将 Azure Databricks 工作区连接到本地网络
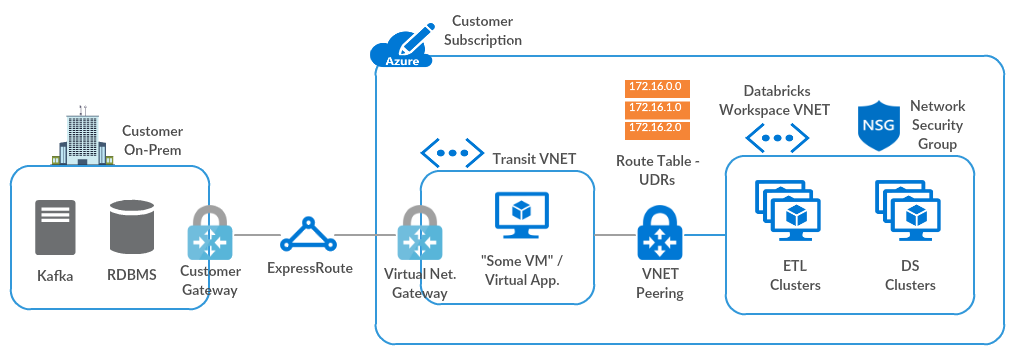
本文介绍如何建立从 Azure Databricks 工作区到本地网络的连接。 通过使用以下中心-分支拓扑,可将流量通过传输虚拟网络 (VNet) 路由到本地网络。
如果在按照本指南操作时需要帮助,请与 Microsoft 和 Databricks 客户团队联系。
要求
Azure Databricks 工作区必须部署在你自己的虚拟网络中,也称为 VNet 注入。
步骤 1:使用 Azure 虚拟网络网关设置传输虚拟网络
需要使用以下方法之一在传输 VNet 中配置 Azure 虚拟网络网关(ExpressRoute 或 VPN)。 如果已有合适的网关,请跳转到在 Azure Databricks 虚拟网络与传输虚拟网络之间建立对等互连。
如果在本地网络与 Azure 之间已设置 ExpressRoute,请按照使用 Azure 门户配置 ExpressRoute 的虚拟网络网关中的步骤进行操作。
否则,请按照使用 Azure 门户配置 VNet 到 VNet VPN 网关连接中的步骤 1-5 进行操作。
如需帮助,请联系 Microsoft 客户团队。
步骤 2:在 Azure Databricks 虚拟网络与传输虚拟网络之间建立对等互连
如果 Azure Databricks 工作区与虚拟网络网关位于同一 VNet 中,请跳转到创建用户定义的路由并将其与 Azure Databricks 虚拟网络子网关联。
否则,请按照在虚拟网络之间建立对等互连中的指示,在 Azure Databricks VNet 和传输 VNet 之间建立对等互连,并选择以下选项:
- 在 Azure Databricks VNet 端使用远程网关。
- 在传输 VNet 端允许网关传输。
有关详细信息,请参阅创建对等互连。
注意
如果与 Azure Databricks 的本地网络连接不能与上述设置一起使用,你还可以选择对等互连两侧的“允许转发的流量”选项来解决此问题。
有关为虚拟网络对等互连配置 VPN 网关传输的信息,请参阅为虚拟网络对等互连配置 VPN 网关传输。
步骤 3:创建用户定义的路由,并将其与 Azure Databricks 虚拟网络子网关联
将 Azure Databricks VNet 与传输 VNet 对等互连后,Azure 会使用传输 VNet 自动配置所有路由。 自动配置不包括从群集节点到 Azure Databricks 控制平面的返回路由。 必须使用用户定义的路由手动创建这些自定义路由。
创建路由表,并启用 BGP 路由传播。
注意
有时,验证本地网络连接设置时,BGP 路由传播会导致失败。 在万不得已时,可禁用 BGP 路由传播。
使用自定义路由中的说明为以下服务添加用户定义的路由。
如果为工作区启用安全的群集连接 (SCC),请使用 SCC 中继 IP,而不是控制平面 NAT IP。
源 地址前缀 下一跃点类型 默认 控制平面 NAT IP
(仅当禁用了 SCC 时需要)Internet 默认 SCC 中继 IP
(仅当启用了 SCC 时需要)Internet 默认 Webapp IP Internet 默认 扩展基础结构 IP Internet 默认 元存储 IP Internet 默认 项目 Blob 存储 IP Internet 默认 日志 Blob 存储 IP Internet 默认 DBFS 根存储 IP (ADLS) Internet 默认 DBFS 根存储 IP (Blob) - 对于 2023 年 3 月 6 日之前创建的工作区。 Internet 若要获取这些服务中的每个服务的 IP 地址,请按照用户定义的 Azure Databricks 路由设置中的说明进行操作。
