在设备上执行响应操作
适用于:
重要
本文中的某些信息与预发行的产品有关,该产品在商业发布之前可能有重大修改。 Microsoft 对此处所提供的信息不作任何明示或默示的保证。
通过隔离设备或收集调查包来快速响应检测到的攻击。 对设备执行操作后,可以在操作中心检查活动详细信息。
响应操作沿着特定设备页的顶部运行,包括:
- 管理标签
- 启动自动调查
- 启动实时响应会话
- 收集调查程序包
- 运行防病毒扫描
- 限制应用执行
- 隔离设备
- 包含设备
- 咨询威胁专家
- 操作中心
重要
Defender for Endpoint 计划 1 仅包括以下手动响应操作:
- 运行防病毒扫描
- 隔离设备
- 停止和隔离文件
- 添加指示器以阻止或允许文件。
Microsoft Defender 商业版目前不包括“停止并隔离文件”操作。
订阅必须包含 Defender for Endpoint 计划 2,才能包含本文中所述的所有响应操作。
可以从以下任一视图中查找设备页:
- 警报队列 - 从警报队列中选择设备图标旁边的设备名称。
- 设备列表 - 从设备列表中选择设备名称的标题。
- 搜索框 - 从下拉菜单中选择设备,然后输入设备名称。
重要
有关每个响应操作的可用性和支持的信息,请参阅每个功能下支持的/最低操作系统要求。
管理标签
添加或管理标记以创建逻辑组附属关系。 设备标记支持网络适当映射,可附加不同的标记以捕获上下文,并启用在事件过程中创建动态列表。
有关设备标记的详细信息,请参阅Create和管理设备标记。
启动自动调查
如果需要,可以在设备上启动新的常规用途自动调查。 调查正在运行时,从设备生成的任何其他警报都将添加到正在进行的自动调查中,直到该调查完成。 此外,如果在其他设备上看到相同的威胁,则会将这些设备添加到调查中。
有关自动调查的详细信息,请参阅 自动调查概述。
启动实时响应会话
实时响应是一项功能,可让你使用远程 shell 连接即时访问设备。 这使你能够进行深入的调查工作,并立即采取响应操作,以及时实时遏制已识别的威胁。
实时响应旨在通过收集取证数据、运行脚本、发送可疑实体进行分析、修正威胁以及主动搜寻新出现的威胁来增强调查。
有关实时响应的详细信息,请参阅 使用实时响应调查设备上的实体。
从设备收集调查包
作为调查或响应过程的一部分,可以从设备收集调查包。 通过收集调查包,可以识别设备的当前状态,并进一步了解攻击者使用的工具和技术。
若要下载包 (Zip 文件) 并调查设备上发生的事件,请执行以下操作:
从设备页面顶部的响应操作行中选择“ 收集调查包 ”。
在文本框中指定要执行此操作的原因。 选择“确认”。
zip 文件下载。
备用步骤:
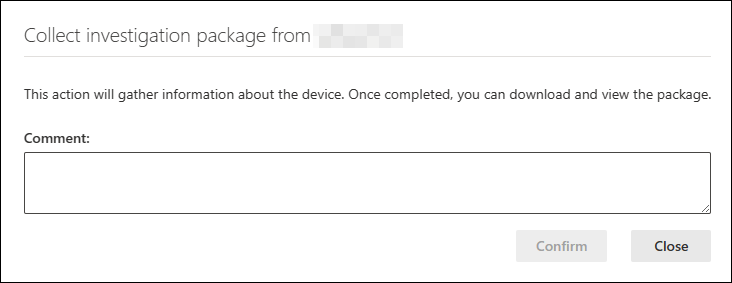
从设备页的响应操作部分选择 “收集调查包 ”。

添加批注并选择“ 确认”。
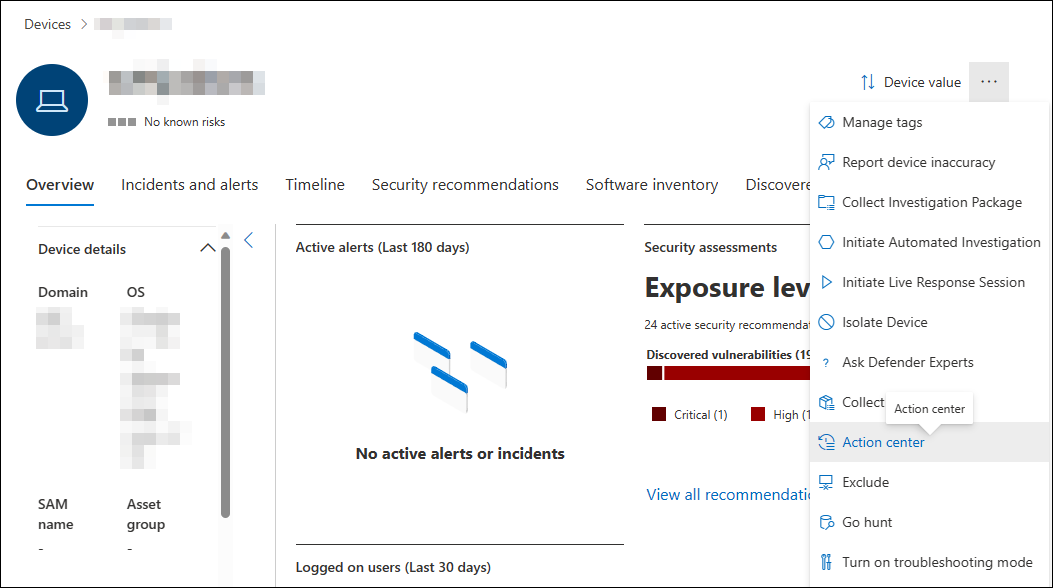
从设备页的响应操作部分选择“ 操作中心 ”。
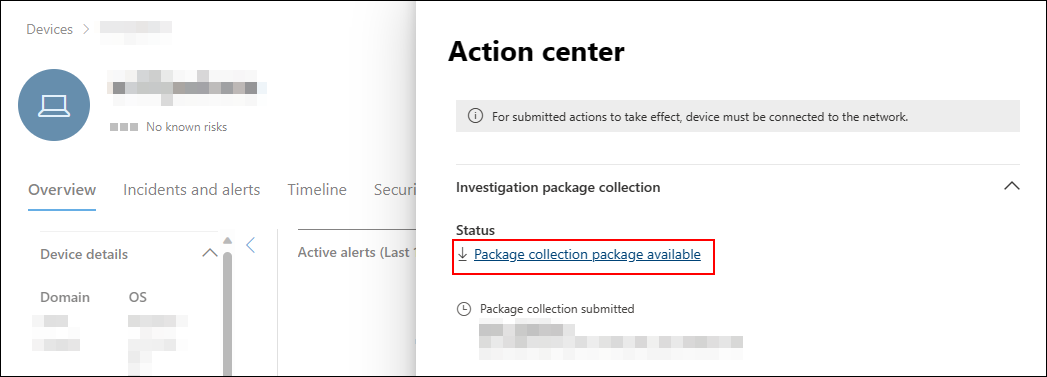
单击 可用的“包收集包 ”以下载收集包。
对于 Windows 设备,包包含以下文件夹:
