你当前正在访问 Microsoft Azure Global Edition 技术文档网站。 如果需要访问由世纪互联运营的 Microsoft Azure 中国技术文档网站,请访问 https://docs.azure.cn。
教程:在 Azure CDN 自定义域中配置 HTTPS
本教程演示如何为与 Azure CDN 终结点关联的自定义域启用 HTTPS 协议。
自定义域上的 HTTPS 协议(例如 https://www.contoso.com)可确保敏感数据通过 TLS/SSL 安全地进行分发。 当 Web 浏览器通过 HTTPS 连接时,浏览器将验证网站的证书。 浏览器会验证它是否由合法的证书颁发机构颁发。 此过程提供安全性并保护 Web 应用程序免受攻击。
默认情况下,Azure CDN 支持对 CDN 终结点主机名使用 HTTPS。 例如,如果创建 CDN 终结点(如 https://contoso.azureedge.net),则会自动启用 HTTPS。
自定义 HTTPS 功能的一些关键属性包括:
无额外费用:可免费获取或续订证书,对 HTTPS 流量也不额外收费。 只需为从 CDN 出口的 GB 数付费。
简单启用:可从 Azure 门户进行一键式预配。 还可以使用 REST API 或其他开发人员工具启用该功能。
提供完整的证书管理:
- 为你处理所有证书获取和管理。
- 在证书过期之前自动预配并续订证书。
在本教程中,你将了解如何执行以下操作:
- 在自定义域上启用 HTTPS 协议。
- 使用 CDN 托管的证书
- 使用自己的证书
- 验证域
- 在自定义域上禁用 HTTPS 协议。
先决条件
注意
建议使用 Azure Az PowerShell 模块与 Azure 交互。 请参阅安装 Azure PowerShell 以开始使用。 若要了解如何迁移到 Az PowerShell 模块,请参阅 将 Azure PowerShell 从 AzureRM 迁移到 Az。
