你当前正在访问 Microsoft Azure Global Edition 技术文档网站。 如果需要访问由世纪互联运营的 Microsoft Azure 中国技术文档网站,请访问 https://docs.azure.cn。
关于点到站点 VPN
点到站点 (P2S) VPN 网关连接用于创建从单个客户端计算机到虚拟网络的安全连接。 可通过从客户端计算机启动连接来建立 P2S 连接。 对于要从远程位置(例如从家里或会议室)连接到 Azure VNet 的远程工作者,此解决方案很有用。 如果只有一些客户端需要连接到 VNet,则还可以使用 P2S VPN 这一解决方案来代替 S2S VPN。 本文适用于资源管理器部署模型。
注意
点到站点配置需要基于路由的 VPN 类型。 有关 VPN 类型的详细信息,请参阅关于 VPN 网关设置。
P2S 使用哪种协议?
点到站点 VPN 可使用以下协议之一:
OpenVPN® 协议,一种基于 SSL/TLS 的 VPN 协议。 由于大多数防火墙都会打开 TLS 所用的出站 TCP 端口 443,因此 TLS VPN 解决方案可以穿透防火墙。 OpenVPN 可用于从 Android、iOS(11.0 及更高版本)、Windows、Linux 和 Mac 设备(macOS 10.13 及更高版本)进行连接。
安全套接字隧道协议 (SSTP),一个基于 TLS 的专属 VPN 协议。 由于大多数防火墙都会打开 TLS 所用的出站 TCP 端口 443,因此 TLS VPN 解决方案可以穿透防火墙。 只有 Windows 设备支持 SSTP。 Azure 支持所有采用 SSTP 并支持 TLS 1.2 的 Windows 版本(Windows 8.1 及更高版本)。
IKEv2 VPN,这是一种基于标准的 IPsec VPN 解决方案。 IKEv2 VPN 可用于从 Mac 设备进行连接(macOS 10.11 和更高版本)。
注意
P2S 的 IKEv2 和 OpenVPN 仅可用于资源管理器部署模型。 它们不可用于经典部署模型。
如何对 P2S VPN 客户端进行身份验证?
在 Azure 接受 P2S VPN 连接之前,必须先对用户进行身份验证。 Azure 提供两种机制用于对连接方用户进行身份验证。
证书身份验证
使用本机 Azure 证书身份验证时,设备上的客户端证书用于对连接方用户进行身份验证。 客户端证书从受信任的根证书生成,并安装在每台客户端计算机上。 可以使用通过企业解决方案生成的根证书,也可以生成自签名证书。
客户端证书的验证由 VPN 网关执行,在建立 P2S VPN 连接期间发生。 验证时需要使用根证书,必须将该证书上传到 Azure。
Microsoft Entra 身份验证
Microsoft Entra 身份验证允许用户使用其 Microsoft Entra 凭据连接到 Azure。 本机 Microsoft Entra 身份验证仅支持 OpenVPN 协议,并且需要使用 Azure VPN 客户端。 支持的客户端操作系统为 Windows 10 或更高版本和 macOS。
通过本机 Microsoft Entra 身份验证,可以将 Microsoft Entra 条件访问和多重身份验证 (MFA) 功能用于 VPN。
大致说来,需要执行以下步骤来配置 Microsoft Entra 身份验证:
使用下列其中一个链接下载最新版本的 Azure VPN 客户端安装文件:
- 使用客户端安装文件安装:https://aka.ms/azvpnclientdownload。
- 在客户端计算机上登录时直接安装:Microsoft Store。
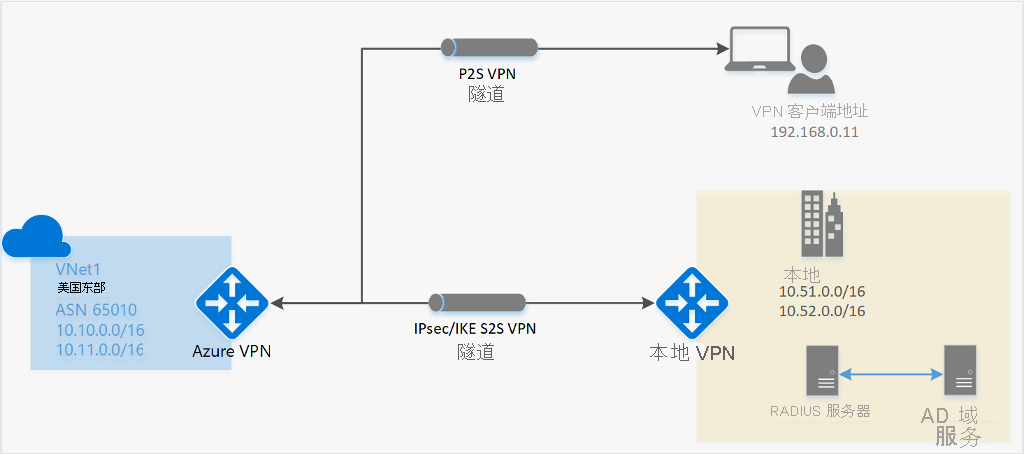
Active Directory (AD) 域服务器
AD 域身份验证可让用户使用其组织域凭据连接到 Azure。 它需要一台与 AD 服务器集成的 RADIUS 服务器。 组织也可以使用其现有的 RADIUS 部署。
可将 RADIUS 服务器部署到本地或 Azure VNet 中。 在身份验证期间,Azure VPN 网关充当传递设备,在 RADIUS 服务器与连接方设备之间来回转发身份验证消息。 因此,RADIUS 服务器必须能够访问网关。 如果 RADIUS 服务器位于本地,需要建立从 Azure 到本地站点的 VPN S2S 连接,才能实现这种访问。
RADIUS 服务器还能与 AD 证书服务集成。 这样,便可以使用 RADIUS 服务器以及用于 P2S 证书身份验证的企业证书部署,作为 Azure 证书身份验证的替代方法。 此方法的优点是不需要将根证书和吊销的证书上传到 Azure。
RADIUS 服务器还能与其他外部标识系统集成。 这样就为 P2S VPN 提供了大量的身份验证选项,包括多重身份验证选项。
客户端配置要求是什么?
