无用户访问
若要调用 Microsoft Graph,应用必须从Microsoft 标识平台获取访问令牌。 此访问令牌包括有关应用是有权代表已登录用户访问 Microsoft Graph 还是使用其自己的标识的信息。 本文提供有关应用如何 通过自己的标识(也称为 仅限应用访问)访问 Microsoft Graph 的指南。
本文详细介绍了应用使用名为 OAuth 2.0 客户端凭据授予流的常用流来调用其自己的标识的 Microsoft Graph 所涉及的原始 HTTP 请求。 或者,可以避免编写原始 HTTP 请求,并使用 Microsoft 构建或支持的身份验证库来处理其中许多详细信息,并帮助你获取访问令牌和调用 Microsoft Graph。 有关详细信息,请参阅 使用 Microsoft 身份验证库 (MSAL) 。
先决条件
在继续执行本文中的步骤之前:
- 了解Microsoft 标识平台中的身份验证和授权概念。 有关详细信息,请参阅 身份验证和授权基础知识。
- 向 Microsoft Entra ID 注册应用。 有关详细信息,请参阅使用 Microsoft 标识平台注册应用程序。
身份验证和授权步骤
若要使应用使用客户端凭据流获取对 Microsoft Graph 的授权和访问权限,必须执行以下五个步骤:
- 向 Microsoft Entra ID 注册应用。
- 对应用配置 Microsoft Graph 应用程序权限。
- 请求管理员同意。
- 请求访问令牌。
- 使用访问令牌调用 Microsoft Graph。
1.注册应用
在应用可以使用 Microsoft 标识平台 终结点或调用 Microsoft Graph 之前,它必须正确注册。 按照步骤在Microsoft Entra 管理中心注册应用。
在应用注册中,保存以下值:
- 应用程序 ID (应用注册门户分配的Microsoft Entra 管理中心) 上称为“对象 ID”。
- 客户端密码 (应用程序密码) 、证书或联合标识凭据。
- 应用的重定向 URI,用于接收来自Microsoft Entra ID的令牌响应。
- 如果应用实现请求管理员同意的功能,则服务的重定向 URI,用于接收管理员同意响应。
2.配置 Microsoft Graph 的权限
Microsoft Graph 公开以自己的标识调用 Microsoft Graph 的应用 的应用程序权限 。 这些权限始终需要管理员同意。
注册应用时,预配置应用所需的应用程序权限。 管理员可以在组织中安装应用时使用Microsoft Entra 管理中心同意这些权限,也可以在应用中提供注册体验,管理员可以通过该体验同意你配置的权限。 Microsoft Entra ID记录管理员同意后,应用可以请求令牌,而无需再次请求同意。
若要在 Azure 应用注册门户中配置应用的应用程序权限,请执行以下步骤:
- 在应用程序的 “API 权限 ”页下,选择“ 添加权限”。