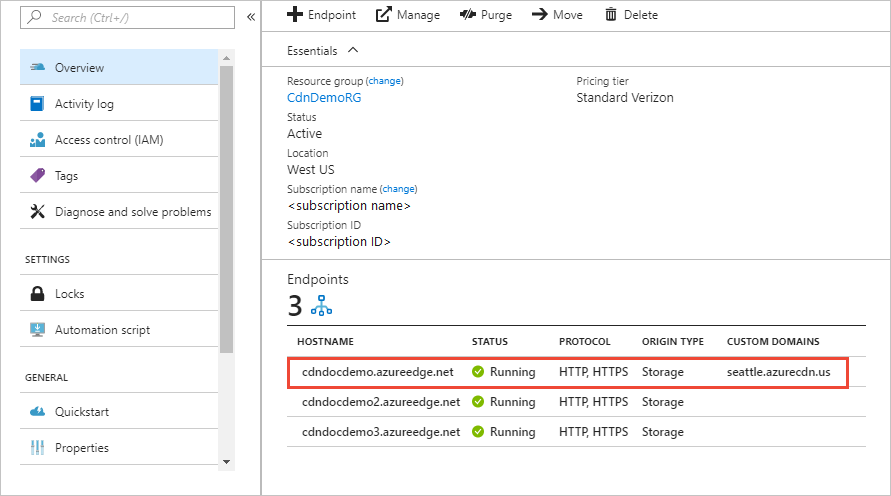
在完成本教程中的步骤之前,先创建 CDN 配置文件和至少一个 CDN 终结点。 有关详细信息,请参阅快速入门:创建 Azure CDN 配置文件和终结点。
在 CDN 终结点上关联 Azure CDN 自定义域。 有关详细信息,请参阅教程:将自定义域添加到 Azure CDN 终结点。
重要
CDN 托管的证书不可用于根域或顶点域。 如果 Azure CDN 自定义域是根域或顶点域,则必须使用“自带证书”功能。
TLS/SSL 证书
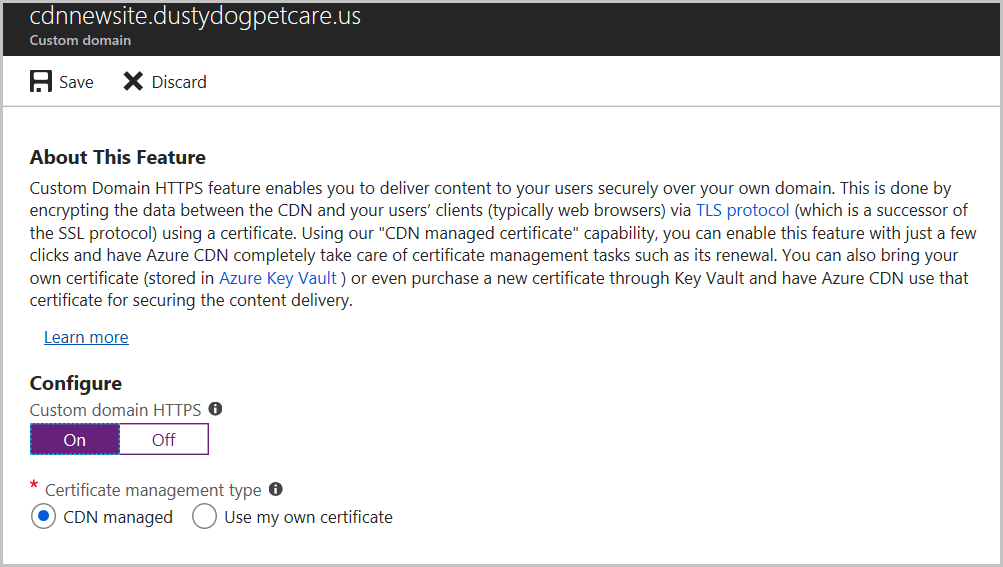
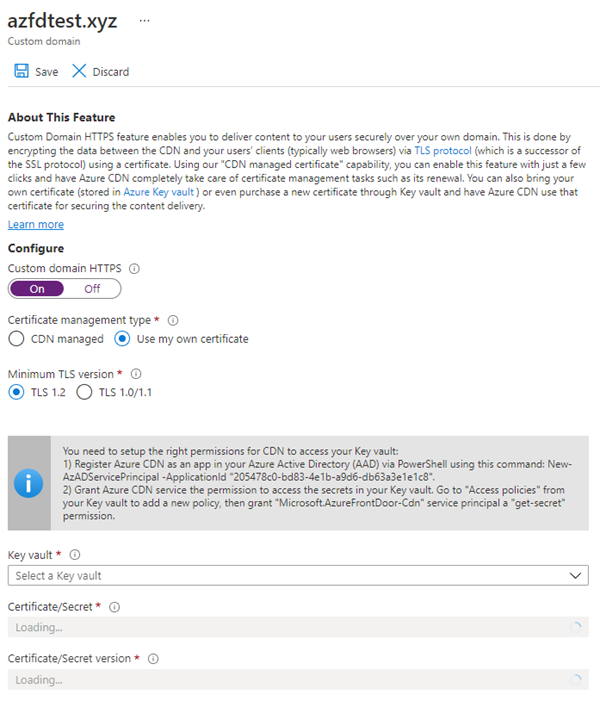
若要在 Azure CDN 自定义域上启用 HTTPS,请使用 TLS/SSL 证书。 可选择是使用 Azure CDN 托管的证书还是自己的证书。
Azure CDN 可处理证书管理任务,例如获取和续订操作。 启用此功能后,进程将立即启动。
如果自定义域已映射到 CDN 终结点,则无需进一步操作。 Azure CDN 将会自动执行步骤并完成请求。
如果自定义域映射到其他位置,请使用电子邮件来验证域所有权。
若要在自定义域上启用 HTTPS,请执行以下步骤:
验证域
如果你有一个自定义域正在使用中,且它已映射到具有 CNAME 记录的自定义终结点,或者你使用的是自己的证书,请转到映射到内容分发网络终结点的自定义域。
如果终结点的 CNAME 记录条目不复存在,或者它包含 cdnverify 子域,请转到未映射到 CDN 终结点的自定义域。
自定义域已通过 CNAME 记录映射到 CDN 终结点
将自定义域添加到终结点时,你在 DNS 域注册器中创建了一个映射到 CDN 终结点主机名的 CNAME 记录。
如果该 CNAME 记录仍然存在,并且不包含 cdnverify 子域,则 DigiCert CA 将使用它来自动验证自定义域的所有权。
如果使用的是自己的证书,则无需验证域。
CNAME 记录应采用以下格式:
