根据网络位置控制对 SharePoint 和 OneDrive 数据的访问
作为 IT 管理员,可以根据你信任的已定义网络位置控制对 Microsoft 365 中 SharePoint 和 OneDrive 资源的访问。 这也称为基于位置的策略。
为此,可以通过指定一个或多个授权的 IP 地址范围来定义受信任的网络边界。 任何尝试从此网络边界外部访问 SharePoint 和 OneDrive (在任何设备上使用 Web 浏览器、桌面应用程序或移动应用) 的用户都将受到阻止。
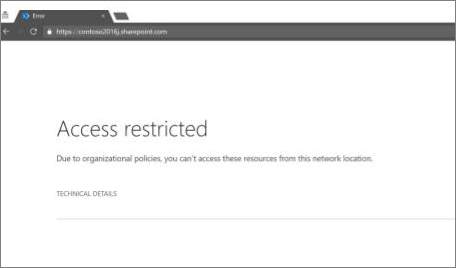
下面是设置基于位置的策略的一些重要注意事项:
外部共享:如果文件和文件夹已与进行身份验证的来宾共享,则他们无法访问定义的 IP 地址范围以外的资源。
从第一方和第三方应用访问:通常,可以从 Exchange、Viva Engage、Skype、Teams、Planner、Power Automate、PowerBI、Power Apps、OneNote 等应用访问 SharePoint 文档。 启用基于位置的策略后,将阻止不支持基于位置的策略的应用。 目前唯一支持基于位置的策略的应用是 Teams、Viva Engage和 Exchange。 这意味着,即使这些应用托管在受信任的网络边界内,也会阻止所有其他应用。 这是因为 SharePoint 无法确定这些应用程序的用户是否在受信任的边界内。
注意
建议为 SharePoint 启用基于位置的策略时,应为 Exchange 和 Viva Engage 配置相同的策略和 IP 地址范围。 SharePoint 依赖于这些服务来强制这些应用的用户在受信任的 IP 范围内。 为了通过 Office.com 门户保护对 SharePoint 的访问,我们建议对“Office 365”使用Microsoft Entra条件访问策略,并在其中配置受信任的 IP 范围。
从动态 IP 范围访问:多个服务和提供程序托管具有动态原始 IP 地址的应用。 例如,从一个 Azure 数据中心运行时访问 SharePoint 的服务可能会由于故障转移条件或其他原因而从其他数据中心开始运行,从而动态更改其 IP 地址。 基于位置的条件访问策略依赖于固定的受信任 IP 地址范围。 如果无法提前确定 IP 地址范围,则基于位置的策略可能不是环境的一个选项。
在新 SharePoint 管理中心中设置基于位置的策略
注意
这些设置最多可能需要 15 分钟才能生效。
- 转到新的 SharePoint 管理中心的“访问控制”,并使用对组织具有管理员权限的帐户登录。
注意
如果Office 365由世纪互联 (中国) 运营,请登录Microsoft 365 管理中心,然后浏览到 SharePoint 管理中心并打开“访问控制”页面。
选择“ 网络位置”,并启用 “仅允许从特定 IP 地址范围进行访问”。
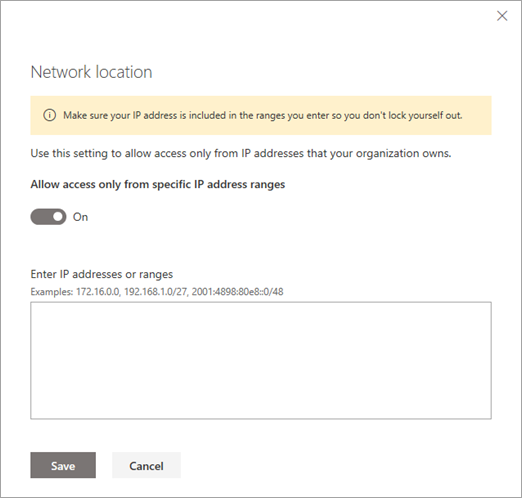
输入 IP 地址和地址范围,以逗号分隔。
重要
请确保包含自己的 IP 地址,以免锁定自己。此设置不仅限制对 OneDrive 和 SharePoint 网站的访问,还限制对 OneDrive 和 SharePoint 管理中心以及运行 PowerShell cmdlet 的访问。 如果锁定自己,并且无法从指定范围内的 IP 地址进行连接,则需要联系支持人员寻求帮助。
如果保存重叠的 IP 地址,用户将看到一条通用错误消息,其中包含指向“输入 IP 允许列表具有重叠”的相关 ID。
注意
若要使用 PowerShell 设置基于位置的策略,请使用 -IPAddressAllowList 参数运行 Set-SPOTenant。 有关详细信息,请参阅 Set-SPOTenant。
反馈
即将发布:在整个 2024 年,我们将逐步淘汰作为内容反馈机制的“GitHub 问题”,并将其取代为新的反馈系统。 有关详细信息,请参阅:https://aka.ms/ContentUserFeedback。
提交和查看相关反馈