你当前正在访问 Microsoft Azure Global Edition 技术文档网站。 如果需要访问由世纪互联运营的 Microsoft Azure 中国技术文档网站,请访问 https://docs.azure.cn。
转换到 Microsoft Defender 漏洞管理
Microsoft Defender for Cloud 正在统一所有漏洞评估解决方案,以利用 Microsoft Defender 漏洞管理漏洞扫描程序。
Microsoft Defender 漏洞管理跨许多云原生用例(例如容器交付和运行时方案)集成。
由 Qualys 提供支持的 Defender for Cloud 容器漏洞评估现已停用。 如果尚未使用 Microsoft Defender 漏洞管理转换到 Azure 漏洞评估,请按照页面上的步骤进行转换。
步骤 1:验证是否已启用扫描
默认情况下,为 Defender for Containers、Defender for Container Registries(已弃用)和 Defender 云安全态势管理启用由 Microsoft Defender 漏洞管理提供支持的容器漏洞评估扫描。 禁用它的组织需要在其中一个计划中重新启用“无代理容器漏洞评估”切换。 它会自动反映到任何已启用的已提及计划中。
有关启用 Microsoft Defender 漏洞管理扫描的详细信息,请参阅启用由 Microsoft Defender 漏洞管理提供支持的漏洞评估。
步骤 2:(可选)更新 REST API 和 Azure Resource Graph 查询
如果以编程方式通过 Qualys(通过 Azure Resource Grap (ARG) Rest API 或子评估 REST API 或 ARG 查询)访问容器漏洞评估结果,则需要更新现有查询,以匹配由 Microsoft Defender 漏洞管理提供支持的新容器漏洞评估提供的新架构和/或 REST API。
下一部分包括一些示例,这些示例有助于了解 Qualys 提供支持的产品/服务的现有查询应如何转换为与 Microsoft Defender 漏洞管理提供支持的产品/服务等效的查询。
ARG 查询示例
应更新用于报告的任何 Azure Resource Graph 查询,以反映前面列出的 Microsoft Defender 漏洞管理评估密钥。 下面是帮助你转换到 Microsoft Defender 漏洞管理查询的示例。
显示运行不正常的容器映像
Qualys
securityresources
| where type == "microsoft.security/assessments/subassessments"
| extend assessmentKey = extract(".*assessments/(.+?)/.*",1, id)
| where assessmentKey == "dbd0cb49-b563-45e7-9724-889e799fa648"
| project
Resource = tolower(extract(@'(?i)(.*?)/providers/Microsoft.Security/([^/]+)', 1, id)),
ResourceType = tolower(split(id,"/").[6]),
subscriptionId,
severity = properties.status.severity,
status = properties.status.code,
VulnId = properties.id,
description = properties.displayName,
patchable = properties.additionalData.patchable,
cve = properties.additionalData.cve,
Repo = properties.additionalData.repositoryName,
imageDigest = properties.additionalData.imageDigest
| where status == 'Unhealthy'
Microsoft Defender 漏洞管理
securityresources
| where type == "microsoft.security/assessments/subassessments"
| extend assessmentKey = extract(".*assessments/(.+?)/.*",1, id)
| where assessmentKey == "c0b7cfc6-3172-465a-b378-53c7ff2cc0d5"
| project
Resource = tolower(extract(@'(?i)(.*?)/providers/Microsoft.Security/([^/]+)', 1, id)),
ResourceType = tolower(split(id,"/").[6]),
subscriptionId,
severity = properties.additionalData.vulnerabilityDetails.severity,
status = properties.status.code,
VulnId = properties.id,
description = properties.description,
fixStatus = properties.additionalData.softwareDetails.fixStatus,
Repo = properties.additionalData.artifactDetails.repositoryName,
imageUri = properties.resourceDetails.id
| where status == 'Unhealthy'
显示运行正常的容器映像
Qualys
securityresources
| where type == "microsoft.security/assessments/subassessments"
| extend assessmentKey = extract(".*assessments/(.+?)/.*",1, id)
| where assessmentKey == "dbd0cb49-b563-45e7-9724-889e799fa648"
| project