- “名称”是指你的自定义域名。
- “值”是你的内容分发网络终结点主机名。
| 名称 | 类型 | 值 |
|---|---|---|
| <[www.contoso.com](www.contoso.com)> | CNAME | contoso.azureedge.net |
有关 CNAME 记录的详细信息,请参阅创建 CNAME DNS 记录。
如果 CNAME 记录采用正确的格式,DigiCert 会自动验证自定义域名,并为域创建证书。 DigitCert 不会向你发送验证电子邮件,并且你无需批准请求。 该证书会在一年内有效,并会在过期前自动续订。 转到等待传播。
自动验证通常需要几个小时。 如果在 24 小时内未看到域完成验证,请创建一个支持票证。
注意
如果通过 DNS 提供商获得证书颁发机构授权 (CAA) 记录,则必须包含用于授权的相应 CA。 DigiCert 是 Microsoft 和 Edgio 配置文件的 CA。 有关管理 CAA 记录的信息,请参阅管理 CAA 记录。 有关 CAA 记录工具,请参阅 CAA 记录帮助器。
未映射到 CDN 终结点的自定义域
如果 CNAME 记录条目包含 cdnverify 子域,请按照此步骤中的其余说明进行操作。
DigiCert 会向以下电子邮件地址发送验证电子邮件。 请验证是否可直接从以下地址之一进行审批:
- admin@your-domain-name.com
- administrator@your-domain-name.com
- webmaster@your-domain-name.com
- hostmaster@your-domain-name.com
- postmaster@your-domain-name.com
你会在几分钟内收到一封电子邮件,要求你批准请求。 如果正在使用垃圾邮件筛选器,请将 verification@digicert.com 添加到其允许列表。 如果未在 24 小时内收到电子邮件,请与 Microsoft 支持部门联系。
