你当前正在访问 Microsoft Azure Global Edition 技术文档网站。 如果需要访问由世纪互联运营的 Microsoft Azure 中国技术文档网站,请访问 https://docs.azure.cn。
在 Azure 应用服务中添加和管理 TLS/SSL 证书
可以添加数字安全证书,以在应用程序代码中使用或在 Azure 应用服务 中保护自定义 DNS 名称,该证书提供了高度可缩放、自我修补的 Web 托管服务。 目前称为传输层安全性 (TLS) 证书,以前也称为安全套接字层 (SSL) 证书,这些专用或公用证书通过加密浏览器、访问的网站和网站服务器之间发送的数据来帮助保护 Internet 连接。
下表列出了可用于在应用服务中添加证书的选项:
| 选项 | 说明 |
|---|---|
| 创建免费应用服务托管证书 | 免费且易于使用的专用证书,用于只需保护应用服务中的自定义域的情形。 |
| 导入应用服务证书 | 由 Azure 管理的私有证书。 它结合了自动化证书管理的简单性以及续订和导出选项的灵活性。 |
| 导入来自 Key Vault 的证书 | 如果使用 Azure Key Vault 管理 PKCS12 证书,则非常有用。 请参阅私有证书要求。 |
| 上传私有证书 | 如果你已有第三方提供商提供的私有证书,则可以上传它。 请参阅私有证书要求。 |
| 上传公用证书 | 公用证书不用于保护自定义域,但可以将其加载到代码中(如果需要它们来访问远程资源)。 |
先决条件
创建应用服务应用。 应用的应用服务计划必须位于“基本”、“标准”、“高级”或“独立”层。 请参阅纵向扩展应用以更新层级。
对于专用证书,请确保它满足所有的应用服务要求。
仅适用于免费证书:
请将需要证书的域映射到应用服务。 如需相关信息,请参阅教程:将现有的自定义 DNS 名称映射到 Azure 应用服务。
对于根域(如 contoso.com),请确保应用未配置任何 IP 限制。 为根域创建证书以及定期续订该证书都依赖于可从 Internet 访问的应用。
私有证书要求
免费应用服务托管证书和应用服务证书已满足应用服务的要求。 如果选择将私有证书上传或导入到应用服务,则证书必须满足以下要求:
- 导出为受密码保护的 PFX 文件(使用三重 DES 进行加密)。
- 包含长度至少为 2048 位的私钥
- 包含证书链中的所有中间证书和根证书。
若要保护 TLS 绑定中的自定义域,证书还有其他要求:
