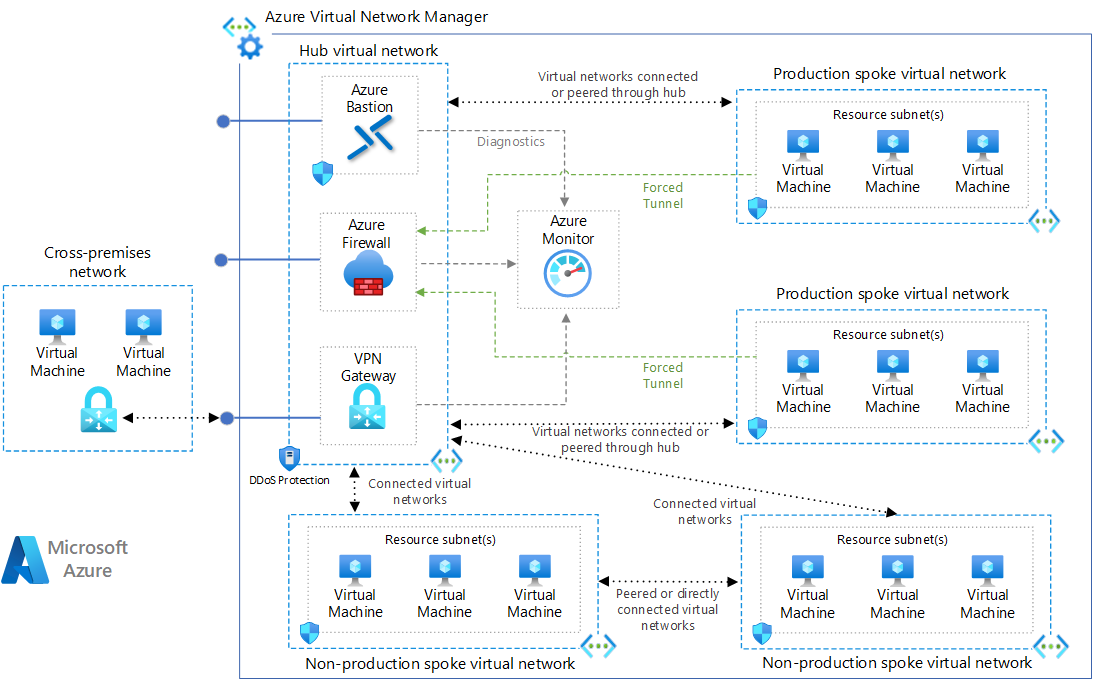
此参考体系结构使用客户托管的中心基础结构组件实现中心辐射型网络模式。 有关 Microsoft 托管的中心基础结构解决方案,请参阅中心辐射型拓扑与 Azure 虚拟 WAN。
体系结构
下载此体系结构的 Visio 文件。
工作流
此中心辐射型网络配置使用以下体系结构元素:
中心虚拟网络。 中心虚拟网络托管共享的 Azure 服务。 分支虚拟网络中托管的工作负载可使用这些服务。 中心虚拟网络是连接到跨界网络的中心点。
辐射型虚拟网络。 分支虚拟网络在每个分支中单独隔离和管理工作负载。 每个工作负载可以包括多个层,并具有通过 Azure 负载均衡器连接的多个子网。 分支可以位于不同的订阅中,并表示不同的环境,例如生产环境和非生产环境。
虚拟网络连接。 此体系结构使用对等互连连接或连接组连接虚拟网络。 对等互连连接和连接组是虚拟网络之间的非传递性、低延迟连接。 对等互连或连接的虚拟网络可以通过 Azure 主干网络交换流量,而无需路由器。 Azure Virtual Network Manager 创建和管理网络组及其连接。
Azure Bastion 主机。 Azure Bastion 使用浏览器提供从 Azure 门户到虚拟机 (VM) 的安全连接。 部署在 Azure 虚拟网络中的 Azure Bastion 主机可以访问该虚拟网络或连接的虚拟网络中的 VM。
Azure 防火墙。 Azure 防火墙托管防火墙实例存在于其自己的子网中。
Azure VPN 网关或 Azure ExpressRoute 网关。 通过虚拟网络网关,虚拟网络可以连接到虚拟专用网 (VPN) 设备或 Azure ExpressRoute 线路。 网关提供跨界网络连接。 有关详细信息,请参阅将本地网络连接到 Microsoft Azure 虚拟网络和使用 VPN 扩展本地网络。
VPN 设备。 用于与跨界网络建立外部连接的 VPN 设备或服务。 VPN 设备可以是硬件设备,也可以是软件解决方案,例如 Windows Server 中的路由和远程访问服务 (RRAS)。 有关详细信息,请参阅经过验证的 VPN 设备和设备配置指南。
组件
Virtual Network Manager 是一项管理服务,可帮助跨 Azure 订阅、区域和租户大规模地对虚拟网络进行分组、配置、部署和管理。 使用 Virtual Network Manager,可通过定义虚拟网络组来对虚拟网络进行标识和逻辑分段。 可以一次性跨网络组中所有虚拟网络定义和应用连接和安全配置。
Azure 虚拟网络是 Azure 中专用网络的基本构建块。 通过虚拟网络,多种 Azure 资源(例如 Azure VM)能以安全方式彼此通信、与跨界网络通信,以及与 Internet 通信。
