Azure 基于角色的访问控制 (Azure RBAC) 是用于管理 Azure 资源访问权限的授权系统。 若要授予访问权限,请将角色分配给特定范围内的用户、组、服务主体或托管标识。 本文介绍如何使用 Azure 门户分配角色。
如果需要在 Microsoft Entra ID 中分配管理员角色,请参阅向用户分配 Microsoft Entra 角色。
你当前正在访问 Microsoft Azure Global Edition 技术文档网站。 如果需要访问由世纪互联运营的 Microsoft Azure 中国技术文档网站,请访问 https://docs.azure.cn。
Azure 基于角色的访问控制 (Azure RBAC) 是用于管理 Azure 资源访问权限的授权系统。 若要授予访问权限,请将角色分配给特定范围内的用户、组、服务主体或托管标识。 本文介绍如何使用 Azure 门户分配角色。
如果需要在 Microsoft Entra ID 中分配管理员角色,请参阅向用户分配 Microsoft Entra 角色。
若要分配 Azure 角色,必须具有:
Microsoft.Authorization/roleAssignments/write 权限,例如基于角色的访问控制管理员或用户访问管理员登录 Azure 门户。
在顶部的“搜索”框中,搜索要授权访问的范围。 例如,搜索“管理组”、“订阅”、“资源组”或某个特定资源 。
单击该范围的特定资源。
下面展示了一个示例资源组。
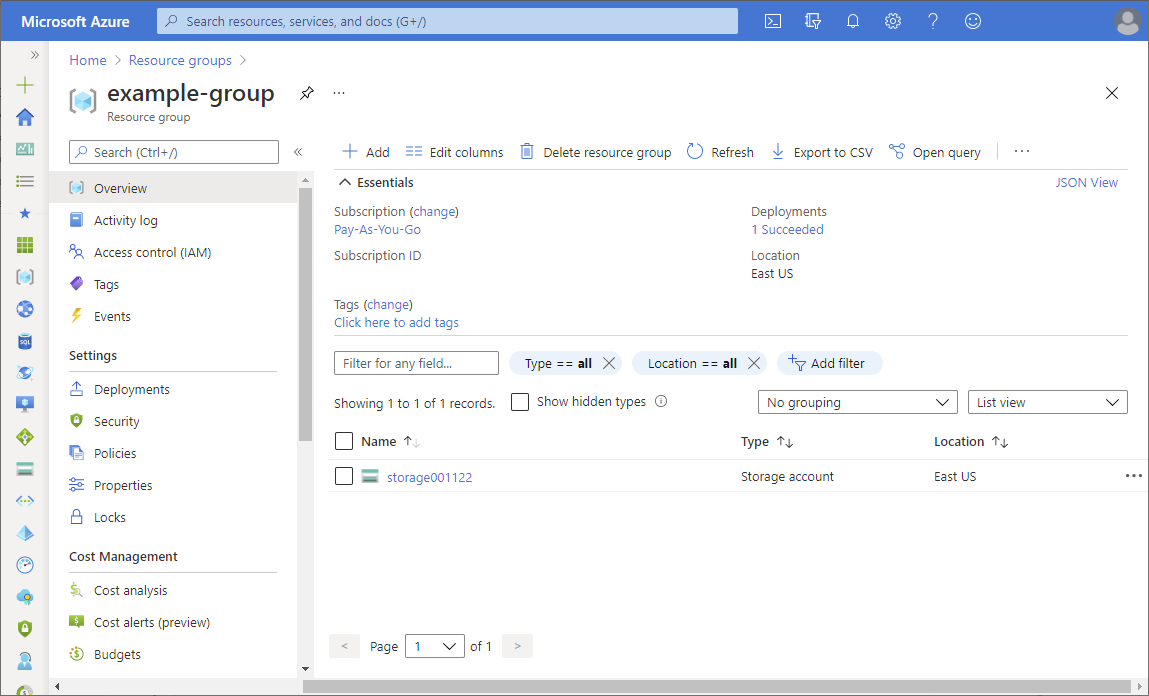