- 选择 Microsoft Graph。
- 选择“应用程序权限”。
- 在 “选择权限 ”对话框中,选择要配置应用的权限。
下面的屏幕快照显示了 Microsoft Graph 应用程序权限的“选择权限”对话框。
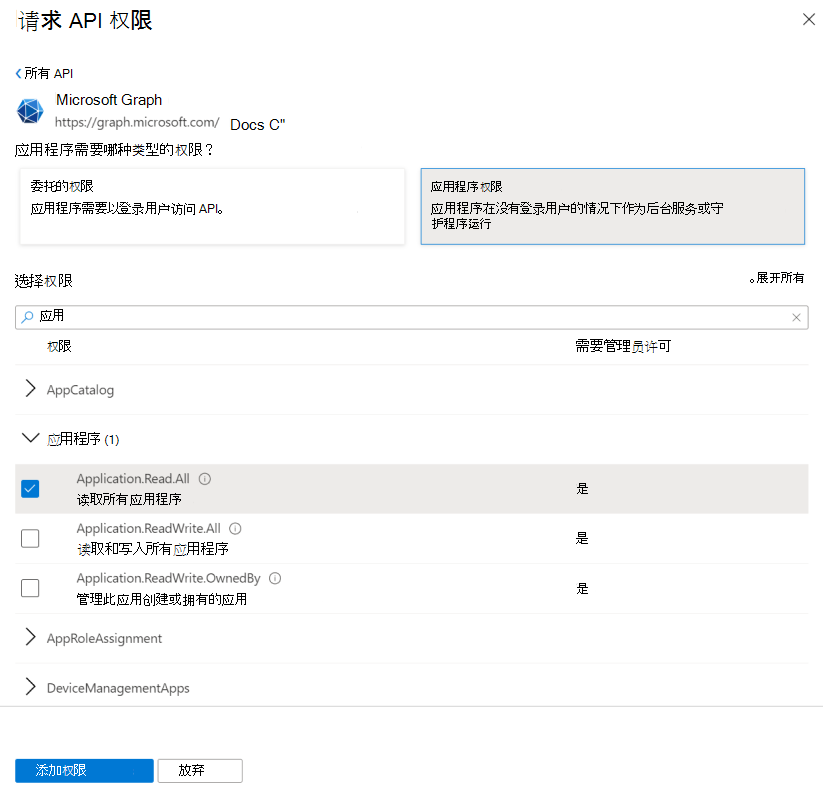
重要
始终配置应用所需的最低特权权限集。 有关详细信息,请参阅 使用 Microsoft Graph 权限的最佳做法。
3.请求管理员同意
管理员可以在Microsoft Entra 管理中心授予应用所需的权限。 但是,如果无权访问Microsoft Entra 管理中心,可以使用 Microsoft 标识平台 /adminconsent 终结点为管理员提供注册体验。
重要
更改已配置的权限时,还必须重复执行该管理员同意过程。 在授权管理员(例如全局管理员)重新访问应用之前,不会反映应用注册门户中所做的更改。
请求
// Line breaks are for legibility only.
GET https://login.microsoftonline.com/{tenant}/adminconsent
?client_id=6731de76-14a6-49ae-97bc-6eba6914391e
&state=12345
&redirect_uri=https://localhost/myapp/permissions HTTP/1.1
| 参数 | 条件 | 说明 |
|---|---|---|
| 租户 | 必需 | 要从中请求权限的目录租户。 该值可以是 GUID 或友好名称格式。 如果不知道用户属于哪个租户,并且想要让他们使用任何租户登录,请使用 common。 |
| client_id | 必需 | Azure 应用注册门户 分配给你的应用的应用程序 ID。 |
| redirect_uri | 必需 | 要在其中发送响应供应用处理的重定向 URI。 它必须与在门户中注册的重定向 URI 之一匹配。 它必须经过 URL 编码,并且可以具有其他路径段。 |
| state | 建议 | 一个值,该值包含在请求中,也会在令牌响应中返回。 它可以是所需的任何内容的字符串。 状态用于在身份验证请求发生前对应用中有关用户状态的信息进行编码,例如用户所访问的页面或视图。 |
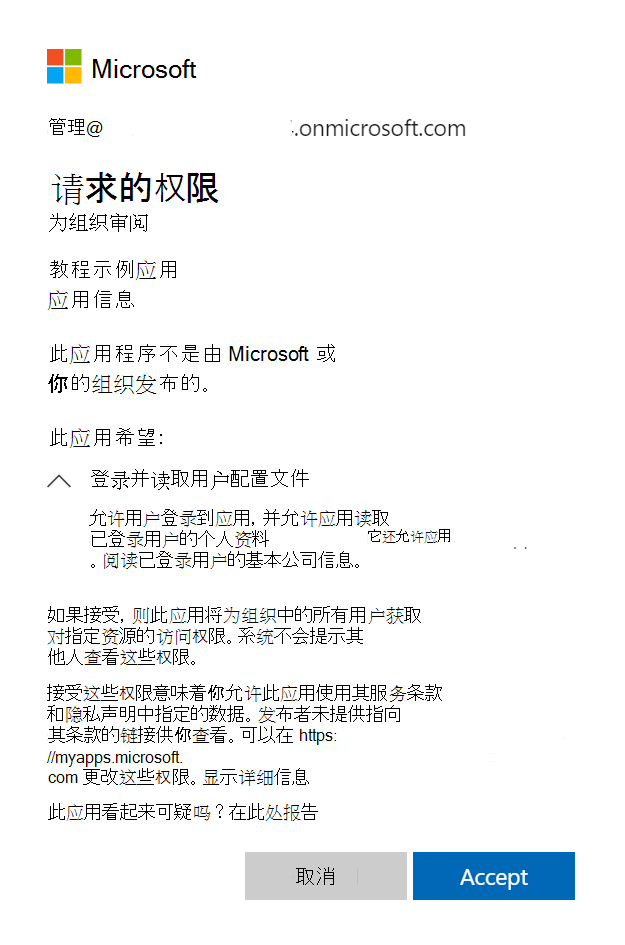
管理员同意体验
对于对/adminconsent终结点的请求,Microsoft Entra ID强制只有授权管理员才能登录以完成请求。 系统会要求管理员批准你在应用注册门户中为应用请求的所有应用程序权限。
以下屏幕截图是Microsoft Entra ID向管理员显示的同意对话框的示例:
响应
如果管理员批准应用程序的权限,则成功响应如下所示:
// Line breaks are for legibility only.