如果基于 IP 的路由在验证设置期间失败,则可为 Microsoft.Storage 创建服务终结点,使所有 DBFS 根存储流量通过 Azure 主干线进行路由。 如果使用此方法,则无需为 DBFS 根存储创建用户定义的路由。
注意
如果要从 Azure Databricks 访问其他 PaaS Azure 数据服务(如 Cosmos DB 或 Azure Synapse Analytics),还必须将这些服务的用户定义的路由添加到路由表中。 使用
nslookup或等效的命令将每个终结点解析到其 IP 地址。使用将路由表关联到子网中的说明,将路由表与 Azure Databricks VNet 公共和专用子网关联。
自定义路由表与 Azure Databricks VNet 子网关联后,就无需编辑网络安全组中的出站安全规则了。 例如,无需使出站规则更具体,因为路由将控制实际流出量。
步骤 4:验证设置
要验证设置:
在 Azure Databricks 工作区中创建群集。
如果群集创建失败,请通读设置说明,逐个尝试其他配置选项。
如果仍无法创建群集,请验证该路由表是否包含所有必需的用户定义的路由。 如果你为 ADLS gen2(对于 2023 年 3 月 6 日前创建的工作区,Azure Blob 存储)使用了服务终结点而非用户定义的路由,则还需要检查那些终结点。
如果仍无法创建群集,请与 Microsoft 和 Databricks 客户团队联系以获取帮助。
使用以下命令对笔记本的本地 IP 执行 Ping 操作:
%sh ping <IP>
在故障排除时如需更多指南,请参阅以下资源:
可选的配置步骤
选项:使用虚拟设备或防火墙路由 Azure Databricks 流量
可使用防火墙或 DLP 设备(如 Azure 防火墙、Palo Alto、Barracuda)筛选来自 Azure Databricks 群集节点的所有传出流量。 这可让你检查传出流量是否符合安全策略,并将一个适用于所有群集的类似于 NAT 的公共 IP 或 CIDR 添加到允许列表。
根据防火墙或 DLP 设备的需要调整以下步骤:
按照创建 NVA 中的说明在传输 VNet 中设置虚拟设备或防火墙。
如需为多个工作区配置一个防火墙,可在 Azure Databricks VNet 中的安全或 DMZ 子网中创建防火墙,该子网独立于现有的专用子网和公共子网。
在自定义路由表中创建一个到 0.0.0.0/0 的其他路由。
将下一个跃点类型设置为“虚拟设备”。
设置下一个跃点地址。
请勿删除在步骤3:创建用户定义的路由并将其与 Azure Databricks 虚拟网络子网关联中创建的路由,但有一种情况例外:如果所有 Blob 流量都需要通过防火墙路由,则可删除 Blob 流量的路由。
如果使用安全或 DMZ 子网方法,则可创建一个仅与 DMZ 子网关联的附加路由表。 在该路由表中,创建一个到 0.0.0.0 的路由。
如果流量发往公用网络,则将该路由的下一个跃点类型设置为 Internet;如果流量发往本地网络,则将其设置为虚拟网络网关。
在防火墙设备中配置“允许”和“拒绝”规则。
如果已删除 Blob 存储的路由,则可将这些路由添加到防火墙的允许列表中。
如果群集依赖于公用存储库(如操作系统存储库或容器注册表),请将其添加到允许列表中。
有关允许列表的信息,请参阅用户定义的 Azure Databricks 路由设置。
选项:配置自定义 DNS
可使用自定义 DNS,并在自己的虚拟网络中部署 Azure Databricks 工作区。 有关如何为 Azure 虚拟网络配置自定义 DNS 的详细信息,请参阅以下 Microsoft 文档:
. 重要提示:若要解析 Azure Artifacts 的 IP 地址,必须将自定义 DNS 配置为将这些请求转发到 Azure 递归解析程序。