你当前正在访问 Microsoft Azure Global Edition 技术文档网站。 如果需要访问由世纪互联运营的 Microsoft Azure 中国技术文档网站,请访问 https://docs.azure.cn。
计划登陆区域网络分段
本部分介绍在登陆区域中提供高度安全的内部网络分段以推动网络零信任实现的关键建议。
设计注意事项:
零信任模型假设处于信息泄露状态,然后将请求视为源自不受控制的网络,并验证每个请求。
高级零信任网络实现采用完全分布式入口/出口云微外围和更深入的微分段。
应用程序安全组 (ASG) 不会跨越虚拟网络或提供跨虚拟网络的保护。
现在通过 Azure 资源管理器模板支持 NSG 流日志。
设计建议:
将子网创建委托给登陆区域所有者。 这样,他们就能定义如何在子网之间划分工作负载(例如单个大型子网、多层应用程序或网络注入应用程序)。 平台团队可以使用 Azure Policy 来确保具有特定规则(例如,拒绝来自 Internet 的入站 SSH 或 RDP,或允许/阻止登陆区域之间的流量)的 NSG 始终关联到具有仅拒绝策略的子网。
使用 NSG 帮助保护子网之间的流量以及平台之间的东/西流量(登陆区域之间的流量)。
应用程序团队应在子网级别的 NSG 中使用应用程序安全组来帮助保护登陆区域中的多层 VM。
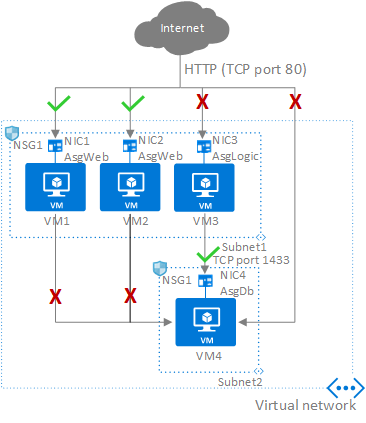
使用 NSG 和应用程序安全组对登陆区域中的流量进行微分段,并避免使用中央 NVA 来筛选流量流。
启用 NSG 流日志,并将其馈送到流量分析,便于深入了解内部和外部流量流。 作为审核和安全方面的最佳做法,应在订阅中的所有关键 VNet/子网上启用流日志。
使用 NSG 可以选择性地允许在登陆区域之间建立连接。
对于虚拟 WAN 拓扑,如果组织需要相关功能用于筛选和记录登陆区域之间流动的流量,请通过 Azure 防火墙跨登陆区域路由流量。
如果组织决定实现到本地的强制隧道(播发默认路由),建议结合以下出站 NSG 规则,在 BGP 会话中断时拒绝从 VNet 直接到 Internet 的出口流量。
注意
需要根据现有的 NSG 规则集调整规则优先级。
| 优先级 | 名称 | 源 | 目标 | 服务 | 操作 | 备注 |
|---|---|---|---|---|---|---|
| 100 | AllowLocal |
Any |
VirtualNetwork |
Any |
Allow |
在正常操作期间允许流量。 启用强制隧道后,只要 BGP 将 0.0.0.0/0 播发到 ExpressRoute 或 VPN 网关,就会将其视为 VirtualNetwork 标记的一部分。 |
| 110 | DenyInternet |
Any |
Internet |
Any |
Deny |
如果 0.0.0.0/0 路由从播发的路由中撤消(例如,由于服务中断或配置错误),则拒绝直接到 Internet 的流量。 |
注意
可以注入到虚拟网络的 Azure PaaS 服务可能与强制隧道不兼容。 控制平面操作仍可能需要直接连接到特定公共 IP 地址,以便服务正确运行。 建议查看具体的服务文档以了解网络要求,并最终使服务子网免于默认路由传播。 UDR 中的服务标记可用于绕过默认路由并仅在特定服务标记可用时重定向控制平面流量。