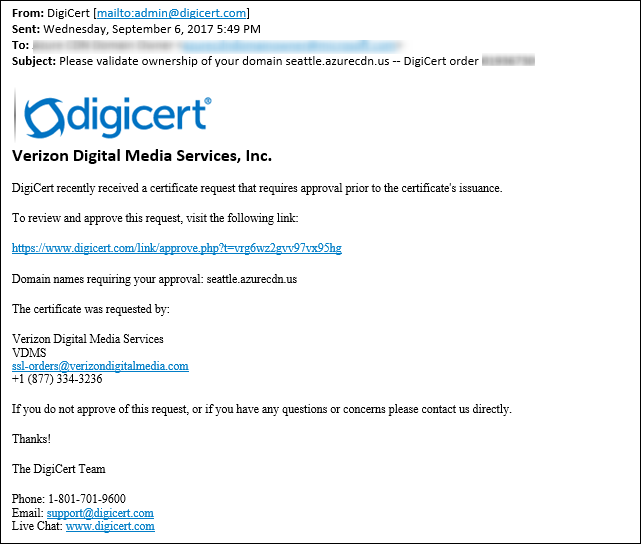
选择批准链接时,会转到以下在线批准表:

按表中的说明操作;有两种验证选项:
可批准通过同一根域(例如 consoto.com)的同一帐户下的所有将来订单。 如果你打算为同一根域添加其他自定义域,建议使用此方法。
可以只批准该请求中使用的特定主机名。 需要对后续请求另外进行审批。
批准后,DigiCert 会针对自定义域名完成证书创建。 该证书会在一年内有效,并会在过期前自动续订。
等待传播
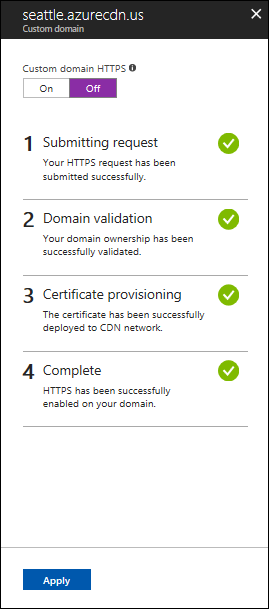
验证域名后,将需要长达 6-8 小时才能使自定义域 HTTPS 功能激活。 当进程完成时,Azure 门户中的自定义 HTTPS 状态将更改为“已启用”。 “自定义域”对话框中的 4 个操作步骤将标记为“已完成”。 自定义域现可使用 HTTPS。
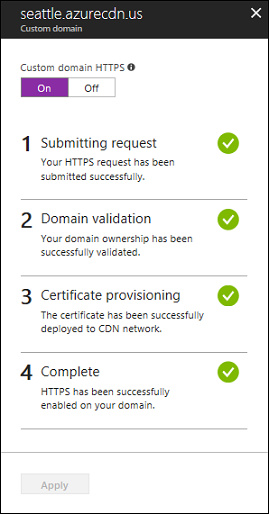
操作进度
下表显示启用 HTTPS 时出现的操作进度。 启用 HTTPS 后,自定义域对话框中将出现四个操作步骤。 当每个步骤变为活动状态时,其下将随之显示其他子步骤详细信息。 并非所有这些子步骤都会执行。 步骤成功完成后,它旁边会显示一个绿色的复选标记。
| 操作步骤 | 操作子步骤详细信息 |
|---|---|
| 1 提交请求 | 提交请求 |
| 正在提交 HTTPS 请求。 | |
| 已成功提交 HTTPS 请求。 | |
| 2 域验证 | 如果域是映射到 CDN 终结点的 CNAME,则会自动验证域。 否则,将会向域的注册记录中列出的电子邮件(WHOIS 注册者)发送验证请求。 |
| 已成功验证域所有权。 | |
| 域所有权验证请求已过期(很可能是客户在 6 天内未响应)。 将不会在域中启用 HTTPS。 * | |
| 客户已拒绝域所有权验证请求。 将不会在域中启用 HTTPS。 * | |