https://localhost/myapp/permissions?admin_consent=True&tenant=38d49456-54d4-455d-a8d6-c383c71e0a6d&state=12345#
| 参数 | 说明 |
|---|---|
| 租户 | 以 GUID 格式向应用程序授予其请求的权限的目录租户。 |
| state | 一个值,该值包含在请求中,也会在令牌响应中返回。 它可以是所需的任何内容的字符串。 状态用于在身份验证请求发生前对应用中有关用户状态的信息进行编码,例如用户所访问的页面或视图。 |
| admin_consent | 设置为 True。 |
4.请求访问令牌
在 OAuth 2.0 客户端凭据授予流中,可使用在注册应用时保存的应用程序 ID 和客户端密码值直接从 Microsoft 标识平台 /token 终结点请求访问令牌。
通过将 作为令牌请求中的 参数的值scope传递https://graph.microsoft.com/.default来指定预配置的权限。
令牌请求
向标识平台终结点发送 POST 请求 /token 以获取访问令牌。 在此请求中,客户端使用客户端密码。
// Line breaks are for legibility only.
POST https://login.microsoftonline.com/{tenant}/oauth2/v2.0/token HTTP/1.1
Host: login.microsoftonline.com
Content-Type: application/x-www-form-urlencoded
client_id=535fb089-9ff3-47b6-9bfb-4f1264799865
&scope=https%3A%2F%2Fgraph.microsoft.com%2F.default
&client_secret=qWgdYAmab0YSkuL1qKv5bPX
&grant_type=client_credentials
| 参数 | 条件 | 说明 |
|---|---|---|
| 租户 | 必需 | 要从中请求权限的目录租户。 该值可以是 GUID 或友好名称格式。 |
| client_id | 必需 | 注册应用时由 Azure 应用注册门户 分配的应用程序 ID。 |
| 范围 | 必需 | 为此请求中的 scope 参数传递的值应为所需资源的标识符(应用程序 ID URI),带有 .default 后缀。 例如,Microsoft Graph 资源应用 ID URI 为 https://graph.microsoft.com/。 因此,对于 Microsoft Graph,scope 的值为 https://graph.microsoft.com/.default。 此值通知 Microsoft 标识平台终结点将管理员同意的所有应用级别权限包含在访问令牌中。 |
| client_secret | 必需 | 在应用注册门户中为应用生成的客户端密码。 确保已对它进行 URL 编码。 |
| grant_type | 必需 | 必须是 client_credentials。 |
令牌响应
成功的响应如下所示:
{
"token_type": "Bearer",
"expires_in": 3599,
"ext_expires_in":3599,
"access_token": "eyJ0eXAiOiJKV1QiLCJhbGciOiJSUzI1NiIsIng1dCI6Ik1uQ19WWmNBVGZNNXBP..."
