Understand data lifecycle
Microsoft is committed to protecting the security of our customers' information. Microsoft implements a Defense-In-Depth strategy to protect customer data and support data against accidental, unauthorized, or unlawful access, disclosure, alteration, loss, or destruction. Our approach uses multiple layers of security and privacy controls to provide greater protection.
As an example, consider the topic of access control. Our account management systems enforce Zero Standing Access (ZSA) and facilitate Just-In-Time (JIT) access, implementing the principle of least privilege to protect our systems and customer information against unauthorized access. Additional complementary controls include only allowing connections to the production environment from authorized Secure Access Workstations, multifactor authentication to verify the identity of engineers, strong encryption to protect data-at-rest and data-in-transit, and extensive logging and monitoring to detect suspicious behavior and escalate potential incidents using our security incident response process.
Microsoft's Defense-In-Depth protects data through the entire data lifecycle, beginning with data collection and ending with its destruction when data is no longer needed.
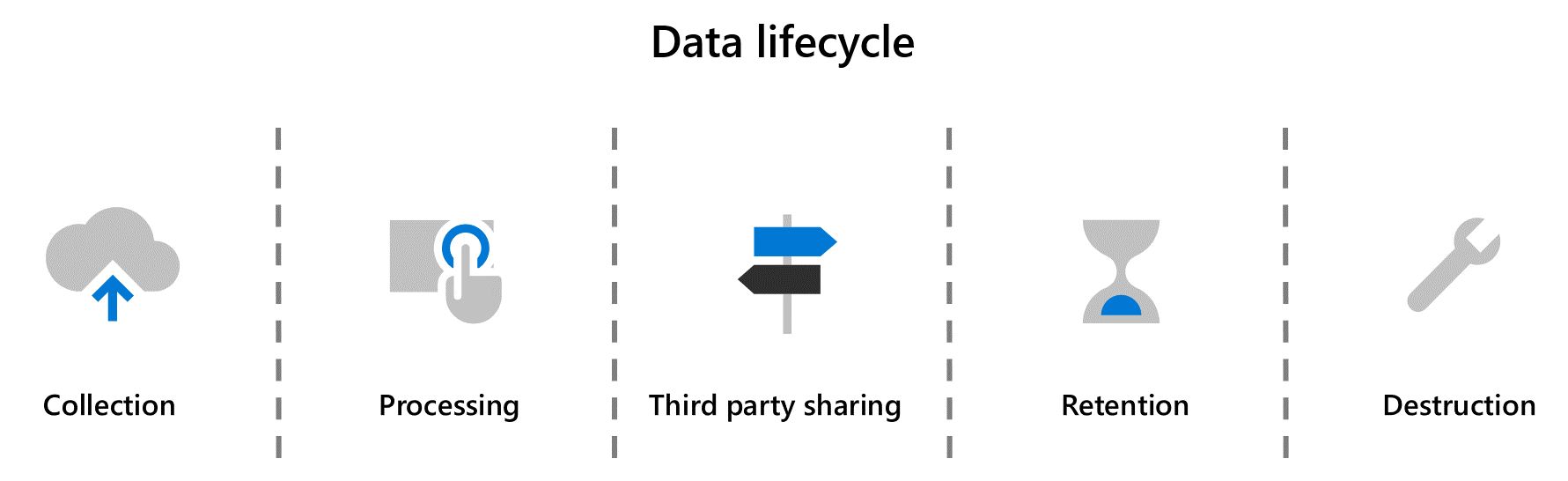
- Collection – Collection begins the data lifecycle and describes the receipt of data by an organization.
- Processing – Processing refers to any action performed on collected data, whether automated or manual.
- Third-party sharing – Third-party sharing is the sharing or onward disclosure of data to third parties.
- Retention – Retention is the persistence of data beyond initial collection. Retention covers data storage locations and data stored in databases.
- Destruction – Destruction marks the end of the data lifecycle. Data destruction follows a defined process for when a customer subscription ends or when there is an active deletion of data by a user or administrator.
Now that you understand the data lifecycle at a high level, we will explore each phase in more detail.