“访问控制(IAM)”是一个页面,通常用于分配角色以授予对 Azure 资源的访问权限。 该功能也称为标识和访问管理 (IAM),会显示在 Azure 门户中的多个位置。
单击“访问控制(IAM)”。
下面显示了资源组的“访问控制(IAM)”页的示例。
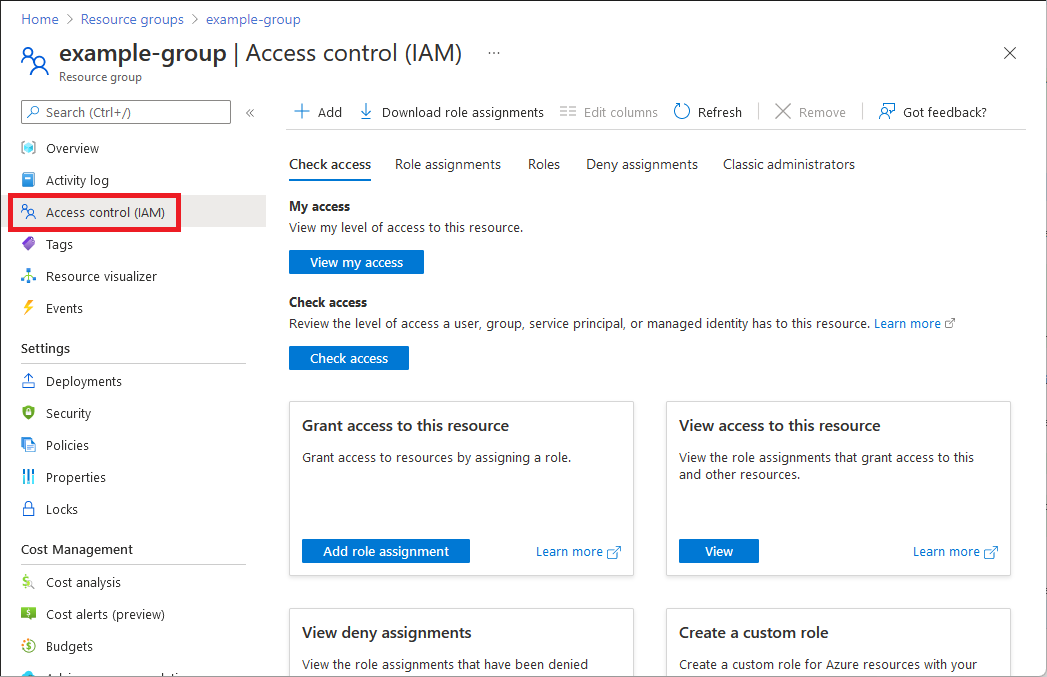
单击“角色分配”选项卡以查看在此范围内的角色分配。
单击“添加”>“角色分配”。
如果没有分配角色的权限,则将禁用“添加角色分配”选项。
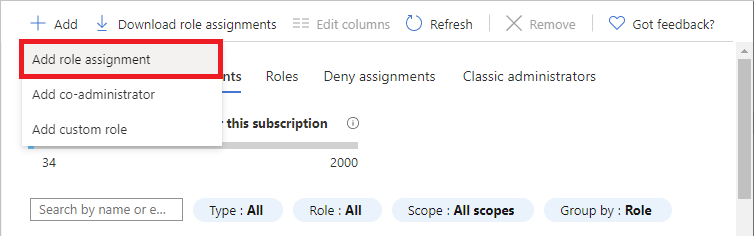
“添加角色分配”页面随即打开。
执行以下步骤:
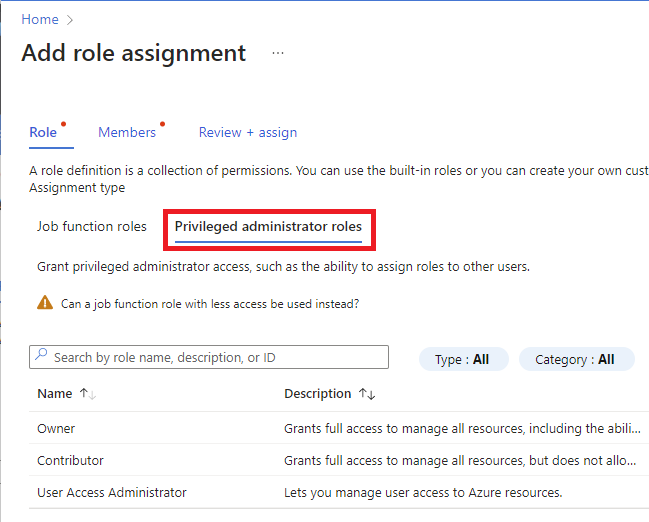
在“角色”选项卡上,选择要使用的角色。