- 包含用于服务器身份验证的扩展密钥用法 (OID = 1.3.6.1.5.5.7.3.1)
- 已由受信任的证书颁发机构签名
注意
椭圆曲线加密 (ECC) 证书适用于应用服务,但本文不予讨论。 有关创建 ECC 证书的具体步骤,请咨询证书颁发机构。
注意
将专用证书添加到应用后,证书将存储在与应用服务计划的资源组、区域和操作系统组合(在内部称为 Web 空间)绑定的部署单元中。 通过此操作,同一资源组、区域和操作系统组合中的其他应用也可以访问该证书。 上传或导入到应用服务的专用证书与同一部署单元中的应用服务共享。
每个 Web 空间最多可添加 1000 个专用证书。
创建免费托管证书
免费应用服务托管证书是用于保护应用服务中的自定义 DNS 名称的统包解决方案。 此 TLS/SSL 服务器证书由应用服务完全管理,并在到期前 45 天以六个月为增量连续自动续订,前提是先决条件设置保持不变,无需你执行任何操作。 所有关联的绑定都使用续订的证书进行更新。 你创建证书并将其绑定到自定义域,然后让应用服务执行其余操作。
重要
在创建免费托管证书之前,请先确保已满足应用的先决条件。
免费证书由 DigiCert 颁发。 对于某些域,必须通过创建值为 0 issue digicert.com 的 CAA 域记录显式允许 DigiCert 作为证书颁发者。
Azure 代表你完全管理证书,因此可以随时更改托管证书的任何方面(包括根证书颁发者)。 这些更改不受你控制。 请确保避免硬性依赖和将做法证书“固定”到托管证书或证书层次结构的任何部分。 如果需要证书固定行为,请使用本文中的其他任何可用方法将证书添加到自定义域。
免费证书具有以下限制:
- 不支持通配符证书。
- 不支持使用已计划弃用和删除的证书指纹作为客户端证书。
- 不支持专用 DNS。
- 不可导出。
- 在应用服务环境 (ASE) 中不受支持。
- 仅支持字母数字字符、破折号 (-) 和句点 (.)。
- 仅支持长度不超过 64 个字符的自定义域。
在 Azure 门户的左侧菜单中,选择“应用程序服务”>“<app-name>”。
在应用的导航菜单上,选择“证书”。 在“托管证书”窗格中,选择“添加证书”。
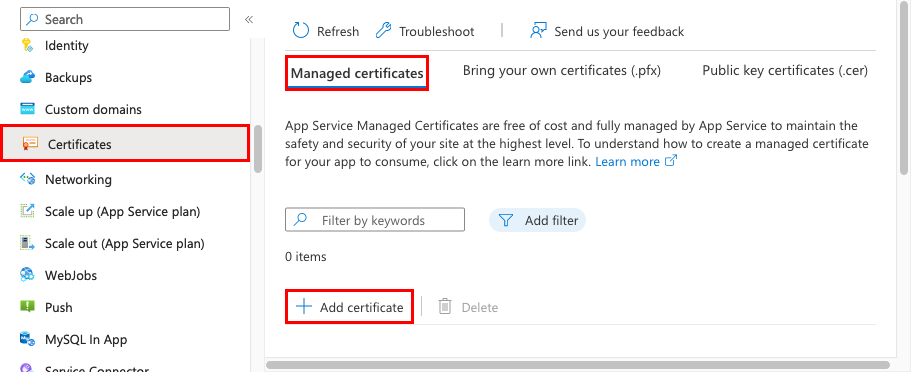
选择免费证书的自定义域,然后选择“验证”。 验证完成后,请选择“添加”。 只能为每个受支持的自定义域创建一个托管证书。
操作完成后,证书会显示在“托管证书”列表中。
