Azure 信息保护在保护数据方面的角色
Azure 信息保护 (AIP) 可为客户提供分类、标记数据并使用加密来保护数据的功能。 Azure 信息保护可让 IT 管理员:
- 根据预设规则自动对电子邮件和文档进行分类
- 向自定义页眉、页脚和水印等内容添加标记
- 使用权限管理保护公司的机密文件,以便:
- 将 RSA 2,048 位密钥用于公钥加密,并将 SHA-256 用于签名操作。
- 将文件加密到组织内外的特定收件人群
- 应用特定权限集以限制文件的可用性
- 根据权限策略中的用户标识和授权来解密内容
这些功能有助于企业更好地控制其数据。 在此背景下,Azure 信息保护在保护公司数据方面发挥着重要作用。
重要
有关 Azure 信息保护工作原理的详细信息,请阅读 Azure RMS 如何工作?(揭秘)。
企业保护现状
如今,很多企业均未部署任何保护技术,文档和电子邮件均以明文形式进行共享,且数据保管人不清楚有权访问特权内容的用户。 SMIME 等保护技术十分复杂,而 ACL 也未必会与电子邮件和文档同时存在。

在基本不受保护的环境中,Azure 信息保护可提供之前不可用的安全措施。 虽然安全是一个不断发展的主题,且无组织敢声称能随时提供 100% 保护,但正确部署 Azure 信息保护却可扩大组织的安全覆盖范围。
共享内容的安全原则
在组织中使用 Azure 信息保护时,IT 管理员可完全控制客户端设备和用户标识管理,从而为在组织内共享搭建起适当的信任平台。 在组织外部发送信息本就不太可信。 考虑信息保护方法时,存在某些必须执行风险评估的原则。 执行此风险评估时,请考虑以下几点:
- 接收人对非托管设备具有物理访问权限,因此可控制设备上出现的所有事项。
- 接收人会通过与非模拟相关的置信度进行身份验证。
在 IT 管理员无法控制设备或标识的情况下,IT 无法控制受保护信息会出现何种情况。 用户进行身份验证并打开受保护的信息后,信息便不再受你控制。 此时,你信任接收人会遵守为内容设置的策略。
无法彻底阻止对受保护内容具有授权访问权限的恶意外部收件人。 Azure 信息保护有助于设定道德界限,并利用启发式应用程序来帮助人们遵守合法的文档访问方式。 当根据标识所提供的访问既定界限内存在隐式信任时,Azure 信息保护可提供帮助。
但是,检测和缓解未来的访问则更简单。 Azure 信息保护服务的文档跟踪功能可跟踪访问权限,而组织则可通过撤消对特定文档的访问权限或撤消用户的访问权限来采取行动。
如果内容异常敏感且组织无法信任接收人,内容的额外安全性就变得至关重要。 建议转换思维以提升安全性,并对文档执行访问控制。
基于标识的安全性
以下部分将探讨针对受保护内容的三大攻击场景,以及如何组合使用环境控制和 Azure 信息保护来缓解针对内容的恶意访问。
未经授权用户发起的攻击
Azure 信息保护中保护的基础是:对受保护内容的访问均基于经身份验证的标识和授权。 因此,借助 Azure 信息保护,未经身份验证或授权则意味着没有访问权限。 这是部署 Azure 信息保护的主要原因,它可让企业从不受限制进行访问的状态变为基于用户身份验证与授权来访问信息的状态。
通过使用此 Azure 信息保护功能,企业可隔离信息。 例如:将人力资源 (HR) 部门的敏感信息在此部门内保持隔离,同时将财务部门的数据限制在该部门内。 Azure 信息保护提供基于标识的访问权限,而不是毫无限制的访问权限。
下图显示了将文档发送到 Tom 的用户 (Bob) 示例。 在本例中,Bob 来自财务部门,而 Tom 则来自销售部门。 如果未授予任何权限,Tom 则无法访问此文档。
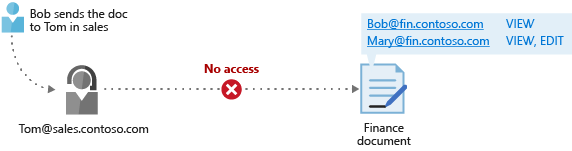
此场景中的关键点在于,Azure 信息保护可阻止未经授权用户发起的攻击。 有关 Azure 信息保护中加密控制功能的详细信息,请阅读 Azure RMS 使用的加密控制功能:算法和密钥长度。
代表用户通过恶意程序进行访问
代表用户进行访问的恶意程序通常是在该用户不知情的情况下发生的。 木马、病毒和其他恶意软件均为可代表用户来执行的恶意程序的经典示例。 如果此类程序可模拟用户的标识或利用用户的权限来执行操作,它则可使用 Azure 信息保护 SDK 并代表不知情用户对内容进行解密。 由于此操作出现于用户的上下文中,因此没有简易方法可防止此攻击。

此处的目的在于增强用户标识的安全性,从而有助于降低恶意应用程序劫持用户标识的能力。 Microsoft Entra ID 提供多个解决方案以帮助保护用户标识;例如,使用双重身份验证。 此外,还有一些包含在 Azure Activity Directory 标识保护中的其他功能会也应进行探索,从而确保用户标识的安全。
保护标识不在 Azure 信息保护的范围之内,且属于管理员的责任范畴。
重要
此外,还须关注“托管”环境以消除恶意程序的存在。 下一场景将对此进行介绍。
已获授权的恶意用户
恶意用户发起的访问其实属于信任受损。 此场景中的启用程序需为可提升用户权限的程序;因为与前一场景不同,此用户自愿提供凭据来破坏信任。

Azure 信息保护旨在确保应用程序位于负责强制实施与文档关联权限的客户端设备上。 通过所有措施,当前受保护内容安全性最薄弱的环节将置于客户端设备上,此时内容将以纯文本形式对最终用户可见。 Microsoft Office 等客户端应用程序会正确遵循这些权限,因此恶意用户无法使用这些应用程序来提升权限。 但通过使用 Azure 信息保护 SDK,蓄意攻击者可创建不遵循这些权限的应用程序,而这便是恶意程序的本质所在。
此场景着重保护客户端设备和应用程序,以便阻止使用恶意应用程序。 IT 管理员可采取的某些步骤如下所列:
- 使用 Windows AppLocker 帮助确保不需要的程序无法执行
- 使用 Intune 和 Microsoft Endpoint Configuration Manager 帮助确保设备“正常运行”
- 确保设备上的防病毒程序处于最新状态
- 将支持 Microsoft Identity Brokers 的应用程序用于身份验证和 SSO
此场景的重点在于:保护客户端计算机和应用程序是用于支撑 Azure 信息保护的信任的重要组成部分。
由于 Azure 信息保护并非旨在防止授予内容访问权限的用户的恶意滥用,因此无法预期 Azure 信息保护能防止内容免受上述用户的恶意修改。 尽管要对内容进行任何形式的修改,事实上首先均需向用户授予对受保护数据的访问权限,而与文档关联的策略和权限本身已正确进行签名且易发现是否已被篡改,但一旦用户被授予所需加密/解密密钥的访问权限,此用户其实便可解密该数据、对其进行修改并重新加密。 无论是在 Microsoft 产品中(例如,Office 文档签名支持、Outlook 中的 s/MIME 支持)还是来自第三方,均可实施众多解决方案以向 Office 文档提供文档签名、作者身份证明、防篡改和不可否认性功能。 不应仅依赖 AIP 的保护功能来防范授权用户的恶意修改。
总结
一种技术无法确保彻底的安全性。 通过各种相互依赖的手段,IT 管理员可缩小现实情况下受保护内容的攻击面。
- Azure 信息保护:防止未经授权访问内容
- Microsoft Intune、Microsoft Endpoint Configuration Manager 和其他设备管理产品:使托管和受控环境免受恶意应用的影响
- Windows AppLocker:使托管和受控环境免受恶意应用的影响
- Microsoft Entra 标识保护:增强用户标识的信任度
- EMS 条件访问:增强设备和标识的信任度