可按名称或说明搜索角色。 还可按类型和类别筛选角色。
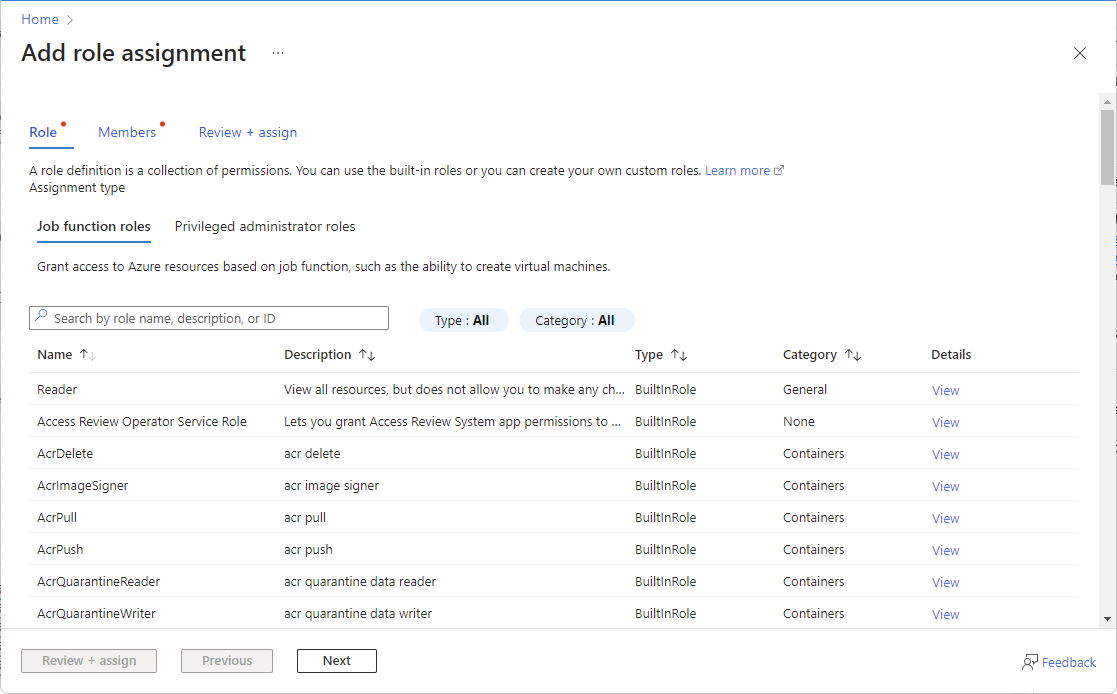
如果要分配特权管理员角色,请选择“特权管理员角色”选项卡以选择角色。
有关使用特权管理员角色分配时的最佳做法,请参阅 Azure RBAC 最佳做法。
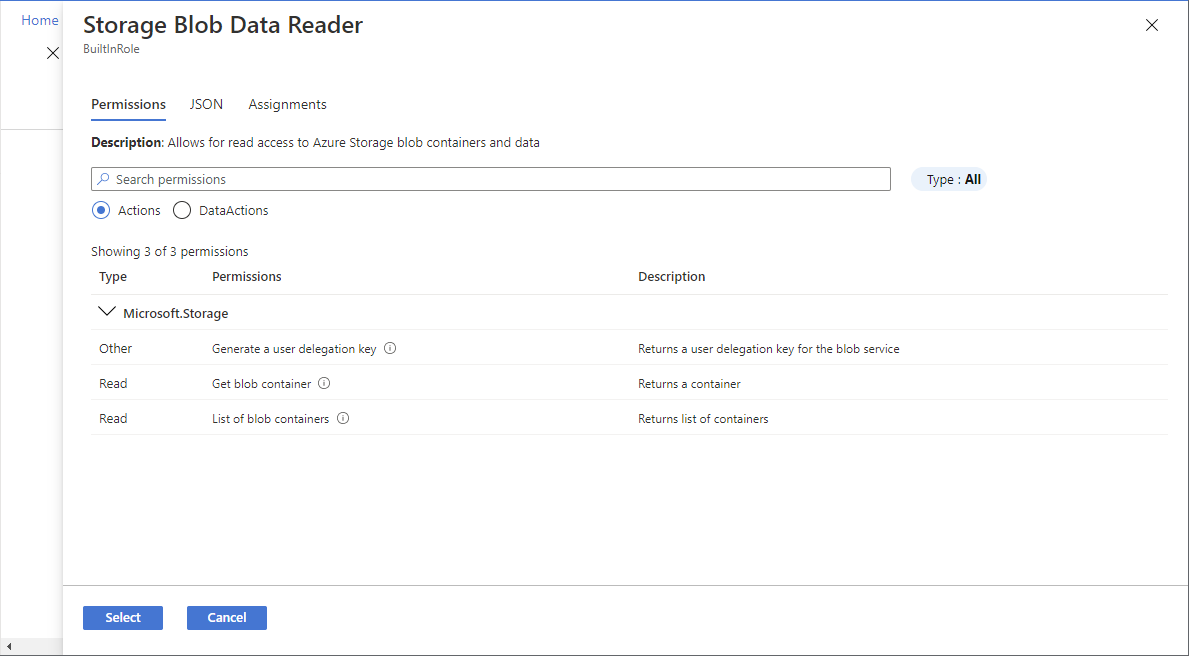
在“详细信息”列中,单击“查看”获取有关角色的更多详细信息 。
单击 “下一步” 。
执行以下步骤:
在“成员”选项卡上选择“用户、组或服务主体”,将所选角色分配给一个或多个 Microsoft Entra 用户、组或服务主体(应用程序)。
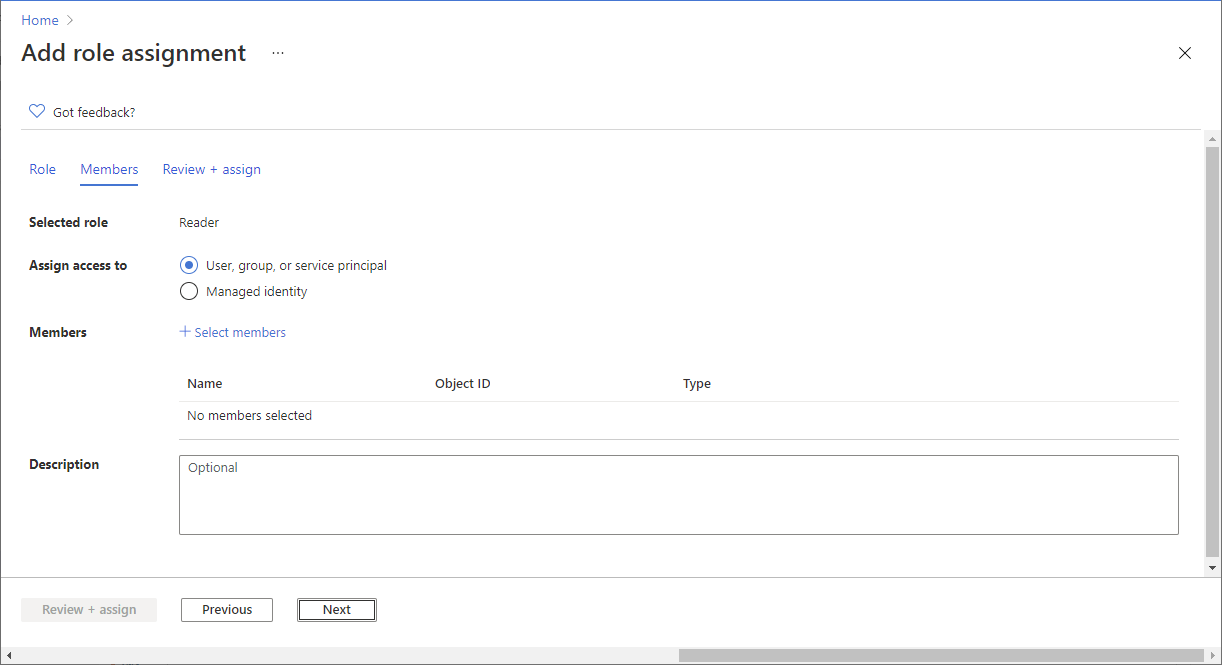
单击“选择成员”。
查找并选择用户、组或服务主体。