Folder 说明 自动运行 包含一组文件,每个文件表示已知自动启动入口点的注册表内容, (ASEP) ,以帮助识别攻击者在设备上的持久性。 注意: 如果未找到注册表项,该文件将包含以下消息:“错误:系统找不到指定的注册表项或值。”已安装的程序 此 .CSV 文件包含可帮助确定设备上当前安装的程序列表。 有关详细信息,请参阅 Win32_Product 类。 网络连接 此文件夹包含一组与连接信息相关的数据点,这些数据点可帮助识别与可疑 URL 的连接、攻击者的命令和控制 (C&C) 基础结构、任何横向移动或远程连接。 - ActiveNetConnections.txt:显示协议统计信息和当前 TCP/IP 网络连接。 提供查找进程建立的可疑连接的能力。
- Arp.txt:显示所有接口的当前地址解析协议 (ARP) 缓存表。 ARP 缓存可以显示网络上已遭到入侵的其他主机或网络上可能曾用于运行内部攻击的可疑系统。
- DnsCache.txt:显示 DNS 客户端解析程序缓存的内容,其中包括从本地 Hosts 文件预加载的两个条目,以及计算机解析的名称查询最近获取的任何资源记录。 这有助于识别可疑连接。
- IpConfig.txt:显示所有适配器的完整 TCP/IP 配置。 适配器可以表示物理接口(例如已安装的网络适配器)或逻辑接口(例如拨号连接)。
- FirewallExecutionLog.txt 和pfirewall.log
注意: pfirewall.log文件必须存在于 %windir%\system32\logfiles\firewall\pfirewall.log 中,因此它将包含在调查包中。 有关创建防火墙日志文件的详细信息,请参阅使用高级安全日志配置Windows Defender防火墙预提取文件 Windows 预提取文件旨在加快应用程序启动过程。 它可用于跟踪系统中最近使用的所有文件,并查找可能已删除但仍可在预提取文件列表中找到的应用程序的跟踪。 - 预提取文件夹:包含中
%SystemRoot%\Prefetch预提取文件的副本。 注意:建议下载预提取文件查看器以查看预提取文件。 - PrefetchFilesList.txt:包含可用于跟踪预提取文件夹是否存在任何复制失败的所有已复制文件的列表。
流程 包含一个 .CSV 文件,其中列出了正在运行的进程,并提供识别设备上正在运行的当前进程的功能。 这在识别可疑进程及其状态时很有用。 计划任务 包含列出计划任务的 .CSV 文件,该文件可用于标识在所选设备上自动执行的例程,以查找设置为自动运行的可疑代码。 安全事件日志 包含安全事件日志,其中包含登录或注销活动的记录,或者系统审核策略指定的其他安全相关事件。 注意: 使用事件查看器打开事件日志文件。服务 包含列出服务及其状态的 .CSV 文件。 Windows Server 消息块 (SMB) 会话 Lists对文件、打印机和串行端口的共享访问,以及网络上节点之间的其他通信。 这有助于识别数据外泄或横向移动。 包含 SMBInboundSessions 和 SMBOutboundSession 的文件。
注意: 如果没有 (入站或出站) 会话,你将获得一个文本文件,告知你找不到 SMB 会话。系统信息 包含列出系统信息(如 OS 版本和网卡)的 SystemInformation.txt 文件。 临时目录 包含一组文本文件,其中列出了系统中每个用户位于 %Temp% 中的文件。 这有助于跟踪攻击者可能已在系统上丢弃的可疑文件。
注意: 如果文件包含以下消息:“系统找不到指定的路径”,则表示此用户没有临时目录,可能是因为用户未登录到系统。用户和组 提供一个文件列表,每个文件都表示一个组及其成员。 WdSupportLogs 提供 MpCmdRunLog.txt 和 MPSupportFiles.cab CollectionSummaryReport.xls 此文件是调查包集合的摘要,它包含数据点列表、用于提取数据的命令、执行状态以及出现失败时的错误代码。 可以使用此报告跟踪包是否包含所有预期数据,并确定是否存在任何错误。 适用于 macOS 和 Linux 设备的集合包包含以下项:
