你当前正在访问 Microsoft Azure Global Edition 技术文档网站。 如果需要访问由世纪互联运营的 Microsoft Azure 中国技术文档网站,请访问 https://docs.azure.cn。
教程 - 使用存储在密钥保管库中的 TLS 证书保护 Azure 中 Windows 虚拟机上的 Web 服务器
适用于:✔️ Windows VM ✔️ 灵活规模集
注意
目前,此文档仅适用于通用化映像。 如果使用专用磁盘尝试此教程,将会收到错误。
要保护 Web 服务器,可以使用传输层安全性 (TLS) 证书来加密 Web 流量。 TLS 证书可存储在 Azure 密钥保管库中,并可安全部署到 Azure 中的 Windows 虚拟机 (VM)。 本教程介绍如何执行下列操作:
- 创建 Azure 密钥保管库。
- 生成证书或将其上传到密钥保管库。
- 创建 VM 并安装 IIS Web 服务器。
- 将证书注入到 VM 中并为 IIS 配置 TLS 绑定。
启动 Azure Cloud Shell
Azure Cloud Shell 是免费的交互式 shell,可以使用它运行本文中的步骤。 它预安装有常用 Azure 工具并将其配置与帐户一起使用。
要打开 Cloud Shell,只需从代码块的右上角选择“打开 Cloudshell”。 也可以通过转到 https://shell.azure.com/powershell 在单独的浏览器标签页中启动 Cloud Shell。 选择“复制”以复制代码块,将其粘贴到 Cloud Shell 中,然后按 Enter 来运行代码块。
概述
Azure Key Vault 保护加密密钥和机密,例如证书或密码。 Key Vault 有助于简化证书管理过程,让我们持续掌控用于访问这些证书的密钥。 可以在密钥保管库中创建自签名证书,或者可以上传已有的现有受信任证书。
将证书注入正在运行的 VM,而不是使用包含植入证书的自定义 VM 映像。 此过程可确保在部署过程中,在 Web 服务器上安装最新的证书。 如果续订或替换了证书,也不需要创建新的自定义 VM 映像。 创建额外的 VM 时,会自动注入最新证书。 在整个过程中,证书永远不会离开 Azure 平台,也不会在脚本、命令行历史记录或模板中公开。
创建 Azure Key Vault
创建 Key Vault 和证书之前,需使用 New-AzResourceGroup 创建资源组。 以下示例在“美国东部” 位置创建名为 myResourceGroupSecureWeb 的资源组:
$resourceGroup = "myResourceGroupSecureWeb"
$location = "East US"
New-AzResourceGroup -ResourceGroupName $resourceGroup -Location $location
接下来,使用 New-AzKeyVault 创建一个密钥保管库。 每个密钥保管库需要具有唯一的名称,并且全部为小写。 将以下示例中的 mykeyvault 替换为自己的唯一密钥保管库名称:
$keyvaultName="mykeyvault"
New-AzKeyVault -VaultName $keyvaultName `
-ResourceGroup $resourceGroup `
-Location $location `
-EnabledForDeployment
生成证书并将其存储在密钥保管库中
为供生产使用,应使用 Import-AzKeyVaultCertificate 导入由受信任提供程序签名的有效证书。 在本教程中,以下示例演示了如何使用 Add-AzKeyVaultCertificate 生成一个自签名证书,该证书使用 New-AzKeyVaultCertificatePolicy 指定的默认证书策略。
$policy = New-AzKeyVaultCertificatePolicy `
-SubjectName "CN=www.contoso.com" `
-SecretContentType "application/x-pkcs12" `
-IssuerName Self `
-ValidityInMonths 12
Add-AzKeyVaultCertificate `
-VaultName $keyvaultName `
-Name "mycert" `
-CertificatePolicy $policy
创建虚拟机
使用 Get-Credential 设置 VM 的管理员用户名和密码:
$cred = Get-Credential
现在,可使用 New-AzVM 创建 VM。 以下示例在“EastUS”位置 创建一个名为 myVM 的 VM。 如果支持的网络资源不存在,则会创建这些资源。 此 cmdlet 还打开端口 443,目的是允许安全的 Web 流量。
# Create a VM
New-AzVm `
-ResourceGroupName $resourceGroup `
-Name "myVM" `
-Location $location `
