Configure Azure Active Directory for Web Portal - HPC Pack 2019
After deployment, you need to configure Azure Active Directory(Azure AD) for the HPC Azure Cluster Management (ACM) Web Portal to work with authentication. You can do this configuration by running a PowerShell script or by manual configuration in the Azure portal. Either way, you effectively create an Azure AD app and associate it with the HPC ACM Web Portal, which is an app of Azure App Service. You need the client id, client secret, and issuer url from the Azure AD app to use HPC ACM CLI.
Use a PowerShell script
You need a PowerShell environment to run the script. The easiest way is to use the PowerShell on Azure Cloud Shell. If you're using local PowerShell, make sure you have installed PowerShell modules AzureRM and AzureAD.
The script to run is https://github.com/Azure/hpcpack-acm/blob/master/src/deployment/SetupAAD.ps1. Save it as file SetupAAD.ps1 to the PowerShell environment you choose. In Cloud Shell, you could do it by using this command:
curl https://raw.githubusercontent.com/Azure/hpcpack-acm/app-service/src/deployment/SetupAAD.ps1 -o SetupAAD.ps1
Run ./SetupAAD.ps1 -? to show the parameters:
SetupAAD.ps1 [-SubscriptionId] <string> [-ResourceGroupName] <string> [-WebAppName] <string> [<CommonParameters>]
There're three required parameters:
SubscriptionId: The ID of Azure subscription in which the Web App for the HPC ACM Web Portal lives.ResourceGroupName: The name of the resource group in which the Web App lives.WebAppName: The name of the Web App for HPC ACM Web Portal.
When the script succeeds, it returns a hash object with three properties: IssuerUrl, ClientId, and ClientSecret. Save them for use in the HPC ACM CLI.
Configure in the Azure portal
Sign into the Azure Web Portal and navigate to the Web App for the HPC ACM Web Portal.
Select Authentication / Authorization under Settings and make these changes:
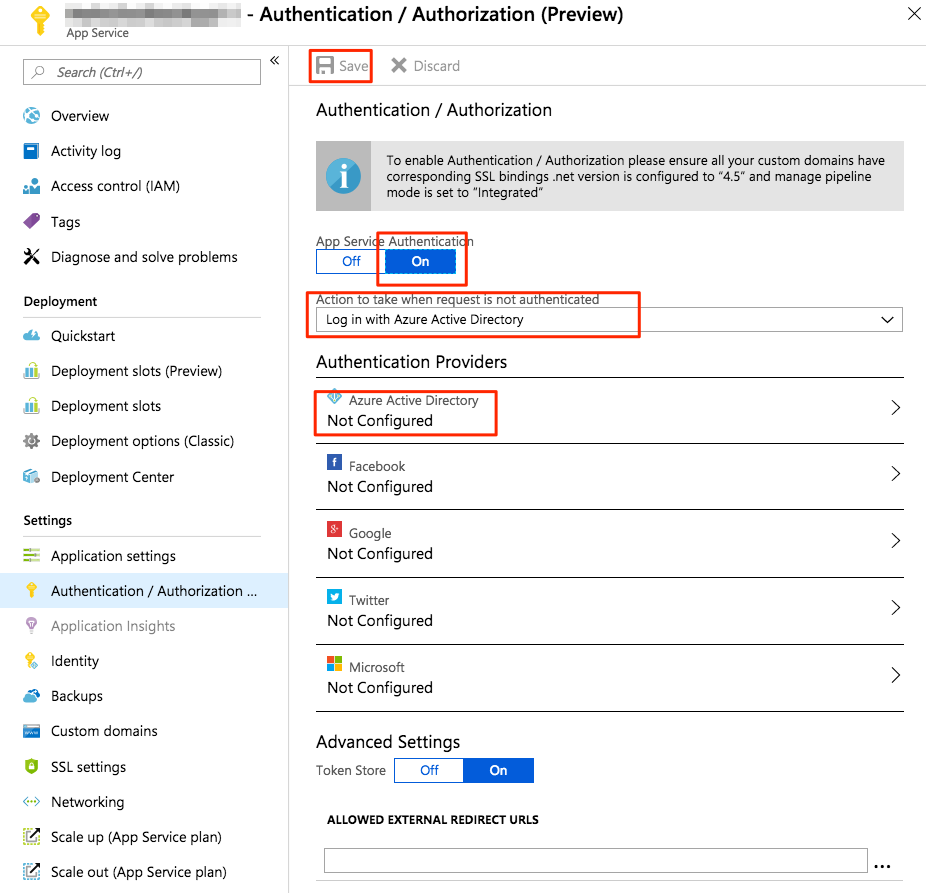
- Turn on App Service Authentication.