可以在“选择”框中键入,以在目录中搜索显示名称或电子邮件地址。

单击“选择”,将用户、组或服务主体添加到“成员”列表中。
若要将所选角色分配给一个或多个托管标识,请选择“托管标识”。
单击“选择成员”。
查找并选择托管标识。
对于系统分配的托管标识,你可以通过 Azure 服务实例选择托管标识。
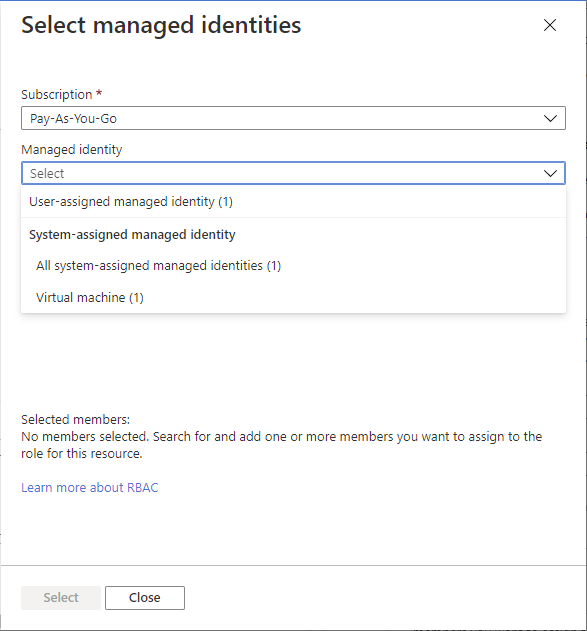
单击“选择”将托管标识添加到“成员”列表中。
在“说明”文本框中,输入此角色分配的可选说明。
稍后,可以在“角色分配”列表中显示此说明。
单击 “下一步” 。
如果所选角色支持使用条件,将会显示“条件”选项卡,你可选择向角色分配添加条件。 条件是可选择性地添加到角色分配中的一项额外检查,可提供更精细的访问控制。
