你当前正在访问 Microsoft Azure Global Edition 技术文档网站。 如果需要访问由世纪互联运营的 Microsoft Azure 中国技术文档网站,请访问 https://docs.azure.cn。
网络安全组如何筛选网络流量
可以使用 Azure 网络安全组来筛选 Azure 虚拟网络中出入 Azure 资源的网络流量。 网络安全组包含安全规则,这些规则可允许或拒绝多种 Azure 资源的入站和出站网络流量。 可以为每项规则指定源和目标、端口以及协议。
可以将资源从多个 Azure 服务部署到一个 Azure 虚拟网络中。 如需完整列表,请参阅可部署到虚拟网络中的服务。 可将零个或一个网络安全组与虚拟机中的每个虚拟网络子网和网络接口相关联。 可将同一网络安全组关联到选定的任意数量的子网和网络接口。
下图描述了如何使用不同的方案来部署网络安全组,以便网络流量通过 TCP 端口 80 出入 Internet:
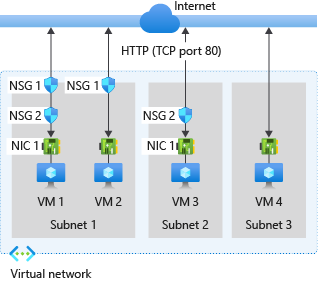
请参阅上图和以下文本,了解 Azure 如何处理网络安全组的入站和出站规则:
入站流量
对于入站流量,Azure 先处理与某个子网相关联的网络安全组(如果有)中的规则,然后处理与网络接口相关联的网络安全组(如果有)中的规则。 此过程也包括子网内流量。
VM1:系统会处理 NSG1 中的安全规则,因为它与 Subnet1 关联,而 VM1位于 Subnet1 中。 除非已创建允许端口 80 入站的规则,否则 DenyAllInbound默认安全规则会拒绝流量。 NSG2 不会评估这些被阻止的流量,因为它们与网络接口相关联。 但是,如果 NSG1 在其安全规则中允许端口 80,NSG2 会处理该流量。 若要允许从端口 80 到虚拟机的流量,NSG1 和 NSG2 必须指定一条规则来允许从 Internet 到端口 80 的流量。
VM2:系统会处理 NSG1 中的规则,因为 VM2 也在 Subnet1 中。 VM2 没有关联到其网络接口的网络安全组,因此会接收 NSG1 所允许的所有流量,或者会受到 NSG1 所拒绝的所有流量拒绝。 当网络安全组关联到子网时,对于同一子网中的所有资源,流量要么被允许,要么被拒绝。
VM3:由于没有网络安全组关联到 Subnet2,系统允许流量进入子网并由 NSG2 处理,因为 NSG2 关联到已附加到 VM3 的网络接口。
VM4:阻止流量发往 VM4,因为网络安全组没有关联到 Subnet3 或虚拟机中的网络接口。 如果没有关联的网络安全组,则阻止所有网络流量通过子网和网络接口。
出站流量
对于出站流量,Azure 先处理与某个网络接口相关联的网络安全组(如果有)中的规则,然后处理与子网相关联的网络安全组(如果有)中的规则。 此过程也包括子网内流量。
VM1:系统会处理 NSG2 中的安全规则。 除非创建安全规则以拒绝从端口 80 到 Internet 的出站流量,否则NSG1和NSG2中的AllowInternetOutbound默认安全规则都会允许流量。 如果NSG2在其安全规则中拒绝端口 80,则会拒绝流量,并且NSG1永远不会对其进行评估。 若要拒绝从虚拟机到端口 80 的流量,则两个网络安全组或其中的一个必须有一条规则来拒绝从端口 80 到 Internet 的流量。
VM2:所有流量都会通过网络接口发送到子网,因为附加到 VM2 的网络接口没有关联的网络安全组。 系统会处理 NSG1 中的规则。
VM3:如果NSG2在其安全规则中拒绝端口 80,则会拒绝流量。 如果NSG2不拒绝端口 80,NSG2中的AllowInternetOutbound默认安全规则会允许流量,因为没有与Subnet2关联的网络安全组。
VM4:允许来自 VM4 的所有网络流量,因为网络安全组没有关联到已附加到虚拟机的网络接口,也没有关联到 Subnet3。
子网内部流量
需要注意的是,与子网关联的 NSG 中的安全规则可能会影响子网中 VM 之间的连接。 默认情况下,同一子网中的虚拟机可以基于默认 NSG 规则进行通信,该 NSG 规则允许子网内流量。 如果将规则添加到拒绝所有入站和出站流量的 NSG1,VM1 和 VM2 将无法再相互通信。
可以通过查看网络接口的有效安全规则,轻松查看已应用到网络接口的聚合规则。 还可以使用 Azure 网络观察程序中的 IP 流验证功能来确定是否允许发往或发自网络接口的通信。 可以使用 IP 流验证以确定是允许还是拒绝通信。 此外,使用 IP 流验证以显示负责允许或拒绝流量的网络安全规则的标识。
注意
网络安全组关联到子网或关联到部署在经典部署模型中的虚拟机和云服务,以及关联到资源管理器部署模型中的子网或网络接口。 若要详细了解 Azure 部署模型,请参阅了解 Azure 部署模型。
提示
建议将网络安全组关联到子网或网络接口,但不要二者都关联,除非你有特定的理由来这样做。 由于关联到子网的网络安全组中的规则可能与关联到网络接口的网络安全组中的规则冲突,因此可能会出现意外的必须进行故障排除的通信问题。
后续步骤
若要了解哪些 Azure 资源可以部署到虚拟网络中并与网络安全组关联,请参阅 Azure 服务的虚拟网络集成。
如果从未创建过网络安全组,可以先完成快速教程以获取一些创建经验。
如果已熟悉网络安全组,需要对其进行管理,请参阅管理网络安全组。
如果有通信问题,需要对网络安全组进行故障排除,请参阅诊断虚拟机网络流量筛选器问题。
了解如何通过网络安全组流日志来分析出入具有关联网络安全组的资源的网络流量。