Resource = tolower(extract(@'(?i)(.*?)/providers/Microsoft.Security/([^/]+)', 1, id)),
ResourceType = tolower(split(id,"/").[6]),
subscriptionId,
status = properties.status.code,
Repo = properties.additionalData.repositoryName,
imageDigest = properties.additionalData.imageDigest
| where status == 'Healthy'
Microsoft Defender 漏洞管理
securityresources
| where type == "microsoft.security/assessments/subassessments"
| extend assessmentKey = extract(".*assessments/(.+?)/.*",1, id)
| where assessmentKey == "c0b7cfc6-3172-465a-b378-53c7ff2cc0d5"
| project
Resource = tolower(extract(@'(?i)(.*?)/providers/Microsoft.Security/([^/]+)', 1, id)),
ResourceType = tolower(split(id,"/").[6]),
subscriptionId,
status = properties.status.code,
Repo = properties.additionalData.artifactDetails.repositoryName,
imageUri = properties.resourceDetails.id
| where status == 'Healthy'
易受攻击的映像数(按严重性)计数
Qualys
securityresources
| where type == "microsoft.security/assessments/subassessments"
| extend assessmentKey = extract(".*assessments/(.+?)/.*",1, id)
| extend status = tostring(parse_json(properties).status.code)
| extend severity = tostring(parse_json(properties).status.severity)
| extend vulId=tostring((properties).id)
| extend Resource = tolower(extract(@'(?i)(.*?)/providers/Microsoft.Security/([^/]+)', 1, id))
| where assessmentKey == "dbd0cb49-b563-45e7-9724-889e799fa648"
| where status == 'Unhealthy'
| distinct
vulId,
severity
| summarize count=count() by tostring(severity)
Microsoft Defender 漏洞管理
securityresources
| where type == "microsoft.security/assessments/subassessments"
| extend assessmentKey = extract(".*assessments/(.+?)/.*",1, id)
| extend severity = tostring(properties.additionalData.vulnerabilityDetails.severity)
| extend status = tostring(parse_json(properties).status.code)
| extend vulId=tostring((properties).id)
| extend Resource = tolower(extract(@'(?i)(.*?)/providers/Microsoft.Security/([^/]+)', 1, id))
| where assessmentKey == "c0b7cfc6-3172-465a-b378-53c7ff2cc0d5"
| where status == 'Unhealthy'
| distinct
vulId,
severity
| summarize count=count() by tostring(severity)
查看 AKS 群集上运行的易受攻击的映像的 Pod、容器和命名空间
Qualys
securityresources
| where type =~ "microsoft.security/assessments/subassessments"
| extend assessmentKey = extract(@"(?i)providers/Microsoft.Security/assessments/([^/]*)", 1, id),
subAssessmentId = tostring(properties.id),
parentResourceId = extract("(.+)/providers/Microsoft.Security", 1, id)
| extend resourceId = extract(@'(?i)(.*?)@([^/]+)', 1,tostring(properties.resourceDetails.id))
| extend severity = tostring(parse_json(properties).status.severity)
| extend VulnId = tostring(parse_json(properties).id)
| extend status = tostring(parse_json(properties).status.code)
| where assessmentKey == "41503391-efa5-47ee-9282-4eff6131462c"
