使用 API 将 SCEP 的第三方 CA 添加到 Intune
在 Microsoft Intune 中,可以添加第三方证书颁发机构 (CA) ,并使用简单证书注册协议 (SCEP) 颁发和验证证书。 添加第三方证书颁发机构 概述了此功能,并介绍了 Intune 中的管理员任务。
还有一些开发人员任务使用 Microsoft 在 GitHub.com 中发布的开源库。 库包含一个 API,该 API:
- 验证 Intune 动态生成的 SCEP 密码
- 通知 Intune 在提交 SCEP 请求的设备上创建的证书
使用此 API,第三方 SCEP 服务器与适用于 MDM 设备的 Intune SCEP 管理解决方案集成。 库从用户提取身份验证、服务位置和 ODATA Intune 服务 API 等方面。
SCEP 管理解决方案
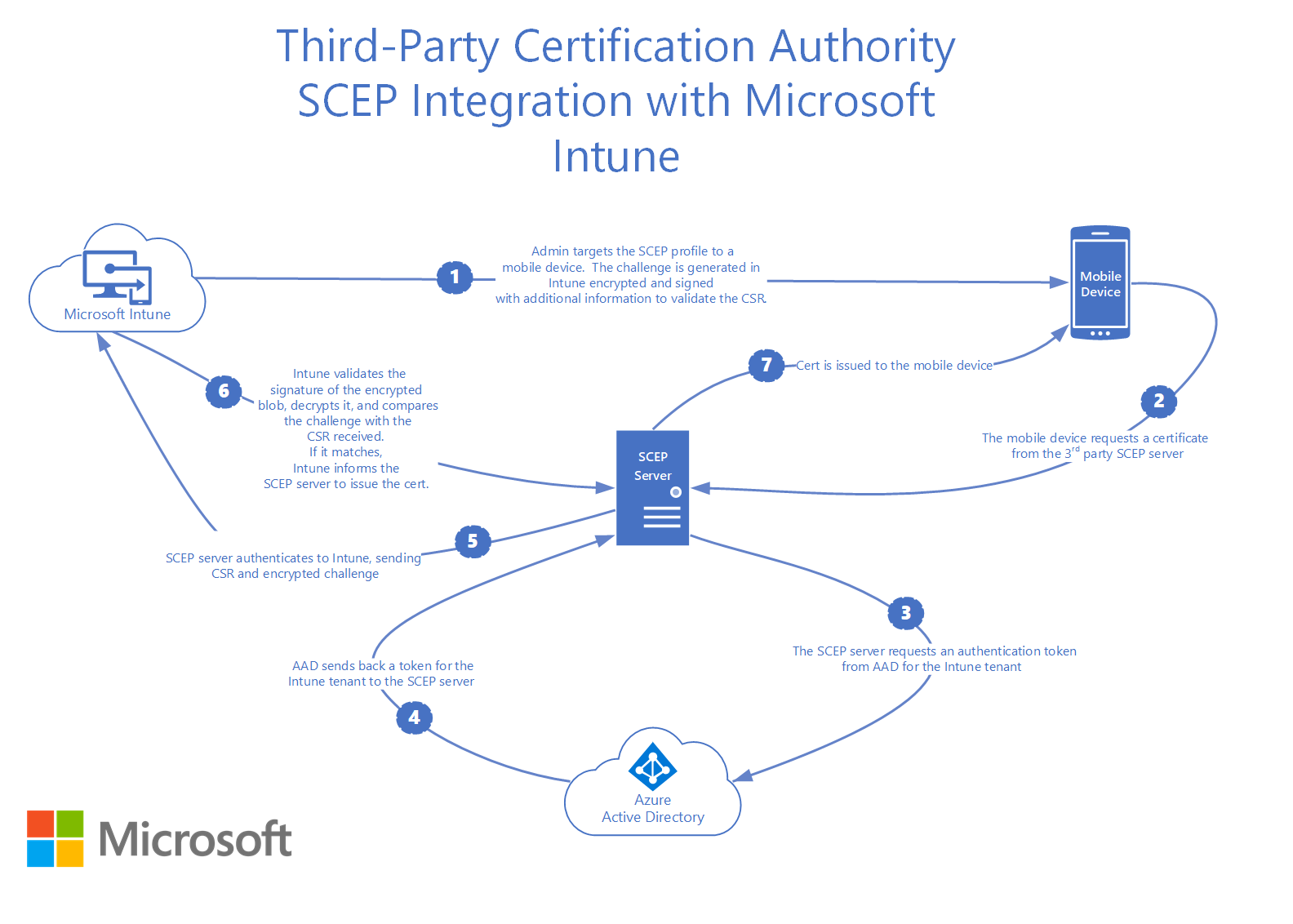
使用 Intune,管理员创建 SCEP 配置文件,然后将这些配置文件分配给 MDM 设备。 SCEP 配置文件包括参数,例如:
- SCEP 服务器的 URL
- 证书颁发机构的受信任的根证书
- 证书属性等
使用 Intune 检查的设备将分配 SCEP 配置文件,并使用这些参数进行配置。 动态生成的 SCEP 质询密码由 Intune 创建,然后分配给设备。
此挑战包含:
- 动态生成的质询密码
- 有关证书签名请求中预期参数的详细信息, (CSR) 设备颁发给 SCEP 服务器
- 质询到期时间
Intune 会加密此信息,对加密的 Blob 进行签名,然后将这些详细信息打包到 SCEP 质询密码中。
联系 SCEP 服务器以请求证书的设备,然后提供此 SCEP 质询密码。 SCEP 服务器将 CSR 和加密的 SCEP 质询密码发送到 Intune 进行验证。 此质询密码和 CSR 必须通过 SCEP 服务器的验证才能向设备颁发证书。 验证 SCEP 质询后,将进行以下检查:
- 验证加密 Blob 的签名
- 验证质询是否未过期
- 验证配置文件是否仍面向设备
- 验证 CSR 中设备请求的证书属性是否与预期值匹配
SCEP 管理解决方案还包括报告。 管理员可以获取有关 SCEP 配置文件的部署状态以及颁发给设备的证书的信息。
与 Intune 集成
要与 Intune SCEP 集成的库的代码可在 Microsoft/Intune-Resource-Access GitHub 存储库中下载。
将库集成到产品中包括以下步骤。 这些步骤需要了解如何使用 GitHub 存储库,以及如何在 Visual Studio 中创建解决方案和项目。
注册以接收来自存储库的通知
克隆或下载存储库
转到文件夹 () https://github.com/Microsoft/Intune-Resource-Access/tree/develop/src/CsrValidation 下
\src\CsrValidation所需的库实现使用自述文件中的说明生成库
在生成 SCEP 服务器的项目中包括库
在 SCEP 服务器上完成以下任务:
- 允许管理员配置本文中的Azure 应用程序标识符、Azure 应用程序密钥和租户 ID () 库用于身份验证。 应允许管理员更新Azure 应用程序密钥。
- 识别包含 Intune 生成的 SCEP 密码的 SCEP 请求