Azure Bastion 是一项完全托管服务,可针对 VM 提供更安全且无缝的远程桌面协议 (RDP) 和安全外壳协议 (SSH) 访问权限,且完全不会曝光其公共 IP 地址。
Azure 防火墙是基于云的托管式网络安全服务,可保护虚拟网络资源。 这项有状态防火墙服务具有内置的高可用性和不受限制的云可伸缩性,可帮助你跨订阅和虚拟网络创建、强制实施和记录应用程序和网络连接策略。
VPN 网关是一种特定类型的虚拟网络网关,通过公共 Internet 在虚拟网络和本地位置之间发送加密的流量。 也可使用 VPN 网关在基于 Microsoft 网络的 Azure 虚拟网络之间发送加密流量。
Azure Monitor 从包括 Azure 和本地环境在内的跨界环境中收集、分析和处理遥测数据。 Azure Monitor 可帮助最大限度地提高应用程序的性能和可用性,在数秒内主动识别问题。
方案详细信息
此参考体系结构实现中心辐射型网络模式,其中中心虚拟网络充当连接到多个分支虚拟网络的中心点。 分支虚拟网络与中心连接,可用于隔离工作负载。 还可以通过使用中心连接到本地网络来实现跨界方案。
此体系结构介绍客户托管的中心基础结构组件的网络模式。 有关 Microsoft 托管的中心基础结构解决方案,请参阅中心辐射型拓扑与 Azure 虚拟 WAN。
使用中心辐射型配置的优点包括:
- 节约成本
- 克服订阅限制
- 工作负荷隔离
有关详细信息,请参阅中心辐射型网络拓扑。
可能的用例
通常使用中心辐射型体系结构时包括的工作负载有以下特点:
- 有多个需要共享服务的环境。 例如,工作负载可能有开发、测试和生产环境。 共享服务可能包括 DNS ID、网络时间协议 (NTP) 或 Active Directory 域服务 (AD DS)。 共享服务放置在中心虚拟网络中,而每个环境部署到不同分支以保持隔离。
- 不需要相互连接但需要访问共享服务。
- 要求对安全性进行集中控制,例如中心内的外围网络(也称为 DMZ)防火墙,在每个分支中分开管理工作负载。
- 要求对连接进行集中控制,例如选择性连接或隔离某些环境或工作负载的分支。
建议
以下建议适用于大多数场景。 除非有优先于这些建议的特定要求,否则请遵循这些建议。
资源组、订阅和区域
此示例解决方案使用单个 Azure 资源组。 此外,还可以在不同的资源组和订阅中实现中心和各个分支。
如果为不同订阅中的虚拟网络建立对等互连,可将这些订阅关联到同一个或不同的 Microsoft Entra 租户。 这种灵活性允许分散管理每个工作负载,同时维护中心内共享的服务。 请参阅创建虚拟网络对等互连 - 资源管理器、不同订阅和 Microsoft Entra 租户。
通常,建议每个区域至少有一个中心。 此配置有助于避免产生单一故障点,例如,避免区域 B 中的中断在网络级别影响到区域 A 资源。