“条件”选项卡看起来可能会有所不同,具体取决于所选角色。
重要
委派具有条件的 Azure 角色分配管理目前为预览版。 有关 beta 版本、预览版或尚未正式发布的版本的 Azure 功能所适用的法律条款,请参阅 Microsoft Azure 预览版的补充使用条款。
如果选择了以下特权角色之一,请按照本部分中的步骤操作。
在“条件”选项卡上“用户可以执行的操作”下,选择“允许用户仅将所选角色分配给所选主体”选项(权限较少)”。
单击“选择角色和主体”以添加条件,用于约束此用户可以向其分配角色的角色和主体。
按照将 Azure 角色分配管理委派给有条件的其他人中的步骤操作。
如果选择了以下存储角色之一,请遵循本部分中的步骤。
如果要根据存储属性进一步优化角色分配,请单击“添加条件”。
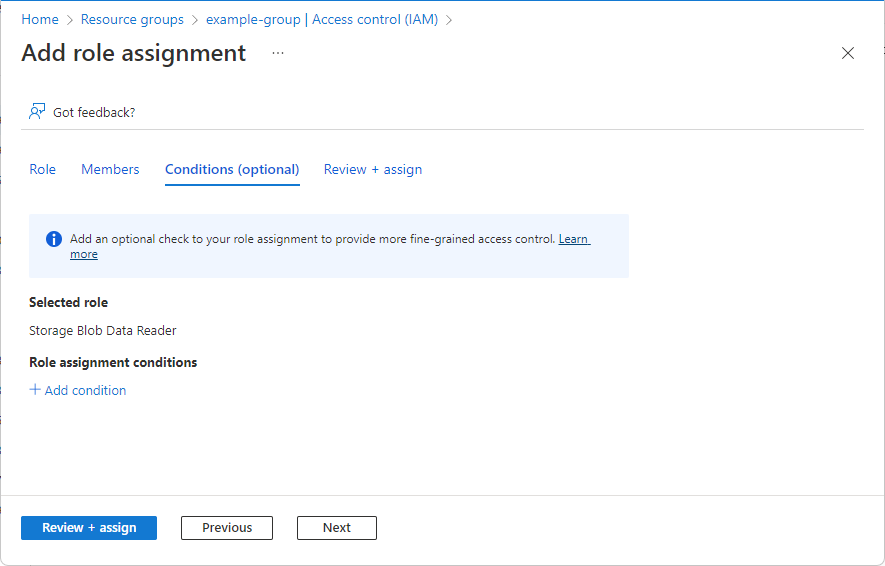
请遵循添加或编辑 Azure 角色分配条件中的步骤。
执行以下步骤:
在“查看 + 分配”选项卡上,查看角色分配设置。
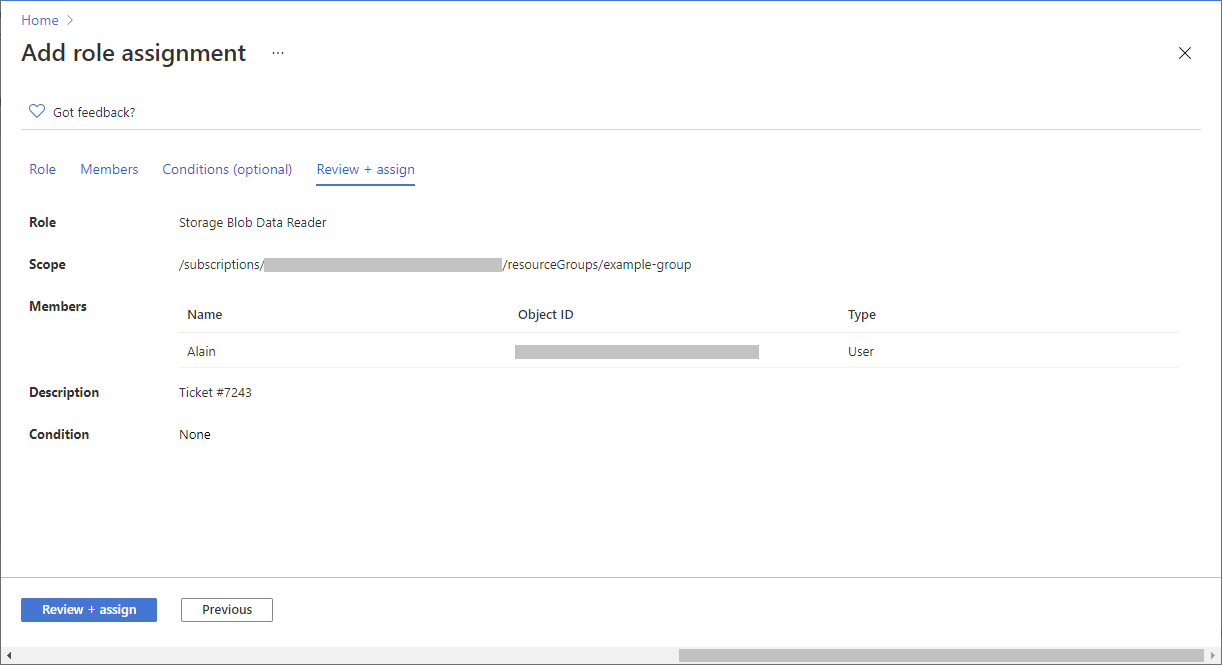
单击“查看 + 分配”以分配角色。
片刻之后,会在所选范围内为安全主体分配角色。
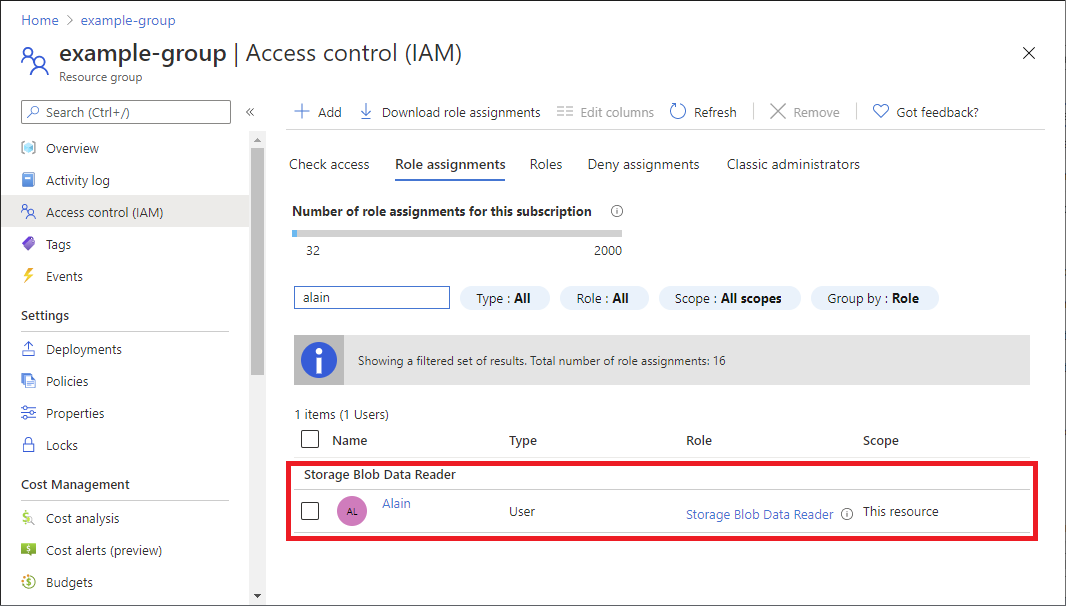
如果看不到角色分配的说明,请单击“编辑列”以添加“说明”列 。
即将发布:在整个 2024 年,我们将逐步淘汰作为内容反馈机制的“GitHub 问题”,并将其取代为新的反馈系统。 有关详细信息,请参阅:https://aka.ms/ContentUserFeedback。
提交和查看相关反馈