| 3 证书预配 | 证书颁发机构当前正在颁发在你的域中启用 HTTPS 所需的证书。 |
| 证书已颁发,当前正将证书部署到 CDN 网络。 最多可能需要 6 小时才能完成此操作。 | |
| 已成功将证书部署到 CDN 网络。 | |
| 4 完成 | 已成功在域中启用 HTTPS。 |
* 除非出现错误,否则不会显示此消息。
如果提交请求之前出现错误,则会显示以下错误消息:
We encountered an unexpected error while processing your HTTPS request. Please try again and contact support if the issue persists.
清理资源 - 禁用 HTTPS
本部分介绍了如何为自定义域禁用 HTTPS。
禁用 HTTPS 功能
在 Azure 门户中,搜索并选择“CDN 配置文件”。
选择 Microsoft 提供的标准 Azure CDN、Edgio 提供的标准 Azure CDN 或 Edgio 提供的高级 Azure CDN 配置文件。
在终结点的列表中,选取包含自定义域的终结点。
选择要禁用 HTTPS 的自定义域。
选择“禁用” 以禁用 HTTPS,然后选择“应用” 。
等待传播
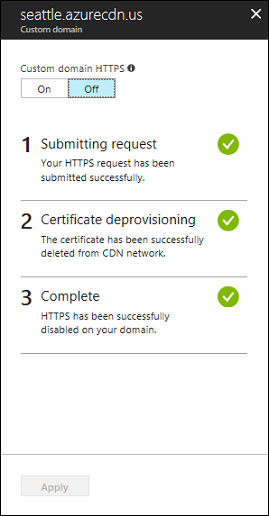
禁用自定义域 HTTPS 功能后,最多可能需要 6-8 小时才会生效。 当进程完成时,Azure 门户中的自定义 HTTPS 状态将更改为“已禁用”。 “自定义域”对话框中的 3 个操作步骤将标记为“已完成”。 自定义域不再能够使用 HTTPS。
操作进度
下表显示在禁用 HTTPS 时发生的操作进程。 禁用 HTTPS 后,“自定义域”对话框中将出现 3 个操作步骤。 当某个步骤变为活动状态时,该步骤下会显示详细信息。 步骤成功完成后,它旁边会显示一个绿色的复选标记。
| 操作进度 | 操作详细信息 |
|---|---|
| 1 提交请求 | 提交请求 |
| 2 证书取消预配 | 删除证书 |
