配置 Microsoft Entra 混合加入
将设备引入 Microsoft Entra ID 可通过云和本地资源中的单一登录 (SSO) 最大程度地提高用户的工作效率。 同时,可以使用条件访问保护对资源的访问。
先决条件
- Microsoft Entra Connect 1.1.819.0 或更高版本。
- 请勿从 Microsoft Entra Connect 同步配置中排除默认设备属性。 若要详细了解同步到 Microsoft Entra ID 的默认设备属性,请参阅 Microsoft Entra Connect 同步的属性。
- 如果要进行混合 Microsoft Entra 联接的设备的计算机对象属于特定的组织单位 (OU),请配置在 Microsoft Entra Connect 中同步所需的正确 OU。 若要详细了解如何使用 Microsoft Entra Connect 同步计算机对象,请参阅基于组织单位的筛选。
- Microsoft Entra 租户混合标识管理员凭据。
- 每个本地 Active Directory 域服务林的企业管理员凭据。
- (联合域)至少为安装了 Active Directory 联合身份验证服务的 Windows Server 2012 R2。
- 用户可以使用 Microsoft Entra ID 注册设备。 可以在配置设备设置一文的“配置设备设置”标题下找到有关此设置的详细信息。
网络连接要求
Microsoft Entra 混合联接要求设备能够从组织的网络中访问以下 Microsoft 资源:
https://enterpriseregistration.windows.nethttps://login.microsoftonline.comhttps://device.login.microsoftonline.comhttps://autologon.microsoftazuread-sso.com(如果使用或计划使用无缝 SSO)- 组织的安全令牌服务 (STS)(联合域)
警告
如果组织使用针对数据丢失防护或 Microsoft Entra 租户限制等方案拦截 SSL 流量的代理服务器,请确保在 TLS 中断和检查中排除发往“https://device.login.microsoftonline.com”的流量。 未能排除此 URL 可能会导致干扰客户端证书身份验证,从而导致设备注册和基于设备的条件访问出现问题。
如果你的组织需要通过出站代理访问 Internet,你可使用 Web 代理自动发现 (WPAD),使 Windows 10 或更新版本计算机能够在 Microsoft Entra ID 中进行设备注册。 若要解决在配置和管理 WPAD 时遇到问题,请参阅排查自动检测的问题。
从 Windows 10 1709 开始,如果不使用 WPAD,则可以在计算机上通过组策略对象 (GPO) 配置 WinHTTP 代理设置。 有关详细信息,请参阅 GPO 部署的 WinHTTP 代理设置。
注意
如果使用 WinHTTP 设置在计算机上配置代理设置,则无法连接到所配置的代理的任何计算机将无法连接到 Internet。
如果组织需要通过经身份验证的出站代理访问 Internet,请确保 Windows 10 或更新版本计算机能够成功对出站代理进行身份验证。 由于 Windows 10 或更新版本计算机使用计算机上下文运行设备注册,因此请使用计算机上下文配置出站代理身份验证。 根据配置要求使用相应的出站代理提供程序。
使用测试设备注册连接脚本验证设备是否能够访问系统帐户下的必需 Microsoft 资源。
托管域
我们认为大多数组织会通过托管域部署 Microsoft Entra 混合联接。 托管域将结合无缝单一登录来使用密码哈希同步 (PHS) 或直通身份验证 (PTA)。 托管域方案不需要配置联合服务器。
使用 Microsoft Entra Connect 为托管域配置Microsoft Entra 混合联接:
打开 Microsoft Entra Connect,然后选择“配置”。
在“其他任务”中,依次选择“配置设备选项”、“下一步”。
在“概述”中选择“下一步”。
在“连接到 Microsoft Entra ID”中,输入 Microsoft Entra 租户混合标识管理员的凭据。
在“设备选项”中,依次选择“配置 Microsoft Entra 混合联接”、“下一步”。
在“设备操作系统”中选择 Active Directory 环境中设备使用的操作系统,然后选择“下一步”。
在“SCP 配置”中,对于你希望 Microsoft Entra Connect 在其中配置服务连接点 (SCP) 的每个林,请完成以下步骤,然后选择“下一步”。
- 选择“林”。
- 选择“身份验证服务”。
- 单击“添加”,输入企业管理员凭据。
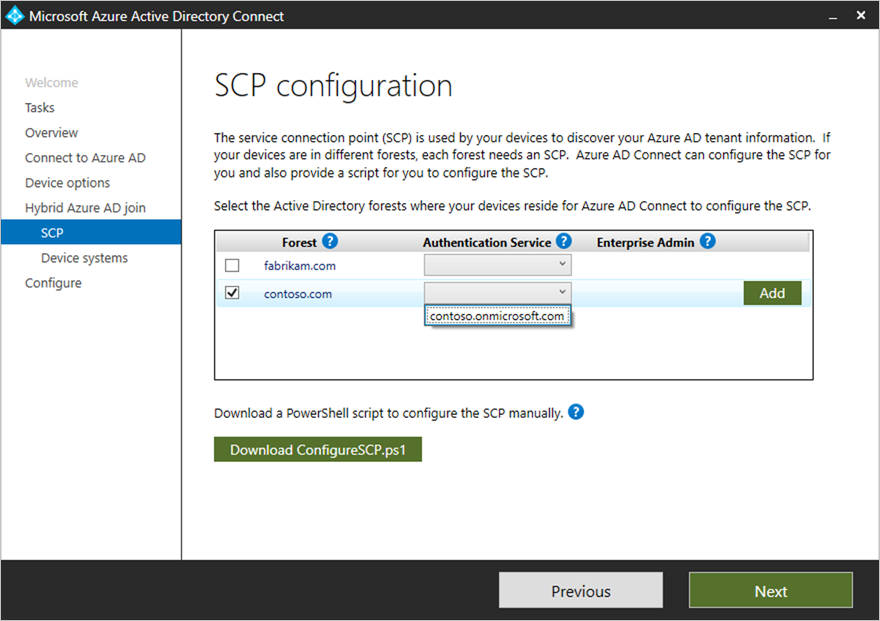
在“已准备好配置”中选择“配置”。
在“配置完成”中选择“退出”。
联合域
