管理员指南:将 PowerShell 与 Azure 信息保护统一客户端配合使用
注意
你是否想要了解 Microsoft Purview 信息保护(以前称为 Microsoft 信息保护 (MIP))方面的信息?
Azure 信息保护加载项已停用,并替换为 Microsoft 365 应用和服务中内置的标签。 详细了解其他 Azure 信息保护组件的支持状态。
新的Microsoft Purview 信息保护客户端(没有加载项)目前为预览版,并计划正式发布。
安装 Azure 信息保护统一标记客户端时,会自动将 PowerShell 命令作为 AzureInformationProtection 模块的一部分进行安装,其中包含用于标记的 cmdlet。
使用 AzureInformationProtection 模块,可以通过运行自动化脚本的命令来管理客户端。
例如:
- Get-AIPFileStatus:获取指定文件的 Azure 信息保护标签和保护信息。
- Set-AIPFileClassification:扫描某个文件,以便根据策略中配置的条件自动设置文件的 Azure 信息保护标签。
- Set-AIPFileLabel:设置或删除文件的 Azure 信息保护标签,并根据标签配置或自定义权限设置或删除保护。
- Set-AIPAuthentication:设置 Azure 信息保护客户端的身份验证凭据。
将 AzureInformationProtection 模块安装在 \ProgramFiles (x86)\Microsoft Azure Information Protection 文件夹中,然后将此文件夹添加到 PSModulePath 系统变量。 此模块的 .dll 命名为 AIP.dll。
重要
AzureInformationProtection 模块不支持配置标签或标签策略的高级设置。
对于这些设置,你需要使用安全与合规中心 PowerShell。 有关详细信息,请参阅 Azure 信息保护统一标记客户端的自定义配置。
提示
若要使用路径长度超过 260 个字符的 cmdlet,请使用自 Windows 10 版本 1607 开始提供的以下组策略设置:
“本地计算机策略”“计算机配置”“管理模板”“所有设置”“启用 Win32 长路径”
对于 Windows Server 2016,在安装 Windows 10 的最新管理模板 (.admx) 时,可以使用相同的组策略设置。
有关详细信息,请参阅 Windows 10 开发人员文档中的最大路径长度限制一节。
使用 AzureInformationProtection 模块的先决条件
除了安装 AzureInformationProtection 模块的先决条件之外,在使用 Azure 信息保护的标记 cmdlet 时还有额外的先决条件:
必须激活 Azure 权限管理服务。
如果你的 Azure 信息保护租户未激活,请参阅从 Azure 信息保护中激活保护服务的说明。
使用自己的帐户从他人的文件中删除保护:
- 必须为你的组织启用超级用户功能。
- 你的帐户必须配置为 Azure权限管理的超级用户。
例如,你可能想要删除对其他人的保护,以便发现或恢复数据。 如果使用标签应用保护,则可以通过设置一个不应用保护的新标签来删除该保护,也可以直接删除标签。
若要删除保护,请将 Set-AIPFileLabel cmdlet 与 RemoveProtection 参数结合使用。 在某些情况下,删除保护功能可能处于禁用状态,必须先使用 Set-LabelPolicy cmdlet 启用该功能。
RMS 到统一标记 cmdlet 的映射
如果已从 Azure RMS 迁移,请注意,与 RMS 相关的 cmdlet 已弃用,可用于统一标记。
已为统一标记将某些旧 cmdlet 替换为新 cmdlet。 例如,如果将 New-RMSProtectionLicense 与 RMS 保护一起使用,并已迁移到统一标记,请改用 New-AIPCustomPermissions。
下表通过用于统一标记的更新版 cmdlet 映射了与 RMS 相关的 cmdlet:
| RMS cmdlet | 统一标记 cmdlet |
|---|---|
| Get-RMSFileStatus | Get AIPFileStatus |
| Get-RMSServer | 与统一标记无关。 |
| Get-RMSServerAuthentication | Set-AIPAuthentication |