| 3 完成 | 已删除证书 |
使用 Edgio 提供的 Azure CDN 自动轮换证书
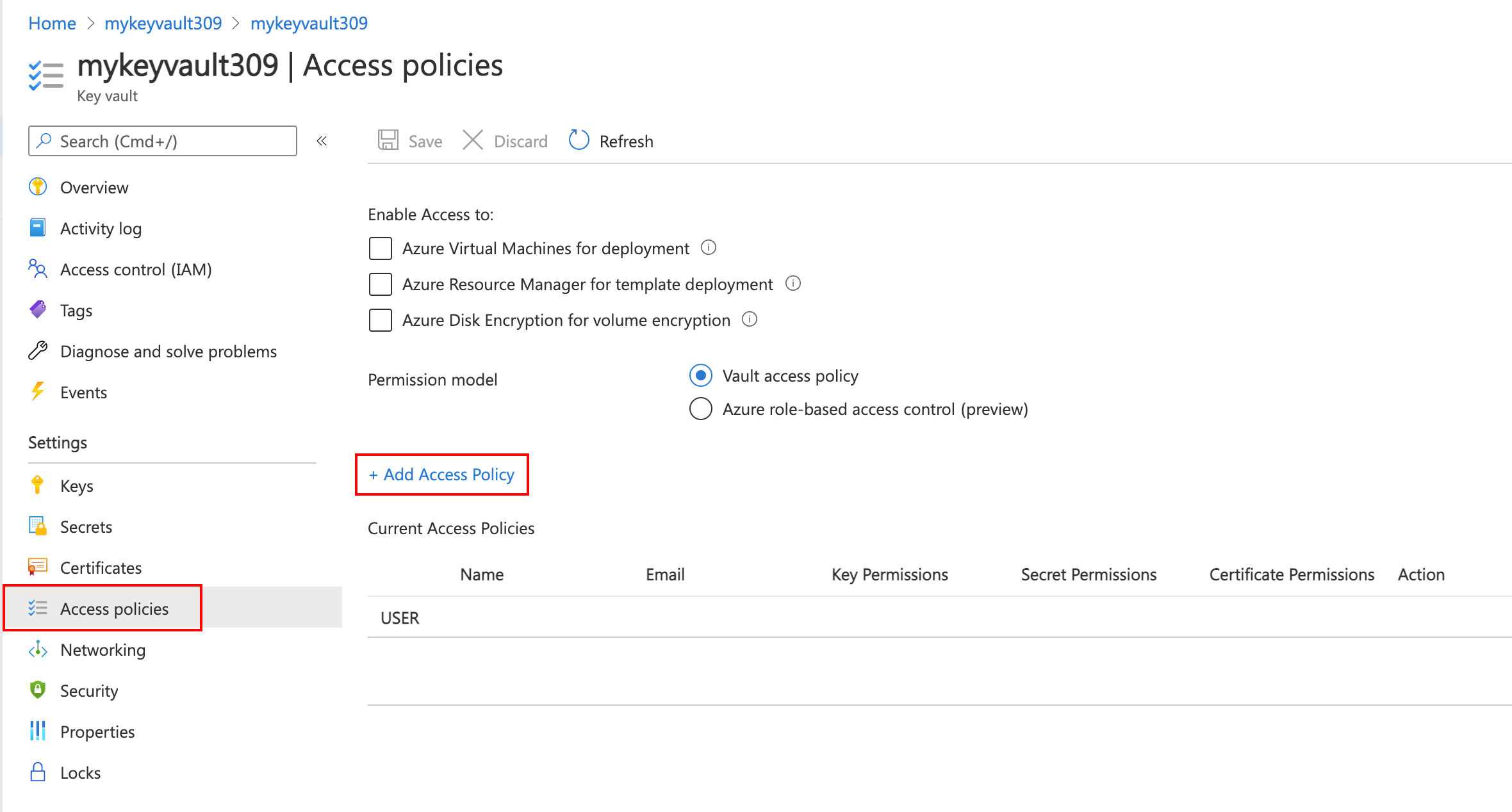
Azure Key Vault 中的托管证书可以利用证书自动启动功能,允许 Edgio 中的 Azure CDN 自动检索更新的证书并将其传播到 Edgio CDN 平台。 启用此功能:
在 Microsoft Entra ID 中将 Azure CDN 注册为应用程序。
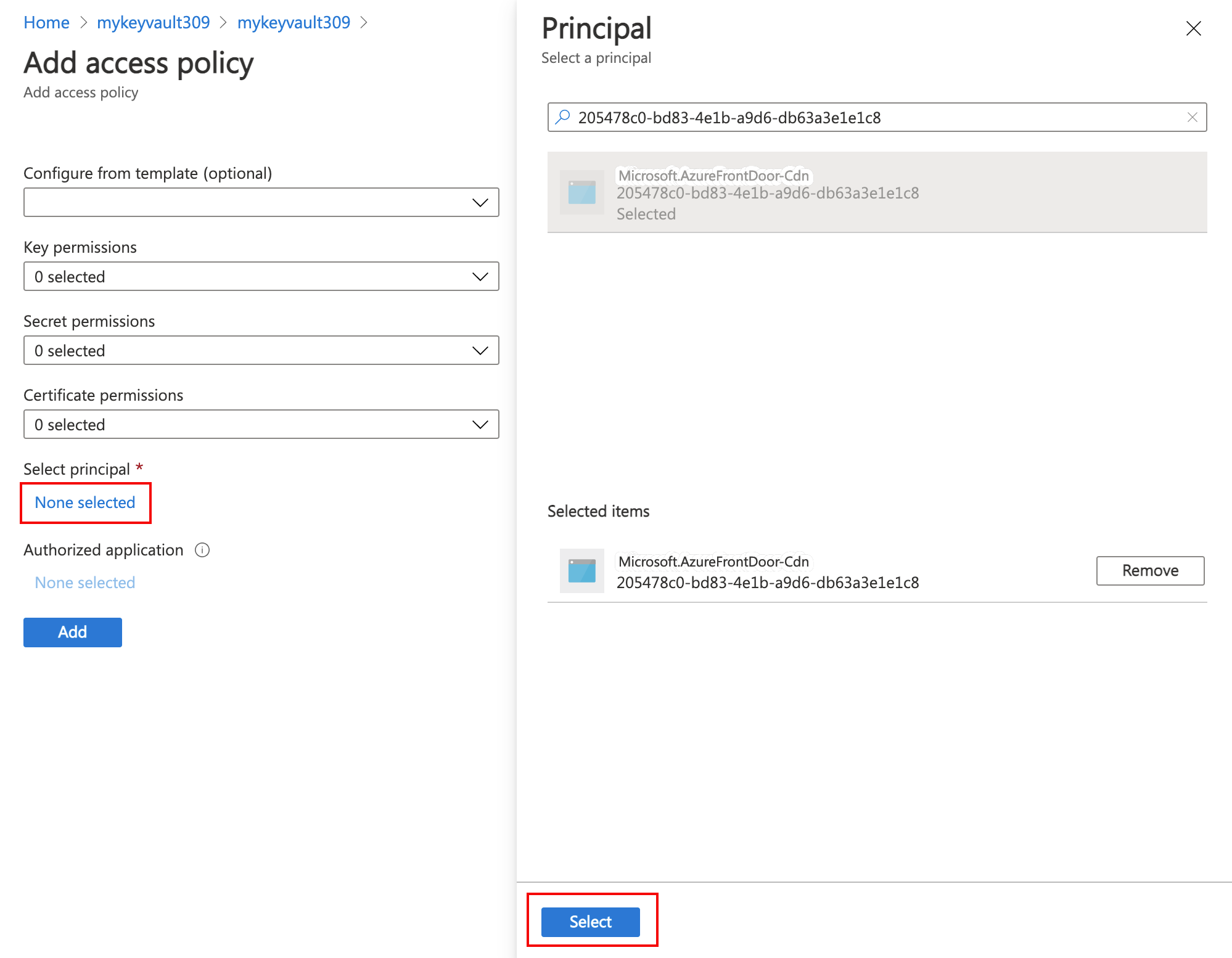
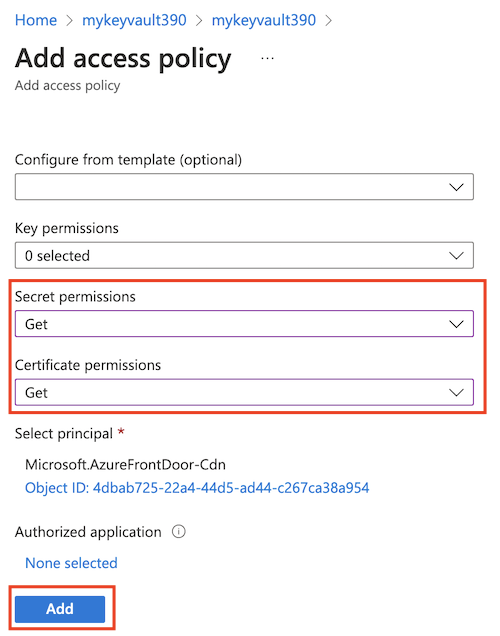
授权 Azure CDN 服务以访问 Key Vault 中的机密。 导航到 Key Vault 中的“访问策略”以添加新策略,然后向 Microsoft.AzureFrontDoor-Cdn 服务主体授予“获取机密”权限。
将证书版本设置为在自定义域菜单中证书管理类型下的最新。 如果选择了特定版本的证书,则需要手动进行更新。
注意
- 请注意,证书自动轮换可能需要长达 24 小时才能完全完成新证书的传播。
- 如果证书用于涵盖多个自定义域,则必须在共享此证书的所有自定义域上启用证书自动轮换,以确保正确操作。 否则,可能会导致 Edgio 平台为未启用此功能的自定义域提供不正确版本的证书。”
常见问题解答
谁是证书提供者?使用哪种类型的证书?
Digicert 提供的专用证书用于自定义域:
- Edgio 的 Azure 内容分发网络
- Microsoft 的 Azure 内容分发网络
你使用基于 IP 的 TLS/SSL 还是服务器名称指示 (SNI) TLS/SSL?
Edgio 提供的 Azure CDN 和 Microsoft 提供的标准 Azure CDN 都使用 SNI TLS/SSL。
如果我未收到 DigiCert 发来的域验证电子邮件,怎么办?
