取りますが、Defender for Storage では、同様のアラートをあまり多く受け取らないようにします。 アクティビティの監視は、パフォーマンス、インジェスト容量、またはデータ アクセスには影響しません。
マルウェア スキャン (Microsoft Defender ウイルス対策を利用)
Defender for Storage でのマルウェア スキャンでは、アップロードされたコンテンツに対してほぼリアルタイムで完全なマルウェア スキャンを実行し、Microsoft Defender ウイルス対策機能を適用することで、ストレージ アカウントを悪意のあるコンテンツから保護します。 信頼されていないコンテンツを処理するためのセキュリティとコンプライアンスの要件を満たします。 すべてのファイルの種類がスキャンされ、すべてのファイルの結果が返されます。 マルウェア スキャンはエージェントレス SaaS ソリューションであり、メンテナンスが不要な大規模な簡単なセットアップを可能にし、大規模な応答の自動化をサポートします。 マルウェア スキャンは、新しい Defender for Storage プランの構成可能な機能であり、スキャンされた GB あたりの価格が設定されます。
マルウェア スキャンの詳細について確認してください。
機密データの脅威検出は、セキュリティ チームがセキュリティ アラートの優先順位付けと調査を効率的に行うのに役立ちます。 リスクのあるデータの機密性が考慮され、検出が向上し、データ侵害が防止されます。 機密データの脅威検出は、機微なデータを含むリソースを検索するためにスマート サンプリング方法を使用するエージェントレス エンジンである機密データ検出を利用します。 機密データ検出は、Microsoft Purview の機密情報の種類 (SID) と分類ラベルと統合されるため、組織の秘密度設定をシームレスに継承できます。
機密データの脅威検出は、新しい Defender for Storage プランで構成可能な機能です。 追加コストなしで有効または無効にすることができます。 詳細については、「機密データの脅威検出」を参照してください。
新しい Microsoft Defender for Storage プランには、保護するストレージ アカウントの数に基づいて予測可能な価格が設定されています。 サブスクリプションまたはリソースのレベルで有効にし、保護されたサブスクリプションから特定のストレージ アカウントを除外するオプションにより、セキュリティの適用範囲を管理する柔軟性が向上しました。 価格プランを使用すると、コスト計算プロセスが簡素化され、ニーズの変化に応じて簡単にスケーリングできます。 大量のトランザクションがあるストレージ アカウントには、その他の料金が適用される場合があります。
Defender for Storage では、Azure Blob Storage ライフサイクル管理トランザクションを含む内部トランザクションも処理されます。 Defender for Storage は、ライフサイクル ポリシーによって生成されたトランザクションに対して課金される場合があります。
マルウェア スキャン - GB あたりの課金、月単位の上限設定、構成
マルウェア スキャンは、スキャンされたデータに対してギガバイト単位で課金されます。 コストの予測可能性を確保するために、ストレージ アカウントのスキャンされたデータ ボリュームごとに毎月の上限を設定できます。 この上限は、サブスクリプション全体に設定する (サブスクリプション内のすべてのストレージ アカウントに影響を及ぼす) ことも、個々のストレージ アカウントに適用することもできます。 保護されたサブスクリプションでは、制限が異なる特定のストレージ アカウントを設定できます。
既定では、ストレージ アカウントごとに 1 か月あたり 5,000 GB の制限が設定されています。 このしきい値を超えると、残りの BLOB のスキャンは 20 GB の信頼区間で停止します。 構成の詳細については、「 Defender for Storage の構成」を参照してください。
既定では、ストレージ アカウントごとに 1 か月あたり 5,000 GB の制限が設定されています。 このしきい値を超えると、残りの BLOB のスキャンは 20 GB の信頼区間で停止します。 構成の詳細については、「 Defender for Storage の構成」を参照してください。
重要
Defender for Storage でのマルウェア スキャンは、最初の 30 日間の試用版には無料で含まれていません。また、Defender for Cloud の 価格ページで利用可能な価格スキームに従って、最初の日から課金されます。 マルウェア スキャンでは、他の Azure サービス (Azure Storage の読み取り操作、Azure Storage BLOB インデックス作成、Azure Event Grid 通知) に対して追加料金が発生します。
Microsoft Defender for Storage は、細かい制御によって大規模なデータをセキュリティで保護します。 サブスクリプション内のすべてのストレージ アカウントに一貫したセキュリティ ポリシーを適用することも、ビジネス ニーズに合わせて特定のアカウント向けにポリシーをカスタマイズすることもできます。 各リソースに必要な保護レベルを選択することで、コストを制御できます。
「Defender for Storage を有効にする」を参照してください。
コストを効果的に管理しながら保護を中断しないようにするために、マルウェア スキャンの上限の使用に関連する 2 つのセキュリティ アラートがあります。 最初のアラート Malware scanning will stop soon: 75% of monthly gigabytes scan cap reached (Preview) は、使用が設定された月次上限の 75% に近づくとトリガーされ、必要に応じて上限を調整するための通知が提供されます。 2 つ目のアラート Malware scanning stopped: monthly gigabytes scan cap reached (Preview) では、上限に達してその月のスキャンが一時停止され、新しいアップロードがスキャンされないままになる可能性があるときに通知します。 どちらのアラートにも、影響を受けるストレージ アカウントに関する詳細が含まれており、アクションを促して通知するため、予期しない費用をかけずに目的のレベルのセキュリティを維持できます。
マルウェア スキャンとハッシュ評価分析の違いを理解する
Defender for Storage は、 マルウェア スキャン と ハッシュ評判分析を使用して、ストレージ アカウントにアップロードされた悪意のあるコンテンツを検出します。
マルウェア スキャンでは、Microsoft Defender ウイルス対策 (MDAV) を使用して Blob Storage にアップロードされた BLOB をスキャンし、詳細なファイル スキャンとハッシュ評判分析を含む包括的な分析を提供します。 この機能により、潜在的な脅威に対する検出が強化されます。
マルウェア スキャンは、新しいプランでのみ利用できる有料機能です。
ハッシュ評判分析では、新しくアップロードされた BLOB とファイルのハッシュ値と Microsoft Defender Threat Intelligence の既知のマルウェアのハッシュ値を比較することで、Blob Storage と Azure Files 内のマルウェアを検出します。 この機能では、すべてのファイル プロトコルと操作の種類がサポートされているわけではないため、一部の操作でマルウェアのアップロードが監視されません。 サポートされていないユース ケースには、SMB ファイル共有や、BLOB が Put Block と Put Block List を使用して作成される場合などがあります。 ハッシュ評価分析は、すべてのプランで利用できます。
要約すると、Blob Storage の新しいプランでのみ使用できるマルウェア スキャンは、マルウェア検出に対する包括的なアプローチを提供します。 これを実現するには、ファイルの完全なコンテンツを分析し、ハッシュ評判分析を手法に組み込みます。


