附录 C:Active Directory 中受保护的帐户和组
适用范围:Windows Server 2022、Windows Server 2019、Windows Server 2016、Windows Server 2012 R2、Windows Server 2012
附录 C:Active Directory 中受保护的帐户和组
在 Active Directory 中,默认的一组高特权帐户和组被视为受保护帐户和组。 对于 Active Directory 中的大多数对象,被委派管理 Active Directory 对象的权限的用户可以更改对象的权限,包括更改权限以允许自己修改特殊组的成员身份。
受保护的帐户和组是通过自动过程设置和强制执行权限的特殊对象,以确保对对象的权限保持一致。 即使将对象移动到 Active Directory 中的不同位置,这些权限仍保持不变。 如果受保护对象的权限被修改,现有流程会确保权限快速恢复为默认值。
受保护组
以下安全帐户和组在 Active Directory 域服务中受到保护:
- Account Operators
- 管理员
- 管理员
- 备份操作员
- Domain Admins
- Domain Controllers
- 企业管理员
- Krbtgt
- 打印操作员
- 只读域控制器
- 复制程序
- Schema Admins
- Server Operators
AdminSDHolder
AdminSDHolder 对象的作用是为域中受保护的帐户和组提供“模板”权限。 在每个 Active Directory 域的系统容器中,将自动创建 AdminSDHolder 作为对象。 其路径为:CN=AdminSDHolder,CN=System,DC=<domain_component>,DC=<domain_component>?。
虽然 Administrators 组拥有 Active Directory 域中的大多数对象,但 Domain Admins 组拥有 AdminSDHolder 对象。 默认情况下,企业管理员可以对任何域的 AdminSDHolder 对象进行更改,域的域管理员和管理员组也是如此。 此外,尽管 AdminSDHolder 的默认所有者是域的域管理员组,但管理员或企业管理员的成员可以取得该对象的所有权。
SDProp
SDProp 是在包含域的 PDC 仿真器 (PDCE) 的域控制器上每隔 60 分钟(默认间隔)运行的一个进程。 SDProp 将域的 AdminSDHolder 对象的权限与域中受保护的帐户和组的权限进行比较。 如果任何受保护帐户和组的权限与 AdminSDHolder 对象的权限不匹配,则 SDProp 会重置受保护帐户和组的权限,使其与为域的 AdminSDHold 对象配置的权限相匹配。
对受保护的组和帐户禁用权限继承。 即使帐户和组移动到目录中的不同位置,它们也不会从新的父对象继承权限。 AdminSDHolder 对象会禁用继承,以便对父对象的权限更改不会更改 AdminSDHolder 的权限。
更改 SDProp 间隔
除非要进行测试,否则一般不需要更改 SDProp 的运行间隔。 如果需要更改 SDProp 间隔,请在域的 PDCE 上,使用注册表编辑器添加或修改 HKLM\SYSTEM\CurrentControlSet\Services\NTDS\Parameters 中的 AdminSDProtectFrequency DWORD 值。
值的范围为 60 到 7200 秒(一分钟到两小时)。 若要删除更改,请删除 AdminSDProtectFrequency 密钥。 删除密钥会导致 SDProp 还原回到 60 分钟间隔。 一般情况下,不应在生产域中减少此间隔,因为这会增加域控制器上的 LSASS 处理开销。 这种开销增加所造成的影响取决于域中受保护对象的数量。
手动运行 SDProp
测试 AdminSDHolder 更改的较好方法是手动运行 SDProp,这会导致任务立即运行但不影响计划的执行。 可以使用 Ldp.exe 或通过运行 LDAP 修改脚本来强制运行 SDProp。 要手动执行 SDProp,请执行以下步骤:
启动 Ldp.exe。
在 Ldp 对话框中单击连接,然后单击连接。
在连接对话框中,键入包含 PDC 仿真器 (PDCE) 角色的域的域控制器名称,然后单击确定。
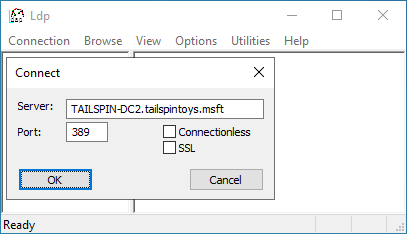
若要验证连接,请确认 Dn: (RootDSE) 与以下屏幕截图类似。 接下来,单击连接,然后单击绑定。
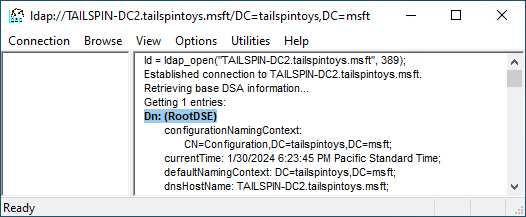
在绑定对话框中,键入有权修改 rootDSE 对象的用户帐户的凭据。 (如果你已以该用户的身份登录,可以选择作为当前已登录用户绑定。)单击确定。
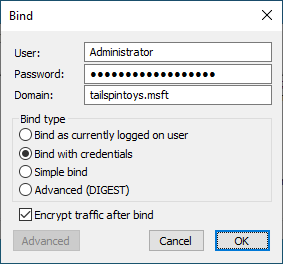
绑定操作完成后,单击浏览,然后单击修改。
在修改对话框中,将 DN 字段留空。 在编辑条目属性字段中键入 RunProtectAdminGroupsTask,在值字段中键入 1。 单击输入以填充条目列表,如下所示。
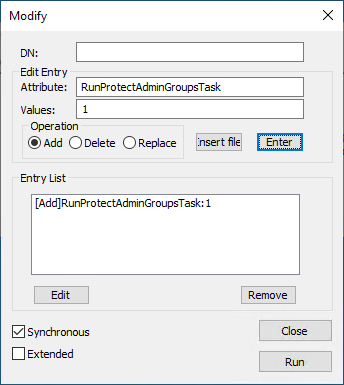
在已填充的修改对话框中单击运行,并验证对 AdminSDHolder 对象所做的更改是否已显示在该对象上。