如果你未在使用 cdnverify 子域,并且 CNAME 条目指向终结点主机名,那么你将不会收到域验证电子邮件。
验证会自动进行。 否则,如果你没有 CNAME 条目,并且在 24 小时内未收到电子邮件,请联系 Microsoft 支持部门。
使用 SAN 证书是否没有使用专用证书安全?
SAN 证书遵循与专用证书相同的加密和安全标准。 所有颁发的 TLS/SSL 证书都使用 SHA-256 来增强服务器安全性。
我是否需要通过我的 DNS 提供商获得证书颁发机构授权记录?
当前无需具备证书颁发机构授权记录。 但是,如果你确实有一个,则必须包含 DigiCert 作为一个有效的 CA。
从 2018 年 6 月 20 日开始,Edgio 提供的 Azure CDN 默认使用专用证书和 SNI TLS/SSL。 使用“使用者可选名称”(SAN) 证书和基于 IP 的 TLS/SSL 的现有自定义域会发生什么情况?
如果 Microsoft 经分析出只有 SNI 客户端请求才会发送到你的应用程序,则现有域会在未来几个月逐渐迁移到单个证书。
如果检测到非 SNI 客户端,则域将保留在具有基于 IP 的 TLS/SSL 的 SAN 证书中。 对非 SNI 的服务或客户端的请求不受影响。
证书续订如何处理自带证书?
若要确保将较新的证书部署到 POP 基础结构,请将新证书上传到 Azure Key Vault。 在 Azure 内容分发网络上的 TLS 设置中,选择最新的证书版本并选择“保存”。 然后,Azure 内容分发网络将传播新的已更新证书。
对于“Edgio 的 Azure CDN”配置文件,如果在多个自定义域上使用相同的 Azure Key Vault 证书(例如通配符证书),请确保将所有使用同一证书的自定义域更新到较新的证书版本。
后续步骤
在本教程中,你了解了如何执行以下操作:
- 在自定义域上启用 HTTPS 协议。
- 使用 CDN 托管的证书
- 使用自己的证书
- 验证域。
- 在自定义域上禁用 HTTPS 协议。
继续学习下一教程,了解如何在 CDN 终结点上配置缓存。