Object macOS Linux 应用程序 所有已安装应用程序的列表 不适用 磁盘卷 - 可用空间量
- 所有已装载磁盘卷的列表
- 所有分区的列表
- 可用空间量
- 所有已装载磁盘卷的列表
- 所有分区的列表
文件 所有打开的文件的列表,其中包含使用这些文件的相应进程 所有打开的文件的列表,其中包含使用这些文件的相应进程 历史记录 Shell 历史记录 不适用 内核模块 所有加载的模块 不适用 网络连接 - 活动连接
- 活动侦听连接
- ARP 表
- 防火墙规则
- 接口配置
- 代理设置
- VPN 设置
- 活动连接
- 活动侦听连接
- ARP 表
- 防火墙规则
- IP 列表
- 代理设置
流程 所有正在运行的进程的列表 所有正在运行的进程的列表 服务和计划任务 - 证书
- 配置文件
- 硬件信息
- CPU 详细信息
- 硬件信息
- 操作系统信息
系统安全信息 - 可扩展固件接口 (EFI) 完整性信息
- 防火墙状态
- 恶意软件删除工具 (MRT) 信息
- 系统完整性保护 (SIP) 状态
不适用 用户和组 - 登录历史记录
- Sudoers
- 登录历史记录
- Sudoers
在设备上运行Microsoft Defender防病毒扫描
作为调查或响应过程的一部分,你可以远程启动防病毒扫描,以帮助识别和修正可能存在于受攻击的设备上的恶意软件。
重要
- macOS 和 Linux 客户端版本 101.98.84 及更高版本支持此操作。 还可以使用实时响应来运行操作。 有关实时响应的详细信息,请参阅 使用实时响应调查设备上的实体
- 无论Microsoft Defender防病毒是否是活动防病毒解决方案,Microsoft Defender防病毒扫描都可以与其他防病毒解决方案一起运行。 Microsoft Defender防病毒可以处于被动模式。 有关详细信息,请参阅Microsoft Defender防病毒兼容性。
选择 “运行防病毒扫描”后,选择要运行的扫描类型 (快速或完整) 并在确认扫描之前添加注释。
操作中心将显示扫描信息,并且设备时间线将包含一个新事件,以反映在设备上提交了扫描操作。 Microsoft Defender防病毒警报将反映扫描期间出现的任何检测。
注意
使用 Defender for Endpoint 响应操作触发扫描时,Microsoft Defender防病毒“ScanAvgCPULoadFactor”值仍适用并限制扫描对 CPU 的影响。 如果未配置 ScanAvgCPULoadFactor,则默认值为扫描期间的最大 CPU 负载限制为 50%。 有关详细信息,请参阅 configure-advanced-scan-types-microsoft-defender-防病毒。
限制应用执行
除了通过停止恶意进程来遏制攻击之外,还可以锁定设备并阻止潜在恶意程序的后续尝试运行。
重要
- 此操作适用于Windows 10版本 1709 或更高版本、Windows 11和 Windows Server 2019 或更高版本的设备。
- 如果你的组织使用 Microsoft Defender 防病毒,则此功能可用。
- 此操作需要满足Windows Defender应用程序控制代码完整性策略格式和签名要求。 有关详细信息,请参阅 代码完整性策略格式和签名) 。