| Clear-RMSAuthentication | Set-AIPAuthentication |
| Set-RMSServerAuthentication | Set-AIPAuthentication |
| Get-RMSTemplate | 与统一标记无关。 |
| New-RMSProtectionLicense | New-AIPCustomPermissions 和 Set-AIPFileLabel,带有 CustomPermissions 参数。 |
| Protect-RMSFile | Set-AIPFileLabel |
| Unprotect-RMSFile | Set-AIPFileLabel,带有 RemoveProtection 参数。 |
如何以非交互方式为 Azure 信息保护标记文件
默认情况下,运行 cmdlet 进行标记时,命令会在交互式 PowerShell 会话中你自己的用户上下文运行。
有关详情,请参阅:
- 以无人参与方式运行 AIP 标记 cmdlet 的先决条件
- 为 Set-AIPAuthentication 创建和配置 Microsoft Entra 应用程序
- 运行 Set-AIPAuthentication cmdlet
注意
如果计算机无法访问 Internet,则无需在 Microsoft Entra ID 中创建应用并运行 Set-AIPAuthentication cmdlet。 相反,请按照断开连接的计算机中的说明操作。
以无人参与方式运行 AIP 标记 cmdlet 的先决条件
若要以无人参与方式运行 Azure 信息保护标记 cmdlet,请使用以下访问详细信息:
可以交互方式登录的 Windows 帐户。
用于委派访问的 Microsoft Entra 帐户。 为了便于管理,请使用从 Active Directory 同步到 Microsoft Entra ID 的单个帐户。
对于委派用户帐户:
要求 详细信息 标签策略 请确保已为此帐户分配了标签策略,并且该策略包含要使用的已发布标签。
如果对不同用户使用标签策略,可能需要创建新的标签策略,发布所有标签,并仅将此策略发布到该委派用户帐户。解密内容 如果此帐户需要解密内容,例如,要重新保护文件并检查其他人保护的文件,请使其成为 Azure 信息保护的超级用户,并确保已启用超级用户功能。 载入控件 如果对分阶段部署实现了载入控件,还请确保已配置的载入控件中包含此帐户。 Microsoft Entra 访问令牌,用于设置和存储委派用户的凭据,以向 Azure 信息保护进行身份验证。 Microsoft Entra ID 中的令牌过期后,必须再次运行此 cmdlet,以获取新令牌。
Set-AIPAuthentication 的参数使用 Microsoft Entra ID 中的应用注册过程中的值。 有关详细信息,请参阅为 Set-AIPAuthentication 创建和配置 Microsoft Entra 应用程序。
首先运行 Set-AIPAuthentication cmdlet,以非交互方式运行标记 cmdlet。
运行 AIPAuthentication cmdlet 的计算机会下载在 Microsoft Purview 合规性门户中分配给你的委托用户帐户的标记策略。
为 Set-AIPAuthentication 创建和配置 Microsoft Entra 应用程序
Set-AIPAuthentication cmdlet 要求对 AppId 和 AppSecret 参数进行应用注册。
若要为统一标记客户端 Set-AIPAuthentication cmdlet 创建新应用注册,请执行以下操作:
在新的浏览器窗口中,登录到与 Azure 信息保护配合使用的 Microsoft Entra 租户的 Azure 门户。
导航到“Microsoft Entra ID”>“管理”>“应用注册”,然后选择“新注册”。
在“注册应用程序”窗格上,指定以下值,然后单击“注册”:
选项 值 名称 AIP-DelegatedUser
根据需要指定其他名称。 对于每个租户,该名称必须是唯一的。支持的帐户类型 选择“仅此组织目录中的帐户”。 重定向 URI(可选) 选择“Web”,然后输入 https://localhost。在“AIP-DelegatedUser”窗格中,复制“应用程序(客户端) ID”的值。
此值类似于以下示例:
77c3c1c3-abf9-404e-8b2b-4652836c8c66。运行 Set-AIPAuthentication cmdlet 时,此值用于 AppId 参数。 粘贴并保存此值,供以后参考。
