什么是 Microsoft Defender 漏洞管理
降低网络风险需要全面的基于风险的漏洞管理,以识别、评估、修正和跟踪最关键资产中的所有最大漏洞,所有这些漏洞都是在单个解决方案中实现的。
Defender 漏洞管理为 Windows、macOS、Linux、Android、iOS 和网络设备提供资产可见性、智能评估和内置修正工具。 Defender 漏洞管理使用 Microsoft 威胁情报、漏洞可能性预测、业务上下文和设备评估,快速并持续地确定最关键资产上最大的漏洞的优先级,并提供安全建议来降低风险。
观看以下视频,详细了解 Defender 漏洞管理。
提示
你知道可以免费试用Microsoft Defender 漏洞管理中的所有功能吗? 了解如何 注册免费试用版。
有关每个产品/服务中包含的特性和功能的详细信息,请参阅比较Microsoft Defender 漏洞管理产品/服务。
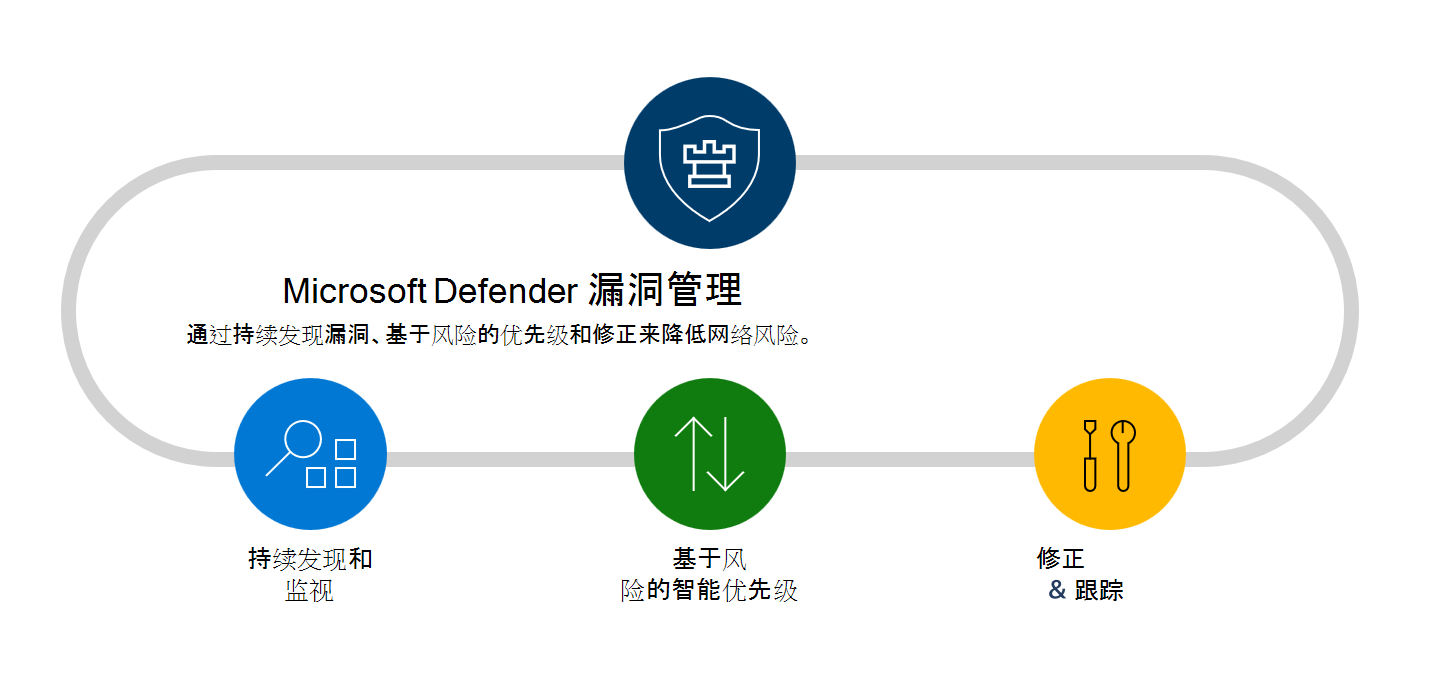
借助 Defender 漏洞管理,你可以为安全和 IT 团队提供支持,以弥合工作流差距,确定组织内的关键漏洞和配置优先级并解决这些漏洞和错误配置问题。 通过:
连续资产发现和监视
即使设备未连接到公司网络,Defender 漏洞管理内置和无代理扫描程序也会持续监视和检测组织中的风险。
合并清单提供组织的软件应用程序、数字证书、硬件和固件以及浏览器扩展的实时视图,以帮助你监视和评估组织的所有资产。
高级漏洞和配置评估工具可帮助你了解和评估网络风险,包括:
- 安全基线评估 - Create可自定义的基线配置文件,以根据既定基准来衡量风险符合性,例如,Internet 安全中心 (CIS) 和安全技术实施指南 (STIG) 。
- 了解软件和漏洞 - 查看组织的软件清单以及安装、卸载和修补程序等软件更改。
- 网络共享评估 - 使用可操作的安全建议评估易受攻击的内部网络共享配置。
- Windows 的身份验证扫描 - 通过提供Microsoft Defender 漏洞管理凭据来远程访问设备,定期扫描非托管 Windows 设备是否存在软件漏洞。
- 威胁分析 & 事件时间线 - 使用事件时间线和实体级漏洞评估来了解漏洞并确定其优先级。
- 浏览器扩展评估 - 查看在组织中不同浏览器上安装的浏览器扩展的列表。 查看有关扩展权限和相关风险级别的信息。
- 数字证书评估 - 在单个中央证书清单页中查看整个组织中安装的证书列表。 在证书过期之前识别证书,并检测由于签名算法薄弱而导致的潜在漏洞。
- 硬件和固件评估 - 查看组织中按系统型号、处理器和 BIOS 组织的已知硬件和固件列表。 每个视图都包含详细信息,例如供应商名称、弱点数、威胁见解以及公开的设备数。
基于风险的智能优先级