- Select Log in with Azure Active Directory for Action to take when request is not authenticated.
- Select and open Azure Active Directory for Authentication Providers for further configuration.
In the Azure Active Directory window, make these changes:
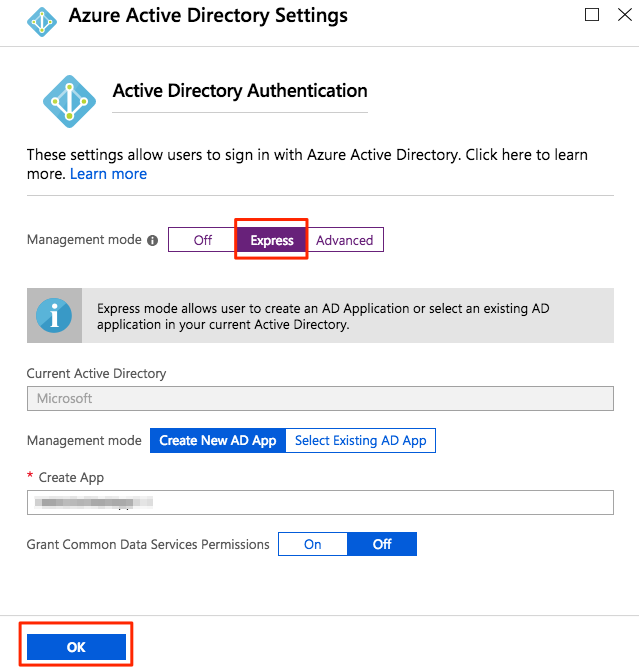
- Select Express for Management mode.
- Select OK
Select Save for the Authentication / Authorization window.
Note
If you want to use HPC ACM CLI, you need to get client ID, client secret, and issuer URL from the Azure AD app, as described in the next section.
Manage Azure Active Directory App
You might want to do some management work on the Azure AD app. For example, you need to get client ID, client secret, and issuer URL for use of HPC ACM CLI or you need to limit the access to the HPC ACM Web Portal to a given set of members in your organization. You can do the management work in the Azure portal.
Navigate to the Web App for the HPC ACM Web Portal. Then select Authentication / Authorization under Settings as above. Then select Azure Active Directory" from the list of Authentication Providers. It shows a UI similar to the following screenshot:
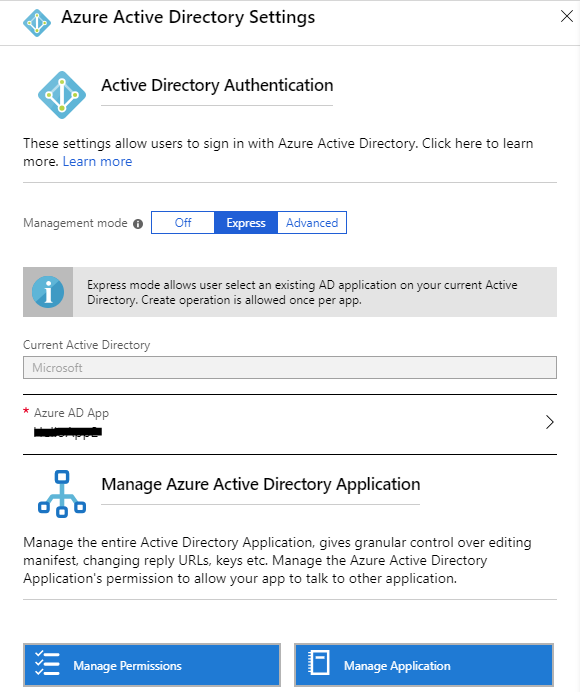
Select Advanced from the Management mode. It shows the Client ID, Issuer Url, and Client Secret:
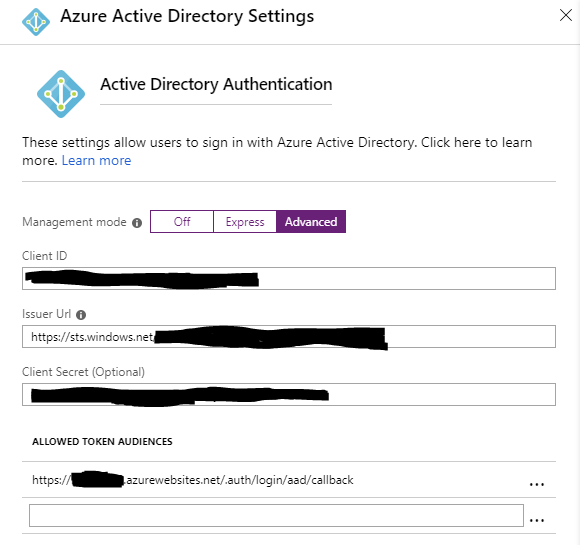
Go back to the Express" mode and select Manage Application, a page for settings of the Azure AD app that shows:
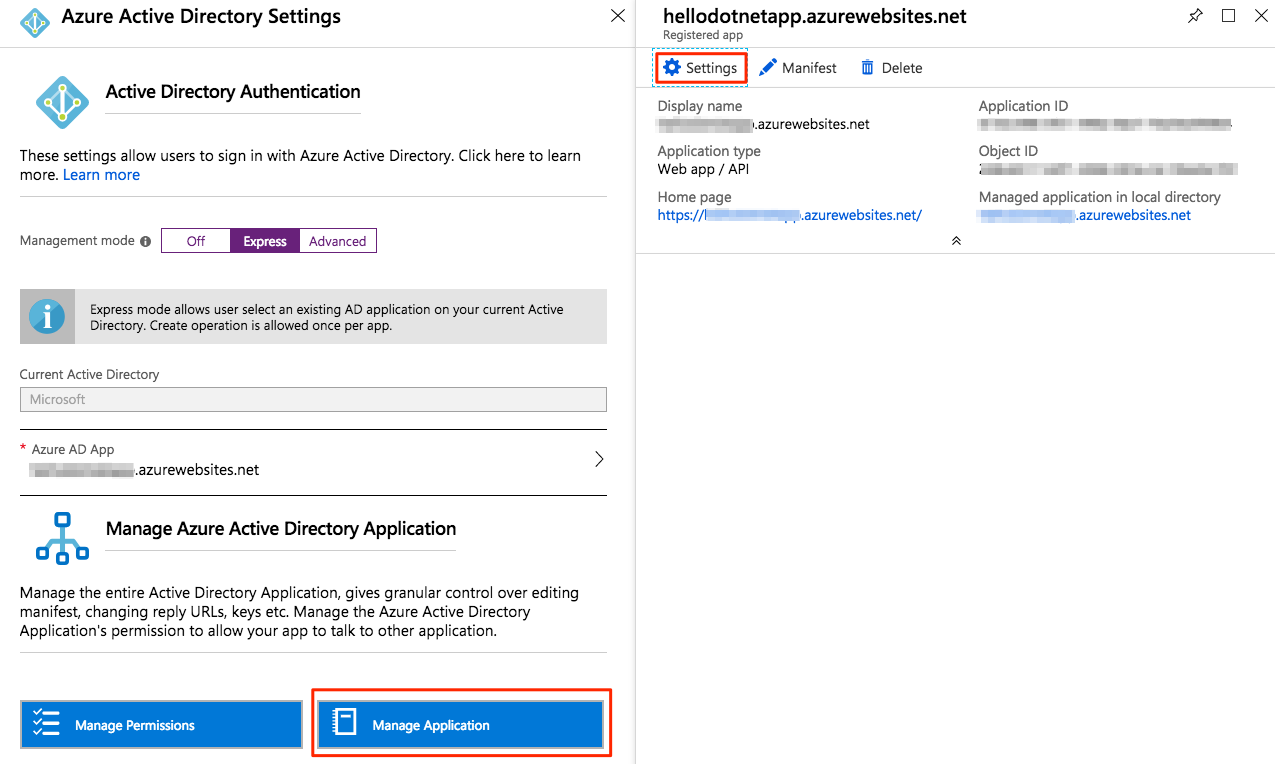
From there, you can do more management work, or explore more options to the Azure AD app.