提交在 Microsoft Entra 应用程序库中发布应用程序的请求
可以在 Microsoft Entra 应用程序库中发布开发的应用程序,该库是数千个应用的目录。 发布应用程序后,用户可以公开使用并添加到其租户中。 有关详细信息,请参阅 Microsoft Entra 应用程序库概述。
若要在 Microsoft Entra 库中发布应用程序,需要完成以下任务:
- 确保完成先决条件。
- 创建并发布文档。
- 提交你的应用程序。
- 加入 Microsoft 合作伙伴网络。
先决条件
若要在库中发布应用程序,必须首先阅读并同意具体的条款和条件。
- 实现对单一登录 (SSO) 的支持。 若要了解有关支持的选项的详细信息,请参阅计划单一登录部署。
对于密码 SSO,请确保你的应用程序支持窗体身份验证,以便可以进行密码保管,从而可以使用密码保管。
对于联合应用程序 (SAML/WS-Fed),应用程序最好支持软件即服务 (SaaS) 模型,但这不是必需的,它也可以是本地应用程序。 企业库应用程序必须支持多个用户配置,而不能仅支持某个特定用户。
对于 OpenID Connect,大多数应用程序都可以作为实现 Microsoft Entra 同意框架的多租户应用程序正常运行。 请参阅此链接,以便将应用程序转换为多租户应用程序。 如果应用程序需要额外的每实例配置(例如客户需要控制自己的机密和证书),则可发布单租户 Open ID Connect 应用程序。
- 预配是可选设置,但强烈建议。 若要详细了解 Microsoft Entra SCIM,请参阅生成 SCIM 终结点并使用 Microsoft Entra ID 配置用户预配。
可以免费注册测试开发帐户。 可免费使用 90 天,并且可获得其所有高级 Microsoft Entra 功能。 如果你使用该帐户进行开发,也可以扩展该帐户:加入 Microsoft 365 开发人员计划。
创建并发布文档
为站点提供应用文档
对于针对企业软件做出决策的决策者来说,易于采用是一个重要因素。 清晰易懂的文档有助于用户采用技术和支持成本的缩减。
创建至少包含以下信息的文档:
- SSO 功能简介
- 协议
- 版本和 SKU
- 支持的标识提供者列表及文档链接
- 应用程序的许可信息
- 用于配置 SSO 的基于角色的访问控制
- SSO 配置步骤
- SAML 的 UI 配置元素,以及提供商的预期值
- 要传递给标识提供者的服务提供商信息
- 如果使用的是 OIDC/OAuth,则需要用户同意才可授予的权限的列表以及业务理由
- 试点用户的测试步骤
- 故障排除信息,包括错误代码和消息
- 针对用户的支持机制
- 有关 SCIM 终结点的详细信息,包括支持的资源和特性
Microsoft 站点上的应用文档
向库中添加 SAML 应用程序时,会创建一个文档,用于说明分步过程。 有关示例,请参阅用于将 SaaS 应用程序与 Microsoft Entra ID 集成的教程。 此文档是根据提交给库的内容创建的。 如果使用 GitHub 帐户对应用程序进行更改,则可以轻松更新文档。
对于 OIDC 应用程序,没有特定于应用程序的文档,我们只有面向所有 OpenID Connect 应用程序的通用教程。
提交你的应用程序
在进行了测试并确认你的应用程序可在 Microsoft Entra ID 中正常工作后,请在 Microsoft 应用程序网络门户中提交应用程序请求。 首次尝试登录到该门户时,你会看到以下两个屏幕之一。
- 如果你收到“不起作用”消息,则需要联系 Microsoft Entra SSO 集成团队。 请提供要用于提交该请求的电子邮件帐户。 最好是类似于