| extend resourceId = tostring(properties.resourceDetails.id),
parsedJson = parse_json(tostring(properties.additionalData))
| extend containerData = parse_json(tostring(parsedJson.data.Containers))
| mv-expand containerDetails = containerData to typeof(dynamic)
| extend ContainerName = tostring(containerDetails.Name),
ContainerPod = tostring(containerDetails.Pod.Name),
Namespace = tostring(containerDetails.Pod.Namespace),
ControllerType = tostring(containerDetails.Pod.ControllerType),
ControllerName = tostring(containerDetails.Pod.ControllerName)
| where status == 'Unhealthy'
|project Image=resourceId, VulnId,severity, Namespace, ContainerName, ContainerPod,ControllerName,ControllerType
Microsoft Defender 漏洞管理
securityresources
| where type =~ "microsoft.security/assessments/subassessments"
| extend assessmentKey=extract(@"(?i)providers/Microsoft.Security/assessments/([^/]*)", 1, id)
| where assessmentKey == "c0b7cfc6-3172-465a-b378-53c7ff2cc0d5"
| extend azureClusterId = tostring(properties.additionalData.clusterDetails.clusterResourceId)
| extend cve =tostring(properties.id)
| extend status = properties.status.code
| extend severity=tostring(parse_json(properties).additionalData.vulnerabilityDetails.severity)
| where status == "Unhealthy"
| extend azureImageId = tostring(properties.resourceDetails.id)
| extend severity = tolower(properties.additionalData.vulnerabilityDetails.severity)
| extend kubernetesContext = properties.additionalData.kubernetesContext
| mv-expand workload = kubernetesContext.workloads
| mv-expand OwnedResource = workload.ownedResources
| mv-expand OwnedContainer = OwnedResource.containers
| mv-expand Container = workload.containers
| extend isController = isnotempty(workload.ownedResources)
| extend namespace = tostring(workload.namespace)
| extend podName = iff(isController, tostring(OwnedResource.name), workload.name)
| extend containerName = iff(isController, tostring(OwnedContainer.name), Container.name)
| extend controllerName = iff(isController, tostring(workload.name),"")
| extend controllerType = iff(isController, tostring(workload.kind),"")
| extend imageName = extract("(.+)@sha256:", 1, azureImageId)
| project imageName, cve, severity, clusterId = azureClusterId, containerName, podName, controllerName, controllerType, namespace
步骤 3:(可选)容器安全报告
Microsoft Defender for Cloud 通过 Azure Workbooks(包括容器安全工作簿)提供现成报告。
此工作簿包括注册表和运行时中的容器漏洞扫描结果。
该工作簿提供 Microsoft Defender 漏洞管理扫描的结果,全面概述了 Azure Registry 容器映像中检测到的漏洞。 容器安全工作簿为容器漏洞评估提供以下好处:
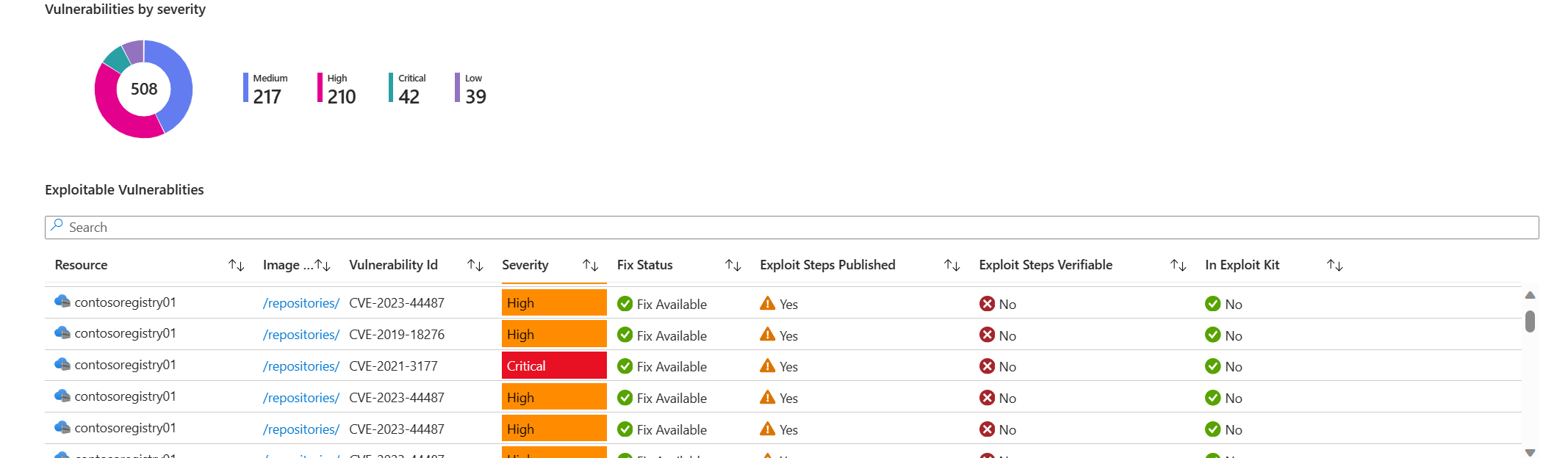
所有漏洞概述:查看在 Azure 容器注册表中检测到并在 AKS 集群上运行的所有漏洞。
可攻击漏洞仪表板:一个专用部分,其中突出显示了具有已知攻击的漏洞,使安全团队能够专注于具有被攻击的高风险的漏洞。 这仅适用于由 Microsoft Defender 漏洞管理提供支持的容器漏洞评估扫描。
其他 ARG 查询:可以使用此工作簿查看有关如何在 Qualys 和 Microsoft Defender 漏洞管理之间查询 ARG 数据的更多示例。 有关如何编辑工作簿的详细信息,请参阅 Microsoft Defender for Cloud 中的工作簿库。