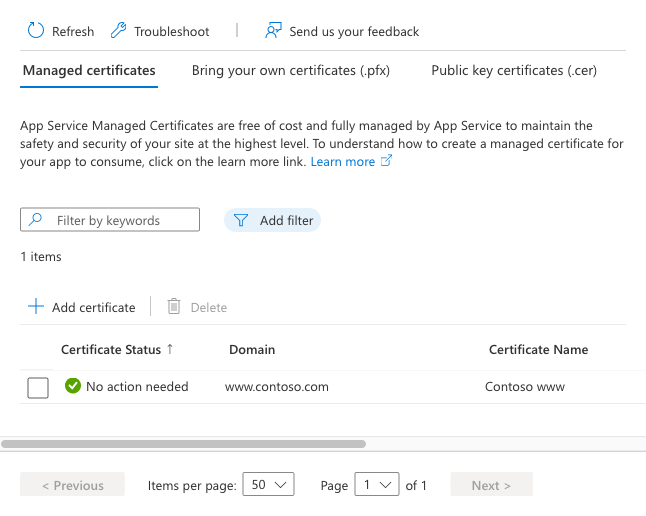
若要使用此证书保护自定义域,仍需要创建证书绑定。 在 Azure 应用服务中使用 TLS/SSL 绑定保护自定义 DNS 名称。
导入应用服务证书
若要导入应用服务证书,请先购买并配置应用服务证书,然后按照此处的步骤进行操作。
在 Azure 门户的左侧菜单中,选择“应用程序服务”>“<app-name>”。
从应用的导航菜单中,请选择“证书”>“自带证书(.pfx)”>“添加证书”。
在“源”中,选择“导入应用服务证书”。
在“应用服务证书”中,选择刚创建的证书。
在“证书友好名称”中,为证书提供应用中的名称。
选择“验证”。 验证成功后,请选择“添加”。
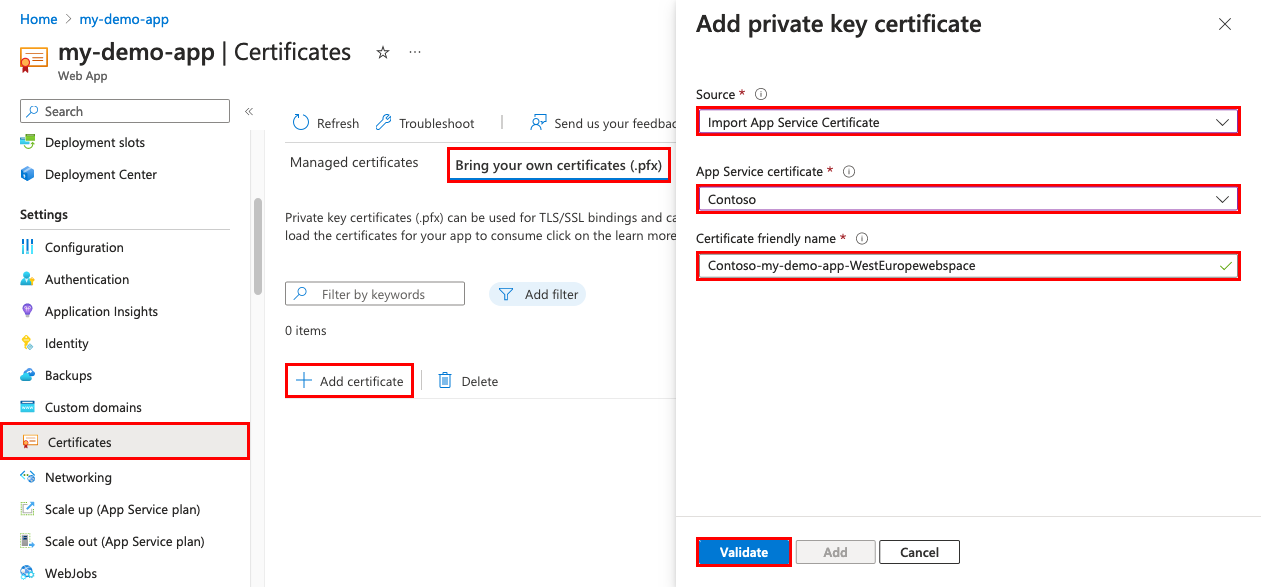
操作完成后,证书会显示在“自带证书”列表中。

若要使用此证书保护自定义域,仍需要创建证书绑定。 在 Azure 应用服务中使用 TLS/SSL 绑定保护自定义 DNS 名称。
导入来自 Key Vault 的证书
如果使用 Azure Key Vault 管理证书,则可以在满足要求的情况下将 PKCS12 证书从 Key Vault 导入应用服务。
授权应用服务读取保管库
默认情况下,应用服务资源提供程序无权访问密钥保管库。 若要将密钥保管库用于证书部署,必须授权资源提供程序对密钥保管库的读取访问权限。
注意
目前,Azure 门户不允许在密钥保管库中配置应用服务证书来使用 RBAC 模型。 但是,你可以使用 Azure CLI、Azure PowerShell 或 ARM 模板部署来执行此配置。 有关详细信息,请参阅使用 Azure 基于角色的访问控制提供对密钥保管库密钥、证书和机密的访问权限。
| 资源提供程序 | 服务主体 AppId | 密钥保管库机密权限 | 密钥保管库证书权限 |
|---|---|---|---|
| Microsoft Azure 应用服务或 Microsoft.Azure.WebSites | - abfa0a7c-a6b6-4736-8310-5855508787cd,对于所有 Azure 订阅都是相同的- 对于 Azure 政府云环境,请使用 6a02c803-dafd-4136-b4c3-5a6f318b4714。 |
获取 | 获取 |
| Microsoft.Azure.CertificateRegistration | 获取 列出 设置 删除 |