联合环境应具有支持以下要求的标识提供者。 如果已有使用 Active Directory 联合身份验证服务 (AD FS) 的联合环境,则已经支持以下要求。
- WIAORMULTIAUTHN 声明: 此声明是为 Windows 下层设备执行 Microsoft Entra 混合联接所必需的。
- WS-Trust 协议: 使用 Microsoft Entra ID 对当前 Microsoft Entra 混合联接的 Windows 设备进行身份验证时需要此协议。 使用 AD FS 时,需要启用以下 WS-Trust 终结点:
/adfs/services/trust/2005/windowstransport/adfs/services/trust/13/windowstransport/adfs/services/trust/2005/usernamemixed/adfs/services/trust/13/usernamemixed/adfs/services/trust/2005/certificatemixed/adfs/services/trust/13/certificatemixed
警告
adfs/services/trust/2005/windowstransport 和 adfs/services/trust/13/windowstransport 应仅作为面向 Intranet 的终结点启用,不能通过 Web 应用程序代理作为面向 Extranet 的终结点公开。 若要详细了解如何禁用 WS-Trust Windows 终结点,请参阅在代理上禁用 WS-Trust Windows 终结点。 可以通过 AD FS 管理控制台中的“服务”“终结点”查看已启用哪些终结点。
使用 Microsoft Entra Connect 为联合环境配置Microsoft Entra 混合联接:
打开 Microsoft Entra Connect,然后选择“配置”。
在“其他任务”页上,选择“配置设备选项”,然后选择“下一步”。
在“概述”页上,选择“下一步”。
在“连接到 Microsoft Entra ID”页面上,输入 Microsoft Entra 租户混合标识管理员的凭据,然后选择“下一步”。
在“设备选项”页面上,依次选择“配置 Microsoft Entra 混合联接”、“下一步”。
在“SCP”页面上,完成以下步骤,然后选择“下一步” :
- 选择林。
- 选择身份验证服务。 除非你的组织仅有 Windows 10 或更新版本客户端,并且你已配置计算机/设备同步,或者你的组织使用无缝 SSO,否则必须选择“AD FS 服务器”。
- 单击“添加”,输入企业管理员凭据。

在“设备操作系统”页面上,选择 Active Directory 环境中设备使用的操作系统,然后选择“下一步” 。
在“联合身份验证配置”页上,输入 AD FS 管理员的凭据,然后选择“下一步”。
在“已准备好进行配置”页上,选择“配置”。
在“配置完成”页上,选择“退出”。
联合注意事项
对于 Windows 10 1803 或更新版本,如果联合环境使用 AD FS 瞬时执行 Microsoft Entra 混合联接失败,则我们会依赖 Microsoft Entra Connect 同步 Microsoft Entra ID 中的计算机对象,以完成 Microsoft Entra 混合联接的设备注册。
其他方案
组织可以在其环境的子集上测试 Microsoft Entra 混合联接,然后再完全推出。 可以在 Microsoft Entra 混合联接目标部署一文中找到完成目标部署的步骤。 组织应在此试点组中包含不同角色和配置文件的用户示例。 设定目标的推出有助于在为整个组织启用之前,确定计划可能未解决的任何问题。
一些组织可能无法使用 Microsoft Entra Connect 来配置 AD FS。 手动配置声明的步骤可在手动配置 Microsoft Entra混合联接一文中找到。
美国政府云(包括 GCCHigh 和 DoD)
对于 Azure 政府中的组织,Microsoft Entra 混合联接要求设备能够从组织的网络中访问以下 Microsoft 资源:
https://enterpriseregistration.windows.net和https://enterpriseregistration.microsoftonline.ushttps://login.microsoftonline.ushttps://device.login.microsoftonline.ushttps://autologon.microsoft.us(如果使用或计划使用无缝 SSO)
Microsoft Entra 混合加入故障排除
如果在完成已加入域的 Windows 设备的 Microsoft Entra 混合联接方面遇到问题,请参阅:
- 使用 dsregcmd 命令排查设备问题
- 排查已加入 Microsoft Entra 混合的 Windows 当前设备的问题
- 排查已加入 Microsoft Entra 混合的 Windows 下层设备的问题
- 排查挂起的设备状态问题