}
| 参数 | 说明 |
|---|---|
| access_token | 请求的访问令牌。 你的应用可以在调用 Microsoft Graph 时使用此令牌。 |
| expires_in | 访问令牌的有效期是多久(以秒为单位)。 |
| ext_expires_in | 用于指示访问令牌的延长生存期,并在令牌颁发服务未响应时支持复原能力。 |
| token_type | 指示令牌类型值。 Microsoft Entra ID支持的唯一类型是 Bearer。 |
5.使用访问令牌调用 Microsoft Graph
拥有访问令牌后,应用会使用它调用 Microsoft Graph,方法是将访问令牌作为 持有者 令牌附加到 HTTP 请求中的 Authorization 标头。 以下请求获取租户中的所有用户。 应用必须具有 User.Read.All 权限才能调用此 API。
GET https://graph.microsoft.com/v1.0/users HTTP/1.1
Authorization: Bearer eyJ0eXAiO ... 0X2tnSQLEANnSPHY0gKcgw
Host: graph.microsoft.com
成功的响应如下所示, () 删除了一些响应标头:
HTTP/1.1 200 OK
Content-Type: application/json;odata.metadata=minimal;odata.streaming=true;IEEE754Compatible=false;charset=utf-8
request-id: f45d08c0-6901-473a-90f5-7867287de97f
client-request-id: f45d08c0-6901-473a-90f5-7867287de97f
OData-Version: 4.0
Date: Wed, 26 Apr 2017 19:53:49 GMT
Content-Length: 407
{
"@odata.context": "https://graph.microsoft.com/v1.0/$metadata#users",
"value": [
{
"businessPhones": [],
"displayName": "Conf Room Adams",
"givenName": null,
"jobTitle": null,
"mail": "Adams@Contoso.com",
"mobilePhone": null,
"officeLocation": null,
"preferredLanguage": null,
"surname": null,
"userPrincipalName": "Adams@Contoso.com",
"id": "8afc02cb-4d62-4dba-b536-9f6d73e9be26"
},
{
"businessPhones": [
"+1 425 555 0109"
],
"displayName": "Adele Vance",
"givenName": "Adele",
"jobTitle": "Retail Manager",
"mail": "AdeleV@Contoso.com",
"mobilePhone": null,
"officeLocation": "18/2111",
"preferredLanguage": null,
"surname": "Vance",
"userPrincipalName": "AdeleV@Contoso.com",
"id": "59bb3898-0621-4414-ac61-74f9d7201355"
}
]
}
受支持的应用场景和资源
以它们自己的标识调用 Microsoft Graph 的应用可分为两个类别:
- 在服务器上运行的没有登录用户的后台服务(守护程序)。
- 具有已登录用户,但也使用自己的标识调用 Microsoft Graph 的应用。 例如,使用需要比用户拥有的更高权限的功能。
在本文中,应用使用客户端密码作为凭据。 可以选择配置证书或联合标识凭据。
有关以自己的标识调用 Microsoft Graph 并使用客户端凭据流的应用的详细信息,请参阅 身份验证流和应用程序方案:守护程序名称中调用 Web API 的守护程序应用。
使用 Microsoft 身份验证库 (MSAL)
在本文中,你演练了通常仅在手动创建和发出原始 HTTP 请求以执行客户端凭据流时所需的低级别协议详细信息。 在生产应用中,使用 Microsoft 生成或支持的身份验证库(例如 Microsoft 身份验证库 (MSAL) )获取安全令牌并调用受保护的 Web API(如 Microsoft Graph)。
MSAL 和其他受支持的身份验证库通过处理验证、Cookie 处理、令牌缓存和安全连接等详细信息简化了此过程,使你能够专注于应用程序的功能。
Microsoft 生成并维护了各种代码示例,这些示例演示了Microsoft 标识平台支持的身份验证库的用法。 若要访问这些代码示例,请参阅Microsoft 标识平台代码示例。
相关内容
- 从 Microsoft 生成和维护的代码示例中进行选择,以运行使用支持的身份验证库、登录用户和调用 Microsoft Graph 的自定义应用。 请参阅 Microsoft Graph 教程。
反馈
即将发布:在整个 2024 年,我们将逐步淘汰作为内容反馈机制的“GitHub 问题”,并将其取代为新的反馈系统。 有关详细信息,请参阅:https://aka.ms/ContentUserFeedback。
提交和查看相关反馈