Get 列出 |
将保管库中的证书导入到应用
在 Azure 门户的左侧菜单中,选择“应用程序服务”>“<app-name>”。
从应用的导航菜单中,请选择“证书”>“自带证书(.pfx)”>“添加证书”。
在“源”中,选择“从密钥保管库导入”。
选择“选择密钥保管库证书”。
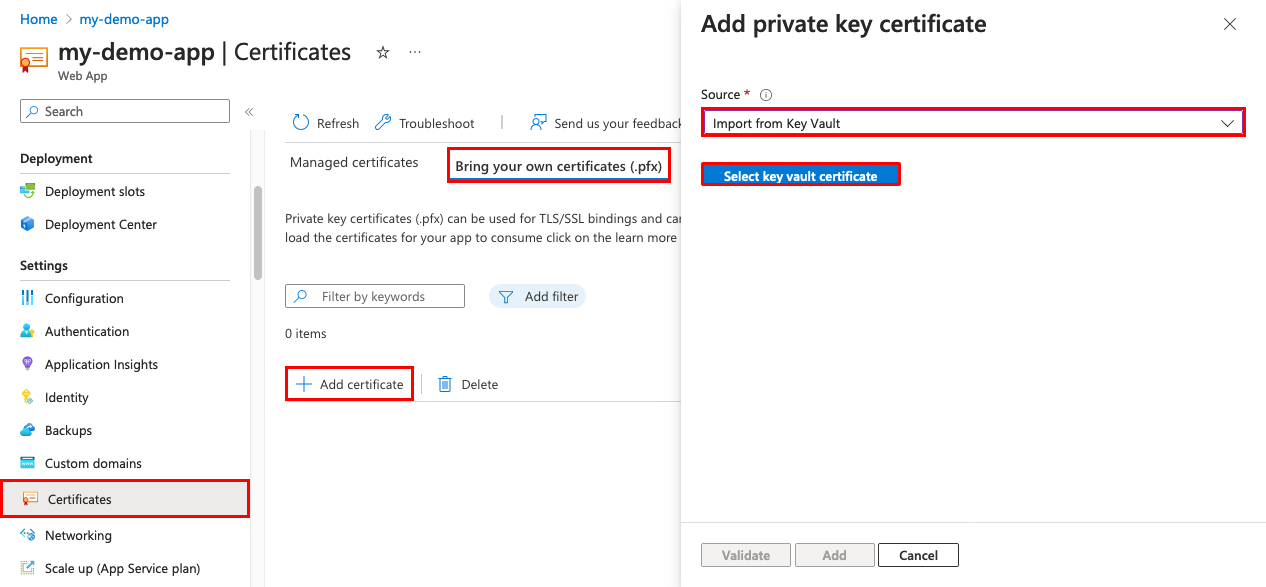
若要帮助选择证书,请使用下表:
设置 说明 订阅 与密钥保管库关联的订阅。 密钥保管库 具有要导入的证书的密钥保管库。 证书 从此列表中,选择保管库中的 PKCS12 证书。 保管库中的所有 PKCS12 证书都已通过其指纹列出,但在应用服务中并非支持所有证书。 完成选择后,依次选择“选择”、“验证”和“添加”。
操作完成后,证书会显示在“自带证书”列表中。 如果导入失败并出现错误,则证书不满足应用服务的要求。

注意
如果使用新证书更新 Key Vault 中的证书,应用服务会在 24 小时内自动同步证书。
若要使用此证书保护自定义域,仍需要创建证书绑定。 在 Azure 应用服务中使用 TLS/SSL 绑定保护自定义 DNS 名称。
上传私有证书
从证书提供程序处获取证书后,请按照本部分中的步骤为应用服务准备好证书。
合并中间证书
如果证书颁发机构在证书链中提供了多个证书,则必须按相同的顺序合并证书。
在文本编辑器中,打开收到的所有证书。
若要存储合并证书,请创建一个名为 mergedcertificate.crt 的文件。
将每个证书的内容复制到此文件中。 请确保遵循证书链指定的证书顺序,从你的证书开始,到根证书结束,例如:
-----BEGIN CERTIFICATE----- <your entire Base64 encoded SSL certificate> -----END CERTIFICATE----- -----BEGIN CERTIFICATE----- <The entire Base64 encoded intermediate certificate 1> -----END CERTIFICATE----- -----BEGIN CERTIFICATE----- <The entire Base64 encoded intermediate certificate 2> -----END CERTIFICATE----- -----BEGIN CERTIFICATE----- <The entire Base64 encoded root certificate> -----END CERTIFICATE-----