- 使用 验证请求 API 库验证 Intune 生成的 SCEP 密码
- 使用库通知 API 将针对具有 Intune 生成的 SCEP 密码的 SCEP 请求颁发的证书通知 Intune。 还要通知 Intune 处理这些 SCEP 请求时可能发生的错误。
- 确认服务器记录的信息足以帮助管理员排查问题
完成本文中的 集成测试 () ,并解决任何问题
向客户提供书面指导,说明:
- SCEP 服务器需要如何载入Microsoft Intune管理中心
- 如何获取配置库所需的Azure 应用程序标识符和Azure 应用程序密钥
在 Azure 中加入 SCEP 服务器
若要向 Intune 进行身份验证,SCEP 服务器需要Azure 应用程序 ID、Azure 应用程序密钥和租户 ID。 SCEP 服务器还需要经过授权才能访问 Intune API。
为了获取此数据,SCEP 服务器管理员登录到Azure 门户,注册应用程序,为应用程序授予Microsoft Intune API\SCEP 质询验证权限和 Application.Read.All 权限,为应用程序创建密钥,然后下载应用程序 ID、其密钥和租户 ID。
有关注册应用程序以及获取 ID 和密钥的指南,请参阅使用门户创建用于访问资源的Microsoft Entra应用程序和服务主体。
Java 库 API
Java 库实现为 Maven 项目,该项目在生成时拉取其依赖项。 API 由 IntuneScepServiceClient 类在 com.microsoft.intune.scepvalidation 命名空间下实现。
IntuneScepServiceClient 类
类 IntuneScepServiceClient 包括 SCEP 服务用于验证 SCEP 密码、通知 Intune 已创建的证书以及列出任何错误的方法。
IntuneScepServiceClient 构造函数
签名:
IntuneScepServiceClient(
Properties configProperties)
说明:
实例化和配置 IntuneScepServiceClient 对象。
参数:
- configProperties - 包含客户端配置信息的属性对象
配置必须包含以下属性:
- AAD_APP_ID=“在载入过程中获取的Azure 应用程序 ID”
- AAD_APP_KEY=“在载入过程中获取的Azure 应用程序密钥”
- TENANT=“在载入过程中获取的租户 ID”
- PROVIDER_NAME_AND_VERSION=“用于标识产品及其版本的信息”
如果解决方案需要具有身份验证或不使用身份验证的代理,则可以添加以下属性:
- PROXY_HOST=“代理托管的主机”。
- PROXY_PORT=“代理正在侦听的端口。”
- PROXY_USER=“代理使用基本身份验证时要使用的用户名。
- PROXY_PASS=“代理使用基本身份验证时要使用的密码。
引发:
- IllegalArgumentException - 如果执行构造函数时没有适当的属性对象,则引发。
重要
最好实例化此类的实例,并使用它来处理多个 SCEP 请求。 这样做可以减少开销,因为它会缓存身份验证令牌和服务位置信息。
安全说明
SCEP 服务器实现者必须保护保存在存储的配置属性中输入的数据,防止篡改和泄露。 建议使用适当的 ACL 和加密来保护信息。