name@yourbusiness.com的业务电子邮件地址。 Microsoft Entra 团队随后会在 Microsoft 应用程序网络门户中添加该帐户。 - 如果你看到“请求访问权限”页,请填写业务理由,然后选择“请求访问权限”。
添加帐户后,可以登录到 Microsoft 应用程序网络门户,然后在主页上选择“提交请求(ISV)”磁贴来提交请求。 如果在登录时看到“登录已被阻止”错误,请参阅 Microsoft 应用程序网络门户登录故障排除。
特定于实现的选项
在应用程序注册表中,选择要启用的功能。 根据应用程序支持的功能,选择“OpenID Connect 和 OAuth 2.0”、“SAML 2.0/WS-Fed”或“密码 SSO(用户名和密码)”。
如果你要为用户预配实现 SCIM 2.0 终结点,请选择“用户预配 (SCIM 2.0)”。 下载要在上架请求中提供的架构。 有关详细信息,请参阅导出预配配置并回退到已知良好状态。 在测试非库应用程序以构建库应用程序时,将使用你配置的架构。
如果你希望在 Microsoft Entra 应用程序库中注册 MDM 应用程序,请选择“注册 MDM 应用”。
可以在 Microsoft 应用程序网络门户上按客户名称跟踪应用程序请求。 有关详细信息,请参阅客户发出的应用程序请求。
时间线
将 SAML 2.0 或 WS-Fed 应用程序列入库中需要 12 到 15 个工作日。
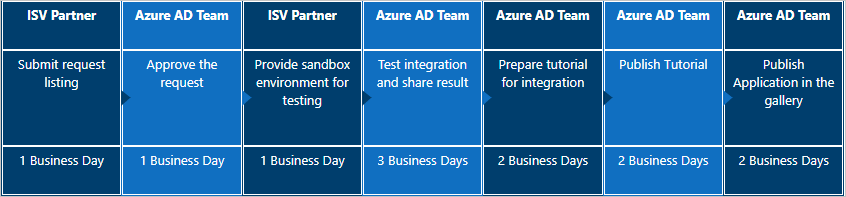
将 OpenID Connect 应用程序列入库中需要 7 到 10 个工作日。

在库中列出 SCIM 预配应用程序的方式因多种因素而异。
并非所有应用程序都可以上架。 根据条款和条件,可能会决定不列出某个应用程序。 应用程序能否上架完全取决于上架团队的决定。
下面是客户请求的应用程序的流。

要上报任何类型的问题,请向 Microsoft Entra SSO 集成团队发送电子邮件。 通常会迅速收到回复。
从库中更新或删除应用程序
可以在 Microsoft 应用程序网络门户中提交应用程序更新请求。 首次尝试登录到该门户时,你会看到以下两个屏幕之一。
如果你收到“不起作用”消息,则需要联系 Microsoft Entra SSO 集成团队。 请提供要用于提交该请求的电子邮件帐户。 最好是类似于
name@yourbusiness.com的业务电子邮件地址。 Microsoft Entra 团队随后会在 Microsoft 应用程序网络门户中添加该帐户。如果你看到“请求访问权限”页,请填写业务理由,然后选择“请求访问权限”。
添加帐户后,可以登录到 Microsoft 应用程序网络门户,通过选择主页上的“提交请求(ISV)”磁贴提交请求,选择“在库中更新我的应用程序列表”,然后相应地选择以下选项之一 -
如果你想要更新应用程序 SSO 功能,请选择“更新我的应用程序的联合 SSO 功能”。
如果你想要更新密码 SSO 功能,请选择“更新我的应用程序的密码 SSO 功能”。
如果你想要将列表从密码 SSO 升级到联合 SSO,请选择“将我的应用程序从密码 SSO 升级到联合 SSO”。
如果你想要更新 MDM 列表,请选择“更新我的 MDM 应用”。
如果你想要改进用户预配功能,请选择“改进我的应用程序的用户预配功能”。
如果你想要从 Microsoft Entra 应用程序库中删除应用程序,请选择“从库中删除我的应用程序列表”。
如果在登录时看到“登录已被阻止”错误,请参阅 Microsoft 应用程序网络门户登录故障排除。
加入 Microsoft 合作伙伴网络
在 Microsoft 合作伙伴网络中,可以即时访问专用的计划、工具、连接和资源。 若要加入该网络并创建面市计划,请参阅与商业客户取得联系。
后续步骤
- 在什么是 Microsoft Entra ID 中的应用程序管理?中详细了解如何管理企业应用程序。