将合并的专用证书导出为 PFX
现在,使用用于生成证书请求的私钥导出合并的 TLS/SSL 证书。 如果使用 OpenSSL 生成证书请求,则已创建私钥文件。
注意
OpenSSL v3 已将默认密码从 3DES 更改为 AES256,但这在命令行 -keypbe PBE-SHA1-3DES -certpbe PBE-SHA1-3DES -macalg SHA1 上是可以替代的。 OpenSSL v1 使用 3DES 作为默认密码,因此无需进行任何特殊修改即可支持生成的 PFX 文件。
若要将证书导出为 PFX 文件,请运行以下命令,但将占位符 <private-key-file> 和 <merged-certificate-file> 分别替换为私钥和合并证书文件的路径。
openssl pkcs12 -export -out myserver.pfx -inkey <private-key-file> -in <merged-certificate-file>出现提示时,请指定导出操作的密码。 稍后将 TLS/SSL 证书上传到应用服务时,必须提供此密码。
如果使用 IIS 或 Certreq.exe 生成证书请求,请将证书安装到本地计算机,然后将证书导出为 PFX 文件。
将证书上传到应用服务
现在可以将证书上传到应用服务了。
在 Azure 门户的左侧菜单中,选择“应用程序服务”>“<app-name>”。
从应用的导航菜单中,请选择“证书”>“自带证书(.pfx)”>“上传证书”。
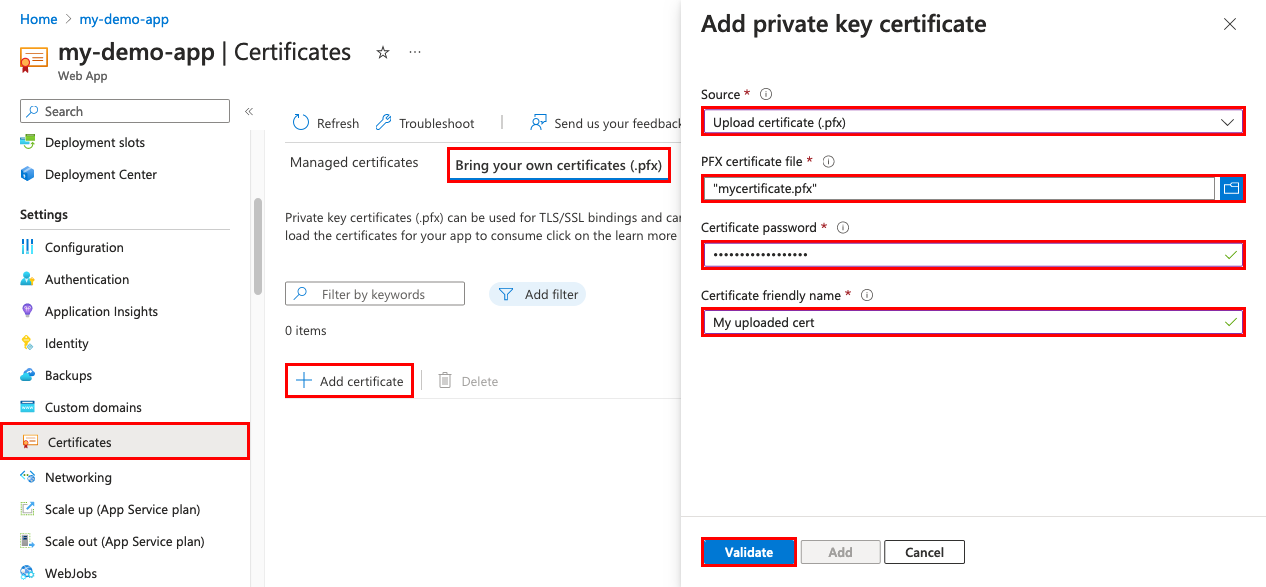
若要帮助上传 .pfx 证书,请使用下表:
设置 说明 PFX 证书文件 选择 .pfx 文件。 证书密码 输入导出 PFX 文件时创建的密码。 证书易记名称 将在 Web 应用中显示的证书名称。 完成选择后,依次选择“选择”、“验证”和“添加”。
操作完成后,证书会显示在“自带证书”列表中。

若要使用此证书保护自定义域,仍需要创建证书绑定。 在 Azure 应用服务中使用 TLS/SSL 绑定保护自定义 DNS 名称。
上传公用证书
支持使用 .cer 格式的公用证书。
注意
将公共证书上传到应用后,该证书只能由它上传到的应用访问。 公共证书必须上传到需要访问的每个 Web 应用。 有关应用服务环境特定场景,请参阅证书和应用服务环境文档