ValidateRequest 方法
签名:
void ValidateRequest(
String transactionId,
String certificateRequest)
说明:
验证 SCEP 证书请求。
参数:
- transactionId - SCEP 事务 ID
- certificateRequest - DER 编码 PKCS #10 证书请求 Base64 编码为字符串
引发:
- IllegalArgumentException - 如果使用无效的参数调用,则引发
- IntuneScepServiceException - 如果发现证书请求无效,则引发
- 异常 - 如果遇到意外错误,则引发
重要
服务器应记录此方法引发的异常。 请注意,这些 IntuneScepServiceException 属性包含有关证书请求验证失败原因的详细信息。
安全说明:
- 如果此方法引发异常,则 SCEP 服务器 不得 向客户端颁发证书。
- SCEP 证书请求验证失败可能表示 Intune 基础结构中存在问题。 或者,它们可能表明攻击者正在尝试获取证书。
SendSuccessNotification 方法
签名:
void SendSuccessNotification(
String transactionId,
String certificateRequest,
String certThumbprint,
String certSerialNumber,
String certExpirationDate,
String certIssuingAuthority)
说明:
通知 Intune 证书是在处理 SCEP 请求过程中创建的。
参数:
- transactionId - SCEP 事务 ID
- certificateRequest - DER 编码 PKCS #10 证书请求 Base64 编码为字符串
- certThumprint - 已预配证书指纹的 SHA1 哈希
- certSerialNumber - 预配证书的序列号
- certExpirationDate - 预配证书的到期日期。 日期时间字符串的格式应设置为 Web UTC 时间 (YYYY-MM-DDThh:mm:ss.sssTZD) ISO 8601。
- certIssuingAuthority - 颁发证书的颁发机构的名称
引发:
- IllegalArgumentException - 如果使用无效的参数调用,则引发
- IntuneScepServiceException - 如果发现证书请求无效,则引发
- 异常 - 如果遇到意外错误,则引发
重要
服务器应记录此方法引发的异常。 请注意,这些 IntuneScepServiceException 属性包含有关证书请求验证失败原因的详细信息。
安全说明:
- 如果此方法引发异常,则 SCEP 服务器 不得 向客户端颁发证书。
- SCEP 证书请求验证失败可能表示 Intune 基础结构中存在问题。 或者,它们可能表明攻击者正在尝试获取证书。
SendFailureNotification 方法
签名:
void SendFailureNotification(
String transactionId,
String certificateRequest,