为了限制应用程序运行,将应用代码完整性策略,该策略仅允许文件在由 Microsoft 颁发的证书签名的情况下运行。 这种限制方法有助于防止攻击者控制受攻击的设备并执行进一步的恶意活动。
注意
你将能够随时取消应用程序运行的限制。 设备页上的按钮将更改为 “删除应用限制”,然后执行与限制应用执行相同的步骤。
在设备页面上选择“ 限制应用执行 ”后,键入注释并选择“ 确认”。 操作中心将显示扫描信息,设备时间线将包含新事件。
设备用户的通知
限制应用时,将显示以下通知,通知用户应用被限制运行:
注意
通知在 Windows Server 2016 和 Windows Server 2012 R2 上不可用。
将设备从网络隔中离出来
根据攻击的严重性和设备的敏感度,你可能希望将设备与网络隔离。 此操作可帮助防止攻击者控制受攻击的设备并执行其他活动,例如数据外泄和横向移动。
重要
- 客户端版本 101.98.84 及更高版本的 macOS 支持将设备与网络隔离。 还可以使用实时响应来运行操作。 有关实时响应的详细信息,请参阅 使用实时响应调查设备上的实体
- 完全隔离适用于运行 Windows 11、Windows 10、版本 1703 或更高版本、Windows Server 2022、Windows Server 2019 Windows Server 2016 和 Windows Server 2012 R2 的设备。
- 可以在系统要求中列出的 Linux 上所有受支持的Microsoft Defender for Endpoint上使用设备隔离功能。 确保已启用以下先决条件:iptable、ip6table 和 Linux 内核,CONFIG_NETFILTER、CONFID_IP_NF_IPTABLES和CONFIG_IP_NF_MATCH_OWNER。
- 选择性隔离适用于运行 Windows 10 版本 1709 或更高版本和Windows 11的设备。
- 隔离设备时,仅允许某些进程和目标。 因此,在隔离设备后,位于完整 VPN 隧道后面的设备将无法访问Microsoft Defender for Endpoint云服务。 建议对Microsoft Defender for Endpoint使用拆分隧道 VPN,并Microsoft Defender防病毒基于云的保护相关流量。
- 此功能支持 VPN 连接。
- 必须至少具有以下一个角色权限:“主动修正操作”。 有关详细信息,请参阅Create和管理角色。
- 必须能够基于设备组设置访问设备。 有关详细信息,请参阅Create和管理设备组。
- 不支持对 macOS 和 Linux 隔离进行排除。
- 当管理员修改或向隔离设备添加新的 iptable 规则时,隔离设备将从隔离中删除。
- 隔离在 Microsoft Hyper-V上运行的服务器会阻止流向服务器的所有子虚拟机的网络流量。
此设备隔离功能在保持与 Defender for Endpoint 服务的连接时,会断开受攻击设备与网络的连接,后者会继续监视设备。
在 Windows 10 版本 1709 或更高版本上,可以更好地控制网络隔离级别。 你还可以选择启用 Outlook、Microsoft Teams 和Skype for Business连接 (“选择性隔离”) 。
注意
你可以随时将设备重新连接到网络。 设备页上的按钮将更改为“ 从隔离中释放”,然后执行与隔离设备相同的步骤。
在设备页面上选择“ 隔离设备 ”后,键入注释并选择“ 确认”。 操作中心将显示扫描信息,设备时间线将包含新事件。
注意