每个应用服务计划最多可上传 1000 个公共证书。
在 Azure 门户的左侧菜单中,选择“应用程序服务”>“<app-name>”。
从应用的导航菜单中,选择“证书”>“公钥证书(.cer)”>“添加证书”。
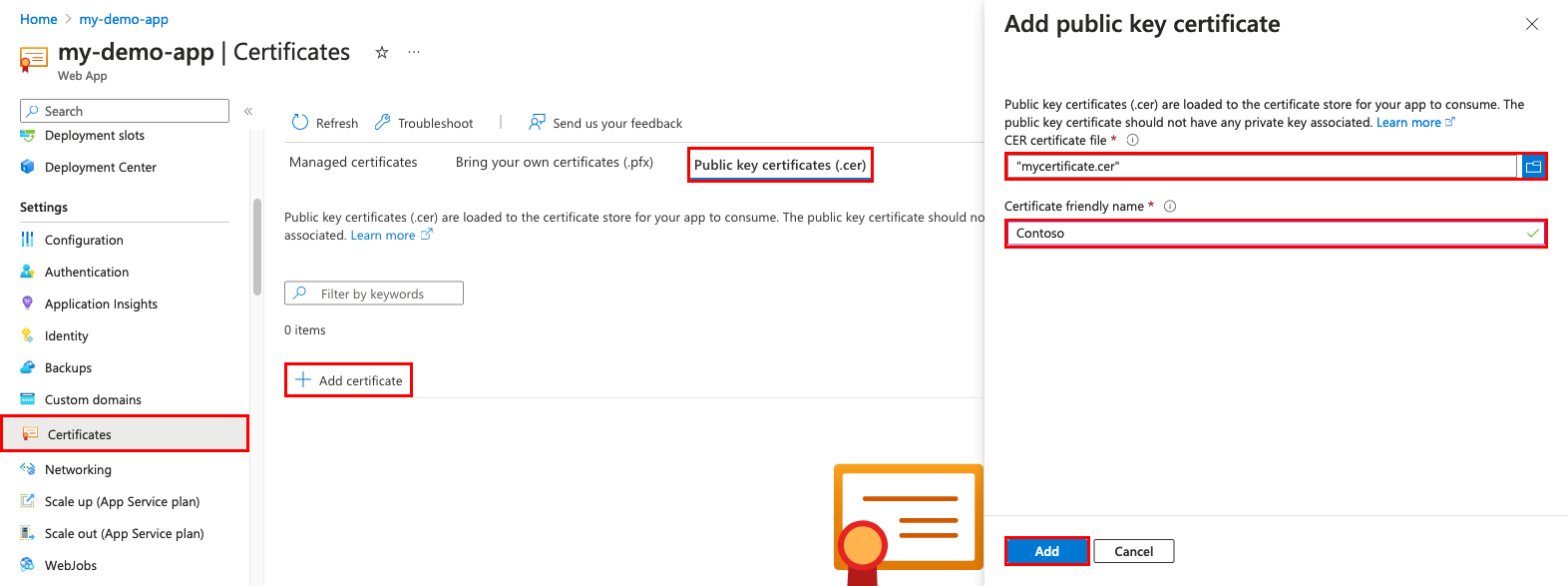
若要帮助上传 .cer 证书,请使用下表:
设置 说明 CER 证书文件 选择 .cer 文件。 证书易记名称 将在 Web 应用中显示的证书名称。 完成后,选择“添加”。
上传证书后,复制证书指纹,查看是否使证书可访问。
续订即将到期的证书
在证书到期之前,请确保将续订的证书添加到应用服务,并更新进程依赖于证书类型的任何证书绑定。 例如,从 Key Vault 导入的证书(包括应用服务证书)每 24 小时自动同步到应用服务,并在你续订证书时更新 TLS/SSL 绑定。 对于上传的证书,没有自动绑定更新。 根据你的方案,查看相应的部分:
续订上传的证书
替换过期证书时,使用新证书更新证书绑定的方式可能会对用户体验产生不利影响。 例如,在删除某个绑定时,即使该绑定是基于 IP 的,入站 IP 地址也可能会更改。 在续订已进行基于 IP 的绑定的证书时,此结果尤其有影响。 若要避免应用的 IP 地址发生更改以及由于 HTTPS 错误而导致应用停机,请按指定顺序执行以下步骤:
转到应用的“自定义域”页,选择“...”操作按钮,然后选择“更新绑定”。
选择新证书,然后选择“更新”。
删除现有证书。
续订从 Key Vault 导入的证书
注意
若要续订应用服务证书,请参阅续订应用服务证书。
若要续订从 Key Vault 导入应用服务的证书,请参阅续订 Azure Key Vault 证书。
在密钥保管库中续订证书后,应用服务会自动同步新证书并在 24 小时内更新任何适用的证书绑定。 若要手动同步,请执行以下步骤:
转到应用的“证书”页。
在“自带证书(.pfx)”下,为导入的密钥保管库证书选择“...”详细信息按钮,然后选择“同步”。
常见问题
如何自动将自带证书添加到应用?
是否可以在应用上配置专用 CA 证书?
应用服务具有受信任的根证书列表,虽然不能在应用服务的多租户变体版本中修改该列表,但可以在应用服务中的单租户环境应用服务环境 (ASE) 的受信任根存储中加载自己的 CA 证书。 (免费、基本、标准和高级应用服务计划都是多租户计划,独立计划是单租户计划。)