Defender 漏洞管理使用 Microsoft 的威胁情报、泄露可能性预测、业务上下文和设备评估来快速确定组织中最大的漏洞的优先级。 来自多个安全源的优先建议的单一视图,以及关键详细信息(包括相关 CVE 和公开的设备),可帮助你快速修正最关键资产上最大的漏洞。 基于风险的智能优先级:
- 专注于新出现的威胁 - 动态调整安全建议的优先级,以及当前在野生环境中利用的漏洞,以及构成最高风险的新威胁。
- 查明活动漏洞 - 关联漏洞管理和 EDR 见解,以确定在组织内活动违规中被利用的漏洞的优先级。
- 保护高价值资产 - 使用业务关键型应用程序、机密数据或高价值用户识别公开的设备。
修正和跟踪
使安全管理员和 IT 管理员能够协作并无缝地修正内置工作流的问题。
- 发送到 IT 的修正请求 - Create特定安全建议Microsoft Intune中的修正任务。
- 阻止易受攻击的应用程序 - 通过阻止特定设备组的易受攻击应用程序来缓解风险。
- 备用缓解措施 - 深入了解其他缓解措施,例如可以降低与软件漏洞相关的风险的配置更改。
- 实时修正状态 - 实时监视整个组织中的修正活动的状态和进度。
导航窗格
| 领域 | 说明 |
|---|---|
| 仪表板 | 获取组织暴露分数、威胁感知、适用于设备的 Microsoft 安全功能分数、即将到期的证书、设备暴露分发、最高安全建议、最易受攻击的软件、热门修正活动和公开最多的设备数据的高级视图。 |
| 建议 | 请参阅安全建议和相关威胁信息的列表。 从列表中选择项时,将打开浮出控件面板,其中包含漏洞详细信息、用于打开软件页面的链接以及修正和异常选项。 如果设备通过Microsoft Entra ID加入,并且已在 Defender for Endpoint 中启用Intune连接,则还可以在 Intune 中开具票证。 |
| 修复 | 请参阅已创建的修正活动和建议异常。 |
| 库存 | 在单个视图中发现和评估组织的所有资产。 |
| 弱点 | 请参阅组织中常见漏洞和风险 (CES) 列表。 |
| 活动日程表 | 查看可能影响组织风险的事件。 |
| 基线评估 | 监视安全基线符合性并实时识别更改。 |
API
运行与漏洞管理相关的 API 调用,以自动执行漏洞管理工作流。 若要开始,请参阅支持的Microsoft Defender for Endpoint API。
有关相关 Defender for Endpoint API,请参阅以下文章:
后续步骤
另请参阅
反馈
即将发布:在整个 2024 年,我们将逐步淘汰作为内容反馈机制的“GitHub 问题”,并将其取代为新的反馈系统。 有关详细信息,请参阅:https://aka.ms/ContentUserFeedback。
提交和查看相关反馈