虚拟网络子网
以下建议概述了如何配置虚拟网络上的子网。
GatewaySubnet
虚拟网络网关需要此子网。 如果不需要建立跨界网络连接,还可以在不使用网关的情况下使用中心辐射型拓扑。
创建一个名为 GatewaySubnet 的子网,且地址范围至少为 /27。 /27 地址范围为子网提供了足够的可伸缩性配置选项,可防止将来达到网关大小限制。 有关设置网关的详细信息,请根据你的连接类型参阅以下参考体系结构:
要实现更高的可用性,可以将 ExpressRoute 外加 VPN 用于故障转移。 请参阅将本地网络连接到 Azure 并将 ExpressRoute 和 VPN 用于故障转移。
AzureFirewallSubnet
创建一个名为 AzureFirewallSubnet 的子网,且地址范围至少为 /26。 无论要如何缩放,/26 地址范围都是推荐的大小,且能应对将来的大小限制。 此子网不支持网络安全组 (NSG)。
Azure 防火墙需要使用此子网。 如果使用合作伙伴网络虚拟设备 (NVA),请遵循其网络要求。
分支网络连接
虚拟网络对等互连或连接组是虚拟网络之间的非传递关系。 如果需要分支虚拟网络相互连接,请在这些分支之间添加对等互连连接,或将这些分支放在同一网络组中。
通过 Azure 防火墙或 NVA 进行分支连接
每个虚拟网络的虚拟网络对等互连数有限。 如果有多个分支需要相互连接,你有可能会耗尽对等互连连接。 连接组也有限制。 有关详细信息,请参阅网络限制和连接组限制。
在这种情况下,请考虑使用用户定义的路由 (UDR) 强制将分支流量发送到 Azure 防火墙或在中心充当路由器的 NVA。 这将允许各个分支相互连接。 若要支持此配置,必须实现已启用强制隧道配置的 Azure 防火墙。 有关详细信息,请参阅 Azure 防火墙强制隧道。
此体系结构设计中的拓扑可让出口流更为顺畅。 虽然 Azure 防火墙主要用于保证出口安全,但它也可用作入口点。 有关中心 NVA 入口路由的更多注意事项,请参阅面向虚拟网络的防火墙和应用程序网关。
通过中心网关进行与远程网络的分支连接
若要配置分支通过中心网关与远程网络通信,可以使用虚拟网络对等互连或连接的网络组。
若要使用虚拟网络对等互连,请在虚拟网络的“对等互连”设置中执行以下操作:
- 在中心内配置对等互连连接以允许网关传输。
- 在每个分支配置对等互连连接以使用远程虚拟网络的网关。
- 配置所有对等互连连接以允许转发流量。
有关详细信息,请参阅创建虚拟网络对等互连。
使用连接的网络组:
- 在 Virtual Network Manager 中,创建网络组并添加成员虚拟网络。
- 创建中心辐射型连接配置。
- 在“分支网络组”处,选择“中心作为网关”。