设备将保持连接到 Defender for Endpoint 服务,即使它与网络隔离。 如果选择启用 Outlook 并Skype for Business通信,则可以在设备隔离时与用户通信。 选择性隔离仅适用于经典版本的 Outlook 和 Microsoft Teams。
从隔离中强制释放设备
设备隔离功能是保护设备免受外部威胁的宝贵工具。 但是,在某些情况下,隔离设备变得无响应。
这些实例有一个可下载的脚本,你可以运行该脚本来强制从隔离中释放设备。 该脚本可通过 UI 中的链接获得。
注意
- 安全中心权限中的管理员和管理安全设置可以强制解除设备隔离。
- 该脚本仅对特定设备有效。
- 脚本将在三天后过期。
若要从隔离中强制释放设备,请执行以下操作:
- 在设备页上,选择“ 下载脚本”以强制从操作菜单中分离设备 。
- 在右侧向导中,选择“ 下载脚本”。
最低要求
“强制释放设备脱离隔离”功能的最低要求是:
- 仅支持 Windows
- 支持以下 Windows 版本:
- Windows 10 21H2 和 22H2 以及 KB KB5023773
- Windows 11版本 21H2,包含KB5023774的所有版本
- Windows 11版本 22H2,包含KB5023778的所有版本
设备用户的通知
当设备被隔离时,将显示以下通知,通知用户设备正在与网络隔离:
注意
通知在非 Windows 平台上不可用。
包含来自网络的设备
识别出已遭到入侵或可能遭到入侵的非托管设备时,可能需要从网络包含该设备。 当你包含设备时,任何Microsoft Defender for Endpoint载入的设备都会阻止与该设备的传入和传出通信。 当安全运营分析员查找、识别和修正受攻击设备上的威胁时,此操作可帮助防止相邻设备受到威胁。
注意
在载入的 Microsoft Defender for Endpoint Windows 10 和 Windows Server 2019+ 设备上,支持阻止与“包含”设备进行传入和传出通信。
如何包含设备
包含设备页中的设备
还可以通过从操作栏中选择“包含设备”,从设备页面 包含设备 :
注意
最多可能需要 5 分钟才能获取新包含的设备的详细信息,Microsoft Defender for Endpoint已载入的设备。
重要
- 如果包含的设备更改了其 IP 地址,则所有Microsoft Defender for Endpoint加入的设备都将识别这一点并开始阻止与新 IP 地址的通信。 原始 IP 地址将不再被阻止 (最长可能需要 5 分钟才能) 查看这些更改。
- 如果包含的设备 IP 由网络上的另一台设备使用,则包含设备时会出现警告,其中包含高级搜寻 (的链接,其中包含预填充的查询) 。 这将为使用同一 IP 的其他设备提供可见性,以帮助你在继续包含设备时做出有意识的决定。
- 如果包含的设备是网络设备,则会显示警告,并显示一条消息,指出这可能导致网络连接问题 (例如,包含充当默认网关) 的路由器。 此时,你将能够选择是否包含设备。
包含设备后,如果行为不符合预期,请验证是否已在载入 Defender for Endpoint 的设备上启用基本筛选引擎 (BFE) 服务。
停止包含设备
可以随时停止包含设备。
从“ 设备清单 ”中选择设备,或打开“设备”页。
从操作菜单中选择“ 从包含中释放 ”。 此操作将还原此设备与网络的连接。
包含来自网络的用户
当网络中某个标识可能遭到入侵时,必须阻止该标识访问网络和不同的终结点。 Defender for Endpoint 可以“包含”标识,阻止其访问,并帮助防止攻击,特别是勒索软件。 包含标识后,任何受支持的Microsoft Defender for Endpoint载入设备都将阻止与 (网络登录、RPC、SMB、RDP) 攻击相关的特定协议中的传入流量,终止正在进行的远程会话并注销现有 RDP 连接, (终止会话本身,包括其所有相关进程) ,同时启用合法流量。 此操作可显著帮助减少攻击的影响。 包含标识后,安全运营分析师将有额外的时间来查找、识别和修正对已泄露标识的威胁。
注意
使用新式代理的载入Microsoft Defender for Endpoint Windows 10和 11 台设备( (Sense 版本 8740 及更高版本) 、Windows Server 2019+ 设备以及 Windows Server 2012R2 和 2016)支持阻止与“包含”用户的传入通信。
如何包含用户
目前,仅通过使用自动攻击中断自动提供包含用户。 当 Microsoft 检测到某个用户遭到入侵时,会自动设置“包含用户”策略。
查看包含用户操作
包含用户后,可以在操作中心的此历史记录视图中查看操作。 在这里,可以查看操作发生的时间,以及组织中包含的用户:
此外,在标识被视为“已包含”后,该用户将被 Defender for Endpoint 阻止,并且无法对任何受支持的 Defender for Endpoint 载入设备执行任何恶意横向移动或远程加密。 这些块将显示为警报,帮助你快速查看受攻击用户尝试访问的设备以及潜在的攻击技术:
撤消包含用户操作
可以随时释放用户的块和包含:
- 在操作中心中选择“包含用户”操作。 在侧窗格中,选择“撤消”
- 从用户清单、事件页面侧窗格或警报侧窗格中选择用户,然后选择 “撤消”
此操作将还原此用户与网络的连接。
包含用户的调查功能
包含用户后,可以通过查看受攻击用户的阻止操作来调查潜在威胁。 在“设备时间线”视图中,可以看到有关特定事件的信息,包括协议和接口粒度,以及与之关联的相关 MITRE 技术。
此外,还可以使用高级搜寻来扩展调查。 在“DeviceEvents”表中查找以“Contain”开头的任何“操作类型”。 然后,可以查看与租户中包含用户相关的所有不同单一阻止事件,深入了解每个块的上下文,并提取与这些事件关联的不同实体和技术。
咨询威胁专家
可以咨询 Microsoft 威胁专家,获取有关可能遭到入侵或已遭到入侵的设备的更多信息。 Microsoft 威胁专家可以直接从Microsoft Defender XDR进行参与,以便及时准确地做出响应。 专家不仅提供有关可能遭到入侵的设备的见解,还有助于更好地了解复杂的威胁、你获取的定向攻击通知,或者是否需要有关警报的详细信息,或者门户中仪表板看到的威胁情报上下文。
有关详细信息 ,请参阅配置和管理终结点攻击通知 。
在操作中心检查活动详细信息
操作中心提供有关在设备或文件上执行的操作的信息。 你将能够查看以下详细信息:
- 调查包集合
- 防病毒扫描
- 应用限制
- 设备隔离
还会显示所有其他相关详细信息,例如提交日期/时间、提交用户以及操作是否成功或失败。
另请参阅
提示
想要了解更多信息? Engage技术社区中的 Microsoft 安全社区:Microsoft Defender for Endpoint技术社区。
反馈
即将发布:在整个 2024 年,我们将逐步淘汰作为内容反馈机制的“GitHub 问题”,并将其取代为新的反馈系统。 有关详细信息,请参阅:https://aka.ms/ContentUserFeedback。
提交和查看相关反馈