客户端配置要求因使用的 VPN 客户端、身份验证类型和协议而异。 下表显示了可用的客户端以及每个配置的相应文章。
| 身份验证 | 隧道类型 | 生成配置文件 | 配置 VPN 客户端 |
|---|---|---|---|
| Azure 证书 | IKEv2、SSTP | Windows | 本机 VPN 客户端 |
| Azure 证书 | OpenVPN | Windows | - OpenVPN 客户端 - Azure VPN 客户端 |
| Azure 证书 | IKEv2、OpenVPN | macOS-iOS | macOS-iOS |
| Azure 证书 | IKEv2、OpenVPN | Linux | Linux |
| Microsoft Entra ID | OpenVPN (SSL) | Windows | Windows |
| Microsoft Entra ID | OpenVPN (SSL) | macOS | macOS |
| RADIUS - 证书 | - | 文章 | 文章 |
| RADIUS - 密码 | - | 文章 | 文章 |
| RADIUS - 其他方法 | - | 文章 | 文章 |
重要
从 2018 年 7 月 1 日开始,Azure VPN 网关将不再支持 TLS 1.0 和 1.1。 VPN 网关将仅支持 TLS 1.2。 仅点到站点连接会受到影响;站点到站点连接不受影响。 如果你在 Windows 10 及更高版本客户端上将 TLS 用于点到站点 VPN,则你无需采取任何操作。 如果在 Windows 7 和 Windows 8 客户端上使用 TLS 建立点到站点连接,请参阅 VPN 网关常见问题解答,了解更新说明。
哪些网关 SKU 支持 P2S VPN?
下表按隧道、连接和吞吐量显示网关 SKU。 有关其他表和有关此表的详细信息,请参阅 VPN 网关设置一文的“网关 SKU”部分。
| VPN 网关 代系 |
SKU | S2S/VNet 到 VNet 隧道 |
P2S SSTP 连接 |
P2S IKEv2/OpenVPN 连接 |
聚合 吞吐量基准 |
BGP | 区域冗余 | 虚拟网络中支持的 VM 数 |
|---|---|---|---|---|---|---|---|---|
| 第 1 代 | 基本 | 最大 10 | 最大 128 | 不支持 | 100 Mbps | 不支持 | 否 | 200 |
| 第 1 代 | VpnGw1 | 最大 30 | 最大 128 | 最大 250 | 650 Mbps | 支持 | 否 | 450 |
| 第 1 代 | VpnGw2 | 最大 30 | 最大 128 | 最大 500 | 1 Gbps | 支持 | 否 | 1300 |
| 第 1 代 | VpnGw3 | 最大 30 | 最大 128 | 最大 1000 | 1.25 Gbps | 支持 | 否 | 4000 |
| 第 1 代 | VpnGw1AZ | 最大 30 | 最大 128 | 最大 250 | 650 Mbps | 支持 | 是 | 1000 |
| 第 1 代 | VpnGw2AZ | 最大 30 | 最大 128 | 最大 500 | 1 Gbps | 支持 | 是 | 2000 |
| 第 1 代 | VpnGw3AZ | 最大 30 | 最大 128 | 最大 1000 | 1.25 Gbps | 支持 | 是 | 5000 |
| 第 2 代 | VpnGw2 | 最大 30 | 最大 128 | 最大 500 | 1.25 Gbps | 支持 | 否 | 685 |
| 第 2 代 | VpnGw3 | 最大 30 | 最大 128 | 最大 1000 | 2.5 Gbps | 支持 | 否 | 2240 |
| 第 2 代 | VpnGw4 | 最大 100* | 最大 128 | 最大 5000 | 5 Gbps | 支持 | 否 | 5300 |
| 第 2 代 | VpnGw5 | 最大 100* | 最大 128 | 最大 10000 | 10 Gbps | 支持 | 否 | 6700 |
| 第 2 代 | VpnGw2AZ | 最大 30 | 最大 128 | 最大 500 | 1.25 Gbps | 支持 | 是 | 2000 |
| 第 2 代 | VpnGw3AZ | 最大 30 | 最大 128 | 最大 1000 | 2.5 Gbps | 支持 | 是 | 3300 |
| 第 2 代 | VpnGw4AZ | 最大 100* | 最大 128 | 最大 5000 | 5 Gbps | 支持 | 是 | 4400 |
| 第 2 代 | VpnGw5AZ | 最大 100* | 最大 128 | 最大 10000 | 10 Gbps | 支持 | 是 | 9000 |
注意
基本 SKU 有限制,不支持 IKEv2、IPv6 或 RADIUS 身份验证。 有关详细信息,请参阅 VPN 网关设置一文。
在 P2S 的 VPN 网关上配置了哪些 IKE/IPsec 策略?
本部分中的表显示用于默认策略的值。 但这些值不反映受支持的可用于自定义策略的值。 对于自定义策略,请参阅 New-AzVpnClientIpsecParameter PowerShell cmdlet 中列出的接受的值。
IKEv2
| Cipher | 完整性 | PRF | DH 组 |
|---|---|---|---|
| GCM_AES256 | GCM_AES256 | SHA384 | GROUP_24 |
| GCM_AES256 | GCM_AES256 | SHA384 | GROUP_14 |
| GCM_AES256 | GCM_AES256 | SHA384 | GROUP_ECP384 |
| GCM_AES256 | GCM_AES256 | SHA384 | GROUP_ECP256 |
| GCM_AES256 | GCM_AES256 | SHA256 | GROUP_24 |
| GCM_AES256 | GCM_AES256 | SHA256 | GROUP_14 |
| GCM_AES256 | GCM_AES256 | SHA256 | GROUP_ECP384 |
| GCM_AES256 | GCM_AES256 | SHA256 | GROUP_ECP256 |
| AES256 | SHA384 | SHA384 | GROUP_24 |
| AES256 | SHA384 | SHA384 | GROUP_14 |
| AES256 | SHA384 | SHA384 | GROUP_ECP384 |
| AES256 | SHA384 | SHA384 | GROUP_ECP256 |
| AES256 | SHA256 | SHA256 | GROUP_24 |
| AES256 | SHA256 | SHA256 | GROUP_14 |
| AES256 | SHA256 | SHA256 | GROUP_ECP384 |
| AES256 | SHA256 | SHA256 | GROUP_ECP256 |
| AES256 | SHA256 | SHA256 | GROUP_2 |
IPsec
| Cipher | 完整性 | PFS 组 |
|---|---|---|
| GCM_AES256 | GCM_AES256 | GROUP_NONE |
| GCM_AES256 | GCM_AES256 | GROUP_24 |
| GCM_AES256 | GCM_AES256 | GROUP_14 |
| GCM_AES256 | GCM_AES256 | GROUP_ECP384 |
| GCM_AES256 | GCM_AES256 | GROUP_ECP256 |
| AES256 | SHA256 | GROUP_NONE |
| AES256 | SHA256 | GROUP_24 |
| AES256 | SHA256 | GROUP_14 |
| AES256 | SHA256 | GROUP_ECP384 |
| AES256 | SHA256 | GROUP_ECP256 |
| AES256 | SHA1 | GROUP_NONE |
在 P2S 的 VPN 网关上配置了哪些 TLS 策略?
TLS
| 策略 |
|---|
| TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256 |
| TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384 |
| TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 |
| TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 |
| TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256 |
| TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384 |
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256 |
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 |
| TLS_RSA_WITH_AES_128_GCM_SHA256 |
| TLS_RSA_WITH_AES_256_GCM_SHA384 |
| TLS_RSA_WITH_AES_128_CBC_SHA256 |
| TLS_RSA_WITH_AES_256_CBC_SHA256 |
如何配置 P2S 连接?
P2S 配置需要相当多的特定步骤。 以下文章包含指导你完成常见 P2S 配置步骤的步骤。
删除 P2S 连接的配置
可以使用 PowerShell 或 CLI 删除某个连接的配置。 有关示例,请参阅常见问题解答。
P2S 路由的工作原理是什么?
请参阅以下文章:
常见问题解答
关于 P2S,有多个基于身份验证的“常见问题解答”部分。
后续步骤
“OpenVPN”是 OpenVPN Inc. 的商标。