有关详细信息,请参阅使用 Azure Virtual Network Manager 创建中心辐射型拓扑。
分支网络通信
允许分支虚拟网络相互通信主要有两种方法:
- 通过 NVA(如防火墙和路由器)进行通信。 此方法在两个分支之间产生跃点。
- 使用虚拟网络对等互连或 Virtual Network Manager 直接连接在分支之间进行通信。 此方法不会在两个分支之间产生跃点,建议使用此方法以最大程度地降低延迟。
通过 NVA 进行通信
如果分支之间需要连接,请考虑在中心部署 Azure 防火墙或其他 NVA。 然后创建路由以将分支中的流量转发到防火墙或 NVA,然后再路由到第二个分支。 在这种情况下,必须配置对等互连连接以允许转发的流量。
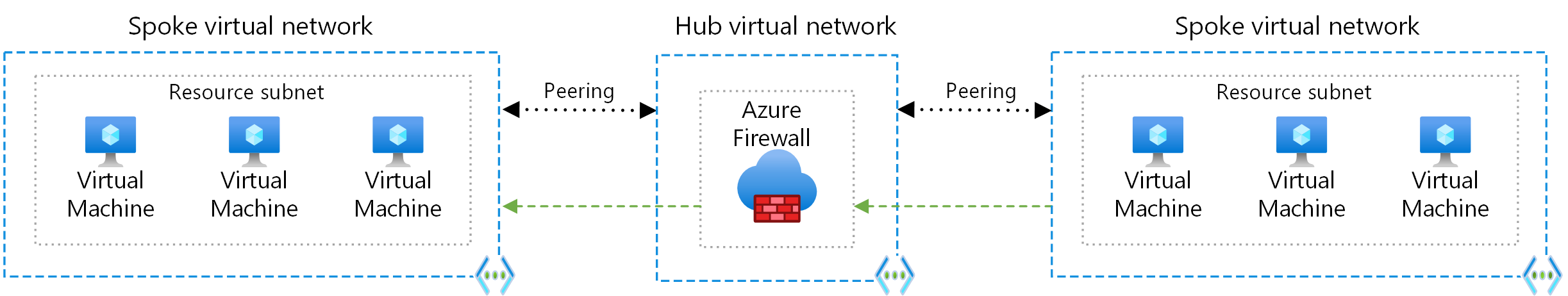
还可以使用 VPN 网关在分支之间路由流量,尽管此选项会影响延迟和吞吐量。 有关配置详细信息,请参阅为虚拟网络对等互连配置 VPN 网关传输。
评估在中心内共享的服务,以确保中心能够针对大量分支进行缩放。 例如,如果中心提供防火墙服务,则在添加多个分支时请考虑防火墙解决方案的带宽限制。 你可以将其中部分共享服务移动到二级中心内。
在分支网络之间进行直接通信
若要在不遍历中心虚拟网络的情况下直接在分支虚拟网络之间连接,可以在分支之间创建对等互连连接,或为网络组启用直接连接。 最好限制对等互连或直接连接到属于同一环境和工作负载的分支虚拟网络。
使用 Virtual Network Manager 时,可以手动将分支虚拟网络添加到网络组,也可以根据定义的条件自动添加网络。 有关详细信息,请参阅分支到分支网络。
下图演示了使用 Virtual Network Manager 在分支之间建立的直接连接。

管理建议
若要集中管理连接和安全控制,请使用 Virtual Network Manager 创建新的中心辐射型虚拟网络拓扑或加入现有拓扑。 使用 Virtual Network Manager 可确保中心辐射型网络拓扑为跨多个订阅、管理组和地区的大规模未来增长做好准备。
Virtual Network Manager 用例方案的示例包括:
- 将分支虚拟网络管理普及到业务部门或应用程序团队等组。 普及可能会导致产生大量的虚拟网络到虚拟网络连接和网络安全规则要求。
- 标准化多个 Azure 区域中的多个副本体系结构,以确保适用于全球分布的应用程序。
为了确保统一的连接和网络安全规则,可以使用网络组对同一 Microsoft Entra 租户下的任何订阅、管理组或区域中的虚拟网络进行分组。 可以通过动态或静态成员身份分配自动或手动将虚拟网络加入网络组。
定义 Virtual Network Manager 使用范围管理的虚拟网络的可发现性。 此功能为所需数量的网络管理器实例提供了灵活性,从而能够进一步实现虚拟网络组的管理普及。