-VirtualNetworkName "myVnet" `
-SubnetName "mySubnet" `
-SecurityGroupName "myNetworkSecurityGroup" `
-PublicIpAddressName "myPublicIpAddress" `
-Credential $cred `
-OpenPorts 443
# Use the Custom Script Extension to install IIS
Set-AzVMExtension -ResourceGroupName $resourceGroup `
-ExtensionName "IIS" `
-VMName "myVM" `
-Location $location `
-Publisher "Microsoft.Compute" `
-ExtensionType "CustomScriptExtension" `
-TypeHandlerVersion 1.8 `
-SettingString '{"commandToExecute":"powershell Add-WindowsFeature Web-Server -IncludeManagementTools"}'
创建 VM 需要几分钟时间。 最后一个步骤通过 Set-AzVmExtension 使用 Azure 自定义脚本扩展来安装 IIS Web 服务器。
将 Key Vault 中的证书添加到 VM
若要将 Key Vault 中的证书添加到 VM,请使用 Get-AzKeyVaultSecret 获取证书的 ID。 使用 Add-AzVMSecret 将证书添加到 VM:
$certURL=(Get-AzKeyVaultSecret -VaultName $keyvaultName -Name "mycert").id
$vm=Get-AzVM -ResourceGroupName $resourceGroup -Name "myVM"
$vaultId=(Get-AzKeyVault -ResourceGroupName $resourceGroup -VaultName $keyVaultName).ResourceId
$vm = Add-AzVMSecret -VM $vm -SourceVaultId $vaultId -CertificateStore "My" -CertificateUrl $certURL | Update-AzVM
将 IIS 配置为使用该证书
再次通过 Set-AzVMExtension 使用自定义脚本扩展来更新 IIS 配置。 此项更新会应用从 Key Vault 注入 IIS 的证书,并配置 Web 绑定:
$publicSettings = '{
"fileUris":["https://raw.githubusercontent.com/Azure-Samples/compute-automation-configurations/master/secure-iis.ps1"],
"commandToExecute":"powershell -ExecutionPolicy Unrestricted -File secure-iis.ps1"
}'
Set-AzVMExtension -ResourceGroupName $resourceGroup `
-ExtensionName "IIS" `
-VMName "myVM" `
-Location $location `
-Publisher "Microsoft.Compute" `
-ExtensionType "CustomScriptExtension" `
-TypeHandlerVersion 1.8 `
-SettingString $publicSettings
测试 Web 应用是否安全
使用 Get-AzPublicIPAddress 获取 VM 的公共 IP 地址。 以下示例获取前面创建的 myPublicIP 的 IP 地址:
Get-AzPublicIPAddress -ResourceGroupName $resourceGroup -Name "myPublicIPAddress" | select "IpAddress"
现可打开 Web 浏览器,并在地址栏中输入 https://<myPublicIP>。 若要接受有关使用自签名证书的安全警告,请依次选择“详细信息”和“继续转到网页”:
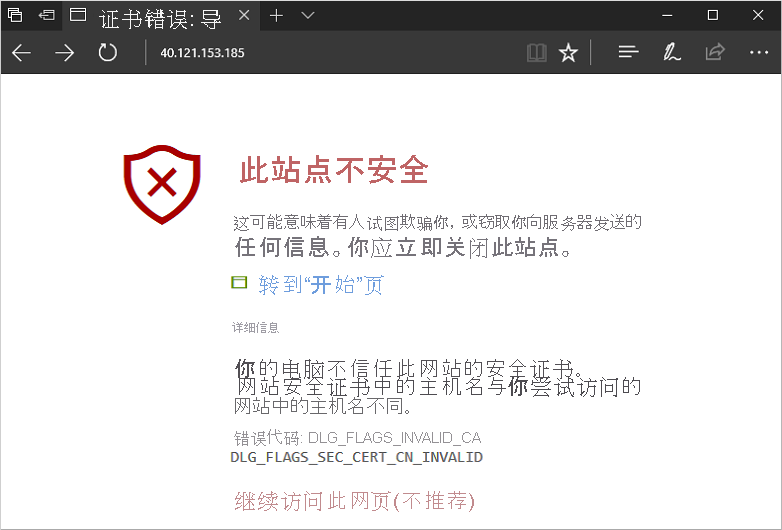
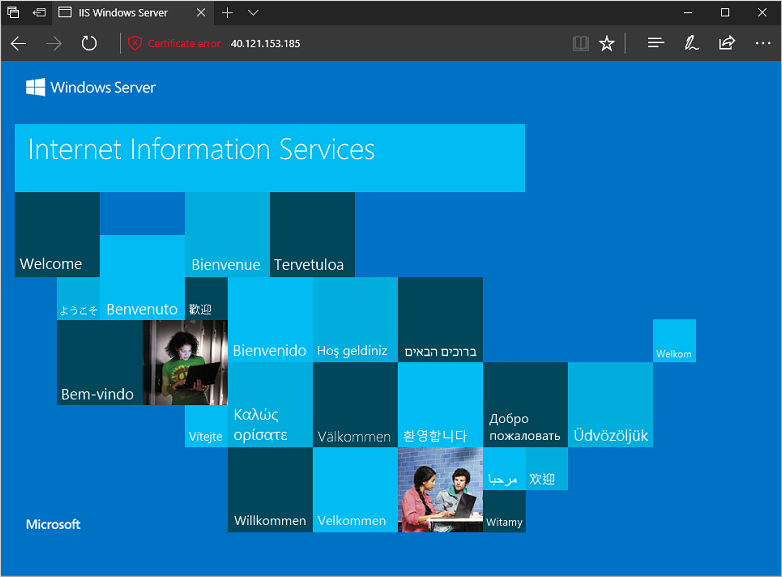
随即显示受保护的 IIS 网站,如下例所示:
后续步骤
在本教程中,你使用了存储在 Azure 密钥保管库中的 TLS 证书来保护 IIS Web 服务器。 你已了解如何执行以下操作:
- 创建 Azure 密钥保管库。
- 生成证书或将其上传到密钥保管库。
- 创建 VM 并安装 IIS Web 服务器。
- 将证书注入到 VM 中并为 IIS 配置 TLS 绑定。
有关预生成的虚拟机脚本示例,请参阅: