你当前正在访问 Microsoft Azure Global Edition 技术文档网站。 如果需要访问由世纪互联运营的 Microsoft Azure 中国技术文档网站,请访问 https://docs.azure.cn。
什么是 Azure 负载均衡器?
“负载均衡”是指在一组后端服务器或资源之间有效地分配传入的网络流量。
Azure 负载均衡器在开放式系统互连 (OSI) 模型的第 4 层上运行。 它是客户端的单一联系点。 负载均衡器将抵达负载均衡器前端的入站流分配到后端池实例。 这些流取决于配置的负载均衡规则和运行状况探测。 后端池实例可以是 Azure 虚拟机,或虚拟机规模集中的实例。
公共负载均衡器 可以为虚拟网络中的虚拟机 (VM) 提供出站连接。 可以通过将专用 IP 地址转换为公共 IP 地址来实现这些连接。 公共负载均衡器用于对传入 VM 的 Internet 流量进行负载均衡。
内部(或专用)负载平衡器 用于仅在前端需要专用 IP 的情况。 内部负载均衡器用于对虚拟网络内部的流量进行负载均衡。 在混合方案中,可以从本地网络访问负载均衡器前端。
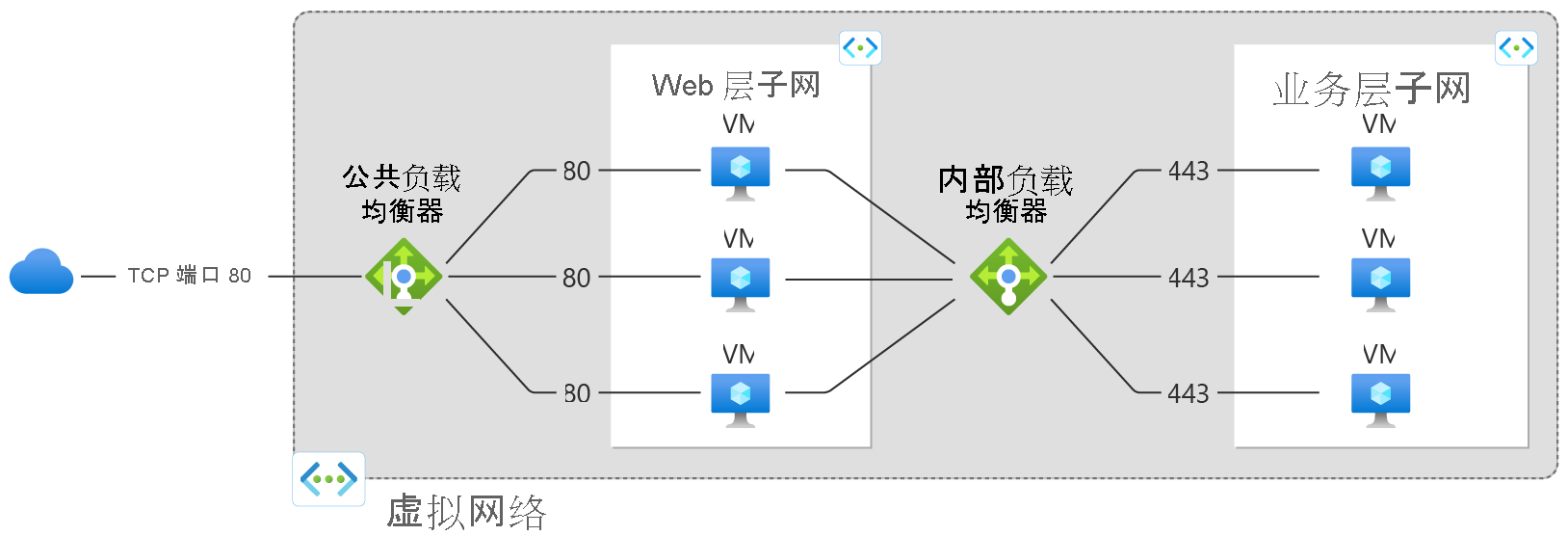
图:使用公共和内部负载均衡器对多层应用程序进行均衡
有关各个负载均衡器组件的详细信息,请参阅 Azure 负载均衡器组件。
为什么使用 Azure 负载均衡器?
使用 Azure 负载均衡器可以缩放应用程序,并创建高度可用的服务。 负载均衡器支持入站和出站方案。 负载均衡器提供低延迟和高吞吐量,以及为所有 TCP 和 UDP 应用程序纵向扩展到数以百万计的流。
可以通过使用 Azure 标准负载均衡器来完成的关键方案包括:
直通负载均衡,这实现了超低延迟。
配置 Azure 虚拟机的出站连接。
使用 运行状况探测 来监视已实现负载均衡的资源。
使用 端口转发 通过公共 IP 地址和端口访问虚拟网络中的虚拟机。
启用对 IPv6负载均衡 的支持。
标准负载均衡器通过 Azure Monitor 提供多维度指标。 可以就给定维度对这些指标进行筛选、分组和细分。 可便于深入了解服务的当前及历史性能和运行状况。 Azure 负载均衡器见解提供了一个预配置的仪表板,其中有用于呈现这些指标的实用可视化效果。 还支持资源运行状况。 有关更多详细信息,请查看标准负载均衡器诊断。
对 多个端口和/或多个 IP 地址 上的服务进行负载均衡。
使用 HA 端口 ,同时对所有端口上的 TCP 和 UDP 流进行负载均衡。
链标准负载均衡器和网关负载均衡器。
默认保护
标准负载均衡器是基于零信任网络安全模型构建的。
标准负载均衡器默认情况下为安全状态,并且是虚拟网络的一部分。 虚拟网络是一个专用的隔离网络。
标准负载均衡器和标准公共 IP 地址对入站连接关闭,除非由网络安全组打开。 NSG 用于显式允许允许的流量。 如果虚拟机资源的子网或 NIC 上没有 NSG,则不允许流量访问此资源。 若要了解 NSG 以及如何将它们应用于你的方案,请参阅网络安全组。
默认情况下,基本负载均衡器对 Internet 开放。
负载均衡器不会存储客户数据。
定价和 SLA
有关标准负载均衡器定价的信息,请参阅负载均衡器定价。 基本负载均衡器是免费提供的。 请参阅负载均衡器的 SLA。 基本负载均衡器没有 SLA。
新增功能
订阅 RSS 源,并在 Azure 更新页上查看最新的 Azure 负载均衡器功能更新。
后续步骤
请参阅创建公共标准负载均衡器以开始使用负载均衡器。
若要详细了解 Azure 负载均衡器限制和组件,请参阅 Azure 负载均衡器组件和 Azure 负载均衡器概念