从侧栏中选择“管理”>“证书和密码”。
在“AIP-DelegatedUse - 证书和密码”窗格的“客户端密码”部分选择“+ 新建客户端密码”。
对于“添加客户端密码”,请指定以下各项,然后选择“添加”:
字段 Value 说明 Azure Information Protection unified labeling clientExpires 指定所选的持续时间(1 年、2 年或永不过期) 返回到“AIP-DelegatedUser - 证书和密码”窗格,在“客户端密码”部分复制“VALUE”的字符串。
此字符串类似于以下示例:
OAkk+rnuYc/u+]ah2kNxVbtrDGbS47L4。若要确保复制所有字符,请选择“复制到剪贴板”图标。
重要
请务必保存此字符串,因为它不会再次显示,并且无法检索。 对于所使用的任何敏感信息,请安全地存储保存的值并限制对它的访问。
从边栏中选择“管理”>“API 权限”。
在“AIP-DelegatedUser - API 权限”窗格上,选择“添加权限”。
在“请求 API 权限”窗格上,确保你在“Microsoft API”选项卡上,然后选择“Azure 权限管理服务”。
当系统提示你提供应用程序所需的权限类型时,请选择“应用程序权限”。
对于“选择权限”,展开“内容”并选择以下各项,然后选择“添加权限”。
- Content.DelegatedReader
- Content.DelegatedWriter
返回到“AIP-DelegatedUser - API 权限”窗格上,再次选择“添加权限”。
在“请求 AIP 权限”窗格上,选择“我的组织使用的 API”,并搜索“Microsoft 信息保护同步服务”。
在“请求获取 API 权限”窗格上,选择“应用程序权限”。
对于“选择权限”,展开“UnifiedPolicy”,选择“UnifiedPolicy.Tenant.Read”,然后选择“添加权限”。
返回到AIP-委托用户-API权限窗格,对你的租户名称<选择授予管理员同意>,然后在出现确认提示时选择是。
API 权限应如下图所示:
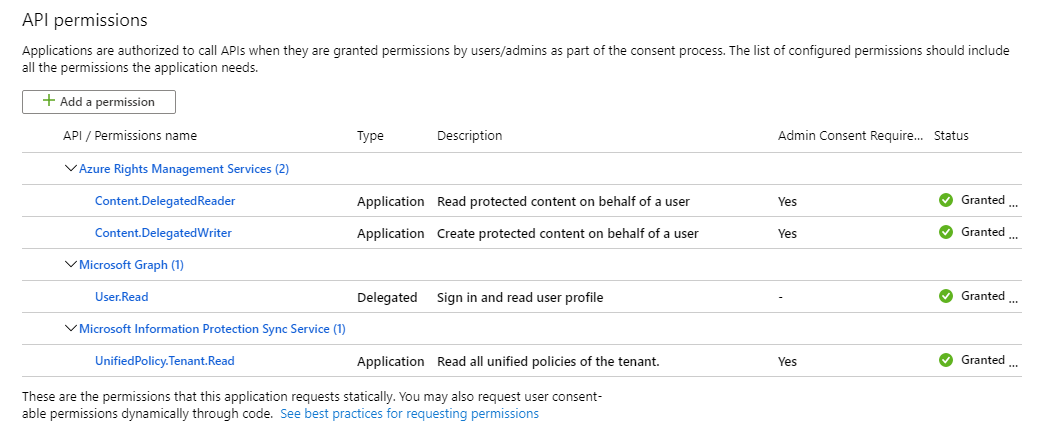
现在,你已使用密码完成此应用的注册,接下来可以运行带有 AppId 和 AppSecret 参数的 Set-AIPAuthentication。 此外,还需要租户 ID。
提示
可以使用 Azure 门户快速复制你的租户 ID:“Microsoft Entra ID”>“管理”>“属性”>“目录 ID”。
运行 Set-AIPAuthentication cmdlet
在选中“以管理员身份运行”选项的情况下打开 Windows PowerShell。
在 PowerShell 会话中,创建一个变量以存储将以非交互方式运行的 Windows 用户帐户的凭据。 例如,如果为扫描程序创建了服务帐户:
$pscreds = Get-Credential "CONTOSO\srv-scanner"系统将提示你输入此帐户的密码。
运行带有 OnBeHalfOf 参数的 Set-AIPAuthentication Cmdlet,将所创建的变量指定为其值。
同时,在 Microsoft Entra ID 中指定你的应用注册值、租户 ID 和委派用户帐户的名称。 例如:
Set-AIPAuthentication -AppId "77c3c1c3-abf9-404e-8b2b-4652836c8c66" -AppSecret "OAkk+rnuYc/u+]ah2kNxVbtrDGbS47L4" -TenantId "9c11c87a-ac8b-46a3-8d5c-f4d0b72ee29a" -DelegatedUser scanner@contoso.com -OnBehalfOf $pscreds
PowerShell cmdlet 的常用参数
有关常用参数的信息,请参阅关于常用参数。
后续步骤
在 PowerShell 会话中,要获得 cmdlet 帮助,请键入 Get-Help <cmdlet name> -online。 例如:
Get-Help Set-AIPFileLabel -online
有关详细信息,请参阅:
反馈
即将发布:在整个 2024 年,我们将逐步淘汰作为内容反馈机制的“GitHub 问题”,并将其取代为新的反馈系统。 有关详细信息,请参阅:https://aka.ms/ContentUserFeedback。
提交和查看相关反馈