long hResult,
String errorDescription)
说明:
通知 Intune 处理 SCEP 请求时出错。 对于此类的方法引发的异常,不应调用此方法。
参数:
- transactionId - SCEP 事务 ID
- certificateRequest - DER 编码 PKCS #10 证书请求 Base64 编码为字符串
- hResult - 最能描述所遇到的错误的 Win32 错误代码。 请参阅 Win32 错误代码
- errorDescription - 所遇到的错误的说明
引发:
- IllegalArgumentException - 如果使用无效的参数调用,则引发
- IntuneScepServiceException - 如果发现证书请求无效,则引发
- 异常 - 如果遇到意外错误,则引发
重要
服务器应记录此方法引发的异常。 请注意,这些 IntuneScepServiceException 属性包含有关证书请求验证失败原因的详细信息。
安全说明:
- 如果此方法引发异常,则 SCEP 服务器 不得 向客户端颁发证书。
- SCEP 证书请求验证失败可能表示 Intune 基础结构中存在问题。 或者,它们可能表明攻击者正在尝试获取证书。
SetSslSocketFactory 方法
签名:
void SetSslSocketFactory(
SSLSocketFactory factory)
说明:
使用此方法通知客户端,在与 Intune 通信时,它必须使用指定的 SSL 套接字工厂 (而不是默认) 。
参数:
- 工厂 - 客户端应用于 HTTPS 请求的 SSL 套接字工厂
引发:
- IllegalArgumentException - 如果使用无效的参数调用,则引发
注意
如果需要,必须在执行此类的其他方法之前设置 SSL 套接字工厂。
集成测试
必须验证和测试解决方案是否与 Intune 正确集成。 下面列出了这些步骤的概述:
- 设置 Intune 试用帐户。
- 在本文) 的 Azure 门户 (中载入 SCEP 服务器。
- 使用加入 SCEP 服务器 时创建的 ID 和密钥配置 SCEP 服务器。
- 注册设备 以在方案测试矩阵中 测试方案。
- 为测试证书颁发机构创建受信任的根证书配置文件。
- 创建 SCEP 配置文件以测试 方案测试矩阵中列出的方案。
- 将配置文件分配给 注册其设备的用户。
- 等待设备与 Intune 同步。 或者,手动 同步设备。
- 确认受信任的根证书和 SCEP 配置文件已部署到设备。
- 确认所有设备上都安装了受信任的根证书。
- 确认已分配的配置文件的 SCEP 证书已安装在所有设备上。
- 确认已安装证书的属性与 SCEP 配置文件中设置的属性匹配。
- 确认已颁发证书在 Intune 管理中心中正确列出
另请参阅
- 添加第三方 CA 概述
- 设置 Intune
- 设备注册
- 配置 SCEP 证书配置文件 (Microsoft NDES Server\Connector 安装程序不用于此方案)
反馈
即将发布:在整个 2024 年,我们将逐步淘汰作为内容反馈机制的“GitHub 问题”,并将其取代为新的反馈系统。 有关详细信息,请参阅:https://aka.ms/ContentUserFeedback。
提交和查看相关反馈