若要将同一网络组中的分支虚拟网络相互连接,请使用 Virtual Network Manager 实现虚拟网络对等互连或直接连接。 使用全局网格选项将网格直接连接扩展到不同区域中的分支网络。 下图显示了区域之间的全局网格连接。

可以将网络组中的虚拟网络关联到安全管理规则的基准集。 网络组安全管理规则可防止分支虚拟网络所有者覆盖基准安全规则,同时他们可以单独添加自己的安全规则集和 NSG。 有关在中心辐射型拓扑中使用安全管理规则的示例,请参阅教程:创建安全的中心辐射型网络。
为了促进网络组、连接和安全规则的可控推出,Virtual Network Manager 配置部署可帮助你安全地将可能的重大配置更改发布到中心辐射型环境。 有关详细信息,请参阅 Azure Virtual Network Manager 中的配置部署。
若要开始使用 Virtual Network Manager,请参阅使用 Azure Virtual Network Manager 创建中心辐射型拓扑。
注意事项
这些注意事项实施 Azure 架构良好的框架的支柱原则,即一套可用于改善工作负载质量的指导原则。 有关详细信息,请参阅 Microsoft Azure 架构良好的框架。
安全性
安全性针对蓄意攻击及滥用宝贵数据和系统提供保障措施。 有关详细信息,请参阅安全性支柱概述。
为确保安全规则的基准集,请确保将安全管理规则与网络组中的虚拟网络相关联。 安全管理规则优先于 NSG 规则,并在 NSG 规则之前进行评估。 与 NSG 规则一样,安全管理规则支持优先级、服务标记和 L3-L4 协议。 有关详细信息,请参阅 Virtual Network Manager 中的安全管理规则。
使用 Virtual Network Manager 部署来促进网络安全规则可能的重大更改的可控推出。
Azure DDoS 防护与应用程序设计最佳做法相结合,提供增强的 DDoS 缓解功能来更全面地防御 DDoS 攻击。 应在任何外围虚拟网络上启用 Azure DDOS 防护。
成本优化
成本优化涉及可以减少不必要的费用以及提高运营效率的方法。 有关详细信息,请参阅成本优化支柱概述。
部署和管理中心辐射型网络时,请考虑以下与成本相关的因素。 有关详细信息,请参阅虚拟网络定价。
Azure 防火墙成本
此体系结构在中心网络中部署 Azure 防火墙实例。 与其他 NVA 相比,将 Azure 防火墙部署用作多个工作负载使用的共享解决方案可以显著节省云成本。 有关详细信息,请参阅Azure 防火墙与网络虚拟设备。
若要有效地使用所有部署的资源,请选择正确的 Azure 防火墙大小。 确定所需的功能以及最适合当前这组工作负载的层级。 若要了解可用的 Azure 防火墙 SKU,请参阅什么是 Azure 防火墙?
专用 IP 地址成本
可以使用专用 IP 地址在对等互连虚拟网络之间或连接组中的网络之间路由流量。 请注意以下成本事项:
- 入口和出口流量在对等互连网络或连接的网络的两端收费。 例如,从区域 1 中的虚拟网络到区域 2 中的另一个虚拟网络的数据传输将产生区域 1 的出站传输费率和区域 2 的入站费率。
- 不同的区域的传输费率不同。
根据对等互连要求规划 IP 寻址,并确保地址空间不会在跨界位置和 Azure 位置之间产生重叠。
卓越运营
卓越运营涵盖了部署应用程序并使其在生产环境中保持运行的运营流程。 有关详细信息,请参阅卓越运营支柱概述。
使用 Azure 网络观察程序通过以下工具监视网络组件并对其进行故障排除:
- 流量分析:显示虚拟网络中生成最多流量的系统。 可以在瓶颈成为问题之前直观地进行识别。
- 网络性能监视器:监视有关 ExpressRoute 线路的信息。
- VPN 诊断:帮助对站点到站点 VPN 连接(用于将应用程序连接到本地用户)进行故障排除。
另请考虑启用 Azure 防火墙诊断日志记录,以更好地深入了解 DNS 请求和日志中的允许/拒绝结果。
部署此方案
此部署包括一个中心虚拟网络和两个连接的分支,还部署了 Azure 防火墙实例和 Azure Bastion 主机。 或者,部署可以包括第一个分支网络中的 VM 和 VPN 网关。
可以选择虚拟网络对等互连或 Virtual Network Manager 连接组来创建网络连接。 每种方法都有多个部署选项。
使用虚拟网络对等互连
运行以下命令在
eastus区域为部署创建名为hub-spoke的资源组。 要使用嵌入式 shell,请选择“试用”按钮。az group create --name hub-spoke --location eastus运行以下命令下载 Bicep 模板。
curl https://raw.githubusercontent.com/mspnp/samples/main/solutions/azure-hub-spoke/bicep/main.bicep > main.bicep运行以下命令以部署中心辐射型网络配置、中心和分支之间的虚拟网络对等互连以及 Azure Bastion 主机。 出现提示时,输入用户名和密码。 可以使用此用户名和密码访问分支网络中的 VM。
az deployment group create --resource-group hub-spoke --template-file main.bicep
有关详细信息和其他部署选项,请查看用于部署此解决方案的中心辐射型 ARM 和 Bicep 模板。
使用 Virtual Network Manager 连接组
运行以下命令为部署创建资源组。 要使用嵌入式 shell,请选择“试用”按钮。
az group create --name hub-spoke --location eastus运行以下命令下载 Bicep 模板。
curl https://raw.githubusercontent.com/mspnp/samples/main/solutions/azure-hub-spoke-connected-group/bicep/main.bicep > main.bicep运行以下命令,将所需的全部模块下载到新目录。
mkdir modules curl https://raw.githubusercontent.com/mspnp/samples/main/solutions/azure-hub-spoke-connected-group/bicep/modules/avnm.bicep > modules/avnm.bicep curl https://raw.githubusercontent.com/mspnp/samples/main/solutions/azure-hub-spoke-connected-group/bicep/modules/avnmDeploymentScript.bicep > modules/avnmDeploymentScript.bicep curl https://raw.githubusercontent.com/mspnp/samples/main/solutions/azure-hub-spoke-connected-group/bicep/modules/hub.bicep > modules/hub.bicep curl https://raw.githubusercontent.com/mspnp/samples/main/solutions/azure-hub-spoke-connected-group/bicep/modules/spoke.bicep > modules/spoke.bicep运行以下命令以部署中心辐射型网络配置、中心和分支之间的虚拟网络连接以及 Bastion 主机。 出现提示时,输入用户名和密码。 可以使用此用户名和密码访问分支网络中的 VM。
az deployment group create --resource-group hub-spoke --template-file main.bicep
有关详细信息和其他部署选项,请查看用于部署此解决方案的中心辐射型 ARM 和 Bicep 模板。
作者
本文由 Microsoft 维护, 它最初是由以下贡献者撰写的。
主要作者:
Alejandra Palacios | 高级客户工程师
其他参与者:
- Matthew Bratschun | 客户工程师
- Jay Li | 高级产品经理
- Telmo Sampaio | 首席服务工程经理
若要查看非公开的 LinkedIn 个人资料,请登录到 LinkedIn。
后续步骤
若要了解安全虚拟中心以及 Azure 防火墙管理器配置的相关安全和路由策略,请参阅什么是安全虚拟中心?
中心辐射型网络拓扑中的中心是 Azure 登陆区域中连接订阅的主要组件。 若要详细了解如何在 Azure 中使用由客户或 Microsoft 管理的路由和安全性构建大规模网络,请参阅定义 Azure 网络拓扑。
相关资源
请参阅以下相关体系结构: